|
Key Exchange
Key exchange (also key establishment) is a method in cryptography by which cryptographic keys are exchanged between two parties, allowing use of a cryptographic algorithm. If the sender and receiver wish to exchange encrypted messages, each must be equipped to encrypt messages to be sent and decrypt messages received. The nature of the equipping they require depends on the encryption technique they might use. If they use a code, both will require a copy of the same codebook. If they use a cipher, they will need appropriate keys. If the cipher is a symmetric key cipher, both will need a copy of the same key. If it is an asymmetric key cipher with the public/private key property, both will need the other's public key. Channel of exchange Key exchange is done either in-band or out-of-band. The key exchange problem The key exchange problem describes ways to exchange whatever keys or other information are needed for establishing a secure communication channel so that no one else ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Signature Algorithm
The Digital Signature Algorithm (DSA) is a Public-key cryptography, public-key cryptosystem and Federal Information Processing Standards, Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the Discrete logarithm, discrete logarithm problem. In a digital signature system, there is a keypair involved, consisting of a private and a public key. In this system a signing entity that declared their public key can generate a signature using their private key, and a verifier can assert the source if it verifies the signature correctly using the declared public key. DSA is a variant of the Schnorr signature, Schnorr and ElGamal signature scheme, ElGamal signature schemes. The National Institute of Standards and Technology (NIST) proposed DSA for use in their Digital Signature Standard (DSS) in 1991, and adopted it as FIPS 186 in 1994. Five revisions to the initial specification have been released. The newest specifi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authoritarianism
Authoritarianism is a political system characterized by the rejection of political plurality, the use of strong central power to preserve the political ''status quo'', and reductions in democracy, separation of powers, civil liberties, and the rule of law. Authoritarian regimes may be either autocratic or oligarchic and may be based upon the rule of a party or the military. States that have a blurred boundary between democracy and authoritarianism have sometimes been characterized as "hybrid democracies", " hybrid regimes" or "competitive authoritarian" states. The political scientist Juan Linz, in an influential 1964 work, ''An Authoritarian Regime: Spain'', defined authoritarianism as possessing four qualities: # Limited political pluralism, which is achieved with constraints on the legislature, political parties and interest groups. # Political legitimacy based on appeals to emotion and identification of the regime as a necessary evil to combat "easily recognizabl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Argument From Authority
An argument from authority is a form of argument in which the opinion of an authority figure (or figures) who lacks relevant expertise is used as evidence to support an argument. The argument from authority is an informal fallacy, and obtaining knowledge in this way is fallible. Forms Deductive This argument is a form of genetic fallacy; in which the conclusion about the validity of a statement is justified by appealing to the characteristics of the person who is speaking, such as also in the '' ad hominem'' fallacy. For this argument, Locke coined the term ''argumentum ad verecundiam'' (appeal to shamefacedness/modesty) because it appeals to the fear of humiliation by appearing disrespectful to a particular authority. This qualification as a logical fallacy implies that this argument is invalid when using the deductive method, and therefore it cannot be presented as infallible. In other words, it is logically invalid to prove a claim is true simply because an authority has ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Legislation
Legislation is the process or result of enrolling, enacting, or promulgating laws by a legislature, parliament, or analogous governing body. Before an item of legislation becomes law it may be known as a bill, and may be broadly referred to as "legislation" while it remains under consideration to distinguish it from other business. Legislation can have many purposes: to regulate, to authorize, to outlaw, to provide (funds), to sanction, to grant, to declare, or to restrict. It may be contrasted with a non-legislative act by an executive or administrative body under the authority of a legislative act. Overview Legislation to design or amend a bill requires identifying a concrete issue in a comprehensive way. When engaging in legislation, drafters and policy-makers must take into consideration the best possible avenues to address problem areas. Possible solutions within bill provisions might involve implementing sanctions, targeting indirect behaviors, authorizing agency ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
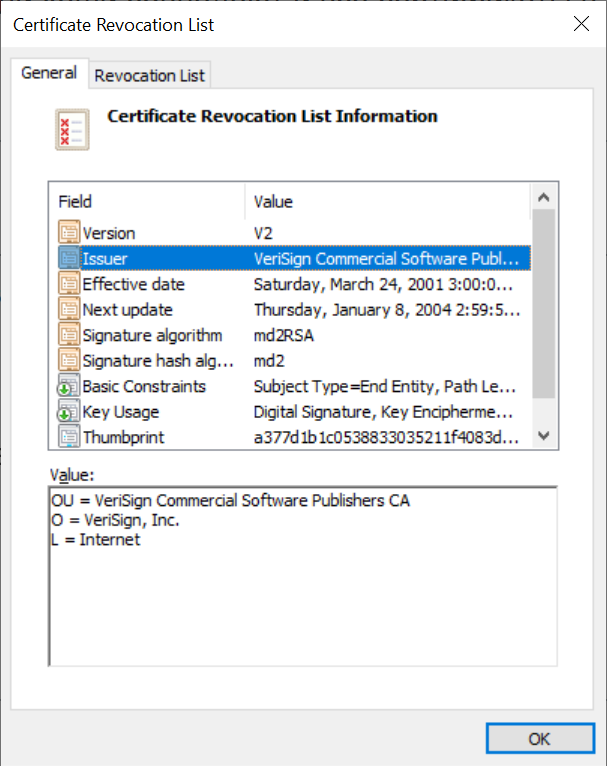
Certificate Revocation List
In cryptography, a certificate revocation list (CRL) is "a list of digital certificates that have been revoked by the issuing certificate authority (CA) before their scheduled expiration date and should no longer be trusted". Publicly trusted CAs in the Web PKI are required (including by the CA/Browser forum) to issue CRLs for their certificates, and they widely do. Browsers and other relying parties might use CRLs, or might use alternate certificate revocation technologies (such as Online Certificate Status Protocol, OCSP) or CRLSets (a dataset derived from CRLs) to check certificate revocation status. Note that OCSP is falling out of favor due to privacy and performance concerns. Subscribers and other parties can also use ARI. Revocation states There are two different states of revocation defined in RFC 5280: ; Revoked: A certificate is irreversibly revoked if, for example, it is discovered that the certificate authority (CA) had improperly issued a certificate, or if a pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Certificate
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity of a public key. The certificate includes the public key and information about it, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the device examining the certificate trusts the issuer and finds the signature to be a valid signature of that issuer, then it can use the included public key to communicate securely with the certificate's subject. In email encryption, code signing, and e-signature systems, a certificate's subject is typically a person or organization. However, in Transport Layer Security (TLS) a certificate's subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices. TLS, sometime ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle (MITM) attack, or on-path attack, is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, where in actuality the attacker has inserted themselves between the two user parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. In this scenario, the attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within range of a Wi-Fi access point hosting a network without encryption could insert themselves as a man in the middle. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ralph Merkle
Ralph C. Merkle (born February 2, 1952) is an American computer scientist and mathematician. He is one of the inventors of public-key cryptography, the inventor of cryptographic hashing, and more recently a researcher and speaker on cryonics. Merkle is a renowned cryptographer, known for devising Merkle's Puzzles, co-inventing the Merkle–Hellman knapsack cryptosystem, and inventing cryptographic hashing ( Merkle–Damgård construction) and Merkle trees. He has worked as a manager at Elxsi, research scientist at Xerox PARC (Palo Alto Research Center), and a nanotechnology theorist at Zyvex. Merkle has held positions as a Distinguished Professor at Georgia Tech, senior research fellow at IMM, faculty member at Singularity University, and board member at Alcor Life Extension Foundation. He received the IEEE Richard W. Hamming Medal in 2010 and has published works on molecular manipulation and self-replicating machines. Ralph Merkle is a grandnephew of baseball star Fr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |