|
Chain Of Trust
In computer security, a chain of trust is established by validating each component of hardware and software from the end entity up to the root certificate. It is intended to ensure that only trusted software and hardware can be used while still retaining flexibility. Introduction A chain of trust is designed to allow multiple users to create and use the software on the system, which would be more difficult if all the keys were stored directly in hardware. It starts with hardware that will only boot from software that is digitally signed ( bootloader). The signing authority will only sign boot programs that enforce security, such as only running programs that are themselves signed, or only allowing signed code to have access to certain features of the machine. This process may continue for several layers. This process results in a chain of trust. The final software can be trusted to have certain properties because if it had been illegally modified its signature would be inva ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chain Of Trust V2
A chain is a serial assembly of connected pieces, called links, typically made of metal, with an overall character similar to that of a rope in that it is flexible and curved in compression but linear, rigid, and load-bearing in tension. A chain may consist of two or more links. Chains can be classified by their design, which can be dictated by their use: * Those designed for lifting, such as when used with a hoist; for pulling; or for securing, such as with a bicycle lock, have links that are torus-shaped, which make the chain flexible in two dimensions (the fixed third dimension being a chain's length). Small chains serving as jewellery are a mostly decorative analogue of such types. * Those designed for transferring power in machines have links designed to mesh with the teeth of the sprockets of the machine, and are flexible in only one dimension. They are known as roller chains, though there are also non-roller chains such as block chains. Two distinct chains can be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Hardware
Computer hardware includes the physical parts of a computer, such as the central processing unit (CPU), random-access memory (RAM), motherboard, computer data storage, graphics card, sound card, and computer case. It includes external devices such as a Computer monitor, monitor, Computer mouse, mouse, Computer keyboard, keyboard, and Computer speakers, speakers. By contrast, software is a set of written instructions that can be stored and run by hardware. Hardware derived its name from the fact it is ''Hardness, hard'' or rigid with respect to changes, whereas software is ''soft'' because it is easy to change. Hardware is typically directed by the software to execute any command or Instruction (computing), instruction. A combination of hardware and software forms a usable computing system, although Digital electronics, other systems exist with only hardware. History Early computing devices were more complicated than the ancient abacus date to the seventeenth century. French ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software
Software consists of computer programs that instruct the Execution (computing), execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital computers in the mid-20th century. Early programs were written in the machine language specific to the hardware. The introduction of high-level programming languages in 1958 allowed for more human-readable instructions, making software development easier and more portable across different computer architectures. Software in a programming language is run through a compiler or Interpreter (computing), interpreter to execution (computing), execute on the architecture's hardware. Over time, software has become complex, owing to developments in Computer network, networking, operating systems, and databases. Software can generally be categorized into two main types: # operating systems, which manage hardware resources and provide services for applicat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bootloader
A bootloader, also spelled as boot loader or called bootstrap loader, is a computer program that is responsible for booting a computer and booting an operating system. If it also provides an interactive menu with multiple boot choices then it's often called a boot manager. When a computer is turned off, its softwareincluding operating systems, application code, and dataremains stored on non-volatile memory. When the computer is powered on, it typically does not have an operating system or its loader in random-access memory (RAM). The computer first executes a relatively small program stored in the boot ROM, which is read-only memory (ROM, and later EEPROM, NOR flash) along with some needed data, to initialize hardware devices such as CPU, motherboard, memory, storage and other I/O devices, to access the nonvolatile device (usually block device, e.g., NAND flash) or devices from which the operating system programs and data can be loaded into RAM. Some earlier computer systems, u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trust Anchor
In cryptographic systems with hierarchical structure, a trust anchor is an authoritative entity for which trust is assumed and not derived. In the X.509 architecture, a root certificate would be the trust anchor from which the whole chain of trust is derived. The trust anchor must be in the possession of the trusting party beforehand to make any further certificate path validation possible. Most operating systems provide a built-in list of self-signed root certificates to act as trust anchors for applications. The Firefox web browser also provides its own list of trust anchors. The end-user of an operating system or web browser is implicitly trusting in the correct operation of that software, and the software manufacturer in turn is delegating trust for certain cryptographic operations to the certificate authorities responsible for the root certificates. See also * Web of trust In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
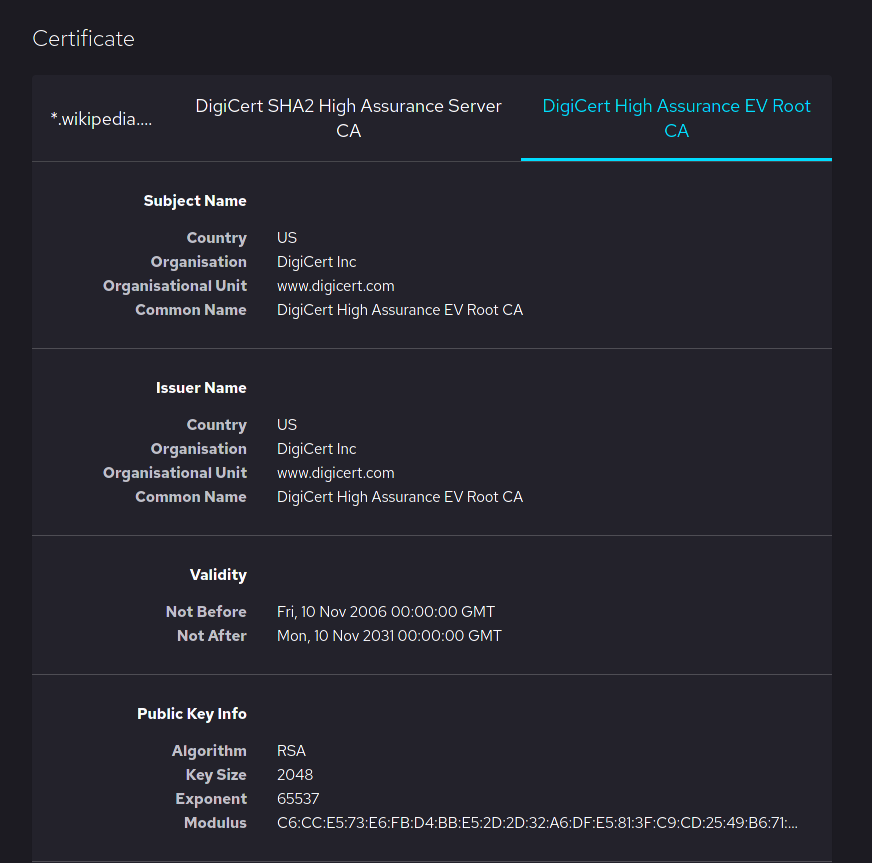
Root Certificate
In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed (and it is possible for a certificate to have multiple trust paths, say if the certificate was issued by a root that was cross-signed) and form the basis of an X.509-based public key infrastructure (PKI). Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string (). For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates. A certificate authority can issue multiple certificates in the form of a tree structure. A root certificate is the top-most certificate of the tree, the private key which is used to "sign" other certificates. All certificates signed by the root certificate, with the "CA" field set to true, inher ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intermediate Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Root Of Trust
In cryptographic systems with hierarchical structure, a trust anchor is an authoritative entity for which trust is assumed and not derived. In the X.509 architecture, a root certificate would be the trust anchor from which the whole chain of trust is derived. The trust anchor must be in the possession of the trusting party beforehand to make any further certificate path validation possible. Most operating systems provide a built-in list of self-signed root certificates to act as trust anchors for applications. The Firefox Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements curr ... web browser also provides its own list of trust anchors. The end-user of an operating system or web browser is implicitly trusting in the correct operation of that software, and the software manufacturer in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Of Trust
In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority (or a hierarchy of such). As with computer networks, there are many independent webs of trust, and any user (through their public key certificate) can be a part of, and a link between, multiple webs. The web of trust concept was first put forth by PGP creator Phil Zimmermann in 1992 in the manual for PGP version 2.0: Note the use of the word emergence in this context. The web of trust makes use of the concept of emergence. Operation of a web of trust All OpenPGP-compliant implementations include a certificate vetting scheme to assist with this; its operation has been termed a web of trust. OpenPGP certificates (which incl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |