|
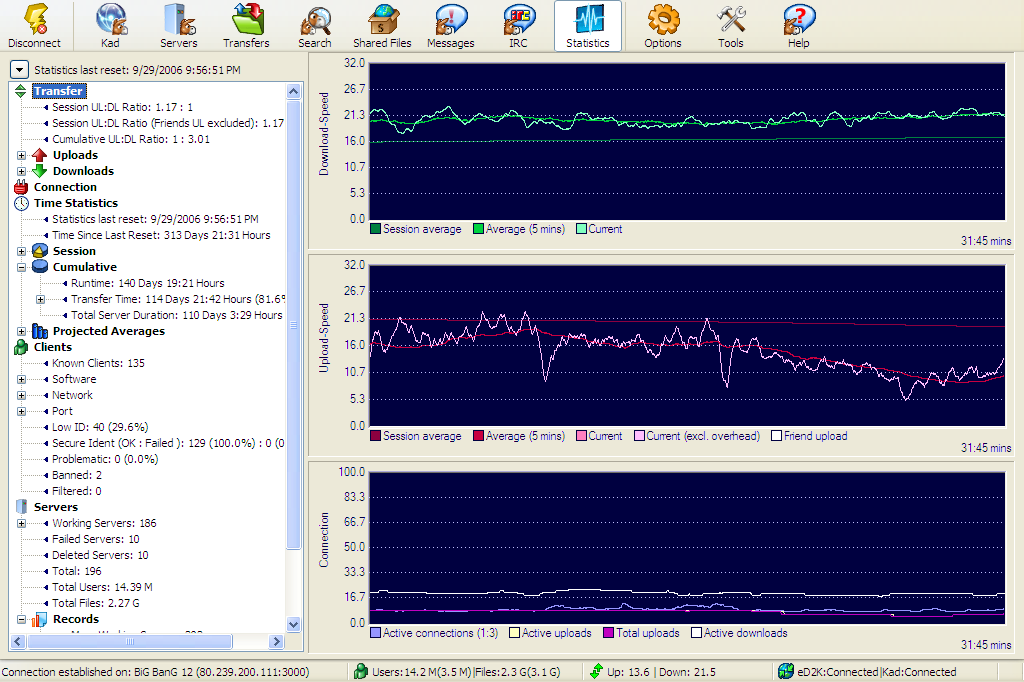
Emule
eMule is a free peer-to-peer file sharing application for Microsoft Windows. Started in May 2002 as an alternative to eDonkey2000, eMule now connects to both the eDonkey network and the Kad network. The distinguishing features of eMule are the direct exchange of sources between client nodes, fast recovery of corrupted downloads, and the use of a credit system to reward frequent uploaders. Furthermore, eMule transmits data in zlib-compressed form to save bandwidth. eMule is coded in C++ using the Microsoft Foundation Classes. Since July 2002 eMule has been free software, released under the GNU General Public License; its popularity has led to eMule's codebase being used as the basis of cross-platform clients aMule, JMule, xMule, along with the release of many eMule ''mods'' (modifications of the original eMule) on the Internet. As of August 2017, it is the fourth most downloaded project on SourceForge, with over 685 million downloads. Development was later restarted by the c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
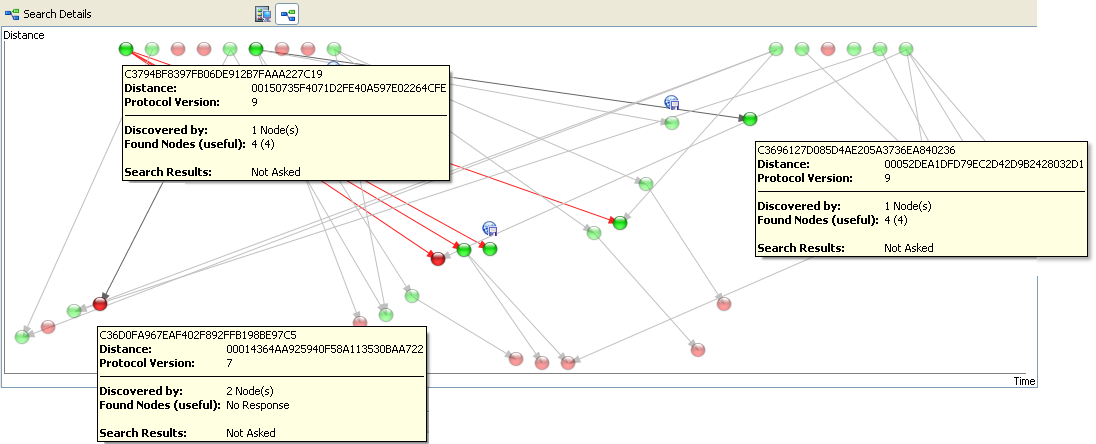
EMule Kad Nodes 20111024142233
eMule is a free peer-to-peer file sharing application for Microsoft Windows. Started in May 2002 as an alternative to eDonkey2000, eMule now connects to both the eDonkey network and the Kad network. The distinguishing features of eMule are the direct exchange of sources between client nodes, fast recovery of corrupted downloads, and the use of a credit system to reward frequent uploaders. Furthermore, eMule transmits data in zlib-compressed form to save bandwidth. eMule is coded in C++ using the Microsoft Foundation Classes. Since July 2002 eMule has been free software, released under the GNU General Public License; its popularity has led to eMule's codebase being used as the basis of cross-platform clients aMule, JMule, xMule, along with the release of many eMule ''mods'' (modifications of the original eMule) on the Internet. As of August 2017, it is the fourth most downloaded project on SourceForge, with over 685 million downloads. Development was later restarted by the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ed2k URI Scheme
In computing, eD2k links (''ed2k://'') are hyperlinks used to denote files stored on computers connected to the eDonkey filesharing P2P network. General Many programs, such as eMule, MLDonkey and the original eDonkey2000 client by '' MetaMachine'', which introduced the link type, as well as others using the eDonkey file sharing protocol, can be used to manage files stored in the filesharing network. eD2k links allow a file to be identified from a link in a web browser and to be downloaded thereafter by a client like eMule, Shareaza or any other compatible software. This linking feature was one of the first URIs to be introduced in peer-to-peer file sharing, and had a vast effect on the development of the eDonkey network, as it allowed external link sites to provide verified content within the network. Nowadays, so-called Magnet links have replaced eD2k links in practice. They serve a similar role, but are not limited to the eD2k hash and can contain other hashes such a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protocol Obfuscation
Protocol encryption (PE), message stream encryption (MSE) or protocol header encrypt (PHE) are related features of some peer-to-peer file-sharing clients, including BitTorrent clients. They attempt to enhance privacy and confidentiality. In addition, they attempt to make traffic harder to identify by third parties including internet service providers (ISPs). However, encryption will not protect one from DMCA notices from sharing not legal content, as one is still uploading material and the monitoring firms can merely connect to the swarm. MSE/PE is implemented in BitComet, BitTornado, Deluge, Flashget, KTorrent, libtorrent (used by various BitTorrent clients, including qBittorrent), Mainline, μTorrent, qBittorrent, rTorrent, Transmission, Tixati and Vuze. PHE was implemented in old versions of BitComet. Similar protocol obfuscation is supported in up-to-date versions of some other (non-BitTorrent) systems including eMule. Purpose As of January 2005, BitTorrent traffic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
JMule
JMule is an open source file sharing client written in Java for eDonkey2000 networks. JMule is released under the terms of the GNU General Public License, it is based on Java platform and requires at least Java SE 6.0 for operation. At a more general level this is a project that try to accomplish several goals. For now the client has Swing and SWT user interfaces, but more user interfaces were to come soon as of 2010. The name "JMule" comes from a "J" (Java) and a "Mule" (like eMule, aMule). Development As of 2010, JMule is under an active development mostly using open source software. The main IDE is Eclipse with AspectJ plugin that runs on Ubuntu Linux. The source code is stored in a public CVS repository provided by SourceForge.net The JMule Team releases nightly build A daily build or nightly build is the practice of completing a software build of the latest version of a program, on a daily basis. This is so it can first be compiled to ensure that all required depe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EDonkey2000
eDonkey2000 (nicknamed "ed2k") was a peer-to-peer file sharing application developed by US company MetaMachine (Jed McCaleb and Sam Yagan), using the Multisource File Transfer Protocol. This client supports both the eDonkey2000 network and the Overnet network. On September 28, 2005, eDonkey was discontinued following a cease and desist letter from the RIAA. eDonkey2000 network Users on the eDonkey2000 network predominantly share large files of tens or hundreds of megabytes, such as CD images, videos, games, and software programs. To ease file searching, some websites list the checksums of sought-after files in the form of an ed2k link. Some of those websites also have lists of active servers for users to update. MetaMachines has also created another file-sharing network called Overnet, which interoperates with the eDonkey network, but without the use of servers. Most eDonkey clients also now use the Overnet network. In 2004, MetaMachines announced it would stop developm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XMule
xMule (short for " X11 Mule") is a discontinued free client for the eDonkey peer-to-peer file sharing network intended to bring it to virtually all the major Unix platforms, with a particular emphasis on Linux. xMule was coded in C++ using wxWidgets and released under GNU General Public License v2. xMule is a fork of lMule, itself a port of eMule. aMule is a fork of xMule. History In January 2003, lMule started as an eMule v0.26d port for Linux. In June 2003, due to differences between the developers and the hijacking of lMule's official website by one contributor, lMule's fork, xMule, was created. Unlike eMule, which uses MFC (Microsoft Foundation Classes), xMule used wxWidgets for the graphical user interface, therefore could run on many platforms. It fully supported Linux and *BSD, and was intended to support Windows and MacOS. On 17 August 2003, Ted R. Smith, xMule's only maintainer who lived in the United States at the time, became involved in a legal bat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows
Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for servers, and Windows IoT for embedded systems. Defunct Windows families include Windows 9x, Windows Mobile, and Windows Phone. The first version of Windows was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). Windows is the most popular desktop operating system in the world, with 75% market share , according to StatCounter. However, Windows is not the most used operating system when including both mobile and desktop OSes, due to Android's massive growth. , the most recent version of Windows is Windows 11 for consumer PCs and tablets, Windows 11 Enterprise for corporations, and Windows Server 2022 for servers. Genealogy By ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kademlia
Kademlia is a distributed hash table for decentralized peer-to-peer computer networks designed by Petar Maymounkov and David Mazières in 2002. It specifies the structure of the network and the exchange of information through node lookups. Kademlia nodes communicate among themselves using UDP. A virtual or overlay network is formed by the participant nodes. Each node is identified by a number or ''node ID''. The ''node ID'' serves not only as identification, but the Kademlia algorithm uses the ''node ID'' to locate values (usually file hashes or keywords). In order to look up the value associated with a given key, the algorithm explores the network in several steps. Each step will find nodes that are closer to the key until the contacted node returns the value or no more closer nodes are found. This is very efficient: like many other s, Kademlia contacts only O(\log n) nodes during the search out of a total of n nodes in the system. Further advantages are found particularly i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kibibyte
The byte is a unit of digital information that most commonly consists of eight bits. Historically, the byte was the number of bits used to encode a single character of text in a computer and for this reason it is the smallest addressable unit of memory in many computer architectures. To disambiguate arbitrarily sized bytes from the common 8-bit definition, network protocol documents such as The Internet Protocol () refer to an 8-bit byte as an octet. Those bits in an octet are usually counted with numbering from 0 to 7 or 7 to 0 depending on the bit endianness. The first bit is number 0, making the eighth bit number 7. The size of the byte has historically been hardware-dependent and no definitive standards existed that mandated the size. Sizes from 1 to 48 bits have been used. The six-bit character code was an often-used implementation in early encoding systems, and computers using six-bit and nine-bit bytes were common in the 1960s. These systems often had memory wor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash List
In computer science, a hash list is typically a list of hashes of the data blocks in a file or set of files. Lists of hashes are used for many different purposes, such as fast table lookup (hash tables) and distributed databases (distributed hash tables). A hash list is an extension of the concept of hashing an item (for instance, a file). A hash list is a subtree of a Merkle tree. Root hash Often, an additional hash of the hash list itself (a ''top hash'', also called ''root hash'' or ''master hash'') is used. Before downloading a file on a p2p network, in most cases the top hash is acquired from a trusted source, for instance a friend or a web site that is known to have good recommendations of files to download. When the top hash is available, the hash list can be received from any non-trusted source, like any peer in the p2p network. Then the received hash list is checked against the trusted top hash, and if the hash list is damaged or fake, another hash list from another ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hash Function
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called ''hash values'', ''hash codes'', ''digests'', or simply ''hashes''. The values are usually used to index a fixed-size table called a ''hash table''. Use of a hash function to index a hash table is called ''hashing'' or ''scatter storage addressing''. Hash functions and their associated hash tables are used in data storage and retrieval applications to access data in a small and nearly constant time per retrieval. They require an amount of storage space only fractionally greater than the total space required for the data or records themselves. Hashing is a computationally and storage space-efficient form of data access that avoids the non-constant access time of ordered and unordered lists and structured trees, and the often exponential storage requirements of direct access of state spaces of large or variable-length keys. Use o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |