|
VoIP Spam
VoIP spam or SPIT (spam over Internet telephony) is unsolicited, automatically dialed telephone calls, typically using voice over Internet Protocol (VoIP) technology. VoIP systems, like e-mail and other Internet applications, are susceptible to abuse by malicious parties who initiate unsolicited and unwanted communications, such as telemarketers and prank callers. VoIP calling rates are cheap, and the technology provides convenient, often free tools, such as Asterisk and other applications. The primary underlying technology driving this threat is the Session Initiation Protocol (SIP), which is a standard for VoIP telecommunications. Various techniques have been devised to detect spam calls; some take effect even before the recipient has answered a call to disconnect it. These techniques rely on statistical analysis of the features of the call, such as the originating IP address, or features of the signalling and media messages. Character VoIP spam is characterized as unsolici ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spamming
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, non-commercial proselytizing, or any prohibited purpose (especially phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have no operating costs beyond the management of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Caller ID Spoofing
Caller ID spoofing is a spoofing attack which causes the telephone network's Caller ID to indicate to the receiver of a call that the originator of the call is a station other than the true originating station. This can lead to a display showing a phone number different from that of the telephone from which the call was placed. The term is commonly used to describe situations in which the motivation is considered malicious by the originator. One effect of the widespread availability of Caller ID spoofing is that, as AARP published in 2019, "you can no longer trust call ID." History Caller ID spoofing has been available for years to people with a specialized digital connection to the telephone company, called an ISDN PRI circuit. Collection agencies, law-enforcement officials, and private investigators have used the practice, with varying degrees of legality. The first mainstream caller ID spoofing service was launched U.S.-wide on September 1, 2004 by California-based Star38 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IOS 10
iOS 10 is the iOS version history, tenth major release of the iOS mobile operating system developed by Apple Inc., being the successor to iOS 9. It was announced at the company's Worldwide Developers Conference on June 13, 2016, and was released on September 13, 2016. It was succeeded by iOS 11 on September 19, 2017. iOS 10 incorporates changes to 3D Touch and the lock screen. There are new features to some apps: Messages (Apple), Messages has additional emojis and third-party apps can extend functionality in iMessage, Apple Maps, Maps has a redesigned interface and additional third-party functions, the Home app manages "HomeKit"-enabled accessories, Photos (Apple), Photos has algorithmic search and categorization of media known as "Memories", and Siri is compatible with third-party app-specific requests, such as starting workouts apps, sending instant messaging, IMs, using Lyft or Uber or to use payment functions. In iOS 10.3, Apple introduced its new file system, APFS. Review ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Apple Inc
Apple Inc. is an American multinational corporation and technology company headquartered in Cupertino, California, in Silicon Valley. It is best known for its consumer electronics, software, and services. Founded in 1976 as Apple Computer Company by Steve Jobs, Steve Wozniak and Ronald Wayne, the company was incorporated by Jobs and Wozniak as Apple Computer, Inc. the following year. It was renamed Apple Inc. in 2007 as the company had expanded its focus from computers to consumer electronics. Apple is the largest technology company by revenue, with billion in the 2024 fiscal year. The company was founded to produce and market Wozniak's Apple I personal computer. Its second computer, the Apple II, became a best seller as one of the first mass-produced microcomputers. Apple introduced the Lisa in 1983 and the Macintosh in 1984, as some of the first computers to use a graphical user interface and a mouse. By 1985, internal company problems led to Jobs leavin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Android (operating System)
Android is an operating system based on a modified version of the Linux kernel and other open-source software, open-source software, designed primarily for touchscreen-based mobile devices such as smartphones and tablet computer, tablets. Android has historically been developed by a consortium of developers known as the Open Handset Alliance, but its most widely used version is primarily developed by Google. First released in 2008, Android is the world's Usage share of operating systems, most widely used operating system; the latest version, released on June 10, 2025, is Android 16. At its core, the operating system is known as the Android Open Source Project (AOSP) and is free and open-source software (FOSS) primarily licensed under the Apache License. However, most devices run the proprietary software, proprietary Android version developed by Google, which ships with additional proprietary closed-source software pre-installed, most notably Google Mobile Services (GMS), which ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google Nexus
Google Nexus is a discontinued line of consumer electronic mobile devices that ran a stock version of the Android (operating system), Android operating system. Google managed the design, development, marketing, and support of these devices, but some development and all manufacturing were carried out by partnering with original equipment manufacturers (OEMs). Alongside the main smartphone products, the line also included tablet computers and streaming media players; the Nexus started out in January 2010 and reached its end in October 2016, replaced by Google Pixel family. Devices in the Nexus line were considered Google's Core product, core Android products. They contained little to no manufacturer or wireless carrier modifications to Android (such as custom touch user interface, user interfaces), although devices sold through carriers may be SIM locked, had some extra branding, and may have received software updates at a slower pace than the unlocked variant. Save for some carr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Google
Google LLC (, ) is an American multinational corporation and technology company focusing on online advertising, search engine technology, cloud computing, computer software, quantum computing, e-commerce, consumer electronics, and artificial intelligence (AI). It has been referred to as "the most powerful company in the world" by the BBC and is one of the world's List of most valuable brands, most valuable brands. Google's parent company, Alphabet Inc., is one of the five Big Tech companies alongside Amazon (company), Amazon, Apple Inc., Apple, Meta Platforms, Meta, and Microsoft. Google was founded on September 4, 1998, by American computer scientists Larry Page and Sergey Brin. Together, they own about 14% of its publicly listed shares and control 56% of its stockholder voting power through super-voting stock. The company went public company, public via an initial public offering (IPO) in 2004. In 2015, Google was reorganized as a wholly owned subsidiary of Alphabet Inc. Go ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telephone Company
A telecommunications company is a kind of electronic communications service provider, more precisely a telecommunications service provider (TSP), that provides telecommunications services such as telephony and data communications access. Many traditional solely telephone companies now function as internet service providers (ISPs), and the distinction between a telephone company and ISP has tended to disappear completely over time, as the current trend for supplier convergence in the industry develops. Additionally, with advances in technology development, other traditional separate industries such as cable television, Voice-over IP (VoIP), and satellite providers offer similar competing features as the telephone companies to both residential and businesses leading to further evolution of corporate identity have taken shape. Due to the nature of capital expenditure involved in the past, most telecommunications companies were government owned agencies or privately-owned mono ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Perceptual Hashing
Perceptual hashing is the use of a fingerprinting algorithm that produces a snippet, hash, or fingerprint of various forms of multimedia. A perceptual hash is a type of locality-sensitive hash, which is analogous if features of the multimedia are similar. This is in contrast to cryptographic hashing, which relies on the avalanche effect of a small change in input value creating a drastic change in output value. Perceptual hash functions are widely used in finding cases of online copyright infringement as well as in digital forensics because of the ability to have a correlation between hashes so similar data can be found (for instance with a differing watermark). Development The 1980 work of Marr and Hildreth is a seminal paper in this field. In 2009, Microsoft Corporation developed PhotoDNA in collaboration with Hany Farid, professor at Dartmouth College. PhotoDNA is a perceptual hashing capability developed to combat the distribution of child sexual abuse material (CSAM ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Acoustic Fingerprint
An acoustic fingerprint is a condensed digital summary, a digital fingerprint, deterministically generated from an audio signal, that can be used to identify an audio sample or quickly locate similar items in a music database. Practical uses of acoustic fingerprinting include identifying songs, melodies, tunes, or advertisements; sound effect library management; and video file identification. Media identification using acoustic fingerprints can be used to monitor the use of specific musical works and performances on radio broadcast, records, CDs, streaming media, and peer-to-peer networks. This identification has been used in copyright compliance, licensing, and other monetization schemes. Attributes A robust acoustic fingerprint algorithm must take into account the perceptual characteristics of the audio. If two files sound alike to the human ear, their acoustic fingerprints should match, even if their binary representations are quite different. Acoustic fingerpr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
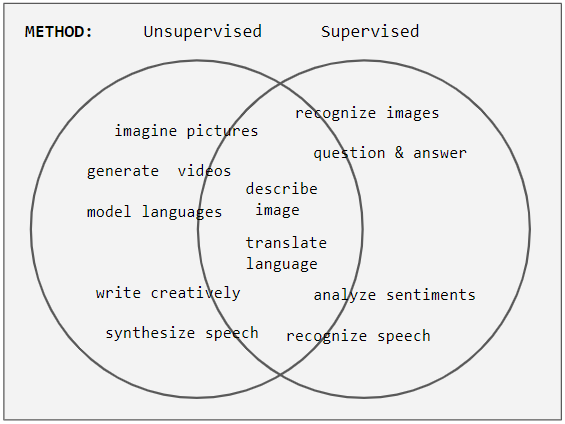
Semi-supervised Learning
Weak supervision (also known as semi-supervised learning) is a paradigm in machine learning, the relevance and notability of which increased with the advent of large language models due to large amount of data required to train them. It is characterized by using a combination of a small amount of human-labeled data (exclusively used in more expensive and time-consuming supervised learning paradigm), followed by a large amount of unlabeled data (used exclusively in unsupervised learning paradigm). In other words, the desired output values are provided only for a subset of the training data. The remaining data is unlabeled or imprecisely labeled. Intuitively, it can be seen as an exam and labeled data as sample problems that the teacher solves for the class as an aid in solving another set of problems. In the Transduction (machine learning), transductive setting, these unsolved problems act as exam questions. In the Inductive reasoning, inductive setting, they become practice problems ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |