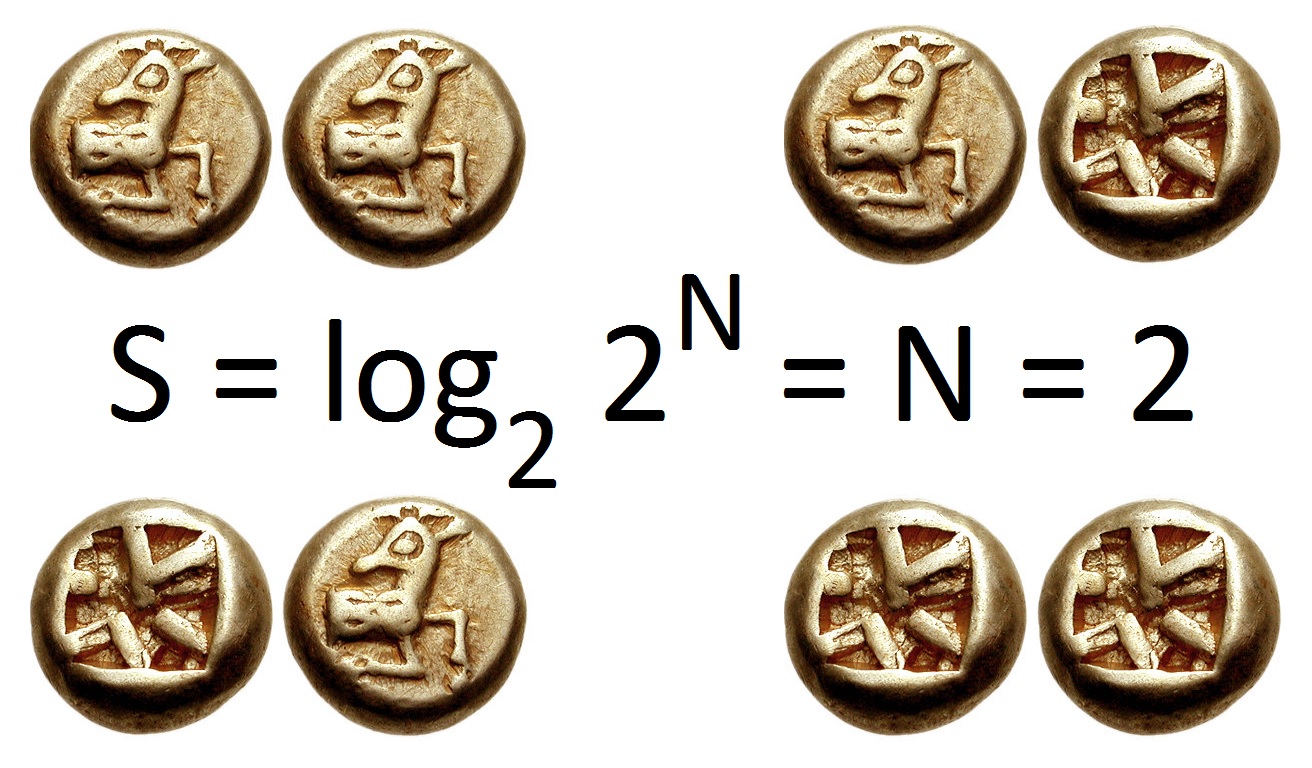|
Password Strength
Password strength is a measure of the effectiveness of a password against guessing or brute-force attacks. In its usual form, it estimates how many trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. The strength of a password is a function of length, complexity, and unpredictability. Using strong passwords lowers the overall risk of a security breach, but strong passwords do not replace the need for other effective security controls. The effectiveness of a password of a given strength is strongly determined by the design and implementation of the authentication factors (knowledge, ownership, inherence). The first factor is the main focus of this article. The rate at which an attacker can submit guessed passwords to the system is a key factor in determining system security. Some systems impose a time-out of several seconds after a small number (e.g. three) of failed password entry attempts. In the absence of other vul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitwarden Desktop 2024
Bitwarden is a freemium open-source software, open-source Password manager, password management service that is used to store sensitive information, such as website credentials, in an Encryption, encrypted vault. Functionalities Bitwarden uses zero-knowledge encryption, meaning the company cannot see its users' data. This is achieved by End-to-end encryption, end-to-end encrypting data with AES-CBC 256-bit and by using PBKDF2 SHA-2, SHA-256/Argon2id to derive the encryption key. To Login, log in, a user can use an email-address and password combination, biometric authentication, two-factor authentication (2FA), Passkey (authentication), passkey, single sign-on, or passwordless login via notification approval on a mobile/desktop device. Additional client functionality includes: import of data from more than 50 password managers (such as LastPass, 1Password, and Keeper (password manager), Keeper) passkey management; export to JSON, encrypted JSON, and Comma-separated values, C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GPGPU
General-purpose computing on graphics processing units (GPGPU, or less often GPGP) is the use of a graphics processing unit (GPU), which typically handles computation only for computer graphics, to perform computation in applications traditionally handled by the central processing unit (CPU). The use of multiple video cards in one computer, or large numbers of graphics chips, further parallelizes the already parallel nature of graphics processing. Essentially, a GPGPU pipeline is a kind of parallel processing between one or more GPUs and CPUs that analyzes data as if it were in image or other graphic form. While GPUs operate at lower frequencies, they typically have many times the number of cores. Thus, GPUs can process far more pictures and graphical data per second than a traditional CPU. Migrating data into graphical form and then using the GPU to scan and analyze it can create a large speedup. GPGPU pipelines were developed at the beginning of the 21st century for grap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary Logarithm
In mathematics, the binary logarithm () is the exponentiation, power to which the number must be exponentiation, raised to obtain the value . That is, for any real number , :x=\log_2 n \quad\Longleftrightarrow\quad 2^x=n. For example, the binary logarithm of is , the binary logarithm of is , the binary logarithm of is , and the binary logarithm of is . The binary logarithm is the logarithm to the base and is the inverse function of the power of two function. There are several alternatives to the notation for the binary logarithm; see the #Notation, Notation section below. Historically, the first application of binary logarithms was in music theory, by Leonhard Euler: the binary logarithm of a frequency ratio of two musical tones gives the number of octaves by which the tones differ. Binary logarithms can be used to calculate the length of the representation of a number in the binary numeral system, or the number of bits needed to encode a message in infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Theory
Information theory is the mathematical study of the quantification (science), quantification, Data storage, storage, and telecommunications, communication of information. The field was established and formalized by Claude Shannon in the 1940s, though early contributions were made in the 1920s through the works of Harry Nyquist and Ralph Hartley. It is at the intersection of electronic engineering, mathematics, statistics, computer science, Neuroscience, neurobiology, physics, and electrical engineering. A key measure in information theory is information entropy, entropy. Entropy quantifies the amount of uncertainty involved in the value of a random variable or the outcome of a random process. For example, identifying the outcome of a Fair coin, fair coin flip (which has two equally likely outcomes) provides less information (lower entropy, less uncertainty) than identifying the outcome from a roll of a dice, die (which has six equally likely outcomes). Some other important measu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shannon (unit)
The shannon (symbol: Sh) is a unit of information named after Claude Shannon, the founder of information theory. IEC 80000-13 defines the shannon as the information content associated with an event when the probability of the event occurring is . It is understood as such within the realm of information theory, and is conceptually distinct from the bit, a term used in data processing and storage to denote a single instance of a binary signal. A sequence of ''n'' binary symbols (such as contained in computer memory or a binary data transmission) is properly described as consisting of ''n'' bits, but the information content of those ''n'' symbols may be more or less than ''n'' shannons depending on the ''a priori'' probability of the actual sequence of symbols. The shannon also serves as a unit of the information entropy of an event, which is defined as the expected value of the information content of the event (i.e., the probability-weighted average of the information content of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Entropy
In information theory, the entropy of a random variable quantifies the average level of uncertainty or information associated with the variable's potential states or possible outcomes. This measures the expected amount of information needed to describe the state of the variable, considering the distribution of probabilities across all potential states. Given a discrete random variable X, which may be any member x within the set \mathcal and is distributed according to p\colon \mathcal\to , 1/math>, the entropy is \Eta(X) := -\sum_ p(x) \log p(x), where \Sigma denotes the sum over the variable's possible values. The choice of base for \log, the logarithm, varies for different applications. Base 2 gives the unit of bits (or " shannons"), while base ''e'' gives "natural units" nat, and base 10 gives units of "dits", "bans", or " hartleys". An equivalent definition of entropy is the expected value of the self-information of a variable. The concept of information entropy was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Salt
In cryptography, a salt is random data fed as an additional input to a one-way function that hashes data, a password or passphrase. Salting helps defend against attacks that use precomputed tables (e.g. rainbow tables), by vastly growing the size of table needed for a successful attack. It also helps protect passwords that occur multiple times in a database, as a new salt is used for each password instance. Additionally, salting does not place any burden on users. Typically, a unique salt is randomly generated for each password. The salt and the password (or its version after key stretching) are concatenated and fed to a cryptographic hash function, and the output hash value is then stored with the salt in a database. The salt does not need to be encrypted, because knowing the salt would not help the attacker. Salting is broadly used in cybersecurity, from Unix system credentials to Internet security. Salts are related to cryptographic nonces. Example Without a salt, iden ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rainbow Tables
A rainbow table is a precomputed Lookup table, table for caching the outputs of a cryptographic hash function, usually for Password cracking, cracking password hashes. Passwords are typically stored not in plain text form, but as hash values. If such a database of hashed passwords falls into the hands of attackers, they can use a precomputed rainbow table to recover the plaintext passwords. A common defense against this attack is to compute the hashes using a key derivation function that adds a "Salt (cryptography), salt" to each password before hashing it, with different passwords receiving different salts, which are stored in plain text along with the hash. Rainbow tables are a practical example of a space–time tradeoff: they use less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple table that stores the hash of every possible password. Rainbow tables were inve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) (Wireless Protected Access), Wi-Fi Protected Access 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, Wired Equivalent Privacy (WEP). WPA (sometimes referred to as the TKIP standard) became available in 2003. The Wi-Fi Alliance intended it as an intermediate measure in anticipation of the availability of the more secure and complex WPA2, which became available in 2004 and is a common shorthand for the full IEEE 802.11i (or IEEE 802.11i-2004) standard. In January 2018, the Wi-Fi Alliance announced the release of WPA3, which has several security improvements over WPA2. As of 2023, most computers that connect to a wireless network have support for using WPA, WPA2, or WPA3. All versions thereof, at least as implemented throu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm In mathematics and computer science, an algorithm () is a finite sequence of Rigour#Mathematics, mathematically rigorous instructions, typically used to solve a class of specific Computational problem, problems or to perform a computation. Algo ..., can Encryption, encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key's security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the pra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Stretching
In cryptography, key stretching techniques are used to make a possibly weak key, typically a password or passphrase, more secure against a brute-force attack by increasing the resources (time and possibly space) it takes to test each possible key. Passwords or passphrases created by humans are often short or predictable enough to allow password cracking, and key stretching is intended to make such attacks more difficult by complicating a basic step of trying a single password candidate. Key stretching also improves security in some real-world applications where the key length has been constrained, by mimicking a longer key length from the perspective of a brute-force attacker. There are several ways to perform key stretching. One way is to apply a cryptographic hash function or a block cipher repeatedly in a loop. For example, in applications where the key is used for a cipher, the key schedule in the cipher may be modified so that it takes a specific length of time to perform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nvidia Tesla
Nvidia Tesla is the former name for a line of products developed by Nvidia targeted at stream processing or GPGPU, general-purpose graphics processing units (GPGPU), named after pioneering electrical engineer Nikola Tesla. Its products began using GPUs from the GeForce 8 series, G80 series, and have continued to accompany the release of new chips. They are programmable using the CUDA or OpenCL application programming interface, APIs. The Nvidia Tesla product line competed with AMD's Radeon Instinct and Intel Xeon Phi lines of deep learning and GPU cards. Nvidia retired the Tesla brand in May 2020, reportedly because of potential confusion with the Tesla, Inc., brand of cars. Its new GPUs are branded Nvidia Data Center GPUs as in the Ampere (microarchitecture), Ampere-based A100 GPU. Nvidia DGX servers feature Nvidia GPGPUs. Overview Offering computational power much greater than traditional Central processing units, microprocessors, the Tesla products targeted the high-perfo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |