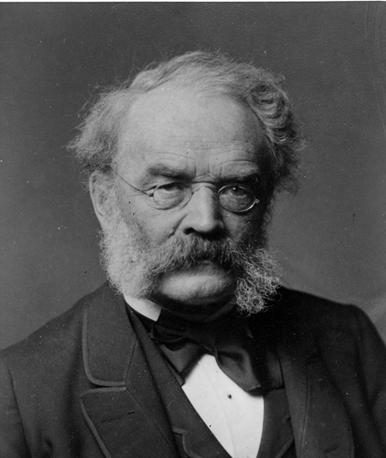|
Government Hacking
Government hacking permits the exploitation of vulnerabilities in electronic products, especially software, to gain remote access to information of interest. This information allows government investigators to monitor user activity and interfere with device operation. Government attacks on security may include malware and encryption backdoors. The National Security Agency's PRISM program and Ethiopia's use of FinSpy are notable examples. The term lawful hacking has been used for law enforcement agencies who utilize hacking. Hackers Security hackers have extensive knowledge of technology (particularly electronic devices and computer programs and networks), and may use their knowledge for illegal or unethical purposes. Hackers take advantage of vulnerabilities in software and systems; the hacking consists of manipulating computer systems or electronic devices to remotely control a machine or access stored data. Due to new technologies, it was necessary to update cryptographic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberspace
Cyberspace is an interconnected digital environment. It is a type of virtual world popularized with the rise of the Internet. The term entered popular culture from science fiction and the arts but is now used by technology strategists, security professionals, governments, military and industry leaders and entrepreneurs to describe the domain of the global technology environment, commonly defined as standing for the global network of interdependent information technology infrastructures, telecommunications networks and computer processing systems. Others consider cyberspace to be just a notional environment in which communication over computer networks occurs. The word became popular in the 1990s when the use of the Internet, networking, and digital communication were all growing dramatically; the term ''cyberspace'' was able to represent the many new ideas and phenomena that were emerging. As a social experience, individuals can interact, exchange ideas, share information, provi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP Address
An Internet Protocol address (IP address) is a numerical label such as that is assigned to a device connected to a computer network that uses the Internet Protocol for communication. IP addresses serve two main functions: network interface identification, and location addressing. Internet Protocol version 4 (IPv4) was the first standalone specification for the IP address, and has been in use since 1983. IPv4 addresses are defined as a 32-bit number, which became too small to provide enough addresses as the internet grew, leading to IPv4 address exhaustion over the 2010s. Its designated successor, IPv6, uses 128 bits for the IP address, giving it a larger address space. Although IPv6 deployment has been ongoing since the mid-2000s, both IPv4 and IPv6 are still used side-by-side . IP addresses are usually displayed in a human-readable notation, but systems may use them in various different computer number formats. CIDR notation can also be used to designate how much ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Investigative Technique
Network Investigative Technique (NIT) is a form of malware (or hacking) employed by the FBI since at least 2002. It is a drive-by download computer program designed to provide access to a computer. Controversies Its usage has raised both Fourth Amendment concerns and jurisdictional issues. The FBI has to date, despite a court order, declined to provide the complete code in a child sex abuse case involving the Tor anonymity network. On May 12, 2016 Mozilla filed an amicus curiae brief inasmuch as the FBI's exploit against the Mozilla Firefox web browsers potentially puts millions of users at risk. It asked that the exploit be told to them before it is told to the defendant, thus raising Fifth Amendment issues as well. Also, US District Judge Robert J. Bryan in Tacoma, Washington has ruled that while the defendant in ''United States v. Michaud'' has the right to review the code, the government also has the right to keep it secret (two other federal judges in related cases have ru ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Federal Bureau Of Investigation
The Federal Bureau of Investigation (FBI) is the domestic Intelligence agency, intelligence and Security agency, security service of the United States and Federal law enforcement in the United States, its principal federal law enforcement agency. An agency of the United States Department of Justice, the FBI is a member of the United States Intelligence Community, U.S. Intelligence Community and reports to both the United States Attorney General, attorney general and the Director of National Intelligence, director of national intelligence. A leading American counterterrorism, counterintelligence, and criminal investigative organization, the FBI has jurisdiction over violations of more than 200 categories of Federal crime in the United States, federal crimes. Although many of the FBI's functions are unique, its activities in support of national security are comparable to those of the British MI5 and National Crime Agency, NCA, the New Zealand Government Communications Security ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Deployment
Software deployment is all of the activities that make a software system available for use. Deployment can involve activities on the producer (software developer) side or on the consumer ( user) side or both. Deployment to consumers is a hard task because the target systems are diverse and unpredictable. Software as a service avoids these difficulties by deploying only to dedicated servers that are typically under the producer's control. Because every software system is unique, the precise processes or procedures within each activity can hardly be defined. Therefore, "deployment" should be interpreted as a ''general process'' that has to be customized according to specific requirements or characteristics. History When computers were extremely large, expensive, and bulky (mainframes and minicomputers), the software was often bundled together with the hardware by manufacturers. If business software needed to be installed on an existing computer, this might require an expens ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jennifer Granick
Jennifer Stisa Granick (born 1969) is an American attorney and educator. Senator Ron Wyden has called Granick an "NBA all-star of surveillance law." She is well known for her work with intellectual property law, free speech, privacy law, and other things relating to computer security, and has represented several high-profile hackers. Early life and education Granick was born and raised in Glen Ridge, New Jersey. Both of her parents were local educators. She attended Glen Ridge High School and then New College in Sarasota, Florida, from which she received a Bachelor of Arts degree in 1990. After that, she moved to San Francisco to attend Hastings Law School, from which she graduated in 1993. Career Granick began her career in criminal defense, first at the state public defender's office, then as a trial attorney at the law firm Campbell & DeMetrick. From 1996 to 2001 she worked in private practice specializing in defending cases involving computer crime. It was during t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for efficient use of the system and may also include accounting software for cost allocation of Scheduling (computing), processor time, mass storage, peripherals, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computerfrom cellular phones and video game consoles to web servers and supercomputers. , Android (operating system), Android is the most popular operating system with a 46% market share, followed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Siemens
Siemens AG ( ) is a German multinational technology conglomerate. It is focused on industrial automation, building automation, rail transport and health technology. Siemens is the largest engineering company in Europe, and holds the position of global market leader in industrial automation and industrial software. The origins of the conglomerate can be traced back to 1847 to the ''Telegraphen Bau-Anstalt von Siemens & Halske'' established in Berlin by Werner von Siemens and Johann Georg Halske. In 1966, the present-day corporation emerged from the merger of three companies: Siemens & Halske, Siemens-Schuckert, and Siemens-Reiniger-Werke. Today headquartered in Munich and Berlin, Siemens and its subsidiaries employ approximately 320,000 people worldwide and reported a global revenue of around €78 billion in 2023. The company is a component of the DAX and Euro Stoxx 50 stock market indices. As of December 2023, Siemens is the second largest German company by market ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sectors of the computing industry – Windows (unqualified) for a consumer or corporate workstation, Windows Server for a Server (computing), server and Windows IoT for an embedded system. Windows is sold as either a consumer retail product or licensed to Original equipment manufacturer, third-party hardware manufacturers who sell products Software bundles, bundled with Windows. The first version of Windows, Windows 1.0, was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). The name "Windows" is a reference to the windowing system in GUIs. The 1990 release of Windows 3.0 catapulted its market success and led to various other product families ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on exploiting the advantages of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer. Many worms are designed only to spread, and do not attempt to change the systems they pass thro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |