|
Strong Customer Authentication
Strong customer authentication (SCA) is a requirement of the EU Revised Directive on Payment Services (PSD2) on payment service providers within the European Economic Area. The requirement ensures that electronic payments are performed with multi-factor authentication, to increase the security of electronic payments. Physical card transactions already commonly have what could be termed strong customer authentication in the EU ( Chip and PIN), but this has not generally been true for Internet transactions across the EU prior to the implementation of the requirement, and many contactless card payments do not use a second authentication factor. The SCA requirement came into force on 14 September 2019. However, with the approval of the European Banking Authority, several EEA countries have announced that their implementation will be temporarily delayed or phased, with a final deadline set for 31 December 2020. Requirement Article 97(1) of the directive requires that payment servi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Payment Services Directive
The Revised Payment Services Directive (PSD2, Directive (EU) 2015/2366, which replaced the Payment Services Directive (PSD), Directive 2007/64/EC) is an EU Directive, administered by the European Commission (Directorate General Internal Market) to regulate payment services and payment service providers throughout the European Union (EU) and European Economic Area (EEA). The PSD's purpose was to increase pan-European competition and participation in the payments industry also from non-banks, and to provide for a level playing field by harmonizing consumer protection and the rights and obligations of payment providers and users. The key objectives of the PSD2 directive are creating a more integrated European payments market, making payments more secure and protecting consumers. Overview The SEPA (Single Euro Payments Area) is a self-regulatory initiative by the European banking sector represented in the European Payments Council, which defines the harmonization of payment products, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reliance Authentication
Reliance authentication is a part of the trust-based identity attribution process whereby a second entity relies upon the Digital identity#Authentication, authentication processes put in place by a first entity. The second entity creates a further element that is unique and specific to its purpose, that can only be retrieved or accessed by the authentication processes of the first entity having first being met. Reliance authentication can be achieved by one or more tokens with random characteristics being transmitted to a secure area controlled by the first entity, where such secure area is only accessible by the person authorised to use the account. The secure area may be an online banking portal, telephone banking system, or mobile banking application. The token is often in the form of a single or plural of debit or credits to a financial account, where the numerical values of the debit or credits form the token, whose numeric value is to be confirmed by the account holder. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Payment Systems
A payment system is any system used to settle financial transactions through the transfer of monetary value. This includes the institutions, payment instruments such as payment cards, people, rules, procedures, standards, and technologies that make its exchange possible.Biago Bossone and Massimo Cirasino, "The Oversight of the Payment Systems: A Framework for the Development and Governance of Payment Systems in Emerging Economies"The World Bank, July 2001, p.7 A payment system is an operational network which links bank accounts and provides for monetary exchange using bank deposits. Some payment systems also include credit mechanisms, which are essentially a different aspect of payment. Payment systems are used in lieu of tendering cash in domestic and international transactions. This consists of a major service provided by banks and other financial institutions. Traditional payment systems include negotiable instruments such as drafts (e.g., cheques) and documentary credits such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
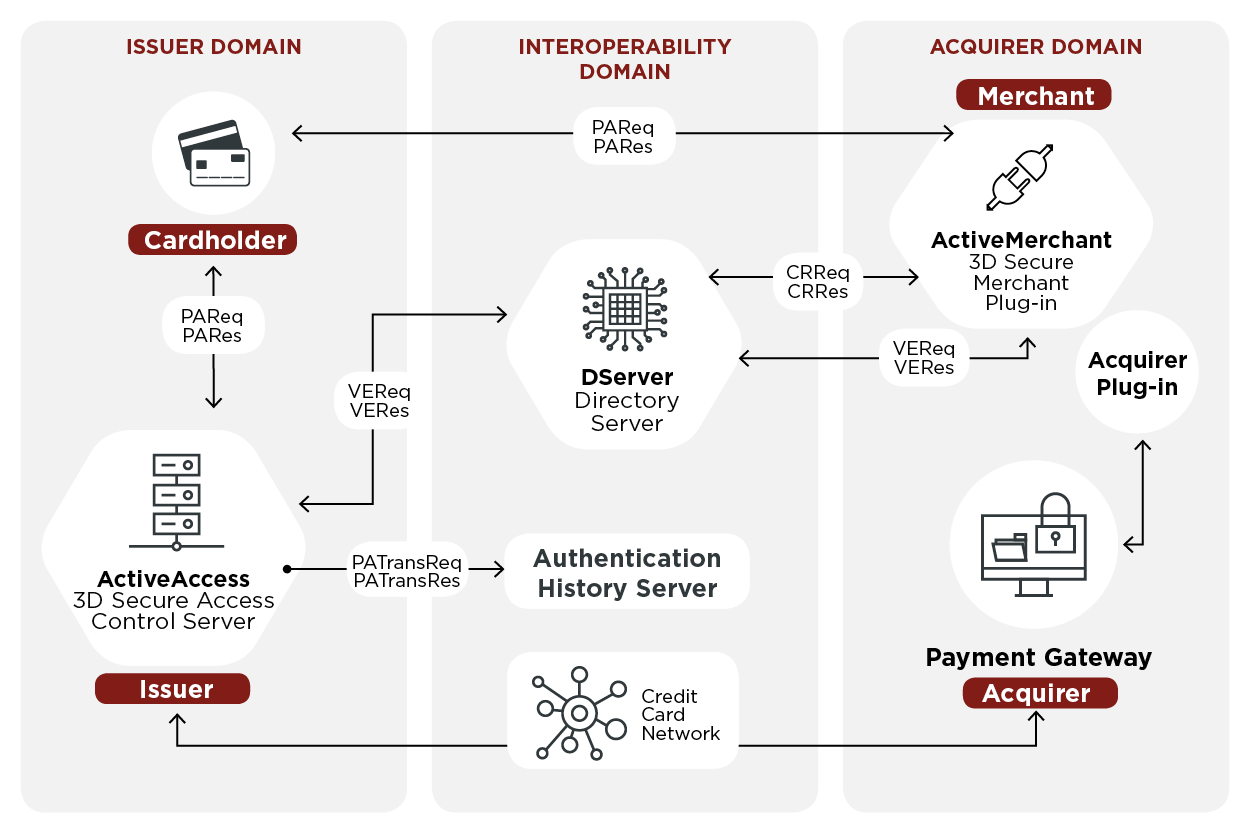
3D Secure
3-D Secure is a protocol designed to be an additional security layer for online credit and debit card transactions. The name refers to the "three domains" which interact using the protocol: the merchant/acquirer domain, the issuer domain, and the interoperability domain. Originally developed in the autumn of 1999 by Celo Communications AB (which was acquired by Gemplus Associates and integrated into Gemplus, Gemalto and now Thales Group) for Visa Inc. in a project named "p42" ("p" from Pole vault as the project was a big challenge and "42" as the answer from the book ''The Hitchhiker's Guide to the Galaxy''). A new updated version was developed by Gemplus between 2000-2001. In 2001 Arcot Systems (now CA Technologies) and Visa Inc. with the intention of improving the security of Internet payments, and offered to customers under the Verified by Visa brand (later rebranded as Visa Secure). Services based on the protocol have also been adopted by Mastercard as SecureCode (later reb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Australian Competition & Consumer Commission
The Australian Competition and Consumer Commission (ACCC) is the chief competition regulator of the Government of Australia, located within the Department of the Treasury. It was established in 1995 with the amalgamation of the Australian Trade Practices Commission and the Prices Surveillance Authority to administer the '' Trade Practices Act 1974'', which was replaced by the ''Competition and Consumer Act 2010'' on 1 January 2011. The ACCC's mandate is to protect consumer rights and business rights and obligations, to perform industry regulation and price monitoring, and to prevent illegal anti-competitive behaviour. Historical origins The ACCC's deeper origins are found in the Restrictive Trade Practices Act of Sir Garfield Barwick, Attorney-General in the Liberal Government of Sir Robert Menzies in 1965.Hocking, Jenny, ''Lionel Murphy: a political biography'', Cambridge University Press, Cambridge, UK, 2000 . p.204 Opponents derided Barwick's Trade Practices Act 1965 as " ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reserve Bank Of India
Reserve Bank of India, abbreviated as RBI, is the central bank of the Republic of India, and regulatory body responsible for regulation of the Indian banking system and Indian rupee, Indian currency. Owned by the Ministry of Finance (India), Ministry of Finance, Government of India, Government of the Republic of India, it is responsible for the control, issue, and maintenance of the supply of the Indian rupee. It also manages the country's main payment systems and works to promote its economic development. The RBI, along with the Indian Banks' Association, established the National Payments Corporation of India to promote and regulate the payment and settlement systems in India. Bharatiya Reserve Bank Note Mudran, Bharatiya Reserve Bank Note Mudran (BRBNM) is a specialised division of RBI through which it prints and mints Indian currency notes (INR) in two of its currency printing presses located in Mysore (Karnataka; Southern India) and Salboni (West Bengal; Eastern India). Depos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Push Notification
Push technology, also known as server Push, refers to a communication method, where the communication is initiated by a server rather than a client. This approach is different from the "pull" method where the communication is initiated by a client. In push technology, clients can express their preferences for certain types of information or data, typically through a process known as the publish–subscribe model. In this model, a client "subscribes" to specific information channels hosted by a server. When new content becomes available on these channels, the server automatically sends, or "pushes," this information to the subscribed client. Under certain conditions, such as restrictive security policies that block incoming HTTP requests, push technology is sometimes simulated using a technique called polling. In these cases, the client periodically checks with the server to see if new information is available, rather than receiving automatic updates. General use Synchronous c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SMS Message
Short Message Service, commonly abbreviated as SMS, is a text messaging service component of most telephone, Internet and mobile device systems. It uses standardized communication protocols that let mobile phones exchange short text messages, typically transmitted over cellular networks. Developed as part of the GSM standards, and based on the SS7 signalling protocol, SMS rolled out on digital cellular networks starting in 1993 and was originally intended for customers to receive alerts from their carrier/operator. The service allows users to send and receive text messages of up to 160 characters, originally to and from GSM phones and later also CDMA and Digital AMPS; it has since been defined and supported on newer networks, including present-day 5G ones. Using SMS gateways, messages can be transmitted over the Internet through an SMSC, allowing communication to computers, fixed landlines, and satellite. MMS was later introduced as an upgrade to SMS with "picture messaging" ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Which?
''Which?'' is a United Kingdom brand name that promotes informed consumer choice in the purchase of goods and services by testing products, highlighting inferior products or services, raising awareness of consumer rights, and offering independent advice. The brand name is used by the Consumers' Association, a registered charity and company limited by guarantee that owns several businesses, including Which? Limited, which publishes the ''Which?'' magazines, and the currently dormant Which? Financial Services Limited (''Which?'' Mortgage and Insurance Advisers operated until 2019) and Which? Legal Limited. The vast majority of the association's income comes from the profit it makes on its trading businesses, for instance subscriptions to ''Which?'' magazine, which are donated to the campaigning part of the organisation to fund advocacy activity and inform the public about consumer issues. ''Which?'' magazine maintains its independence by not accepting advertising, and the organ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Register
''The Register'' (often also called El Reg) is a British Technology journalism, technology news website co-founded in 1994 by Mike Magee (journalist), Mike Magee and John Lettice. The online newspaper's Nameplate_(publishing), masthead Logo, sublogo is "''Biting the hand that feeds IT''." The publication's primary focus is information technology news and opinions. Situation Publishing Ltd is the site's publisher. Drew Cullen is an owner and Linus Birtles is the managing director. Andrew Orlowski was the executive editor before leaving the website in May 2019. History ''The Register'' was founded in London as an email newsletter called ''Chip Connection''. In 1998 ''The Register'' became a daily online news source. Magee left in 2001 to start competing publications ''The Inquirer'', and later the ''IT Examiner'' and ''TechEye''. In 2002, ''The Register'' expanded to have a presence in London and San Francisco, creating ''The Register USA'' at theregus.com through a joint ventu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Payment
An e-commerce payment system (or an electronic payment system) facilitates the acceptance of electronic payment for offline transfer, also known as a subcomponent of electronic data interchange (EDI), e-commerce payment systems have become increasingly popular due to the widespread use of the internet-based shopping and banking. Credit cards remain the most common form of payment for e-commerce transactions. As of 2008, in North America, almost 90% of online retail transactions were made with this payment type.Turban, E. King, D. McKay, J. Marshall, P. Lee, J & Vielhand, D. (2008). Electronic Commerce 2008: A Managerial Perspective. London: Pearson Education Ltd. p.550 It is difficult for an online retailer to operate without supporting credit and debit cards due to their widespread use. Online merchants must comply with stringent rules stipulated by the credit and debit card issuers (e.g. Visa and Mastercard) in accordance with a bank and financial regulation in the countries ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
One-time Password
A one-time password (OTP), also known as a one-time PIN, one-time passcode, one-time authorization code (OTAC) or dynamic password, is a password that is valid for only one login session or transaction, on a computer system or other digital device. OTPs avoid several shortcomings that are associated with traditional (static) password-based authentication; a number of implementations also incorporate two-factor authentication by ensuring that the one-time password requires access to ''something a person has'' (such as a small keyring fob device with the OTP calculator built into it, or a smartcard or specific cellphone) as well as ''something a person knows'' (such as a PIN). OTP generation algorithms typically make use of pseudorandomness or randomness to generate a shared key or seed, and cryptographic hash functions, which can be used to derive a value but are hard to reverse and therefore difficult for an attacker to obtain the data that was used for the hash. This is necessa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |