|
Kerckhoffs's Principle
Kerckhoffs's principle (also called Kerckhoffs's desideratum, assumption, axiom, doctrine or law) of cryptography was stated by the Dutch cryptographer Auguste Kerckhoffs in the 19th century. The principle holds that a cryptosystem should be secure, even if everything about the system, except the key, is public knowledge. This concept is widely embraced by cryptographers, in contrast to security through obscurity, which is not. Kerckhoffs's principle was phrased by the American mathematician Claude Shannon as "the enemy knows the system", i.e., "one ought to design systems under the assumption that the enemy will immediately gain full familiarity with them". In that form, it is called Shannon's maxim. Another formulation by American researcher and professor Steven M. Bellovin is: In other words—design your system assuming that your opponents know it in detail. (A former official at NSA's National Computer Security Center told me that the standard assumption there was that ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Auguste Kerckhoffs
Auguste Kerckhoffs (19 January 1835 – 9 August 1903) was a Dutch linguist and cryptographer in the late 19th century. Biography Kerckhoffs was born in Nuth, the Netherlands, as Jean Guillaume Auguste Victor François Hubert Kerckhoffs, son of Jean Guillaume Kerckhoffs, mayor of the village of Nuth, and Jeanette Elisabeth Lintjens. Kerckhoffs studied at the University of Liège. After a period of teaching in schools in the Netherlands and France, he became a professor of German language at the École des Hautes Études Commerciales (Paris) and the École Arago. Principles He is best known today for his two-part paper published in 1883 in ''Le Journal des Sciences Militaires'' (''Journal of Military Science'') entitled ''La Cryptographie Militaire'' (''Military Cryptography''). These articles surveyed the then state-of-the-art in military cryptography, and made a plea for considerable improvements in French practice. They also included many pieces of practical advice ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is ''encipherment''. To encipher or encode is to convert information into cipher or code. In common parlance, "cipher" is synonymous with "code (cryptography), code", as they are both a set of steps that encrypt a message; however, the concepts are distinct in cryptography, especially classical cryptography. Codes generally substitute different length strings of characters in the output, while ciphers generally substitute the same number of characters as are input. A code maps one meaning with another. Words and phrases can be coded as letters or numbers. Codes typically have direct meaning from input to key. Codes primarily function to save time. Ciphers are algorithmic. The given input must follow the cipher's process to be solved. Ciphers are commonly used to encrypt written info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet standard, Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements and all its participants are volunteers. Their work is usually funded by employers or other sponsors. The IETF was initially supported by the federal government of the United States but since 1993 has operated under the auspices of the Internet Society, a non-profit organization with local chapters around the world. Organization There is no membership in the IETF. Anyone can participate by signing up to a working group mailing list, or registering for an IETF meeting. The IETF operates in a bottom-up task creation mode, largely driven by working groups. Each working group normally has appointed two co-chairs (occasionally three); a charter that describes its focus; and what it is expected to produce, and when. It is open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Randy Bush (scientist)
Randy Bush is a fellow at Arrcus and a research fellow at Internet Initiative Japan. He was among the inaugural inductees into the Internet Hall of Fame in 2012, given by the Internet Society. Career Bush has been working in the computer industry since 1966. He began with programming languages and specifically compilers. In 1977 he co-founded Northwest Microcomputer Systems with several other businessmen and computer engineers in Coos Bay, Oregon. The company released the 85/P, a Pascal development microcomputer, in 1978. In the late 1980s and early 1990s, Bush played a role in bringing the Internet to South Africa. Bush was the senior engineer of the Verio founding team in the late 1990s, and worked there for five years as the Vice President of IP Networking. He was the Principal Engineer at RAINet in the early 90s, which was later acquired by Verio at which time he joined Verio. He was the founder of the Network Startup Resource Center and worked there as a PI. Bush has ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content Scramble System
The Content Scramble System (CSS) is a digital rights management (DRM) and encryption system employed on many commercially produced DVD-Video discs. CSS utilizes a proprietary 40-bit stream cipher algorithm. The system was introduced around 1996 and was first compromised in 1999. CSS is one of several complementary systems designed to restrict DVD-Video access. It has been superseded by newer DRM schemes such as Content Protection for Recordable Media (CPRM), or by Advanced Encryption Standard (AES) in the Advanced Access Content System (AACS) DRM scheme used by HD DVD and Blu-ray Disc, which have 56-bit and 128-bit key sizes, respectively, providing a much higher level of security than the less secure 40-bit key size of CSS. Preliminary note The content scramble system (CSS) is a collection of proprietary protection mechanisms for DVD-Video discs. CSS attempts to restrict access to the content only for licensed applications. According to the DVD Copy Control Assoc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Type 1 Encryption
The U.S. National Security Agency (NSA) used to rank cryptographic products or algorithms by a certification called product types. Product types were defined in the National Information Assurance Glossary (CNSSI No. 4009, 2010) which used to define Type 1, 2, 3, and 4 products. The definitions of numeric type products have been removed from the government lexicon and are no longer used in government procurement efforts. Type 1 product A Type 1 product was a device or system certified by NSA for use in cryptographically securing classified U.S. Government information. A Type 1 product was defined as: Cryptographic equipment, assembly or component classified or certified by NSA for encrypting and decrypting classified and sensitive national security information when appropriately keyed. Developed using established NSA business processes and containing NSA approved algorithms. Used to protect systems requiring the most stringent protection mechanisms. They were available to U.S. Go ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Atlantic Monthly
''The Atlantic'' is an American magazine and multi-platform publisher based in Washington, D.C. It features articles on politics, foreign affairs, business and the economy, culture and the arts, technology, and science. It was founded in 1857 in Boston as ''The Atlantic Monthly'', a literary and cultural magazine that published leading writers' commentary on education, the abolition of slavery, and other major political issues of that time. Its founders included Francis H. Underwood and prominent writers Ralph Waldo Emerson, Oliver Wendell Holmes Sr., Henry Wadsworth Longfellow, Harriet Beecher Stowe, and John Greenleaf Whittier. James Russell Lowell was its first editor. During the 19th and 20th centuries, the magazine also published the annual ''The Atlantic Monthly Almanac''. The magazine was purchased in 1999 by businessman David G. Bradley, who fashioned it into a general editorial magazine primarily aimed at serious national readers and " thought leaders"; in 2017, he ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
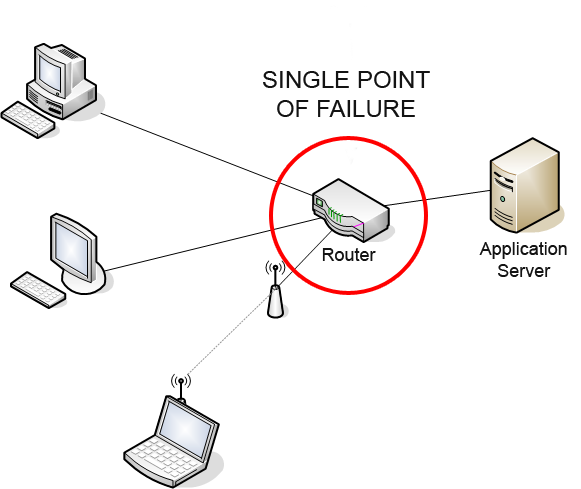
Single Point Of Failure
A single point of failure (SPOF) is a part of a system that would Cascading failure, stop the entire system from working if it were to fail. The term single point of failure implies that there is not a backup or redundant option that would enable the system to continue to function without it. SPOFs are undesirable in any system with a goal of high availability or Reliability engineering, reliability, be it a business practice, software application, or other industrial system. If there is a SPOF present in a system, it produces a potential interruption to the system that is substantially more disruptive than an error would elsewhere in the system. Overview Systems can be made robust by adding Redundancy (engineering), redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of wikt:malfunction, malfunction. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graceful Exit
Gracefulness, or being graceful, is the physical characteristic of displaying "pretty agility", in the form of elegant movement, poise, or balance. The etymological root of ''grace'' is the Latin word ''gratia'' from ''gratus'', meaning pleasing. Gracefulness has been described by reference to its being aesthetically pleasing. For example: The difficulty in defining exactly what constitutes gracefulness is described in this analysis of Henri Bergson's use of the term: Gracefulness is often referenced by simile, for example with people being described as "graceful as a swan", or "as graceful as a ballerina". The concept of gracefulness is applied both to movement, and to inanimate objects. For example, certain trees are commonly referred to as being "graceful", such as the '' Betula albosinensis'', '' Prunus × yedoensis'' (Yoshino cherry), and ''Areca catechu'' (betel-nut palm). Gracefulness is sometimes also attributed to non-corporeal human actions, such as the use of lan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bruce Schneier
Bruce Schneier (; born January 15, 1963) is an American cryptographer, computer security professional, privacy specialist, and writer. Schneier is an Adjunct Lecturer in Public Policy at the Harvard Kennedy School and a Fellow at the Berkman Klein Center for Internet & Society as of November, 2013. He is a board member of the Electronic Frontier Foundation, Access Now, and The Tor Project; and an advisory board member of Electronic Privacy Information Center and VerifiedVoting.org. He is the author of several books on general security topics, computer security and cryptography and is a squid enthusiast. Early life and education Bruce Schneier is the son of Martin Schneier, a Brooklyn Supreme Court judge. He grew up in the Flatbush neighborhood of Brooklyn, New York, attending P.S. 139 and Hunter College High School. After receiving a physics bachelor's degree from the University of Rochester in 1984, he went to American University in Washington, D.C., and got his ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Dump
In computing, a core dump, memory dump, crash dump, storage dump, system dump, or ABEND dump consists of the recorded state of the working memory of a computer program at a specific time, generally when the program has crashed or otherwise terminated abnormally. In practice, other key pieces of program state are usually dumped at the same time, including the processor registers, which may include the program counter and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and debugging errors in computer programs. On many operating systems, a fatal exception in a program automatically triggers a core dump. By extension, the phrase "to dump core" has come to mean in many cases, any fatal error, regardless of whether a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Steganographic
Steganography ( ) is the practice of representing information within another message or physical object, in such a manner that the presence of the concealed information would not be evident to an unsuspecting person's examination. In computing/electronic contexts, a computer file, message, image, or video is concealed within another file, message, image, or video. Generally, the hidden messages appear to be (or to be part of) something else: images, articles, shopping lists, or some other cover text. For example, the hidden message may be in invisible ink between the visible lines of a private letter. Some implementations of steganography that lack a formal shared secret are forms of security through obscurity, while key-dependent steganographic schemes try to adhere to Kerckhoffs's principle. The word ''steganography'' comes from Greek ''steganographia'', which combines the words ''steganós'' (), meaning "covered or concealed", and ''-graphia'' () meaning "writing". The firs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |