|
Non-lock Concurrency Control
In Computer Science, in the field of databases, non-lock concurrency control is a concurrency control method used in relational databases without using lock (computer science), locking. There are several non-lock concurrency control methods, which involve the use of timestamps on transaction to determine transaction priority: * Optimistic concurrency control ** Timestamp-based concurrency control ** Validation-based concurrency control ** Multiversion concurrency control *** Snapshot isolation See also * Concurrency pattern * InterBase * Lock-free and wait-free algorithms References Concurrency control Transaction processing {{Database-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, information, and automation. Computer science spans Theoretical computer science, theoretical disciplines (such as algorithms, theory of computation, and information theory) to Applied science, applied disciplines (including the design and implementation of Computer architecture, hardware and Software engineering, software). Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of computational problem, problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and preventing security vulnerabilities. Computer graphics (computer science), Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
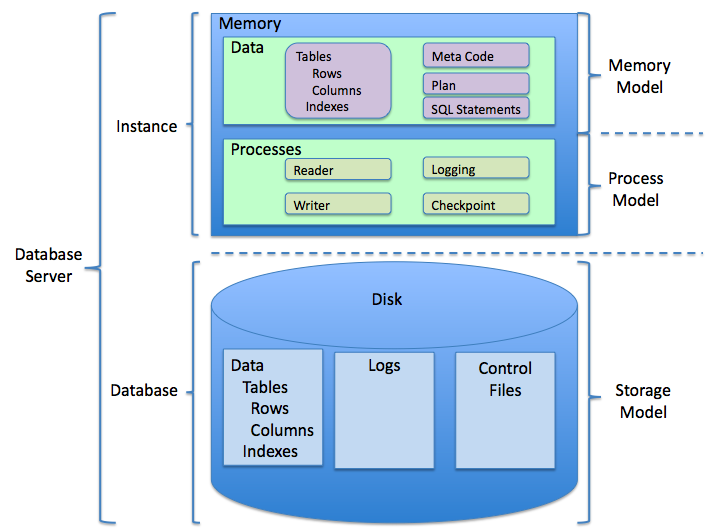
Database
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an application associated with the database. Before digital storage and retrieval of data have become widespread, index cards were used for data storage in a wide range of applications and environments: in the home to record and store recipes, shopping lists, contact information and other organizational data; in business to record presentation notes, project research and notes, and contact information; in schools as flash c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concurrency Control
In information technology and computer science, especially in the fields of computer programming, operating systems, multiprocessors, and databases, concurrency control ensures that correct results for concurrent operations are generated, while getting those results as quickly as possible. Computer systems, both software and hardware, consist of modules, or components. Each component is designed to operate correctly, i.e., to obey or to meet certain consistency rules. When components that operate concurrently interact by messaging or by sharing accessed data (in memory or storage), a certain component's consistency may be violated by another component. The general area of concurrency control provides rules, methods, design methodologies, and theories to maintain the consistency of components operating concurrently while interacting, and thus the consistency and correctness of the whole system. Introducing concurrency control into a system means applying operation constraints ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Relational Database
A relational database (RDB) is a database based on the relational model of data, as proposed by E. F. Codd in 1970. A Relational Database Management System (RDBMS) is a type of database management system that stores data in a structured format using rows and columns. Many relational database systems are equipped with the option of using SQL (Structured Query Language) for querying and updating the database. History The concept of relational database was defined by E. F. Codd at IBM in 1970. Codd introduced the term ''relational'' in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by ''relation''. One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lock (computer Science)
In computer science, a lock or mutex (from mutual exclusion) is a synchronization primitive that prevents state from being modified or accessed by multiple threads of execution at once. Locks enforce mutual exclusion concurrency control policies, and with a variety of possible methods there exist multiple unique implementations for different applications. Types Generally, locks are ''advisory locks'', where each thread cooperates by acquiring the lock before accessing the corresponding data. Some systems also implement ''mandatory locks'', where attempting unauthorized access to a locked resource will force an exception in the entity attempting to make the access. The simplest type of lock is a binary semaphore. It provides exclusive access to the locked data. Other schemes also provide shared access for reading data. Other widely implemented access modes are exclusive, intend-to-exclude and intend-to-upgrade. Another way to classify locks is by what happens when the lock st ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Optimistic Concurrency Control
Optimistic concurrency control (OCC), also known as optimistic locking, is a non-locking concurrency control method applied to transactional systems such as relational database management systems and software transactional memory. OCC assumes that multiple transactions can frequently complete without interfering with each other. While running, transactions use data resources without acquiring locks on those resources. Before committing, each transaction verifies that no other transaction has modified the data it has read. If the check reveals conflicting modifications, the committing transaction rolls back and can be restarted. Optimistic concurrency control was first proposed in 1979 by H. T. Kung and John T. Robinson. OCC is generally used in environments with low data contention. When conflicts are rare, transactions can complete without the expense of managing locks and without having transactions wait for other transactions' locks to clear, leading to higher throughput than ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timestamp-based Concurrency Control
In computer science, a timestamp-based concurrency control algorithm is a optimistic concurrency control method. It is used in some databases to safely handle transactions using timestamps. Operation Assumptions * Every timestamp value is unique and accurately represents an instant in time. * A higher-valued timestamp occurs later in time than a lower-valued timestamp. Generating a timestamp A number of different approaches can generate timestamps * Using the value of the system's clock at the start of a transaction as the timestamp. * Using a thread-safe shared counter that is incremented at the start of a transaction as the timestamp. * A combination of the above two methods. Formal definition Each transaction (T_i) is an ordered list of actions (A_). Before the transaction performs its first action (A_), it is marked with the current timestamp, or any other strictly totally ordered sequence: TS(T_i) = NOW(). Every transaction is also given an initially empty set of transacti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiversion Concurrency Control
Multiversion concurrency control (MCC or MVCC), is a non-locking concurrency control method commonly used by database management systems to provide concurrent access to the database and in programming languages to implement transactional memory. Description Without concurrency control, if someone is reading from a database at the same time as someone else is writing to it, it is possible that the reader will see a half-written or inconsistent piece of data. For instance, when making a wire transfer between two bank accounts if a reader reads the balance at the bank when the money has been withdrawn from the original account and before it was deposited in the destination account, it would seem that money has disappeared from the bank. Isolation is the property that provides guarantees in the concurrent accesses to data. Isolation is implemented by means of a concurrency control protocol. The simplest way is to make all readers wait until the writer is done, which is known as a rea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Snapshot Isolation
In databases, and transaction processing (transaction management), snapshot isolation is a guarantee that all reads made in a transaction will see a consistent snapshot of the database (in practice it reads the last committed values that existed at the time it started), and the transaction itself will successfully commit only if no updates it has made conflict with any concurrent updates made since that snapshot. Snapshot isolation has been adopted by several major database management systems, such as InterBase, Firebird, Oracle, MySQL, PostgreSQL, SQL Anywhere, MongoDB and Microsoft SQL Server (2005 and later). The main reason for its adoption is that it allows better performance than serializability, yet still avoids most of the concurrency anomalies that serializability avoids (but not all). In practice snapshot isolation is implemented within multiversion concurrency control (MVCC), where generational values of each data item (versions) are maintained: MVCC is a common way to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concurrency Pattern
In software engineering, concurrency patterns are those types of design patterns that deal with the multi-threaded programming paradigm. Examples of this class of patterns include: * Active object * Balking pattern * Barrier * Double-checked locking * Guarded suspension * Leaders/followers pattern * Monitor object * Nuclear reaction * Reactor pattern * Readers–writer lock * Scheduler pattern * Thread pool pattern * Thread-local storage See also * '' Design Patterns'' (book) * Behavioral pattern * Creational pattern In software engineering, creational design patterns are design patterns that deal with object creation Object may refer to: General meanings * Object (philosophy), a thing, being, or concept ** Object (abstract), an object which does not ex ... * Structural pattern References External links ScaleConf Presentation about concurrency patternsGopherCon Rethinking Classical Concurrency Patterns [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
InterBase
InterBase is a relational database management system (RDBMS) currently developed and marketed by Embarcadero Technologies. It runs on the operating systems Microsoft Windows, macOS, Linux, Oracle Solaris, Solaris, Android (operating system), Android, and iOS. Technology InterBase is a SQL-92-compliant relational database and supports standard interfaces such as JDBC, ODBC, and ADO.NET. History Multiversion concurrency control before InterBase Multiversion concurrency control is described in some detail in sections 4.3 and 5.5 of the 1981 paper "Concurrency Control in Distributed Database Systems" by Phil Bernstein, Philip Bernstein and Nathan Goodman while employed by the Computer Corporation of America. Bernstein and Goodman's paper cites a 1978 dissertation by D.P. Reed, which describes Multiversion concurrency control, MVCC and claims it as an original work. Early years Jim Starkey was working at Digital Equipment Corporation, DEC on their DATATRIEVE 4th generation languag ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lock-free And Wait-free Algorithms
In computer science, an algorithm is called non-blocking if failure or suspension of any thread cannot cause failure or suspension of another thread; for some operations, these algorithms provide a useful alternative to traditional blocking implementations. A non-blocking algorithm is lock-free if there is guaranteed system-wide progress, and wait-free if there is also guaranteed per-thread progress. "Non-blocking" was used as a synonym for "lock-free" in the literature until the introduction of obstruction-freedom in 2003. The word "non-blocking" was traditionally used to describe telecommunications networks that could route a connection through a set of relays "without having to re-arrange existing calls" (see Clos network). Also, if the telephone exchange "is not defective, it can always make the connection" (see nonblocking minimal spanning switch). Motivation The traditional approach to multi-threaded programming is to use locks to synchronize access to shared res ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |