|
Surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing, or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. Increasingly, Government, governments may also obtain Customer data, consumer data through the purchase of online information, effectively expanding surveillance capabilities through commercially available digital records. It can also include simple technical methods, such as Human intelligence (intelligence gathering), human intelligence gathering and postal interception. Surveillance is used by citizens, for instance for protecting their neighborhoods. It is widely used by governments for intelligence gathering, including espionage, prevention of crime, the protection of a process, person, group or object, or the investigat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Surveillance Video Cameras, Gdynia
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing, or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. Increasingly, governments may also obtain consumer data through the purchase of online information, effectively expanding surveillance capabilities through commercially available digital records. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens, for instance for protecting their neighborhoods. It is widely used by governments for intelligence gathering, including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Closed-circuit Television
Closed-circuit television (CCTV), also known as video surveillance, is the use of closed-circuit television cameras to transmit a signal to a specific place on a limited set of monitors. It differs from broadcast television in that the signal is not openly transmitted, though it may employ point-to-point, point-to-multipoint (P2MP), or mesh wired or wireless links. Even though almost all video cameras fit this definition, the term is most often applied to those used for surveillance in areas that require additional security or ongoing monitoring ( videotelephony is seldom called "CCTV"). The deployment of this technology has facilitated significant growth in state surveillance, a substantial rise in the methods of advanced social monitoring and control, and a host of crime prevention measures throughout the world. Though surveillance of the public using CCTV is common in many areas around the world, video surveillance has generated significant debate about balancing its us ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Carnivore (FBI)
Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation (FBI) that was designed to monitor email and electronic communications. It used a customizable packet sniffer that could monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software. Development Carnivore grew out of an earlier FBI project called "Omnivore", which itself replaced an older undisclosed (at the time) surveillance tool migrated at the US Navy by FBI Director of Integrity and Compliance, Patrick W. Kelley. In September 2000, the FBI's Data Intercept Technology Unit (DITU) in Quantico, Virginia, launched a project to migrate Omnivore from Sun's Solaris operating system to a Windows NT platform. This was done to facilitate the miniaturization of the system and support a wider range of personal computer (CPU) equipment. The migration project was called "Triple Phoenix" and the re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Privacy
Privacy (, ) is the ability of an individual or group to seclude themselves or information about themselves, and thereby express themselves selectively. The domain of privacy partially overlaps with security, which can include the concepts of appropriate use and Information security, protection of information. Privacy may also take the form of bodily integrity. Throughout history, there have been various conceptions of privacy. Most cultures acknowledge the right of individuals to keep aspects of their personal lives out of the public domain. The right to be free from unauthorized invasions of privacy by governments, corporations, or individuals is enshrined in the privacy laws of many countries and, in some instances, their constitutions. With the rise of technology, the debate regarding privacy has expanded from a bodily sense to include a digital sense. In most countries, the right to digital privacy is considered an extension of the original right to privacy, and many count ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Espionage
Espionage, spying, or intelligence gathering, as a subfield of the intelligence field, is the act of obtaining secret or confidential information ( intelligence). A person who commits espionage on a mission-specific contract is called an ''espionage agent'' or ''spy''. A person who commits espionage as a fully employed officer of a government is called an intelligence officer. Any individual or spy ring (a cooperating group of spies), in the service of a government, company, criminal organization, or independent operation, can commit espionage. The practice is clandestine, as it is by definition unwelcome. In some circumstances, it may be a legal tool of law enforcement and in others, it may be illegal and punishable by law. Espionage is often part of an institutional effort by a government or commercial concern. However, the term tends to be associated with state spying on potential or actual enemies for military purposes. Spying involving corporations is known as c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
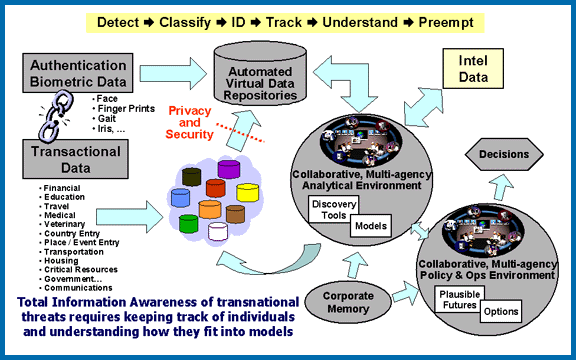
Information Awareness Office
The Information Awareness Office (IAO) was established by the United States Defense Advanced Research Projects Agency (DARPA) in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric warfare, asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). It was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States, including personal e-mails, social networks, credit card records, phone calls, medical records, and numerous other sources, without any requirement for a search warrant. The information was then analyzed for suspicious activities, connections between individuals, and "threats".Total Information Aware ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Internet
The Internet (or internet) is the Global network, global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a internetworking, network of networks that consists of Private network, private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, Wireless network, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, streaming media and file sharing. The origins of the Internet date back to research that enabled the time-sharing of computer resources, the development of packet switching in the 1960s and the design of computer networks for data communication. The set of rules (communication protocols) to enable i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Data Mining
Data mining is the process of extracting and finding patterns in massive data sets involving methods at the intersection of machine learning, statistics, and database systems. Data mining is an interdisciplinary subfield of computer science and statistics with an overall goal of extracting information (with intelligent methods) from a data set and transforming the information into a comprehensible structure for further use. Data mining is the analysis step of the " knowledge discovery in databases" process, or KDD. Aside from the raw analysis step, it also involves database and data management aspects, data pre-processing, model and inference considerations, interestingness metrics, complexity considerations, post-processing of discovered structures, visualization, and online updating. The term "data mining" is a misnomer because the goal is the extraction of patterns and knowledge from large amounts of data, not the extraction (''mining'') of data itself. It also is a buzzwo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Postal Interception
Postal interception is the act of retrieving another person's mail for the purpose of either ensuring that the mail is not delivered to the recipient, or to spy on them. For instance, the American Central Intelligence Agency (CIA) and Federal Bureau of Investigation (FBI) were involved in numerous large-scale operations targeting US activist groups, whose mail was opened and photographed. In one such programme, over 215,000 letters were opened. In the United Kingdom, the Special Investigations Unit of the General Post Office was responsible for postal interception. Since 2002, the United States Postal Service photographs the outside of all mail, retains those images for weeks or months, and provides them to police or other investigators upon a simple request. See also * COINTELPRO * Surveillance * Church committee * Black room * Postal censorship Postal censorship is the inspection or examination of mail, most often by governments. It can include opening, reading and total ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Authoritarian
Authoritarianism is a political system characterized by the rejection of political plurality, the use of strong central power to preserve the political ''status quo'', and reductions in democracy, separation of powers, civil liberties, and the rule of law. Authoritarian regimes may be either autocratic or oligarchic and may be based upon the rule of a party or the military. States that have a blurred boundary between democracy and authoritarianism have sometimes been characterized as "hybrid democracies", " hybrid regimes" or "competitive authoritarian" states. The political scientist Juan Linz, in an influential 1964 work, ''An Authoritarian Regime: Spain'', defined authoritarianism as possessing four qualities: # Limited political pluralism, which is achieved with constraints on the legislature, political parties and interest groups. # Political legitimacy based on appeals to emotion and identification of the regime as a necessary evil to combat "easily recognizable ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |