|
Antivirus
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, Spam (electronic), spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the "Creeper (program), Creeper virus". This computer virus infected Digital Equipment Corporation's (Digital Equipment Corporation, DEC) PDP-10 mainframe computers running the TENEX (operating system), TENEX operating system. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ESET NOD32
ESET NOD32 Antivirus, commonly known as NOD32, is an antivirus software package made by the Slovakia, Slovak company ESET. ESET NOD32 Antivirus is sold in two editions, Home Edition and Business Edition. The Business Edition packages add ESET Remote Administrator allowing for server deployment and management, mirroring of threat signature database updates and the ability to install on Microsoft Windows Server operating systems. History NOD32 The acronym NOD stands for ''Nemocnica na Okraji Disku'' ("Hospital at the boot sector, end of the disk"), a pun related to the Czechoslovakia, Czechoslovak medical drama series ''Hospital at the End of the City, Nemocnice na kraji města'' (''Hospital at the End of the City''). The first version of NOD32 called NOD-ICE was a DOS-based program. It was created in 1987 by Miroslav Trnka and Peter Paško at the time when computer viruses started to become increasingly prevalent on PCs running DOS. Due to the limitations of the OS (lack of Co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee VirusScan
McAfee Antivirus is an antivirus software created and maintained by McAfee (formerly known as Intel Security, and Network Associates prior to that). Originally marketed as a standalone product, it is also bundled with McAfee Antivirus Plus, McAfee Internet Security, McAfee Total Protection, McAfee McAfee+ Premium, McAfee+ Advanced, McAfee+ Ultimate, and McAfee Business Protection. McAfee+ provides all-in-one protection for a user's personal info, privacy, and all their devices. It supports Windows, Mac, iOS, Android and ChromeOS devices and includes integrated antivirus, firewall and safe browsing capabilities as well as identity and privacy protection with identity monitoring, credit and financial monitoring, identity theft coverage and restoration,secure VPN, Online Account Cleanup, Personal Data Cleanup, Social Media Privacy Manager, and McAfee's AI-powered Scam Detector. VirusScan Enterprise Before McAfee completed the sale of its enterprise business it also produced a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of malware that, when executed, replicates itself by modifying other computer programs and Code injection, inserting its own Computer language, code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a Computer program, host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. By contrast, a computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the Computer program, host program, but can run independently and actively carry out attacks. Virus writers use social engineering (security), social engineering deceptions and exploit detailed knowledge of vulnerability (computing), security vulnerabilities to initially infect systems an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
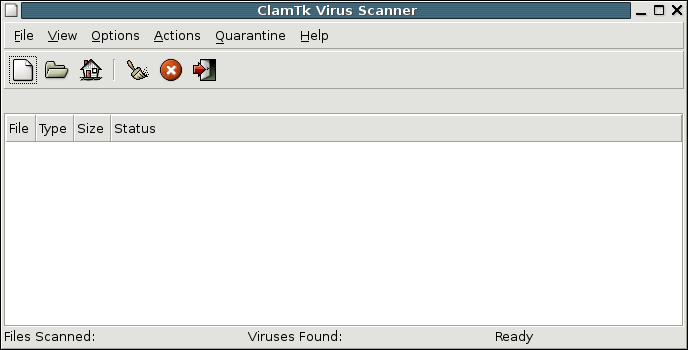
ClamTk 5
ClamTk is a free and open-source graphical interface for the ClamAV command-line antivirus software program for Linux desktop users. It provides both on-demand and scheduled scanning. The project was started by Dave Mauroni in February 2004. As of April 2024, the program is no longer maintained. ClamTk was originally written using the Tk widget toolkit, for which it is named, but it was later re-written in Perl, using the GTK toolkit. The interface has evolved considerably over time and recent versions are quite different than early releases, adding features and changing the interface presentation. It is dual-licensed under the GNU General Public License version 1 or later, and the Artistic License. Features The ClamTk interface allows scanning of single files or directories. It can be configured for recursive scans, scanning all sub-directories, for whitelists, to scan for potentially unwanted applications (PUAs), to exclude hidden files, or large files over 20 MB. In 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
John McAfee
John David McAfee ( ; 18 September 1945 – 23 June 2021) was a British and American computer programmer, businessman, and two-time presidential candidate who unsuccessfully sought the Libertarian Party (United States), Libertarian Party nomination for president of the United States 2016 Libertarian National Convention, in 2016 and 2020 Libertarian National Convention, in 2020. In 1987, he wrote the first commercial Antivirus software, anti-virus software, founding McAfee, McAfee Associates to sell his creation. He resigned in 1994 and sold his remaining stake in the company. McAfee became the company's most vocal critic in later years, urging consumers to uninstall the company's anti-virus software, which he characterized as bloatware. He disavowed the company's continued use of his name in branding, a practice that has persisted in spite of a short-lived corporate rebrand attempt under Intel ownership. McAfee's fortunes plummeted in the 2008 financial crisis. After leaving McAf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau of ''malicious software'')Tahir, R. (2018)A study on malware and malware detection techniques . ''International Journal of Education and Management Engineering'', ''8''(2), 20. is any software intentionally designed to cause disruption to a computer, server (computing), server, Client (computing), client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. Researchers tend to classify malware into one or more sub-types (i.e. computer viruses, Computer worm, worms, Trojan horse (computing), Trojan horses, logic bombs, ransomware, spyware, adware, rogue software, Wiper (malware), wipers and keyloggers). Malware poses serious problems to individuals and businesses on the Internet. According to NortonLifeLock, Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 66 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American proprietary software company focused on online protection for consumers worldwide headquartered in San Jose, California. The company was purchased by Intel in February 2011; with this acquisition, it became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a Minority interest, 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it Public company#Privatization, private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
G Data Software
G Data CyberDefense AG (until September 2019 ''G Data Software AG'') is a German software company that focuses on computer security. The company was founded in 1985 and is headquartered in Bochum. They are known for being the creators of the world's first antivirus software. G Data uses multiple scanning engines; one is developed in-house and the other is the Bitdefender engine. G Data provides several security products that are targeted at home and business markets. The company has a North American subsidiary located in Newark, Delaware. History Antivirus Programs & Cyber Security (1985–2006) G Data was founded in Bochum, Germany, in 1985. The company introduced its first computer security product Anti-Virus Kit (AVK) in 1988 for Atari ST. In 1990, this program was given a graphical user interface for MS-DOS for the first time. In 1993, G Data developed the software GeoRoute, the first route planner with intelligent mapping. Beside focus on the securit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bernd Fix
Bernd Fix (born 19 March 1962 in Wittingen, Lower Saxony) is a German hacker and computer security expert. Biography After final secondary-school examination from Gymnasium Hankensbüttel in 1981, Bernd Fix studied Astrophysics and Philosophy at the universities of Göttingen and Heidelberg. He received his diplom for a work in the field of theoretical astrophysics in 1989. From 1998 Fix was living and working in Switzerland; he moved to Berlin in 2014. In 1986 Fix joined the Chaos Computer Club (CCC) in Hamburg and started to work on computer security issues, focussing on computer virus research. He published a first demo virus (Rushhour) in autumn 1986 in the Datenschleuder #17, the hacker magazine edited by the CCC. He also contributed results of his research to the book "Computer Viruses" by Ralf Burger. From 1987 to 1989 Fix was one of the spokespersons for the Chaos Computer Club and author for the " Hacker Bible 2". In 1987 he devised a method to neutralize the Vie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Elk Cloner
Elk Cloner is one of the first known microcomputer viruses that spread "in the wild", i.e., outside the computer system or laboratory in which it was written. It attached itself to the Apple II operating system and spread by floppy disk. It was written around 1982 by programmer and entrepreneur Rich Skrenta as a 15-year-old high school student, originally as a joke, and put onto a game disk. Infection and symptoms Elk Cloner spread by infecting the Apple DOS 3.3 operating system using a technique now known as a boot sector virus. It was attached to a program being shared on a disk (usually a game). At set numbers of times the disk's program had been run (all multiples of 5), it would cause various strange behaviors of the Apple II, many requiring a reboot to correct. Most noticeably, every 50th time the program was run, instead of executing normally, it would change to a blank screen that displayed a poem about the virus. If a computer booted from an infected floppy disk, a cop ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the Global network, global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a internetworking, network of networks that consists of Private network, private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, Wireless network, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and Web application, applications of the World Wide Web (WWW), email, electronic mail, internet telephony, streaming media and file sharing. The origins of the Internet date back to research that enabled the time-sharing of computer resources, the development of packet switching in the 1960s and the design of computer networks for data communication. The set of rules (communication protocols) to enable i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (electronic)
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, non-commercial proselytizing, or any prohibited purpose (especially phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: messaging spam, instant messaging spam, Newsgroup spam, Usenet newsgroup spam, spamdexing, Web search engine spam, spam in blogs, wiki spam, classified advertising, online classified ads spam, mobile phone spam, mobile phone messaging spam, Forum spam, Internet forum spam, junk fax, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam (food), Spam, a luncheon meat, by way of a Spam (Monty Python sketch), Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |