|
Gardening (cryptanalysis)
In cryptanalysis, gardening is the act of encouraging a target to use known plaintext in an encrypted message, typically by performing some action the target is sure to report. It was a term used during World War II at the British Government Code and Cypher School at Bletchley Park, England, for schemes to entice the Germans to include particular words, which the British called " cribs", in their encrypted messages. This term presumably came from RAF minelaying missions, or "gardening" sorties. "Gardening" was standard RAF slang for sowing mines in rivers, ports and oceans from low heights, possibly because each sea area around the European coasts was given a code-name of flowers or vegetables. The technique is claimed to have been most effective against messages produced by the German Navy's Enigma machines. If the Germans had recently swept a particular area for mines, and analysts at Bletchley Park were in need of some cribs, they might (and apparently did on several occas ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. In addition to mathematical analysis of cryptographic algorithms, cryptanalysis includes the study of side-channel attacks that do not target weaknesses in the cryptographic algorithms themselves, but instead exploit weaknesses in their implementation. Even though the goal has been the same, the methods and techniques of cryptanalysis have changed drastically through the history of cryptography, adapting to increasing cryptographic complexity, ranging from the pen-and-paper methods of the past, through machines like the British Bombes and Colossus computers at Bletchley Park in World War II, to the mathematically advanced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Known Plaintext
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the world's countries participated, with many nations mobilising all resources in pursuit of total war. Tanks in World War II, Tanks and Air warfare of World War II, aircraft played major roles, enabling the strategic bombing of cities and delivery of the Atomic bombings of Hiroshima and Nagasaki, first and only nuclear weapons ever used in war. World War II is the List of wars by death toll, deadliest conflict in history, causing World War II casualties, the death of 70 to 85 million people, more than half of whom were civilians. Millions died in genocides, including the Holocaust, and by massacres, starvation, and disease. After the Allied victory, Allied-occupied Germany, Germany, Allied-occupied Austria, Austria, Occupation of Japan, Japan, a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Government Code And Cypher School
The Government Code and Cypher School (GC&CS) was a British signals intelligence agency set up in 1919. During the First World War, the British Army and Royal Navy had separate signals intelligence agencies, MI1b and NID25 (initially known as Room 40) respectively. It was particularly known for its work on codebreaking at Bletchley Park and after the war became the Government Communications Headquarters (GCHQ). Interwar period In 1919, the Cabinet's Secret Service Committee, chaired by Lord Curzon, recommended that a peacetime codebreaking agency should be created, a task which was given to the Director of Naval Intelligence, Hugh Sinclair.Johnson, 1997, p. 44 Sinclair merged staff from NID25 and MI1b into the new organisation, which initially consisted of around 25–30 officers and a similar number of clerical staff. It was titled the "Government Code and Cypher School" (GC&CS), a cover-name which was chosen by Victor Forbes of the Foreign Office. Alastair Denniston, who h ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the Second World War. During World War II, the estate housed the Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers most importantly the German Enigma machine, Enigma and Lorenz cipher, Lorenz ciphers. The GC&CS team of codebreakers included John Tiltman, Dilwyn Knox, Alan Turing, Harry Golombek, Gordon Welchman, Conel Hugh O'Donel Alexander, Hugh Alexander, Donald Michie, W. T. Tutte, Bill Tutte and Stuart Milner-Barry. The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus computer, Colossus, the world's first programmable digital electronic computer. Codebreaking operations at Bletchley Park ended in 1946 and al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crib (cryptanalysis)
The known-plaintext attack (KPA) is an attack model for cryptanalysis where the attacker has access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib" originated at Bletchley Park, the British World War II decryption operation, where it was defined as: History The usage "crib" was adapted from a slang term referring to cheating (e.g., "I cribbed my answer from your test paper"). A "crib" originally was a literal or interlinear translation of a foreign-language text—usually a Latin or Greek text—that students might be assigned to translate from the original language. The idea behind a crib is that cryptologists were looking at incomprehensible ciphertext, but if they had a clue about some word or phrase that might be expected to be in the ciphertext, they would have a "wedge," a test to break into it. If their otherwise random attacks on the cipher managed to sometimes produce th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enigma Machine
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the Wehrmacht, German military. The Enigma machine was considered so secure that it was used to encipher the most top-secret messages. The Enigma has an electromechanical Rotor machine, rotor mechanism that scrambles the 26 letters of the alphabet. In typical use, one person enters text on the Enigma's keyboard and another person writes down which of the 26 lights above the keyboard illuminated at each key press. If plaintext is entered, the illuminated letters are the ciphertext. Entering ciphertext transforms it back into readable plaintext. The rotor mechanism changes the electrical connections between the keys and the lights with each keypress. The security of the system depends on machine settings that were generally changed daily, based ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Naval Mine
A naval mine is a self-contained explosive weapon placed in water to damage or destroy surface ships or submarines. Similar to anti-personnel mine, anti-personnel and other land mines, and unlike purpose launched naval depth charges, they are deposited and left to wait until, depending on their fuzing, they are triggered by the approach of or contact with any vessel. Naval mines can be used offensively, to hamper enemy shipping movements or lock vessels into a harbour; or defensively, to create "safe" zones protecting friendly sea lanes, harbours, and naval assets. Mines allow the minelaying force commander to concentrate warships or defensive assets in mine-free areas giving the adversary three choices: undertake a resource-intensive and time-consuming minesweeping effort, accept the casualties of challenging the minefield, or use the unmined waters where the greatest concentration of enemy firepower will be encountered. Although international law requires signatory nations ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bletchley
Bletchley is a constituent town of Milton Keynes, Buckinghamshire, England, in the south-west of the city, split between the civil parishes in England, civil parishes of Bletchley and Fenny Stratford and West Bletchley, which In 2011 had a combined population of 37,114. Bletchley is best known for Bletchley Park, the headquarters of Britain's World War II codebreaking organisation, and now a major tourist attraction. The National Museum of Computing is also located on the Park. History Origins and early modern history The town name is Old English, Anglo-Saxon and means ''Blæcca's clearing''. It was first recorded in Manorialism, manorial rolls in the 12th century as ''Bicchelai'', then later as ''Blechelegh'' (13th century) and ''Blecheley'' (14th–16th centuries). Just to the south of Fenny Stratford, there was Romano-British town, ''Magiovinium, M'' on either side of Watling Street, a Roman road. Bletchley was originally a minor village on the outskirts of Fenny Stratfo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Minesweeping
Minesweeping is the practice of removing explosive naval mines, usually by a specially designed ship called a minesweeper using various measures to either capture or detonate the mines, but sometimes also with an aircraft made for that purpose. Minesweeping has been practiced since the advent of naval mining in 1855 during the Crimean War. The first minesweepers date to that war and consisted of British rowboats trailing Grappling hook, grapnels to snag the mines. By ship A sweep is either a contact sweep, a wire dragged through the water by one or two ships to cut the mooring wire of floating mines, or a distance sweep that mimics a ship to detonate the mines. The sweeps are dragged by minesweeper (ship), minesweepers, either purpose-built military ships or converted Commercial trawler, trawlers. Each run covers between , and the ships must move slowly in a straight line, making them vulnerable to enemy fire. This was exploited by the Turkish army in the Battle of Gallipoli i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
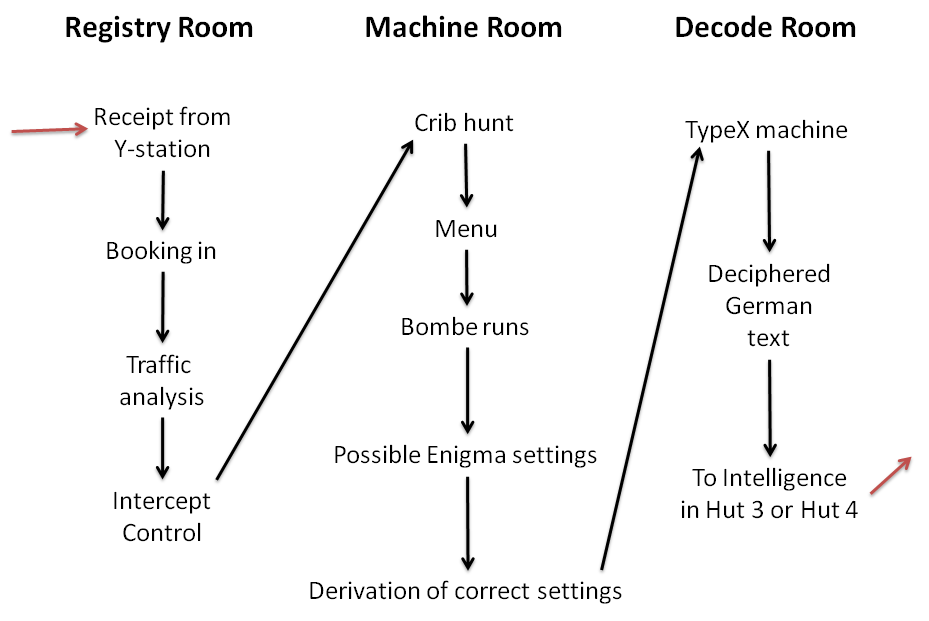
Cryptanalysis Of The Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies of World War II, Allies in World War II to read substantial amounts of Morse code, Morse-coded radio communications of the Axis powers that had been enciphered using Enigma machines. This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the codename ''Ultra (cryptography), Ultra''. The Enigma machines were a family of portable cipher machines with rotor machine, rotor scramblers. Good operating procedures, properly enforced, would have made the plugboard Enigma machine unbreakable to the Allies at that time. The German plugboard-equipped Enigma became the principal cryptography, crypto-system of the Third Reich, German Reich and later of other Axis powers. In December 1932 it was broken by mathematician Marian Rejewski at the Polish General Staff's Cipher Bureau (Poland), Cipher Bureau, using mathematical permutation group theory ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |