|
Software Companies Based In Utah
Software consists of computer programs that instruct the execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital computers in the mid-20th century. Early programs were written in the machine language specific to the hardware. The introduction of high-level programming languages in 1958 allowed for more human-readable instructions, making software development easier and more portable across different computer architectures. Software in a programming language is run through a compiler or interpreter to execute on the architecture's hardware. Over time, software has become complex, owing to developments in networking, operating systems, and databases. Software can generally be categorized into two main types: # operating systems, which manage hardware resources and provide services for applications # application software, which performs specific tasks for users The rise of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
JavaScript Code
JavaScript (), often abbreviated as JS, is a programming language and core technology of the World Wide Web, alongside HTML and CSS. Ninety-nine percent of websites use JavaScript on the Client (computing), client side for Web page, webpage behavior. Web browsers have a dedicated JavaScript engine that executes the client Source code, code. These engines are also utilized in some Server (computing), servers and a variety of Application software, apps. The most popular runtime system for non-browser usage is Node.js. JavaScript is a High-level programming language, high-level, often Just-in-time compilation, just-in-time–compiled language that conforms to the ECMAScript standard. It has dynamic typing, Prototype-based programming, prototype-based object-oriented programming, object-orientation, and first-class functions. It is Programming paradigm, multi-paradigm, supporting Event-driven programming, event-driven, functional programming, functional, and imperative programming ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software As A Service
Software as a service (SaaS ) is a cloud computing service model where the provider offers use of application software to a client and manages all needed physical and software resources. SaaS is usually accessed via a web application. Unlike other software delivery models, it separates "the possession and ownership of software from its use". SaaS use began around 2000, and by 2023 was the main form of software application deployment. Unlike most self-hosted software products, only one version of the software exists and only one operating system and configuration is supported. SaaS products typically run on rented infrastructure as a service (IaaS) or platform as a service (PaaS) systems including hardware and sometimes operating systems and middleware, to accommodate rapid increases in usage while providing instant and continuous availability to customers. SaaS customers have the abstraction of limitless computing resources, while economy of scale drives down the cost. Sa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
07R01
7R may refer to: * Kawasaki Ninja ZX-7R, a supersports bike * KRCR-TV, a television station in Redding, California that used the branding of "7R" in the past for its designation in ''TV Guide'' listings * RusLine, IATA airline designator * Sony α7R, a full-frame E-mount digital mirrorless camera * Yaesu VX-7R, a handheld amateur radio transceiver See also * R7 (other) {{Letter-NumberCombDisambig ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vulnerability (computing)
Vulnerabilities are flaws or weaknesses in a system's design, implementation, or management that can be exploited by a malicious actor to compromise its security. Despite a system administrator's best efforts to achieve complete correctness, virtually all hardware and software contain bugs where the system does not behave as expected. If the bug could enable an attacker to compromise the confidentiality, integrity, or availability of system resources, it can be considered a vulnerability. Insecure software development practices as well as design factors such as complexity can increase the burden of vulnerabilities. Vulnerability management is a process that includes identifying systems and prioritizing which are most important, scanning for vulnerabilities, and taking action to secure the system. Vulnerability management typically is a combination of remediation, mitigation, and acceptance. Vulnerabilities can be scored for severity according to the Common Vulnerability S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Bug
A software bug is a design defect ( bug) in computer software. A computer program with many or serious bugs may be described as ''buggy''. The effects of a software bug range from minor (such as a misspelled word in the user interface) to severe (such as frequent crashing). In 2002, a study commissioned by the US Department of Commerce's National Institute of Standards and Technology concluded that "software bugs, or errors, are so prevalent and so detrimental that they cost the US economy an estimated $59 billion annually, or about 0.6 percent of the gross domestic product". Since the 1950s, some computer systems have been designed to detect or auto-correct various software errors during operations. History Terminology ''Mistake metamorphism'' (from Greek ''meta'' = "change", ''morph'' = "form") refers to the evolution of a defect in the final stage of software deployment. Transformation of a ''mistake'' committed by an analyst in the early stages of the softw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data or the unlawful use, Data breach, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g., electronic or physical, tangible (e.g., Document, paperwork), or intangible (e.g., knowledge). Information security's primary focus is the balanced protection of data confidentiality, data integrity, integrity, and data availability, availability (also known as the 'CIA' triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process. To stand ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Quality Assurance
Software quality assurance (SQA) is a means and practice of monitoring all software engineering processes, methods, and work products to ensure compliance against defined standards. It may include ensuring conformance to standards or models, such as ISO/IEC 9126 (now superseded by ISO 25010), SPICE or CMMI. It includes standards and procedures that managers, administrators or developers may use to review and audit software products and activities to verify that the software meets quality criteria which link to standards. SQA encompasses the entire software development process, including requirements engineering, software design, coding, code reviews, source code control, software configuration management, testing, release management and software integration. It is organized into goals, commitments, abilities, activities, measurements, verification and validation. Purpose SQA involves a three-pronged approach: * Organization-wide policies, procedures and standar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
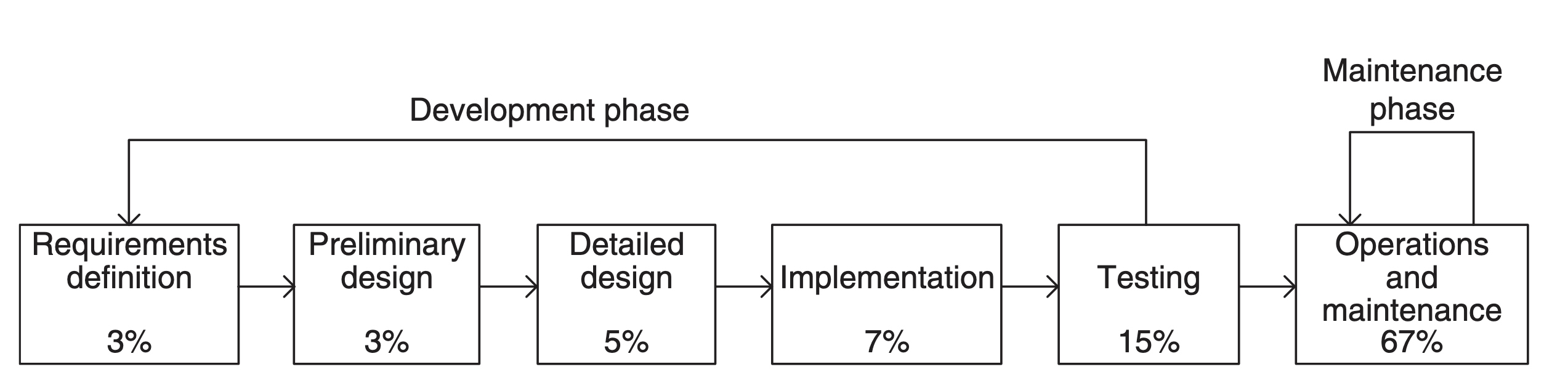
Software Maintenance
Software maintenance is the modification of software after delivery. Software maintenance is often considered lower skilled and less rewarding than new development. As such, it is a common target for outsourcing or offshoring. Usually, the team developing the software is different from those who will be maintaining it. The developers lack an incentive to write the code to be easily maintained. Software is often delivered incomplete and almost always contains some bugs that the maintenance team must fix. Software maintenance often initially includes the development of new functionality, but as the product nears the end of its lifespan, maintenance is reduced to the bare minimum and then cut off entirely before the product is withdrawn. Each maintenance cycle begins with a change request typically originating from an end user. That request is evaluated and if it is decided to implement it, the programmer studies the existing code to understand how it works before implementing the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Release Life Cycle
The software release life cycle is the process of developing, testing, and distributing a software product (e.g., an operating system). It typically consists of several stages, such as pre-alpha, alpha, beta, and release candidate, before the final version, or "gold", is released to the public. Pre-alpha refers to the early stages of development, when the software is still being designed and built. Alpha testing is the first phase of formal testing, during which the software is tested internally using White-box testing, white-box techniques. Beta testing is the next phase, in which the software is tested by a larger group of users, typically outside of the organization that developed it. The beta phase is focused on reducing impacts on users and may include usability testing. After beta testing, the software may go through one or more release candidate phases, in which it is refined and tested further, before the final version is released. Some software, particularly in the int ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Testing
Software testing is the act of checking whether software satisfies expectations. Software testing can provide objective, independent information about the Quality (business), quality of software and the risk of its failure to a User (computing), user or sponsor. Software testing can determine the Correctness (computer science), correctness of software for specific Scenario (computing), scenarios but cannot determine correctness for all scenarios. It cannot find all software bug, bugs. Based on the criteria for measuring correctness from an test oracle, oracle, software testing employs principles and mechanisms that might recognize a problem. Examples of oracles include specifications, Design by Contract, contracts, comparable products, past versions of the same product, inferences about intended or expected purpose, user or customer expectations, relevant standards, and applicable laws. Software testing is often dynamic in nature; running the software to verify actual output ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Programming
Computer programming or coding is the composition of sequences of instructions, called computer program, programs, that computers can follow to perform tasks. It involves designing and implementing algorithms, step-by-step specifications of procedures, by writing source code, code in one or more programming languages. Programmers typically use high-level programming languages that are more easily intelligible to humans than machine code, which is directly executed by the central processing unit. Proficient programming usually requires expertise in several different subjects, including knowledge of the Domain (software engineering), application domain, details of programming languages and generic code library (computing), libraries, specialized algorithms, and Logic#Formal logic, formal logic. Auxiliary tasks accompanying and related to programming include Requirements analysis, analyzing requirements, Software testing, testing, debugging (investigating and fixing problems), imple ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
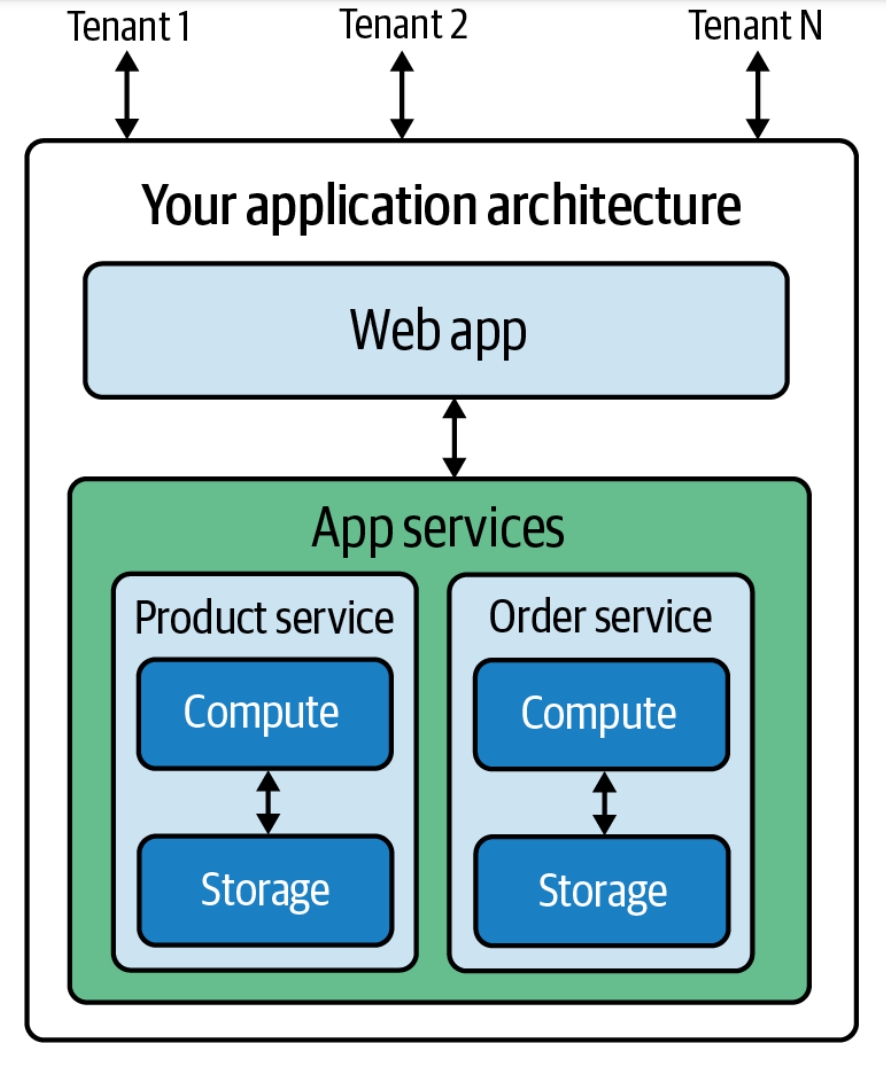
Software Design
Software design is the process of conceptualizing how a software system will work before it is implemented or modified. Software design also refers to the direct result of the design process the concepts of how the software will work which consists of both design documentation and undocumented concepts. Software design usually is directed by goals for the resulting system and involves problem-solving and planning including both high-level software architecture and low-level component and algorithm design. In terms of the waterfall development process, software design is the activity of following requirements specification and before coding. General process The design process enables a designer to model various aspects of a software system before it exists. Creativity, past experience, a sense of what makes "good" software, and a commitment to quality are success factors for a competent design. However, the design process is not always a straightforward procedure ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |