Session initiation protocol on:
[Wikipedia]
[Google]
[Amazon]
The Session Initiation Protocol (SIP) is a signaling protocol used for initiating, maintaining, and terminating
 SIP is only involved in the signaling operations of a media communication session and is primarily used to set up and terminate voice or video calls. SIP can be used to establish two-party (
SIP is only involved in the signaling operations of a media communication session and is primarily used to set up and terminate voice or video calls. SIP can be used to establish two-party (sip:username@domainname '' or ''sip:username@hostport '', where ''domainname'' requires DNS SRV records to locate the servers for SIP domain while ''hostport'' can be an
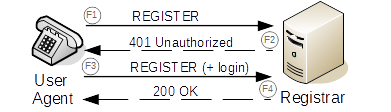 A registrar is a SIP endpoint that provides a location service. It accepts REGISTER requests, recording the address and other parameters from the user agent. For subsequent requests, it provides an essential means to locate possible communication peers on the network. The location service links one or more IP addresses to the SIP URI of the registering agent. Multiple user agents may register for the same URI, with the result that all registered user agents receive the calls to the URI.
SIP registrars are logical elements and are often co-located with SIP proxies. To improve network scalability, location services may instead be located with a redirect server.
A registrar is a SIP endpoint that provides a location service. It accepts REGISTER requests, recording the address and other parameters from the user agent. For subsequent requests, it provides an essential means to locate possible communication peers on the network. The location service links one or more IP addresses to the SIP URI of the registering agent. Multiple user agents may register for the same URI, with the result that all registered user agents receive the calls to the URI.
SIP registrars are logical elements and are often co-located with SIP proxies. To improve network scalability, location services may instead be located with a redirect server.
 Session border controllers (SBCs) serve as middleboxes between user agents and SIP servers for various types of functions, including network topology hiding and assistance in
Session border controllers (SBCs) serve as middleboxes between user agents and SIP servers for various types of functions, including network topology hiding and assistance in
IANA: SIP Parameters
IANA: SIP Event Types Namespace
{{Authority control VoIP protocols Videotelephony Application layer protocols
communication session
In computer science and networking in particular, a session is a time-delimited two-way link, a practical (relatively high) layer in the tcp/ip protocol enabling interactive expression and information exchange between two or more communication d ...
s that include voice, video and messaging applications. SIP is used in Internet telephony
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms Internet ...
, in private IP telephone systems, as well as mobile phone calling over LTE (VoLTE
Voice over LTE (VoLTE) is an LTE high-speed wireless communication standard for mobile phones and data terminals, including Internet of things (IoT) devices and wearables. VoLTE has up to three times more voice and data capacity than older 3G ...
).
The protocol defines the specific format of messages exchanged and the sequence of communications for cooperation of the participants. SIP is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol
The Hypertext Transfer Protocol (HTTP) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information systems. HTTP is the foundation of data communication for the World Wide We ...
(HTTP) and the Simple Mail Transfer Protocol (SMTP). A call established with SIP may consist of multiple media streams, but no separate streams are required for applications, such as text messaging, that exchange data as payload in the SIP message.
SIP works in conjunction with several other protocols that specify and carry the session media. Most commonly, media type and parameter negotiation and media setup are performed with the Session Description Protocol (SDP), which is carried as payload in SIP messages. SIP is designed to be independent of the underlying transport layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-e ...
protocol and can be used with the User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in packets) to other hosts on an Internet Protocol (IP) netwo ...
(UDP), the Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonl ...
(TCP), and the Stream Control Transmission Protocol
The Stream Control Transmission Protocol (SCTP) is a computer networking communications protocol in the transport layer of the Internet protocol suite. Originally intended for Signaling System 7 (SS7) message transport in telecommunication, the p ...
(SCTP). For secure transmissions of SIP messages over insecure network links, the protocol may be encrypted with Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securi ...
(TLS). For the transmission of media streams (voice, video) the SDP payload carried in SIP messages typically employs the Real-time Transport Protocol (RTP) or the Secure Real-time Transport Protocol (SRTP).
History
SIP was originally designed byMark Handley
Mark Handley is a playwright and screenwriter.
In 1977, he and his wife moved to the Pacific Northwest where they lived in isolation in a log cabin that they built themselves. He is best known for his play ''Idioglossia
An idioglossia (from ...
, Henning Schulzrinne, Eve Schooler and Jonathan Rosenberg in 1996 to facilitate establishing multicast
In computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused wi ...
multimedia sessions on the Mbone. The protocol was standardized as in 1999. In November 2000, SIP was accepted as a 3GPP signaling protocol and permanent element of the IP Multimedia Subsystem
The IP Multimedia Subsystem or IP Multimedia Core Network Subsystem (IMS) is a standardised architectural framework for delivering IP multimedia services. Historically, mobile phones have provided voice call services over a circuit-switched-styl ...
(IMS) architecture for IP-based streaming multimedia services in cellular network
A cellular network or mobile network is a communication network where the link to and from end nodes is wireless. The network is distributed over land areas called "cells", each served by at least one fixed-location transceiver (typically th ...
s. In June 2002 the specification was revised in and various extensions and clarifications have been published since.
SIP was designed to provide a signaling and call setup protocol for IP-based communications supporting the call processing functions and features present in the public switched telephone network
The public switched telephone network (PSTN) provides infrastructure and services for public telecommunication. The PSTN is the aggregate of the world's circuit-switched telephone networks that are operated by national, regional, or local telep ...
(PSTN) with a vision of supporting new multimedia applications. It has been extended for video conferencing, streaming media
Streaming media is multimedia that is delivered and consumed in a continuous manner from a source, with little or no intermediate storage in network elements. ''Streaming'' refers to the delivery method of content, rather than the content i ...
distribution, instant messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and tri ...
, presence information In computer and telecommunications networks, presence information is a status indicator that conveys ability and willingness of a potential communication partner—for example a user—to communicate. A user's client provides presence information ...
, file transfer File transfer is the transmission of a computer file through a communication channel from one computer system to another. Typically, file transfer is mediated by a communications protocol. In the history of computing, numerous file transfer protoco ...
, Internet fax and online game
An online game is a video game that is either partially or primarily played through the Internet or any other computer network available. Online games are ubiquitous on modern gaming platforms, including PCs, consoles and mobile devices, and s ...
s.
SIP is distinguished by its proponents for having roots in the Internet community rather than in the telecommunications industry. SIP has been standardized primarily by the Internet Engineering Task Force
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements an ...
(IETF), while other protocols, such as H.323
H.323 is a recommendation from the ITU Telecommunication Standardization Sector (ITU-T) that defines the protocols to provide audio-visual communication sessions on any packet network. The H.323 standard addresses call signaling and control, mu ...
, have traditionally been associated with the International Telecommunication Union
The International Telecommunication Union is a specialized agency of the United Nations responsible for many matters related to information and communication technologies. It was established on 17 May 1865 as the International Telegraph Unio ...
(ITU).
Protocol operation
unicast
Unicast is data transmission from a single sender (red) to a single receiver (green). Other devices on the network (yellow) do not participate in the communication.
In computer networking, unicast is a one-to-one transmission from one point in ...
) or multiparty (multicast
In computer networking, multicast is group communication where data transmission is addressed to a group of destination computers simultaneously. Multicast can be one-to-many or many-to-many distribution. Multicast should not be confused wi ...
) sessions. It also allows modification of existing calls. The modification can involve changing addresses or ports, inviting more participants, and adding or deleting media streams. SIP has also found applications in messaging applications, such as instant messaging, and event subscription and notification.
SIP works in conjunction with several other protocols that specify the media format and coding and that carry the media once the call is set up. For call setup, the body of a SIP message contains a Session Description Protocol (SDP) data unit, which specifies the media format, codec and media communication protocol. Voice and video media streams are typically carried between the terminals using the Real-time Transport Protocol (RTP) or Secure Real-time Transport Protocol (SRTP).
Every resource of a SIP network, such as user agents, call routers, and voicemail boxes, are identified by a Uniform Resource Identifier
A Uniform Resource Identifier (URI) is a unique sequence of characters that identifies a logical or physical resource used by web technologies. URIs may be used to identify anything, including real-world objects, such as people and places, conc ...
(URI). The syntax of the URI follows the general standard syntax also used in Web services and e-mail. The URI scheme used for SIP is ''sip'' and a typical SIP URI has the form ''IP address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface ident ...
or a fully qualified domain name of the host and port. If secure transmission is required, the scheme ''sips'' is used.
SIP employs design elements similar to the HTTP request and response transaction model. Each transaction consists of a client request that invokes a particular method or function on the server and at least one response. SIP reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text-based format.
SIP can be carried by several transport layer
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-e ...
protocols including Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonl ...
(TCP), User Datagram Protocol
In computer networking, the User Datagram Protocol (UDP) is one of the core communication protocols of the Internet protocol suite used to send messages (transported as datagrams in packets) to other hosts on an Internet Protocol (IP) netwo ...
(UDP), and Stream Control Transmission Protocol
The Stream Control Transmission Protocol (SCTP) is a computer networking communications protocol in the transport layer of the Internet protocol suite. Originally intended for Signaling System 7 (SS7) message transport in telecommunication, the p ...
(SCTP). SIP clients typically use TCP or UDP on port numbers 5060 or 5061 for SIP traffic to servers and other endpoints. Port 5060 is commonly used for non-encrypted signaling traffic whereas port 5061 is typically used for traffic encrypted with Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securi ...
(TLS).
SIP-based telephony networks often implement call processing features of Signaling System 7
Signalling System No. 7 (SS7) is a set of telephony signaling protocols developed in 1975, which is used to set up and tear down telephone calls in most parts of the world-wide public switched telephone network (PSTN). The protocol also perf ...
(SS7), for which special SIP protocol extensions exist, although the two protocols themselves are very different. SS7 is a centralized protocol, characterized by a complex central network architecture and dumb endpoints (traditional telephone handsets). SIP is a client-server protocol of equipotent peers. SIP features are implemented in the communicating endpoints, while the traditional SS7 architecture is in use only between switching centers.
Network elements
The network elements that use the Session Initiation Protocol for communication are called ''SIP user agents''. Each ''user agent'' (UA) performs the function of a ''user agent client'' (UAC) when it is requesting a service function, and that of a ''user agent server'' (UAS) when responding to a request. Thus, any two SIP endpoints may in principle operate without any intervening SIP infrastructure. However, for network operational reasons, for provisioning public services to users, and for directory services, SIP defines several specific types of network server elements. Each of these service elements also communicates within the client-server model implemented in user agent clients and servers.User agent
A user agent is a logical network endpoint that sends or receives SIP messages and manages SIP sessions. User agents have client and server components. The user agent client (UAC) sends SIP requests. The user agent server (UAS) receives requests and returns a SIP response. Unlike other network protocols that fix the roles of client and server, e.g., in HTTP, in which a web browser only acts as a client, and never as a server, SIP requires both peers to implement both roles. The roles of UAC and UAS only last for the duration of a SIP transaction. A SIP phone is anIP phone
A VoIP phone or IP phone uses voice over IP technologies for placing and transmitting telephone calls over an IP network, such as the Internet. This is in contrast to a standard phone which uses the traditional public switched telephone network ...
that implements client and server functions of a SIP user agent and provides the traditional call functions of a telephone, such as dial, answer, reject, call hold, and call transfer. SIP phones may be implemented as a hardware device or as a softphone. As vendors increasingly implement SIP as a standard telephony platform, the distinction between hardware-based and software-based SIP phones is blurred and SIP elements are implemented in the basic firmware functions of many IP-capable communications devices such as smartphone
A smartphone is a portable computer device that combines mobile telephone and computing functions into one unit. They are distinguished from feature phones by their stronger hardware capabilities and extensive mobile operating systems, whi ...
s.
In SIP, as in HTTP, the user agent
In computing, a user agent is any software, acting on behalf of a user, which "retrieves, renders and facilitates end-user interaction with Web content". A user agent is therefore a special kind of software agent.
Some prominent examples of us ...
may identify itself using a message header field (''User-Agent''), containing a text description of the software, hardware, or the product name. The user agent field is sent in request messages, which means that the receiving SIP server can evaluate this information to perform device-specific configuration or feature activation. Operators of SIP network elements sometimes store this information in customer account portals, where it can be useful in diagnosing SIP compatibility problems or in the display of service status.
Proxy server
A proxy server is a network server with UAC and UAS components that functions as an intermediary entity for the purpose of performing requests on behalf of other network elements. A proxy server primarily plays the role of call routing; it sends SIP requests to another entity closer to the destination. Proxies are also useful for enforcing policy, such as for determining whether a user is allowed to make a call. A proxy interprets, and, if necessary, rewrites specific parts of a request message before forwarding it. SIP proxy servers that route messages to more than one destination are called forking proxies. The forking of a SIP request establishes multiple dialogs from the single request. Thus, a call may be answered from one of multiple SIP endpoints. For identification of multiple dialogs, each dialog has an identifier with contributions from both endpoints.Redirect server
A redirect server is a user agent server that generates 3xx (redirection) responses to requests it receives, directing the client to contact an alternate set of URIs. A redirect server allows proxy servers to direct SIP session invitations to external domains.Registrar
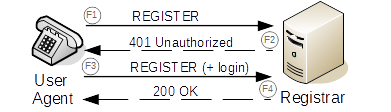 A registrar is a SIP endpoint that provides a location service. It accepts REGISTER requests, recording the address and other parameters from the user agent. For subsequent requests, it provides an essential means to locate possible communication peers on the network. The location service links one or more IP addresses to the SIP URI of the registering agent. Multiple user agents may register for the same URI, with the result that all registered user agents receive the calls to the URI.
SIP registrars are logical elements and are often co-located with SIP proxies. To improve network scalability, location services may instead be located with a redirect server.
A registrar is a SIP endpoint that provides a location service. It accepts REGISTER requests, recording the address and other parameters from the user agent. For subsequent requests, it provides an essential means to locate possible communication peers on the network. The location service links one or more IP addresses to the SIP URI of the registering agent. Multiple user agents may register for the same URI, with the result that all registered user agents receive the calls to the URI.
SIP registrars are logical elements and are often co-located with SIP proxies. To improve network scalability, location services may instead be located with a redirect server.
Session border controller
 Session border controllers (SBCs) serve as middleboxes between user agents and SIP servers for various types of functions, including network topology hiding and assistance in
Session border controllers (SBCs) serve as middleboxes between user agents and SIP servers for various types of functions, including network topology hiding and assistance in NAT traversal
Network address translation traversal is a computer networking technique of establishing and maintaining Internet protocol connections across gateways that implement network address translation (NAT).
NAT traversal techniques are required for m ...
. SBCs are an independently engineered solution and are not mentioned in the SIP RFC.
Gateway
Gateways can be used to interconnect a SIP network to other networks, such as the PSTN, which use different protocols or technologies.SIP messages
SIP is a text-based protocol with syntax similar to that of HTTP. There are two different types of SIP messages: requests and responses. The first line of a request has a ''method'', defining the nature of the request, and a Request-URI, indicating where the request should be sent. The first line of a response has a ''response code''.Requests
Requests initiate a functionality of the protocol. They are sent by a user agent client to the server and are answered with one or more SIP responses, which return a result code of the transaction, and generally indicate the success, failure, or other state of the transaction.Responses
Responses are sent by the user agent server indicating the result of a received request. Several classes of responses are recognized, determined by the numerical range of result codes: * 1xx: Provisional responses to requests indicate the request was valid and is being processed. * 2xx: Successful completion of the request. As a response to an INVITE, it indicates a call is established. The most common code is 200, which is an unqualified success report. * 3xx: Call redirection is needed for completion of the request. The request must be completed with a new destination. * 4xx: The request cannot be completed at the server for a variety of reasons, including bad request syntax (code 400). * 5xx: The server failed to fulfill an apparently valid request, including server internal errors (code 500). * 6xx: The request cannot be fulfilled at any server. It indicates a global failure, including call rejection by the destination.Transactions
SIP defines a transaction mechanism to control the exchanges between participants and deliver messages reliably. A transaction is a state of a session, which is controlled by various timers. Client transactions send requests and server transactions respond to those requests with one or more responses. The responses may include provisional responses with a response code in the form ''1xx'', and one or multiple final responses (2xx – 6xx). Transactions are further categorized as either type ''invite'' or type ''non-invite''. Invite transactions differ in that they can establish a long-running conversation, referred to as a ''dialog'' in SIP, and so include an acknowledgment (ACK) of any non-failing final response, e.g., ''200 OK''.Instant messaging and presence
The Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE) is the SIP-based suite of standards forinstant messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and tri ...
and presence information In computer and telecommunications networks, presence information is a status indicator that conveys ability and willingness of a potential communication partner—for example a user—to communicate. A user's client provides presence information ...
. Message Session Relay Protocol In computer networking, the Message Session Relay Protocol (MSRP) is a protocol for transmitting a series of related instant messages in the context of a communications session. An application instantiates the session with the Session Description Pr ...
(MSRP) allows instant message sessions and file transfer.
Conformance testing
The SIP developer community meets regularly at conferences organized by SIP Forum to test interoperability of SIP implementations. The TTCN-3 test specification language, developed by a task force atETSI
The European Telecommunications Standards Institute (ETSI) is an independent, not-for-profit, standardization organization in the field of information and communications. ETSI supports the development and testing of global technical standard ...
(STF 196), is used for specifying conformance tests for SIP implementations.
Performance testing
When developing SIP software or deploying a new SIP infrastructure, it is important to test the capability of servers and IP networks to handle certain call load: number of concurrent calls and number of calls per second. SIP performance tester software is used to simulate SIP and RTP traffic to see if the server and IP network are stable under the call load. The software measures performance indicators like answer delay, answer/seizure ratio, RTPjitter
In electronics and telecommunications, jitter is the deviation from true periodicity of a presumably periodic signal, often in relation to a reference clock signal. In clock recovery applications it is called timing jitter. Jitter is a signific ...
and packet loss
Packet loss occurs when one or more packets of data travelling across a computer network fail to reach their destination. Packet loss is either caused by errors in data transmission, typically across wireless networks, or network congestion.Ku ...
, round-trip delay time
In telecommunications, round-trip delay (RTD) or round-trip time (RTT) is the amount of time it takes for a signal to be sent ''plus'' the amount of time it takes for acknowledgement of that signal having been received. This time delay includes p ...
.
Applications
''SIP connection'' is a marketing term for voice over Internet Protocol (VoIP) services offered by manyInternet telephony service provider An Internet telephony service provider (ITSP) offers digital telecommunications services based on Voice over Internet Protocol (VoIP) that are provisioned via the Internet.
ITSPs provide services to end-users directly or as whole-sale suppliers ...
s (ITSPs). The service provides routing of telephone calls from a client's private branch exchange
A business telephone system is a multiline telephone system typically used in business environments, encompassing systems ranging in technology from the key telephone system (KTS) to the private branch exchange (PBX).
A business telephone syst ...
(PBX) telephone system to the PSTN. Such services may simplify corporate information system infrastructure by sharing Internet access
Internet access is the ability of individuals and organizations to connect to the Internet using computer terminals, computers, and other devices; and to access services such as email and the World Wide Web. Internet access is sold by Interne ...
for voice and data, and removing the cost for Basic Rate Interface (BRI) or Primary Rate Interface (PRI) telephone circuits.
SIP trunking is a similar marketing term preferred for when the service is used to simplify a telecom infrastructure by sharing the carrier access circuit for voice, data, and Internet traffic while removing the need for PRI circuits.
SIP-enabled video surveillance cameras can initiate calls to alert the operator of events, such as the motion of objects in a protected area.
SIP is used in audio over IP
Audio over IP (AoIP) is the distribution of digital audio across an IP network such as the Internet. It is used increasingly to provide high-quality audio feeds over long distances. The application is also known as audio contribution over IP (ACI ...
for broadcasting
Broadcasting is the distribution of audio or video content to a dispersed audience via any electronic mass communications medium, but typically one using the electromagnetic spectrum (radio waves), in a one-to-many model. Broadcasting began wi ...
applications where it provides an interoperable means for audio interfaces from different manufacturers to make connections with one another.
Implementations
The U.S.National Institute of Standards and Technology
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into physical s ...
(NIST), Advanced Networking Technologies Division provides a public-domain Java
Java (; id, Jawa, ; jv, ꦗꦮ; su, ) is one of the Greater Sunda Islands in Indonesia. It is bordered by the Indian Ocean to the south and the Java Sea to the north. With a population of 151.6 million people, Java is the world's mo ...
implementation that serves as a reference implementation for the standard. The implementation can work in proxy server or user agent scenarios and has been used in numerous commercial and research projects. It supports in full and a number of extension RFCs including (event notification) and (reliable provisional responses).
Numerous other commercial and open-source SIP implementations exist. See List of SIP software.
SIP-ISUP interworking
SIP-I, Session Initiation Protocol with encapsulated ISUP, is a protocol used to create, modify, and terminate communication sessions based on ISUP using SIP and IP networks. Services using SIP-I include voice, video telephony, fax and data. SIP-I and SIP-T are two protocols with similar features, notably to allow ISUP messages to be transported over SIP networks. This preserves all of the detail available in the ISUP header. SIP-I was defined by theITU-T
The ITU Telecommunication Standardization Sector (ITU-T) is one of the three sectors (divisions or units) of the International Telecommunication Union (ITU). It is responsible for coordinating standards for telecommunications and Information Co ...
, whereas SIP-T was defined by the IETF
The Internet Engineering Task Force (IETF) is a standards organization for the Internet and is responsible for the technical standards that make up the Internet protocol suite (TCP/IP). It has no formal membership roster or requirements an ...
.
Encryption
Concerns about the security of calls via the public Internet have been addressed by encryption of the SIP protocol for secure transmission. The URI scheme SIPS is used to mandate that SIP communication be secured withTransport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securi ...
(TLS). SIPS URIs take the form sips:user@example.com.
End-to-end encryption of SIP is only possible if there is a direct connection between communication endpoints. While a direct connection can be made via Peer-to-peer SIP
Peer-to-peer SIP (P2P-SIP) is an implementation of a distributed voice over Internet Protocol (VoIP) or instant messaging communications application using a peer-to-peer (P2P) architecture in which session control between communication end points i ...
or via a VPN between the endpoints, most SIP communication involves multiple hops, with the first hop being from a user agent to the user agent's ITSP. For the multiple-hop case, SIPS will only secure the first hop; the remaining hops will normally not be secured with TLS and the SIP communication will be insecure. In contrast, the HTTPS protocol provides end-to-end security as it is done with a direct connection and does not involve the notion of hops.
The media streams (audio and video), which are separate connections from the SIPS signaling stream, may be encrypted using SRTP. The key exchange for SRTP is performed with SDES (), or with ZRTP (). When SDES is used, the keys will be transmitted via insecure SIP unless SIPS is used. One may also add a MIKEY () exchange to SIP to determine session keys for use with SRTP.
See also
* Computer telephony integration (CTI) *Computer-supported telecommunications applications Computer-supported telecommunications applications (CSTA) is an abstraction layer for telecommunications applications. It is independent of underlying protocols. It has a telephone device model that enables CTI applications to work with a wide ran ...
(CSTA)
* H.323
H.323 is a recommendation from the ITU Telecommunication Standardization Sector (ITU-T) that defines the protocols to provide audio-visual communication sessions on any packet network. The H.323 standard addresses call signaling and control, mu ...
protocols H.225.0 and H.245 H.245 is a control channel protocol used with ne.g. H.323 and H.324 communication sessions, and involves the line transmission of non-telephone signals. It also offers the possibility to be tunneled within H.225.0 call signaling messages. This ea ...
* IP Multimedia Subsystem
The IP Multimedia Subsystem or IP Multimedia Core Network Subsystem (IMS) is a standardised architectural framework for delivering IP multimedia services. Historically, mobile phones have provided voice call services over a circuit-switched-styl ...
(IMS)
* Media Gateway Control Protocol
The Media Gateway Control Protocol (MGCP) is a signaling and call control communication protocol used in voice over IP (VoIP) telecommunication systems. It implements the media gateway control protocol architecture for controlling media gate ...
(MGCP)
* Mobile VoIP
* MSCML The Media Server Control Markup Language (MSCML) is a protocol used in conjunction with the Session Initiation Protocol (SIP) to enable the delivery of advanced multimedia conferencing services over IP networks. The MSCML specification has been pu ...
(Media Server Control Markup Language)
* Network convergence
* Rendezvous protocol
* RTP payload formats
* SIGTRAN (Signaling Transport)
* SIP extensions for the IP Multimedia Subsystem
* SIP provider
* Skinny Client Control Protocol (SCCP)
* T.38
T.38 is an ITU recommendation for allowing transmission of fax over IP networks (FoIP) in real time.
History
The T.38 fax relay standard was devised in 1998 as a way to permit faxes to be transported across IP networks between existing Group 3 ...
* XIMSS (XML Interface to Messaging, Scheduling, and Signaling)
Notes
References
* *External links
IANA: SIP Parameters
IANA: SIP Event Types Namespace
{{Authority control VoIP protocols Videotelephony Application layer protocols