|
List Of ISO Standards 28000–29999
This is a list of publishedThis list generally excludes draft versions. International Organization for Standardization (ISO) standards and other deliverables.ISO deliverables include "specifications" (ISO/PAS, ISO/TS), "reports" (ISO/TR), etc, which are not referred to by ISO as "standards". For a complete and up-to-date list of all the ISO standards, see the ISO catalogue. The standards are protected by and most of them must be purchased. However, about 300 of the standards produced by ISO and 's Joint Technical Committee 1 ( |
International Organization For Standardization
The International Organization for Standardization (ISO ; ; ) is an independent, non-governmental, international standard development organization composed of representatives from the national standards organizations of member countries. Membership requirements are given in Article 3 of the ISO Statutes. ISO was founded on 23 February 1947, and () it has published over 25,000 international standards covering almost all aspects of technology and manufacturing. It has over 800 technical committees (TCs) and subcommittees (SCs) to take care of standards development. The organization develops and publishes international standards in technical and nontechnical fields, including everything from manufactured products and technology to food safety, transport, IT, agriculture, and healthcare. More specialized topics like electrical and electronic engineering are instead handled by the International Electrotechnical Commission.Editors of Encyclopedia Britannica. 3 June 2021.Inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ISO/IEC 29119
ISO/IEC/IEEE 29119 ''Software and systems engineering -- Software testing'' is a series of five international standards for software testing. First developed in 2007 and released in 2013, the standard "defines vocabulary, processes, documentation, techniques, and a process assessment model for testing that can be used within any software development lifecycle." History and revisions Development of the set of ISO/IEC/IEEE 29119 software testing standards began in May 2007, based on existing standards such as the Institute of Electrical and Electronics Engineers's IEEE 829 (test documentation), and IEEE 1008 (unit testing); and the BSI Group's BS 7925-1 (vocabulary) and -2 (software components). At first the International Organization for Standardization (ISO) had no working group with significant software testing experience, so the ISO created WG26, which by 2011 was represented by more than 20 different countries. Initially four sections were developed for the standard: Concepts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Speck (cipher)
Speck is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Speck has been optimized for performance in software implementations, while its sister algorithm, Simon, has been optimized for hardware implementations. Speck is an add–rotate–xor (ARX) cipher. The NSA began working on the Simon and Speck ciphers in 2011. The agency anticipated some agencies in the US federal government would need a cipher that would operate well on a diverse collection of Internet of Things devices while maintaining an acceptable level of security. Cipher description Speck supports a variety of block and key sizes. A block is always two words, but the words may be 16, 24, 32, 48 or 64 bits in size. The corresponding key is 2, 3 or 4 words. The round function consists of two rotations, adding the right word to the left word, xoring the key into the left word, then xoring the left word into the right word. The number of rounds depends ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Simon (cipher)
Simon is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013. Simon has been optimized for performance in hardware implementations, while its sister algorithm, Speck, has been optimized for software implementations. The NSA began working on the Simon and Speck ciphers in 2011. The agency anticipated some agencies in the US federal government would need a cipher that would operate well on a diverse collection of Internet of Things devices while maintaining an acceptable level of security. Description of the cipher The Simon block cipher is a balanced Feistel cipher with an ''n''-bit word, and therefore the block length is 2''n''. The key length is a multiple of ''n'' by 2, 3, or 4, which is the value ''m''. Therefore, a Simon cipher implementation is denoted as Simon2''n''/''nm''. For example, Simon64/128 refers to the cipher operating on a 64-bit plaintext block (''n'' = 32) that uses a 128-bit key. The b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rabin Cryptosystem
The Rabin cryptosystem is a family of public-key encryption schemes based on a trapdoor function whose security, like that of RSA, is related to the difficulty of integer factorization. The Rabin trapdoor function has the advantage that inverting it has been mathematically proven to be as hard as factoring integers, while there is no such proof known for the RSA trapdoor function. It has the disadvantage that each output of the Rabin function can be generated by any of four possible inputs; if each output is a ciphertext, extra complexity is required on decryption to identify which of the four possible inputs was the true plaintext. Naive attempts to work around this often either enable a chosen-ciphertext attack to recover the secret key or, by encoding redundancy in the plaintext space, invalidate the proof of security relative to factoring. Public-key encryption schemes based on the Rabin trapdoor function are used mainly for examples in textbooks. In contrast, RSA is the b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ECDSA
In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic-curve cryptography. Key and signature sizes As with elliptic-curve cryptography in general, the bit size of the private key believed to be needed for ECDSA is about twice the size of the security level, in bits. For example, at a security level of 80 bits—meaning an attacker requires a maximum of about 2^ operations to find the private key—the size of an ECDSA private key would be 160 bits. On the other hand, the signature size is the same for both DSA and ECDSA: approximately 4 t bits, where t is the exponent in the formula 2^, that is, about 320 bits for a security level of 80 bits, which is equivalent to 2^ operations. Signature generation algorithm Suppose Alice wants to send a signed message to Bob. Initially, they must agree on the curve parameters (\textrm, G, n). In addition to the field and equation of the cu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OFB Mode
In cryptography, a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity. A block cipher by itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block. Most modes require a unique binary sequence, often called an initialization vector (IV), for each encryption operation. The IV must be non-repeating, and for some modes must also be random. The initialization vector is used to ensure that distinct ciphertexts are produced even when the same plaintext is encrypted multiple times independently with the same key. Block ciphers may be capable of operating on more than one block size, but during transformation the block size is always fixed. Block cipher modes op ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
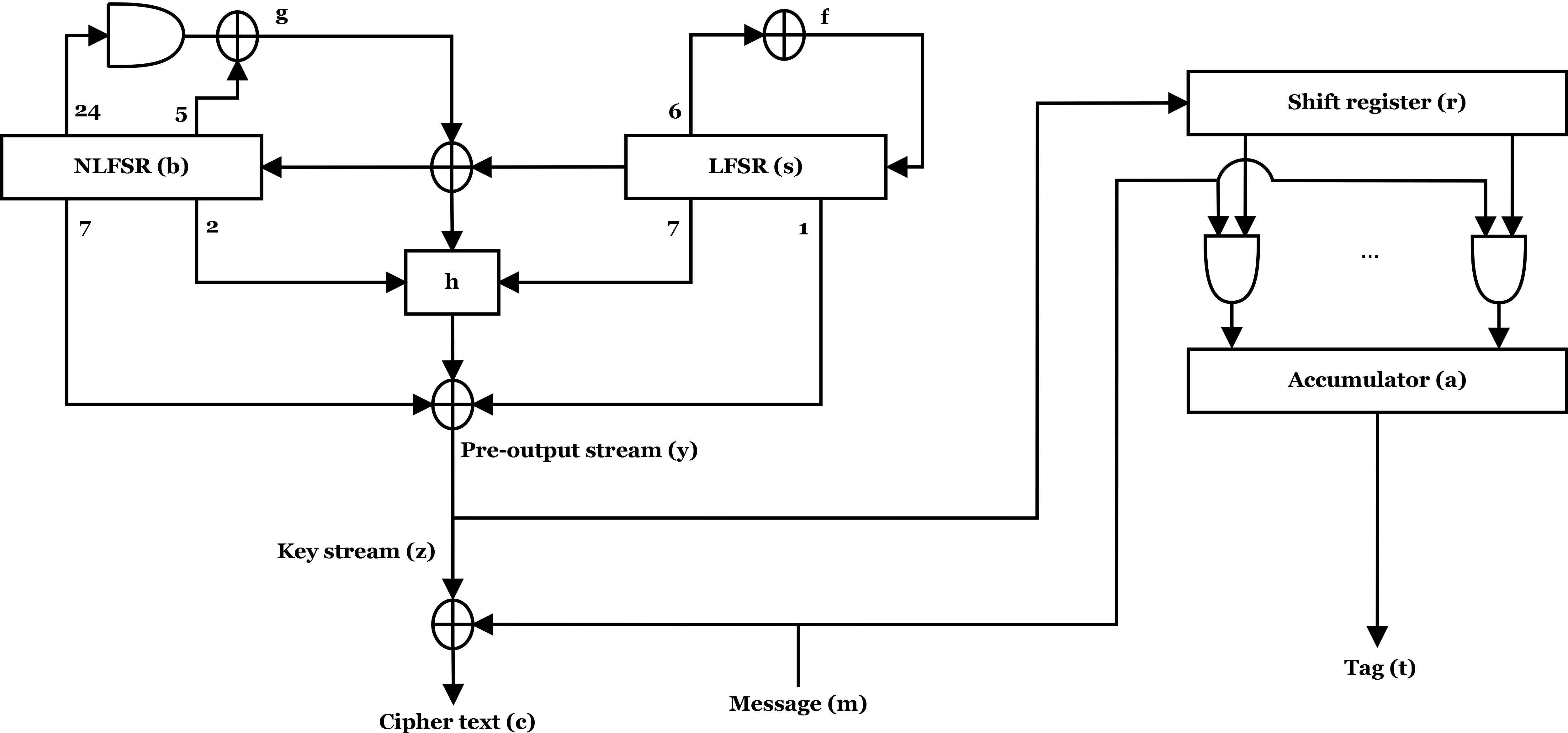
Grain 128a
The Grain 128a stream cipher was first purposed at Symmetric Key Encryption Workshop (SKEW) in 2011 as an improvement of the predecessor Grain 128, which added security enhancements and optional message authentication using the Encrypt & MAC approach. One of the important features of the Grain (cipher), Grain family is that the throughput can be increased at the expense of additional hardware. Grain 128a is designed by Martin Ågren, Martin Hell, Thomas Johansson and Willi Meier. Description of the cipher Grain 128a consists of two large parts: Pre-output function and MAC. The pre-output function has an internal state size of 256 bits, consisting of two registers of size 128 bit: NLFSR and LFSR. The MAC supports variable tag lengths w such that 0 [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elliptic Curve Diffie–Hellman
In mathematics, an ellipse is a plane curve surrounding two focal points, such that for all points on the curve, the sum of the two distances to the focal points is a constant. It generalizes a circle, which is the special type of ellipse in which the two focal points are the same. The elongation of an ellipse is measured by its eccentricity e, a number ranging from e = 0 (the limiting case of a circle) to e = 1 (the limiting case of infinite elongation, no longer an ellipse but a parabola). An ellipse has a simple algebraic solution for its area, but for its perimeter (also known as circumference), integration is required to obtain an exact solution. The largest and smallest diameters of an ellipse, also known as its width and height, are typically denoted and . An ellipse has four extreme points: two '' vertices'' at the endpoints of the major axis and two ''co-vertices'' at the endpoints of the minor axis. Analytically, the equation of a standard ellipse centered at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PRESENT
The present is the period of time that is occurring now. The present is contrasted with the past, the period of time that has already occurred; and the future, the period of time that has yet to occur. It is sometimes represented as a hyperplane in space-time, typically called "now", although modern physics demonstrates that such a hyperplane cannot be defined uniquely for observers in relative motion. The present may also be viewed as a duration. Historiography Contemporary history describes the historical timeframe immediately relevant to the present time and is a certain perspective of modern history. Philosophy and religion Philosophy of time "The present" raises the question: "How is it that all sentient beings experience ''now'' at the same time?" There is no logical reason why this should be the case and no easy answer to the question. In Buddhism Buddhism and many of its associated paradigms emphasize the importance of living in the present moment—being ful ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AES-128
The Advanced Encryption Standard (AES), also known by its original name Rijndael (), is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001. AES is a variant of the Rijndael block cipher developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, who submitted a proposal to NIST during the AES selection process. Rijndael is a family of ciphers with different key and block sizes. For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the U.S. government. It supersedes the Data Encryption Standard (DES), which was published in 1977. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data. In the United States, AES was announced by the NIST as U.S. FIPS PUB 197 (FIPS 197) on Nove ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sharable Content Object Reference Model
Sharable Content Object Reference Model (SCORM) is a collection of standards and specifications for web-based electronic educational technology (also called e-learning). It defines communications between client side content and a host system (called "the run-time environment"), which is commonly supported by a learning management system. SCORM also defines how content may be packaged into a transferable ZIP file called "Package Interchange Format." SCORM is a specification of the Advanced Distributed Learning (ADL) Initiative from the Office of the United States Secretary of Defense. SCORM 2004 introduced a complex idea called sequencing, which is a set of rules that specifies the order in which a learner may experience content objects. In simple terms, they constrain a learner to a fixed set of paths through the training material, permit the learner to "bookmark" their progress when taking breaks, and assure the acceptability of test scores achieved by the learner. The standa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |