|
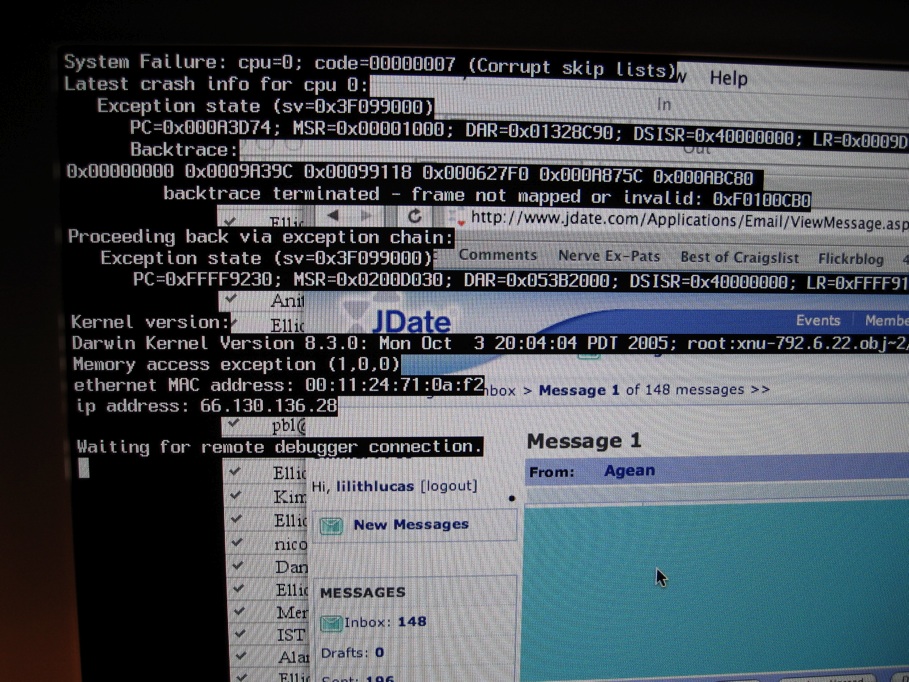
Crash (computing)
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. On some operating systems or individual applications, a crash reporting service will report the crash and any details relating to it (or give the user the option to do so), usually to the developer(s) of the application. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error. Most crashes are the result of a software bug. Typical causes include accessing invalid memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier bug, executing invalid machine instructions (an illegal or unauthorized opcode), or triggering an unhandled exception. The original software bug that started this chain of events is typically considere ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crashed Computer
"Crashed" is the third U.S. rock single, (the fifth overall), from the band Daughtry's debut album. It was released only to U.S. rock stations on September 5, 2007. Upon its release the song got adds at those stations, along with some Alternative and Top 40 stations. The song's release is like the release of " What I Want" in that while " Over You" was the mainstream third single, "Crashed" was the third single on U.S. rock stations. Music video Like "What I Want" it did not have an official video, since the band made one for the main third single, "Over You" instead. It did however have an unofficial promo video that mixes black and white scenes of the band performing with clips from the ACC and SEC College Football season, which the song was used to open. This video can be viewed here. Song usage and live performances The song, as mentioned, has been used to open the ACC and SEC College Football season and has been the opening number for the band's shows. In the United Stat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exception Handling
In computing and computer programming, exception handling is the process of responding to the occurrence of ''exceptions'' – anomalous or exceptional conditions requiring special processing – during the execution of a program. In general, an exception breaks the normal flow of execution and executes a pre-registered ''exception handler''; the details of how this is done depend on whether it is a hardware or software exception and how the software exception is implemented. Exceptions are defined by different layers of a computer system, and the typical layers are CPU-defined interrupts, operating system (OS)-defined signals, programming language-defined exceptions. Each layer requires different ways of exception handling although they may be interrelated, e.g. a CPU interrupt could be turned into an OS signal. Some exceptions, especially hardware ones, may be handled so gracefully that execution can resume where it was interrupted. Definition The definition of an excep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Debugger
A debugger is a computer program used to test and debug other programs (the "target" programs). Common features of debuggers include the ability to run or halt the target program using breakpoints, step through code line by line, and display or modify the contents of memory, CPU registers, and stack frames. The code to be examined might alternatively be running on an '' instruction set simulator'' (ISS), a technique that allows great power in its ability to halt when specific conditions are encountered, but which will typically be somewhat slower than executing the code directly on the appropriate (or the same) processor. Some debuggers offer two modes of operation, full or partial simulation, to limit this impact. An exception occurs when the program cannot normally continue because of a programming bug or invalid data. For example, the program might have tried to use an instruction not available on the current version of the CPU or attempted to access unavailable or pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graphical User Interface
A graphical user interface, or GUI, is a form of user interface that allows user (computing), users to human–computer interaction, interact with electronic devices through Graphics, graphical icon (computing), icons and visual indicators such as secondary notation. In many applications, GUIs are used instead of text-based user interface, text-based UIs, which are based on typed command labels or text navigation. GUIs were introduced in reaction to the perceived steep learning curve of command-line interfaces (CLIs), which require commands to be typed on a computer keyboard. The actions in a GUI are usually performed through direct manipulation interface, direct manipulation of the graphical elements. Beyond computers, GUIs are used in many handheld mobile devices such as MP3 players, portable media players, gaming devices, smartphones and smaller household, office and Distributed control system, industrial controls. The term ''GUI'' tends not to be applied to other lower-displa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Core Dump
In computing, a core dump, memory dump, crash dump, storage dump, system dump, or ABEND dump consists of the recorded state of the working Computer storage, memory of a computer program at a specific time, generally when the program has crash (computing), crashed or otherwise terminated abnormally. In practice, other key pieces of Context switch, program state are usually dumped at the same time, including the processor registers, which may include the program counter and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and debugging errors in computer programs. On many operating systems, a fatal exception in a program automatically triggers a core dump. By extension, the phrase "to dump core" has come to mean in many ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signal (IPC)
Signals are standardized messages sent to a running program to trigger specific behavior, such as quitting or error handling. They are a limited form of inter-process communication (IPC), typically used in Unix, Unix-like, and other POSIX-compliant operating systems. A signal is an asynchronous notification sent to a process or to a specific thread within the same process to notify it of an event. Common uses of signals are to interrupt, suspend, terminate or kill a process. Signals originated in 1970s Bell Labs Unix and were later specified in the POSIX standard. When a signal is sent, the operating system interrupts the target process's normal flow of execution to deliver the signal. Execution can be interrupted during any non-atomic instruction. If the process has previously registered a signal handler, that routine is executed. Otherwise, the default signal handler is executed. Embedded programs may find signals useful for inter-process communications, as sign ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exception Handling
In computing and computer programming, exception handling is the process of responding to the occurrence of ''exceptions'' – anomalous or exceptional conditions requiring special processing – during the execution of a program. In general, an exception breaks the normal flow of execution and executes a pre-registered ''exception handler''; the details of how this is done depend on whether it is a hardware or software exception and how the software exception is implemented. Exceptions are defined by different layers of a computer system, and the typical layers are CPU-defined interrupts, operating system (OS)-defined signals, programming language-defined exceptions. Each layer requires different ways of exception handling although they may be interrelated, e.g. a CPU interrupt could be turned into an OS signal. Some exceptions, especially hardware ones, may be handled so gracefully that execution can resume where it was interrupted. Definition The definition of an excep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Software
Application software is any computer program that is intended for end-user use not operating, administering or programming the computer. An application (app, application program, software application) is any program that can be categorized as application software. Common types of applications include word processor, media player and accounting software. The term ''application software'' refers to all applications collectively and can be used to differentiate from system and utility software. Applications may be bundled with the computer and its system software or published separately. Applications may be proprietary or open-source. The short term ''app'' (coined in 1981 or earlier) became popular with the 2008 introduction of the iOS App Store, to refer to applications for mobile devices such as smartphones and tablets. Later, with introduction of the Mac App Store (in 2010) and Windows Store (in 2011), the term was extended in popular use to include desktop a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Crash Airport
A computer is a machine that can be programmed to automatically carry out sequences of arithmetic or logical operations (''computation''). Modern digital electronic computers can perform generic sets of operations known as ''programs'', which enable computers to perform a wide range of tasks. The term computer system may refer to a nominally complete computer that includes the hardware, operating system, software, and peripheral equipment needed and used for full operation; or to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems, including simple special-purpose devices like microwave ovens and remote controls, and factory devices like industrial robots. Computers are at the core of general-purpose devices such as personal computers and mobile devices such as smartphones. Computers power the Internet, which links billions of computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and Code injection, inserting its own Computer language, code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a Computer program, host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the Computer program, host program, but can run independently and actively carry out attacks. Virus writers use social engineering (security), social engineering deceptions and exploit detailed knowledge of vulnerability (computing), security vulnerabilities to initially infect systems an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Arbitrary Code Execution
In computer security, arbitrary code execution (ACE) is an attacker's ability to run any commands or code of the attacker's choice on a target machine or in a target process. An arbitrary code execution vulnerability is a security flaw in software or hardware allowing arbitrary code execution. A program that is designed to exploit such a vulnerability is called an arbitrary code execution exploit. The ability to trigger arbitrary code execution over a network (especially via a wide-area network such as the Internet) is often referred to as remote code execution (RCE or RCX). Arbitrary code execution signifies that if someone sends a specially designed set of data to a computer, they can make it do whatever they want. Even though this particular weakness may not cause actual problems in the real world, researchers have discussed whether it suggests a natural tendency for computers to have vulnerabilities that allow unauthorized code execution. Vulnerability types There are a n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker
A hacker is a person skilled in information technology who achieves goals and solves problems by non-standard means. The term has become associated in popular culture with a security hackersomeone with knowledge of bug (computing), bugs or exploit (computer security), exploits to break into computer systems and access data which would otherwise be inaccessible to them. In a positive connotation, though, hacking can also be utilized by legitimate figures in legal situations. For example, law enforcement agencies sometimes use hacking techniques to collect evidence on criminals and other malicious actors. This could include using anonymity tools (such as a Virtual private network, VPN or the dark web) to mask their identities online and pose as criminals. Hacking can also have a broader sense of any roundabout solution to a problem, or programming and hardware development in general, and hacker culture has spread the term's broader usage to the general public even outside the pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |