International Obfuscated C Code Contest on:
[Wikipedia]
[Google]
[Amazon]
The International Obfuscated C Code Contest (abbreviated IOCCC) is a
' IOCCC. Retrieved 2013-04-08.), or avoiding commonly used constructs in the C programming language in favor of much more obscure ways of achieving the same thing. Contributions have included source code formatted to resemble images, text, etc., after the manner of
B,i,y,u,b,I 11*G=I,x=10,z=15,M=1e4;X(w,c,h,e,S,s)main()
#define _ -F<00, , --F-OO--;
int F=00,OO=00;main()F_OO()
(This entry was written in
aerojockey.com. Retrieved 2013-04-08. as listed and described in ''Calculated Bets: Computers, Gambling, and Mathematical Modeling to Win'' (2001) and shown below:
#include
#include
#include
#include
double L ,o ,P
,_=dt,T,Z,D=1,d,
s 99E,h= 8,I,
J,K,w 99M,m,O
,n 99j=33e-3,i=
1E3,r,t, u,v ,W,S=
74.5,l=221,X=7.26,
a,B,A=32.2,c, F,H;
int N,q, C, y,p,U;
Window z; char f 2 ; GC k; main()
 This program needs the following command line on a Linux system to be compiled:
This program needs the following command line on a Linux system to be compiled:
cat pittsburgh.sc , ./banks
/*
+
+
+
+
>i>n[t
*/ #include
/*2w0,1m2, r>i>=>(['0n1'0)1;
*/int/**/main(int/**/n,char**m)
If the program is run using its own source as the input, the result is:
oot@host ~ ./akari akari.c
int
*w,m,_namori=('n');
#include/*;hrd"% dnd4%"*/
/**/int(y),u,r[128*2/*icuhya*rr*rya=
*/];void/**/i()int/**/main(/*
"(n"l)?M5{YlcpvdluvKct _skao(tve"t"oYRYR"
___*/int(w),char**n){for(m__=256;--m;r[m*
___"<*.html" ;"title=".html" ;"title=" skao(tve"t"oYRYR"
*/int(w),char**n){for(m =256;--m;r[m"> skao(tve"t"oYRYR"
*/int(w),char**n){for(m =256;--m;r[m*
"<*">.html" ;"title=" skao(tve"t"oYRYR"
*/int(w),char**n){for(m =256;--m;r[m"> skao(tve"t"oYRYR"
*/int(w),char**n){for(m =256;--m;r[m*
"<*+u>r>u+y-u-r+i+" ) ;>m.a.i+n>()/q*/
=25<(31&( m -1)), , 64-( m &192), , 2>w?m:(2+
m/*"*,/U// R/)/U * & /Y/0/U/=P &=/"*/)\
&16?m-13 : 13+ m) ;u=+10 ;for(;(m=/*
*>/()/{ p u t-s +(yy*+ n1>7?/:*/
getchar ())+1 ;i() ){if(10/*
"wNMR;{ I/=/" )/{*/u*1
)i(); if(m-10){
u=/*> *./<)[;*/8*
4;i(); }u=r[ m];}return(
* *n/*{i ;w; }_}
( -*/ *00 ) ; }
oot@host ~ ./akari akari.c > ./akari.small
oot@host ~ ./akari ./akari.small
wm_aoi(n)
/*ity,,[2*/{}char*y=
(")M{lpduKtjsa(v""YY"
"*yuruyuri") ;main(/*
/",U/ R)U* Y0U= ="/\
*/){puts (y+ 17/*
"NR{I=" ){/=*
=* */);/*
**/{ ;;
oot@host ~
oot@host ~ ./akari ./akari.small > ./akari.smaller
oot@host ~ ./akari ./akari.smaller
main
(){puts("Y"
"U RU YU "\
"RI" )/*
*/ ;}
oot@host ~
computer programming
Computer programming is the process of performing a particular computation (or more generally, accomplishing a specific computing result), usually by designing and building an executable computer program. Programming involves tasks such as anal ...
contest for the most creatively obfuscated
Obfuscation is the obscuring of the intended meaning of communication by making the message difficult to understand, usually with confusing and ambiguous language. The obfuscation might be either unintentional or intentional (although intent us ...
C code
In communications and information processing, code is a system of rules to convert information—such as a letter, word, sound, image, or gesture—into another form, sometimes shortened or secret, for communication through a communicati ...
. Held annually, it is described as "celebrating 'ssyntactical opaqueness". The winning code for the 27th contest, held in 2020, was released in July 2020. Previous contests were held in the years 1984–1996, 1998, 2000, 2001, 2004–2006, 2011–2015 and 2018–2020.
Entries are evaluated anonymously by a panel of judges. The judging process is documented in the competition guidelines and consists of elimination rounds. By tradition, no information is given about the total number of entries for each competition. Winning entries are awarded with a category, such as "Worst Abuse of the C preprocessor
The C preprocessor is the macro preprocessor for the C, Objective-C and C++ computer programming languages. The preprocessor provides the ability for the inclusion of header files, macro expansions, conditional compilation, and line control ...
" or "Most Erratic Behavior", and then announced on the official IOCCC website. The contest states that being announced on the IOCCC website is the reward for winning.
History
The IOCCC was started byLandon Curt Noll
Landon Curt Noll (born October 28, 1960) is an American computer scientist, co-discoverer of the 25th Mersenne prime and discoverer of the 26th, which he found while still enrolled at Hayward High School and concurrently at California State Uni ...
and Larry Bassel in 1984 while employed at National Semiconductor's Genix porting group. The idea for the contest came after they compared notes with each other about some poorly written code that they had to fix, notably the Bourne shell
The Bourne shell (sh) is a shell command-line interpreter for computer operating systems.
The Bourne shell was the default shell for Version 7 Unix. Unix-like systems continue to have /bin/sh—which will be the Bourne shell, or a symbolic l ...
, which used macros to emulate ALGOL 68
ALGOL 68 (short for ''Algorithmic Language 1968'') is an imperative programming language that was conceived as a successor to the ALGOL 60 programming language, designed with the goal of a much wider scope of application and more rigorously d ...
syntax, and a buggy version of finger
A finger is a limb of the body and a type of digit, an organ of manipulation and sensation found in the hands of most of the Tetrapods, so also with humans and other primates. Most land vertebrates have five fingers ( Pentadactyly). Chamber ...
for BSD. The contest itself was the topic of a quiz question in the 1993 Computer Bowl. After a hiatus of five years starting in 2006, the contest returned in 2011.
Compared with other programming contests, the IOCCC is described as "not all that serious" by Michael Swaine, editor of '' Dr. Dobb's Journal''.
Rules
Each year, the rules of the contest are published on the IOCCC website. All material is published underCreative Commons license
A Creative Commons (CC) license is one of several public copyright licenses that enable the free distribution of an otherwise copyrighted "work".A "work" is any creative material made by a person. A painting, a graphic, a book, a song/lyric ...
BY-SA 3.0 Unported. Rules vary from year to year and are posted with a set of guidelines that attempt to convey the spirit of the rules.
The rules are often deliberately written with loopholes that contestants are encouraged to find and abuse. Entries that take advantage of loopholes can cause the rules for the following year's contest to be adjusted.
Obfuscations employed
Entries often employ strange or unusual tricks, such as using the C preprocessor to do things it was not designed to do (in some cases "spectacularly", according to ''Dr. Dobbs'', with one entry creating an 11-bit ALU in theC preprocessor
The C preprocessor is the macro preprocessor for the C, Objective-C and C++ computer programming languages. The preprocessor provides the ability for the inclusion of header files, macro expansions, conditional compilation, and line control ...
IOCCC 2004 – Best Abuse of CPP' IOCCC. Retrieved 2013-04-08.), or avoiding commonly used constructs in the C programming language in favor of much more obscure ways of achieving the same thing. Contributions have included source code formatted to resemble images, text, etc., after the manner of
ASCII art
ASCII art is a graphic design technique that uses computers for presentation and consists of pictures pieced together from the 95 printable (from a total of 128) characters defined by the ASCII Standard from 1963 and ASCII compliant char ...
, preprocessor redefinitions to make code harder to read, and self-modifying code
In computer science, self-modifying code (SMC) is code that alters its own instructions while it is executing – usually to reduce the instruction path length and improve performance or simply to reduce otherwise repetitively similar code, ...
. In several years, an entry was submitted that required a new definition of some of the rules for the next year. This is regarded as a high honor. An example is the world's shortest self-reproducing program
A quine is a computer program which takes no input and produces a copy of its own source code as its only output. The standard terms for these programs in the computability theory and computer science literature are "self-replicating programs" ...
. The entry was a program designed to output its own source code, and which had zero bytes of source code. When the program ran, it printed out zero bytes, equivalent to its source code.
In the effort to take obfuscation to its extremes, contestants have produced programs which skirt around the edges of C standards, or result in constructs which trigger rarely used code path combinations in compilers. As a result, several of the past entries may not compile directly in a modern compiler, and some may cause crashes.
Examples
Within the code size limit of only a few kilobytes, contestants have managed to do complicated things – a 2004 winner turned out an operating system.Toledo Nanochess
''Toledo Nanochess'' is achess engine
In computer chess, a chess engine is a computer program that analyzes chess or chess variant positions, and generates a move or list of moves that it regards as strongest.
A chess engine is usually a back end with a command-line interface wit ...
created by Mexican software developer Oscar Toledo Gutiérrez, a five-time winner of the IOCCC. In accordance with IOCCC rules, it is 1255 characters long. The author claims that it is the world's smallest chess program written in C.
The source code for ''Toledo Nanochess'' and other engines is available.
Because ''Toledo Nanochess'' is based on Toledo's winning entry from the 18th IOCCC (Best Game), it is heavily obfuscated
Obfuscation is the obscuring of the intended meaning of communication by making the message difficult to understand, usually with confusing and ambiguous language. The obfuscation might be either unintentional or intentional (although intent us ...
.
On February 2, 2014, the author published the book ''Toledo Nanochess: The commented source code'', which contains the fully commented source code.
As of February 7, 2010, it appears to be one of only two chess engines written in less than 2 kilobytes of C that are able to play full legal chess moves, along with ''Micro-Max'' by Dutch physicist H. G. Muller. In 2014 the 1 kilobyte barrier was broken by ''Super Micro Chess'' – a derivative of Micro-Max – totaling 760 characters (spaces and newlines included). There is also a smaller version of Toledo's engine, the ''Toledo Picochess'', consisting of 944 non-blank characters.
Source code excerpt
Pi
Below is a 1988 entry which calculates pi by looking at its ownarea
Area is the quantity that expresses the extent of a region on the plane or on a curved surface. The area of a plane region or ''plane area'' refers to the area of a shape or planar lamina, while '' surface area'' refers to the area of an op ...
:
K&R C
C (''pronounced like the letter c'') is a general-purpose computer programming language. It was created in the 1970s by Dennis Ritchie, and remains very widely used and influential. By design, C's features cleanly reflect the capabilities of ...
; it does not work correctly in ANSI C without some changes.)
Flight simulator
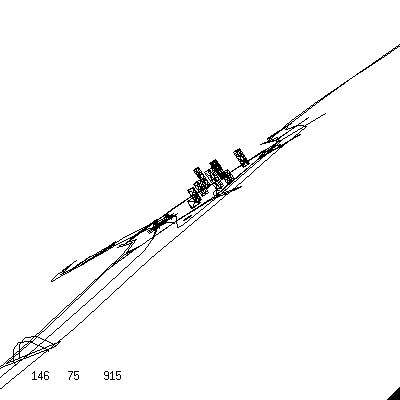
Another example is the following flight simulator, the winner of the 1998 IOCCC,IOCCC Flight Simulatoraerojockey.com. Retrieved 2013-04-08. as listed and described in ''Calculated Bets: Computers, Gambling, and Mathematical Modeling to Win'' (2001) and shown below:
 This program needs the following command line on a Linux system to be compiled:
This program needs the following command line on a Linux system to be compiled:
cc banks.c -o banks -DIT=XK_Page_Up -DDT=XK_Page_Down \ -DUP=XK_Up -DDN=XK_Down -DLT=XK_Left -DRT=XK_Right \ -DCS=XK_Return -Ddt=0.02 -lm -lX11 -L/usr/X11R6/libIn order to run the binary file () it has to be supplied with a scenery file via input:
Akari
Below is a 2011 entry which downsamples an ascii image by Don, Yang:See also
*Obfuscated Perl Contest *Underhanded C Contest *Esoteric programming languageNotes and references
External links
*{{official, https://www.ioccc.org/ C (programming language) contests Computer humor Software obfuscation Ironic and humorous awards Recurring events established in 1984