|
Office Of Intelligence And Counterintelligence
The Office of Intelligence and Counterintelligence (OICI; also abbreviated IN, DOE-IN, DOE/IN, I&CI, or OIC) is an office of the United States Department of Energy (DOE) responsible for all intelligence and counterintelligence activities throughout the DOE complex. It was established in 2006 by the merger of pre-existing Energy Department intelligence and security organizations. Due to its central role, OICI is designated DOE's Headquarters Intelligence. As a component of the United States Intelligence Community in addition to the Department of Energy, OICI reports to both the Director of National Intelligence and Secretary of Energy. Overview The Office of Intelligence and Counterintelligence provides information to the Secretary of Energy and other senior federal policymakers. A member of the United States Intelligence Community, it contributes unique scientific and technical analysis capabilities with a specialty in energy security. The office protects information and techno ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Seal Of The United States Department Of Energy
Seal may refer to any of the following: Common uses * Pinniped, a diverse group of semi-aquatic marine mammals, many of which are commonly called seals, particularly: ** Earless seal, also called "true seal" ** Fur seal ** Eared seal * Seal (emblem), a device to impress an emblem, used as a means of authentication, on paper, wax, clay or another medium (the impression is also called a seal) * Seal (mechanical), a device which helps prevent leakage, contain pressure, or exclude contamination where two systems join ** Hermetic seal, an airtight mechanical seal * Security seals such as labels, tapes, bands, or ties affixed onto a container in order to prevent and detect tampering Arts, entertainment and media * ''Seal'' (1991 album), by Seal * ''Seal'' (1994 album), sometimes referred to as ''Seal II'', by Seal * '' Seal IV'', a 2003 album by Seal * '' Seal Online'', a 2003 massively multiplayer online role-playing game Law * Seal (contract law), a legal formality for con ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Radioactive Waste
Radioactive waste is a type of hazardous waste that contains radioactive material. It is a result of many activities, including nuclear medicine, nuclear research, nuclear power generation, nuclear decommissioning, rare-earth mining, and nuclear weapons reprocessing. The storage and disposal of radioactive waste is regulated by government agencies in order to protect human health and the environment. Radioactive waste is broadly classified into 3 categories: low-level waste (LLW), such as paper, rags, tools, clothing, which contain small amounts of mostly short-lived radioactivity; intermediate-level waste (ILW), which contains higher amounts of radioactivity and requires some shielding; and high-level waste (HLW), which is highly radioactive and hot due to decay heat, thus requiring cooling and shielding. Spent nuclear fuel can be processed in nuclear reprocessing plants. One third of the total amount have already been reprocessed. With nuclear reprocessing 96% of the spent fue ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Threat Intelligence
Cyber threat intelligence (CTI) is a subfield of cybersecurity that focuses on the structured collection, analysis, and dissemination of data regarding potential or existing cyber threats. It provides organizations with the insights necessary to anticipate, prevent, and respond to cyberattacks by understanding the behavior of threat actors, their tactics, and the vulnerabilities they exploit. Cyber threat intelligence sources include open source intelligence, social media intelligence, human Intelligence, technical intelligence, device log files, forensically acquired data or intelligence from the internet traffic and data derived for the deep and dark web. In recent years, threat intelligence has become a crucial part of companies' cyber security strategy since it allows companies to be more proactive in their approach and determine which threats represent the greatest risks to a business. This puts companies on a more proactive front, actively trying to find their vulnera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nuclear Terrorism
Nuclear terrorism is the use of a nuclear weapon or radiological weapon as an act of terrorism. There are many possible terror incidents, ranging in feasibility and scope. These include the sabotage of a nuclear facility, the intentional irradiation of citizens, or the detonation of a radiological device, colloquially termed a dirty bomb, but consensus is lacking. According to the 2005 United Nations International Convention for the Suppression of Acts of Nuclear Terrorism nuclear terrorism is an offense committed if a person unlawfully and intentionally "uses in any way radioactive material … with the intent to cause death or serious bodily injury; or with the intent to cause substantial damage to property or to the environment; or with the intent to compel a natural or legal person, an international organization or a State to do or refrain from doing an act." The possibility of terrorist organizations using nuclear weapons has been identified by nuclear powers and conside ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nuclear Material
Nuclear material refers to the metals uranium, plutonium, and thorium, in any form, according to the IAEA. This is differentiated further into "source material", consisting of natural and depleted uranium, and "special fissionable material", consisting of enriched uranium ( U-235), uranium-233, and plutonium-239. Uranium ore concentrates are considered to be a "source material", although these are not subject to safeguards under the Nuclear Non-Proliferation Treaty. According to the Nuclear Regulatory Commission(NRC), there are four different types of regulated nuclear materials: special nuclear material, source material, byproduct material and radium. Special nuclear materials have plutonium, uranium-233 or uranium with U233 or U235 that has a content found more than in nature. Source material is thorium or uranium that has a U235 content equal to or less than what is in nature. Byproduct material is radioactive material that is not source or special nuclear material. It can be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nuclear Fuel Cycle
The nuclear fuel cycle, also known as the nuclear fuel chain, describes the series of stages that nuclear fuel undergoes during its production, use, and recycling or disposal. It consists of steps in the ''front end'', which are the preparation of the fuel, steps in the ''service period'' in which the fuel is used during reactor operation, and steps in the ''back end'', which are necessary to safely manage, contain, and either reprocess or dispose of spent nuclear fuel. If spent fuel is not reprocessed, the fuel cycle is referred to as an ''open fuel cycle'' (or a ''once-through fuel cycle''); if the spent fuel is reprocessed, it is referred to as a ''closed fuel cycle''. Basic concepts Nuclear power relies on fissionable material that can sustain a chain reaction with neutrons. Examples of such materials include uranium and plutonium. Most nuclear reactors use a moderator to lower the kinetic energy of the neutrons and increase the probability that fission will occur. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nuclear Weapons
A nuclear weapon is an explosive device that derives its destructive force from nuclear reactions, either nuclear fission, fission (fission or atomic bomb) or a combination of fission and nuclear fusion, fusion reactions (thermonuclear weapon), producing a nuclear explosion. Both bomb types release large quantities of energy from relatively small amounts of matter. Nuclear bombs have had Nuclear weapon yield, yields between 10 tons (the W54) and 50 megatons for the Tsar Bomba (see TNT equivalent). Yields in the low kilotons can devastate cities. A thermonuclear weapon weighing as little as can release energy equal to more than 1.2 megatons of TNT (5.0 Petajoule, PJ). Apart from the blast, Effects of nuclear explosions, effects of nuclear weapons include Firestorm, firestorms, extreme Thermal radiation, heat and ionizing radiation, radioactive nuclear fallout, an Nuclear electromagnetic pulse, electromagnetic pulse, and a radar blackout. The first nuclear weapons were deve ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intelligence Analysis
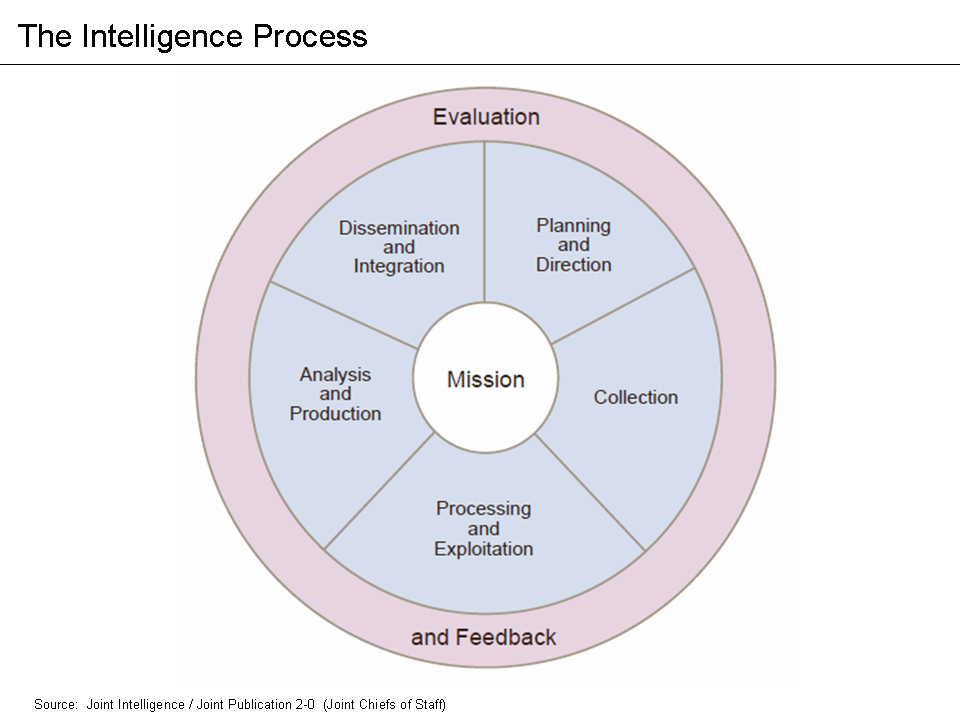
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberately deceptive information; the :wikt:analyst, analyst must correlate the similarities among deceptions and extract a common truth. Although its practice is found in its purest form inside national intelligence agency, intelligence agencies, its methods are also applicable in fields such as business intelligence or competitive intelligence. Overview Intelligence analysis is a way of reducing the ambiguity of highly ambiguous situations. Many analysts prefer the middle-of-the-road explanation, rejecting high or low probability explanations. Analysts may use their own standard of proportionality as to the risk acceptance of the opponent, rejecting that the opponent may take an extreme risk to achieve what the analyst regards as a minor gai ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Homeland Security
Homeland security is an American national security term for "the national effort to ensure a homeland that is safe, secure, and resilient against terrorism and other hazards where American interests, aspirations, and ways of life can thrive" to the "national effort to prevent terrorist attacks within the United States, reduce the vulnerability of the U.S. to terrorism, and minimize the damage from attacks that do occur." According to an official work published by the Congressional Research Service in 2013, the "Homeland security" term's definition has varied over time. Homeland security is not constrained to terrorist incidents. Terrorism is violent, criminal acts committed by individuals and/or groups to further ideological goals stemming from influences, such as those of a political, religious, social, racial, or environmental nature. Within the US, an all-hazards approach exists regarding homeland security endeavors. In this sense, homeland security encompasses both natural d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intellectual Property
Intellectual property (IP) is a category of property that includes intangible creations of the human intellect. There are many types of intellectual property, and some countries recognize more than others. The best-known types are patents, copyrights, trademarks, and trade secrets. The modern concept of intellectual property developed in England in the 17th and 18th centuries. The term "intellectual property" began to be used in the 19th century, though it was not until the late 20th century that intellectual property became commonplace in most of the world's List of national legal systems, legal systems."property as a common descriptor of the field probably traces to the foundation of the World Intellectual Property Organization (WIPO) by the United Nations." in Mark A. Lemley''Property, Intellectual Property, and Free Riding'', Texas Law Review, 2005, Vol. 83:1031, page 1033, footnote 4. Supporters of intellectual property laws often describe their main purpose as encouragin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Counterintelligence
Counterintelligence (counter-intelligence) or counterespionage (counter-espionage) is any activity aimed at protecting an agency's Intelligence agency, intelligence program from an opposition's intelligence service. It includes gathering information and conducting activities to prevent espionage, sabotage, assassinations or other Intelligence field, intelligence activities conducted by, for, or on behalf of foreign powers, organizations or persons. Many countries will have multiple organizations focusing on a different aspect of counterintelligence, such as domestic, international, and counter-terrorism. Some states will formalize it as part of the police structure, such as the United States' Federal Bureau of Investigation (FBI). Others will establish independent bodies, such as the United Kingdom's MI5, others have both intelligence and counterintelligence grouped under the same agency, like the Canadian Security Intelligence Service (CSIS). History Modern tactics of espiona ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |