|
Replication (computer Science)
Replication in computing refers to maintaining multiple copies of data, processes, or resources to ensure consistency across redundant components. This fundamental technique spans database management system, databases, file system, file systems, and distributed computing, distributed systems, serving to improve high availability, availability, fault-tolerance, accessibility, and performance. Through replication, systems can continue operating when components fail (failover), serve requests from geographically distributed locations, and balance load across multiple machines. The challenge lies in maintaining consistency between replicas while managing the fundamental tradeoffs between data consistency, system availability, and Network partition, network partition tolerance – constraints known as the CAP theorem. Terminology Replication in computing can refer to: * ''Data replication'', where the same data is stored on multiple data storage device, storage devices * ''Computation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computer, computing machinery. It includes the study and experimentation of algorithmic processes, and the development of both computer hardware, hardware and software. Computing has scientific, engineering, mathematical, technological, and social aspects. Major computing disciplines include computer engineering, computer science, cybersecurity, data science, information systems, information technology, and software engineering. The term ''computing'' is also synonymous with counting and calculation, calculating. In earlier times, it was used in reference to the action performed by Mechanical computer, mechanical computing machines, and before that, to Computer (occupation), human computers. History The history of computing is longer than the history of computing hardware and includes the history of methods intended for pen and paper (or for chalk and slate) with or without the aid of tables. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Lock Manager
A distributed lock manager (DLM) runs in every machine in a cluster, with an identical copy of a cluster-wide lock database. Operating systems use lock managers to organise and serialise the access to resources. In this way a DLM provides software applications which are distributed across a cluster on multiple machines with a means to synchronize their accesses to shared resources. DLMs have been used as the foundation for several successful clustered file systems, in which the machines in a cluster can use each other's storage via a unified file system, with significant advantages for performance and availability. The main performance benefit comes from solving the problem of disk cache coherency between participating computers. The DLM is used not only for file locking but also for coordination of all disk access. VMScluster, the first clustering system to come into widespread use, relied on the OpenVMS DLM in just this way. Resources The DLM uses a generalized concept ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Synchrony
Reliable multicast is any computer networking protocol that provides a '' reliable'' sequence of packets to multiple recipients simultaneously, making it suitable for applications such as multi-receiver file transfer. Overview Multicast is a network addressing method for the delivery of information to a group of destinations simultaneously using the most efficient strategy to deliver the messages over each link of the network only once, creating copies only when the links to the multiple destinations split (typically network switches and routers). However, like the User Datagram Protocol, multicast does not guarantee the delivery of a message stream. Messages may be dropped, delivered multiple times, or delivered out of order. A reliable multicast protocol adds the ability for receivers to detect lost and/or out-of-order messages and take corrective action (similar in principle to TCP), resulting in a gap-free, in-order message stream. Reliability The exact meaning of ''r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keyspace (data Store)
A keyspace (or key space) in a NoSQL data store is an object that holds together all column families of a design. It is the outermost grouping of the data in the data store. It resembles the schema concept in Relational database management systems. Generally, there is one keyspace per application. Structure A keyspace may contain column families or super columns. Each super column contains one or more column families, and each column family contains at least one column. The keyspace is the highest abstraction in a distributed data store. This is fundamental in preserving the structural heuristics in dynamic data retrieval. Multiple relay protocol algorithms are integrated within the simple framework. Comparison with relational database systems The keyspace has similar importance like a schema has in a database. In contrast to the schema, however, it does not stipulate any concrete structure, like it is known in the entity–relationship model used widely in the relational da ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Paxos Algorithm
Paxos is a family of protocols for solving Consensus (computer science), consensus in a network of unreliable or fallible processors. Consensus is the process of agreeing on one result among a group of participants. This problem becomes difficult when the participants or their communications may experience failures. Consensus protocols are the basis for the state machine replication approach to distributed computing, as suggested by Leslie Lamport and surveyed by Fred B. Schneider, Fred Schneider. State machine replication is a technique for converting an algorithm into a fault-tolerant, distributed implementation. Ad-hoc techniques may leave important cases of failures unresolved. The principled approach proposed by Lamport et al. ensures all cases are handled safely. The Paxos protocol was first submitted in 1989 and named after a fictional legislative consensus system used on the Paxi, Paxos island in Greece, where Lamport wrote that the parliament had to function "even thou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Consensus (computer Science)
A fundamental problem in distributed computing and multi-agent systems is to achieve overall system reliability in the presence of a number of faulty processes. This often requires coordinating processes to reach consensus, or agree on some data value that is needed during computation. Example applications of consensus include agreeing on what transactions to commit to a database in which order, state machine replication, and atomic broadcasts. Real-world applications often requiring consensus include cloud computing, clock synchronization, PageRank, opinion formation, smart power grids, state estimation, control of UAVs (and multiple robots/agents in general), load balancing, blockchain, and others. Problem description The consensus problem requires agreement among a number of processes (or agents) on a single data value. Some of the processes (agents) may fail or be unreliable in other ways, so consensus protocols must be fault-tolerant or resilient. The processes must p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Atomic Broadcast
In fault-tolerant distributed computing, an atomic broadcast or total order broadcast is a broadcast where all correct processes in a system of multiple processes receive the same set of messages in the same order; that is, the same sequence of messages. The broadcast is termed " atomic" because it either eventually completes correctly at all participants, or all participants abort without side effects. Atomic broadcasts are an important distributed computing primitive. Properties The following properties are usually required from an atomic broadcast protocol: # Validity: if a correct participant broadcasts a message, then all correct participants will eventually receive it. # Uniform Agreement: if one correct participant receives a message, then all correct participants will eventually receive that message. # Uniform Integrity: a message is received by each participant at most once, and only if it was previously broadcast. # Uniform Total Order: the messages are totally order ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deterministic Finite Automaton
In the theory of computation, a branch of theoretical computer science, a deterministic finite automaton (DFA)—also known as deterministic finite acceptor (DFA), deterministic finite-state machine (DFSM), or deterministic finite-state automaton (DFSA)—is a finite-state machine that accepts or rejects a given string of symbols, by running through a state sequence uniquely determined by the string. ''Deterministic'' refers to the uniqueness of the computation run. In search of the simplest models to capture finite-state machines, Warren McCulloch and Walter Pitts were among the first researchers to introduce a concept similar to finite automata in 1943. The figure illustrates a deterministic finite automaton using a state diagram. In this example automaton, there are three states: S0, S1, and S2 (denoted graphically by circles). The automaton takes a finite sequence of 0s and 1s as input. For each state, there is a transition arrow leading out to a next state for both 0 an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
State Machine Replication
In computer science, state machine replication (SMR) or state machine approach is a general method for implementing a fault-tolerant service by replicating servers and coordinating client interactions with server replicas. The approach also provides a framework for understanding and designing replication management protocols. Problem definition Distributed service In terms of clients and services, each service comprises one or more servers and exports operations that clients invoke by making requests. Although using a single, centralized server is the simplest way to implement a service, the resulting service can only be as fault tolerant as the processor executing that server. If this level of fault tolerance is unacceptable, then multiple servers that fail independently can be used. Usually, replicas of a single server are executed on separate processors of a distributed system, and protocols are used to coordinate client interactions with these replicas. State machine For the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ACID
An acid is a molecule or ion capable of either donating a proton (i.e. Hydron, hydrogen cation, H+), known as a Brønsted–Lowry acid–base theory, Brønsted–Lowry acid, or forming a covalent bond with an electron pair, known as a Lewis acid. The first category of acids are the proton donors, or Brønsted–Lowry acid–base theory, Brønsted–Lowry acids. In the special case of aqueous solutions, proton donors form the hydronium ion H3O+ and are known as Acid–base reaction#Arrhenius theory, Arrhenius acids. Johannes Nicolaus Brønsted, Brønsted and Martin Lowry, Lowry generalized the Arrhenius theory to include non-aqueous solvents. A Brønsted–Lowry or Arrhenius acid usually contains a hydrogen atom bonded to a chemical structure that is still energetically favorable after loss of H+. Aqueous Arrhenius acids have characteristic properties that provide a practical description of an acid. Acids form aqueous solutions with a sour taste, can turn blue litmus red, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
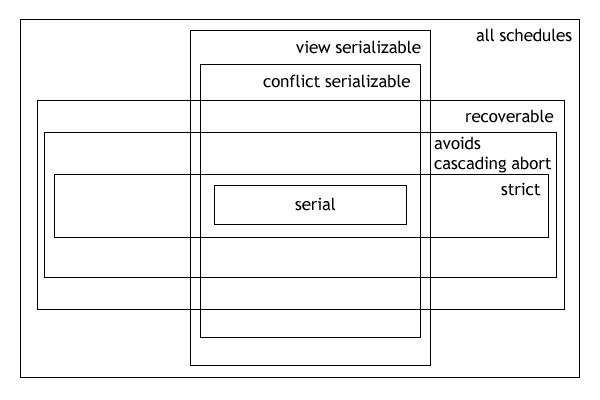
One-copy Serializability
In the fields of databases and transaction processing (transaction management), a schedule (or history) of a system is an abstract model to describe the order of executions in a set of transactions running in the system. Often it is a ''list'' of operations (actions) ordered by time, performed by a set of transactions that are executed together in the system. If the order in time between certain operations is not determined by the system, then a ''partial order'' is used. Examples of such operations are requesting a read operation, reading, writing, aborting, committing, requesting a lock, locking, etc. Often, only a subset of the transaction operation types are included in a schedule. Schedules are fundamental concepts in database concurrency control theory. In practice, most general purpose database systems employ conflict-serializable and strict recoverable schedules. Notation Grid notation: * Columns: The different transactions in the schedule. * Rows: The time order of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transactional Data
In data management, dynamic data or transactional data is information that is periodically updated, meaning it changes asynchronously over time as new information becomes available. The concept is important in data management, since the time scale of the data determines how it is processed and stored. Data that is not dynamic is considered either static (unchanging) or persistent, which is data that is infrequently accessed and not likely to be modified. Dynamic data is also different from streaming data, which is a constant flow of information. Dynamic data may be updated at any time, with periods of inactivity in between. Examples In enterprise data management, dynamic data is likely to be transactional, but it is not limited to financial or business transactions. It may also include engineering transactions, such as a revised schematic diagram A schematic, or schematic diagram, is a designed representation of the elements of a system using abstract, graphic symbols ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |