Intelligence cycle (target-centric approach) on:
[Wikipedia]
[Google]
[Amazon]
The target-centric approach to intelligence is a method of
{{DEFAULTSORT:Cycle (target-centric approach) Intelligence analysis Military intelligence Intelligence assessment
intelligence analysis
Intelligence analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberate ...
that Robert M. Clark introduced in his book "Intelligence Analysis: A Target-Centric Approach" in 2003 to offer an alternative methodology to the traditional intelligence cycle
The Intelligence cycle describes how intelligence is ideally processed in civilian and military intelligence agencies, and law enforcement organizations. It is a closed path consisting of repeating nodes, which (if followed) will result in finis ...
. Its goal is to redefine the intelligence process in such a way that all of the parts of the intelligence cycle come together as a network. It is a collaborative process where collectors, analysts and customers are integral, and information does not always flow linearly.
Target-centric analysis
Intelligence process
The most common view of the intelligence process is the model known as theintelligence cycle
The Intelligence cycle describes how intelligence is ideally processed in civilian and military intelligence agencies, and law enforcement organizations. It is a closed path consisting of repeating nodes, which (if followed) will result in finis ...
. In the original concept of this model, the steps are isolated stages where each part has a designated purpose or task. When the contributors and collectors complete data collection, the cycle continues. While this procedure completes each part of the cycle, it may constrain the flow of
information. The intelligence community often discusses the problems
A problem is a difficulty which may be resolved by problem solving.
Problem(s) or The Problem may also refer to:
People
* Problem (rapper), (born 1985) American rapper Books
* ''Problems'' (Aristotle), an Aristotelian (or pseudo-Aristotelian) co ...
with this pure model and offers multiple approaches to solving them.
In the pure model, there is limited opportunity for contributors or consumers to ask questions or provide feedback. To fully understand what they analyze, analysts should have the opportunity to ask questions about the sources where collectors gathered information. Likewise, when the decision-maker receives an intelligence estimate, he or she should have the opportunity to ask questions concerning not only how the analyst reached a particular conclusion, but also questions concerning the reliability of sources.
Sherman Kent
Sherman Kent (December 6, 1903 – March 11, 1986), was a Yale University history professor who, during World War II and through 17 years of Cold War-era service in the Central Intelligence Agency, pioneered many of the methods of intelligenc ...
the "father of intelligence analysis," left a legacy in not only his work, but in the faculty members at the Sherman Kent Center. The faculty teaches intelligence principles to future intelligence analysts. According to Jack Davis, of the Sherman Kent Center, Kent encouraged arguments and dissent among analysts, as well as taking into account a "wide range of outside opinions." Kent also encouraged "collective responsibility for judgment," which supports a network approach to intelligence. In such a network, analysts are directly accountable for the work, and a decision maker or consumer's questions help the intelligence process by leading by pushing the analyst to challenge and refine his or her own work.
It is important to note that agencies constantly modify the traditional, pure model in intelligence practice. For example, various "centers" under the Director of National Intelligence deliberately put collectors and analysts into teams.
The traditional intelligence cycle separates collectors, processors, and analysts and too often results in "throwing information over the wall" to become the next person's responsibility. Everyone neatly avoids responsibility for the quality of the final product. Because this "compartmentalized process results in formalized and relatively inflexible requirements at each stage, it is more predictable and therefore more vulnerable to an opponent’s countermeasures.”
Kurt April and Julian Bessa examined weaknesses of the competitive intelligence community in their article "A Critique of the Strategic Competitive Intelligence Process within a Global Energy Multinational." They examined two competitive intelligence processes: ''Competitive Strategic Business Intelligence'' (CIAD) and ''Competitive Technical Intelligence'' (CTI). According to April and Bessa, CIAD is a linear process where the intelligence product moves upward through the layers of the organization. In contrast, CTI is a more networked model. They found that the organizational structure associated with CIAD prevents open-sharing of information and ideas, and is a stumbling block to intelligence analysis.”
Testifying to the House Committee on Homeland Security Mr. Eliot A. Jardines
Eliot A. Jardines was the first Assistant Deputy Director of National Intelligence for Open Source (ADDNI/OS) in the United States.Analysis of competing hypotheses
The analysis of competing hypotheses (ACH) is a methodology for evaluating multiple competing hypotheses for observed data. It was developed by Richards (Dick) J. Heuer, Jr., a 45-year veteran of the Central Intelligence Agency, in the 1970s for ...
and cognitive traps for intelligence analysis.
Creating the model

Models in intelligence
Conceptual models
Conceptual may refer to:
Philosophy and Humanities
*Concept
*Conceptualism
* Philosophical analysis (Conceptual analysis)
*Theoretical definition (Conceptual definition)
*Thinking about Consciousness (Conceptual dualism)
*Pragmatism (Conceptual p ...
are useful for the analytic process, and are particularly helpful to help understand the target-centric approach to intelligence. A conceptual model is an abstract invention of the mind that best incorporates and takes advantage of an analyst's thought process. The model allows the analyst to use a powerful descriptive tool to both estimate current situations and predict future circumstances.
Sources of intelligence information
Once the analyst constructs the skeleton structure of the model, the next step is to add substance. This is where the analyst must research, gather information, and synthesize to populate the model. For an analyst to successfully populate a model for a complex target, he or she must find information from a wide range of both classified and unclassified sources. This includes retrieving information from the body of existing intelligence. Depending on the target, an analyst may seek out information fromopen source intelligence
Open-source intelligence (OSINT) is the collection and analysis of data gathered from open sources (covert and publicly available sources) to produce actionable intelligence. OSINT is primarily used in national security, law enforcement, and busi ...
(information available to the general public), human intelligence (HUMINT
Human intelligence (abbreviated HUMINT and pronounced as ''hyoo-mint'') is intelligence gathered by means of interpersonal contact, as opposed to the more technical intelligence gathering disciplines such as signals intelligence (SIGINT), imager ...
), measures and signatures intelligence (MASINT
Measurement and signature intelligence (MASINT) is a technical branch of intelligence gathering, which serves to detect, track, identify or describe the distinctive characteristics (signatures) of fixed or dynamic target sources. This often incl ...
), signals intelligence (SIGINT
Signals intelligence (SIGINT) is intelligence-gathering by interception of '' signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly used in communication ...
), or imagery intelligence (IMINT
Imagery intelligence (IMINT), pronounced as either as ''Im-Int'' or ''I-Mint'', is an intelligence gathering discipline wherein imagery is analyzed (or "exploited") to identify information of intelligence value. Imagery used for defense intel ...
). Even though open source information is inexpensive or free, and easily accessible, it can be just as useful as the more specialized, technical intelligence sources that are expensive to use.Clark 2006, p.111.
Populating the model
Populating the model forces the analyst to collate the collected data, organize the data, and evaluate evidence for relevance and credibility. Finally, after the analyst examines each piece of data, the analyst must incorporate the information into the target model. As the body of information builds in the model, the analyst can more easily determine where there are inconsistencies in conclusions. This requires the analyst to carry out further research to support or deny a particular conclusion. Also, as the analyst populates the model, the target model shows where gaps exist in the model. These gaps also force the analyst to collect additional information to more completely describe the target.Organizational analysis
Clark defined anorganization
An organization or organisation (English in the Commonwealth of Nations, Commonwealth English; American and British English spelling differences#-ise, -ize (-isation, -ization), see spelling differences), is an legal entity, entity—such as ...
as a system that "can be viewed and analyzed from three perspectives: structure, function, and process."Clark 2006, p.227. ''Structure'' describes the parts of the whole organization, emphasizing people who are part of the organization, and their relationships with one another as part of that whole. ''Function'' describes the product of the organization and emphasizes decision-making. Finally, ''Process'' describes the activities and knowledge that formulate the final product. An analyst must consider each of these components while examining a particular target organization. Most importantly, when an analyst successfully describes the target organization with a full understanding of its structure, function, and process, the model demonstrates the target's strengths and weaknesses to the analyst. Weaknesses or changes in the target organization aid the analyst in constructing a predictive, reliable analysis.
Applications of the target-centric approach to intelligence
The target-centric approach to intelligence does not aim to deny other intelligence processes. Instead, it offers an alternative method to the established intelligence process. The intelligence cycle, like many other systems, continually needs improvement. In the wake of the 2001 terrorist attacks, the 9/11 Commission declared that theUS intelligence community
The United States of America (U.S.A. or USA), commonly known as the United States (U.S. or US) or America, is a country primarily located in North America. It consists of 50 states, a federal district, five major unincorporated territori ...
needed improvements in gathering and sharing information. According to the 9/11 Commission, U.S. intelligence agencies experienced inadequate coordination and cooperation. This is one example of failure in the intelligence cycle
Failure in the intelligence cycle or intelligence failure, is the outcome of the inadequacies within the intelligence cycle. The intelligence cycle itself consists of six steps that are constantly in motion. The six steps
are: requirements, coll ...
, where a breakdown in the accepted process led to devastating results.
General Stanley A. McChrystal
Stanley Allen McChrystal (born August 14, 1954) is a retired United States Army general best known for his command of Joint Special Operations Command (JSOC) from 2003 to 2008 where his organization was credited with the death of Abu Musab al-Zarq ...
wrote in 2014 about a targeting cycle called "F3EA" used in the Iraq War
{{Infobox military conflict
, conflict = Iraq War {{Nobold, {{lang, ar, حرب العراق (Arabic) {{Nobold, {{lang, ku, شەڕی عێراق ( Kurdish)
, partof = the Iraq conflict and the War on terror
, image ...
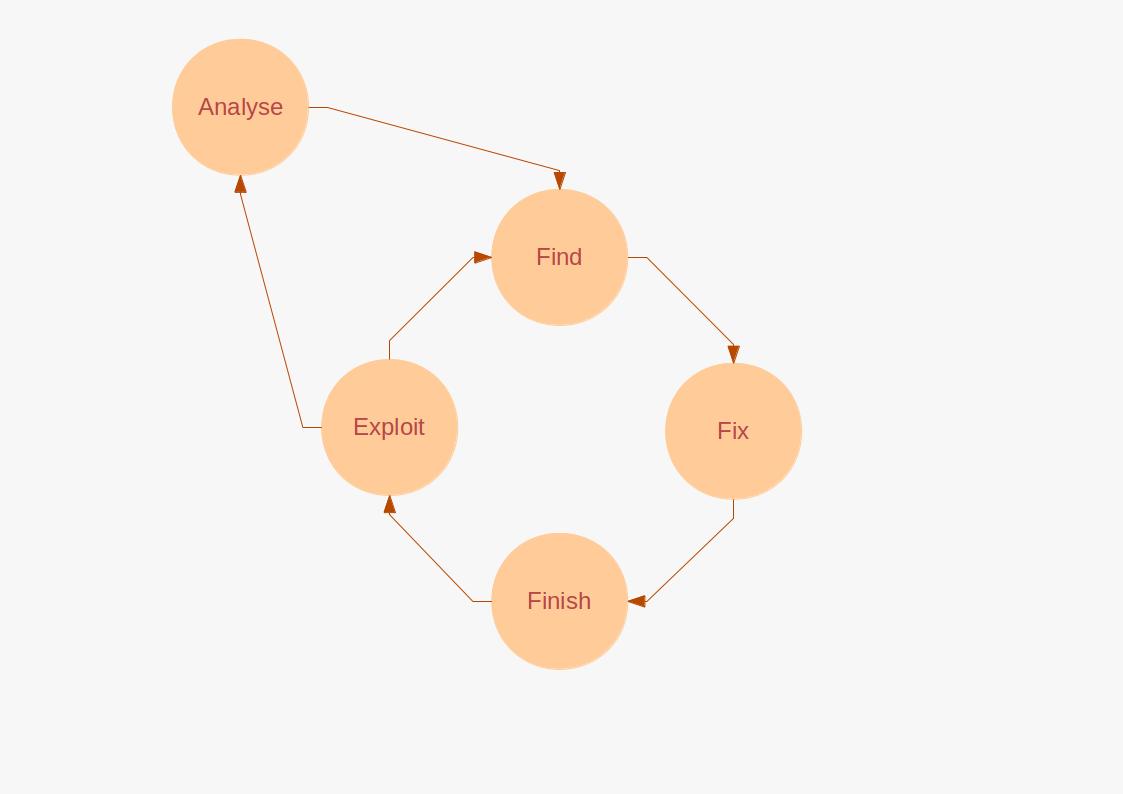
, which stands for:
#Find: A target (person or location) is first identified and located.
#Fix: The target is then kept under continuous surveillance while a Positive Identification is established.
#Finish: A raiding force is assigned to capture or kill the target.
#Exploit: Intelligence material is secured and mined, with detainees interrogated.
#Analyze: Information is studied to identify further targeting opportunities.
Criticisms
According to Heuer, analysts can always strive to improve estimates, and no method guarantees accurate conclusions every time. Analysts should expect intelligence failures, and refine the methodology to learn from what worked and what did not work. Also, according to Johnston, time constraints are one of the most difficult obstacles for intelligence analysts. A target-centric model, by its very nature, is a network process that, in its ideal form, is more time-consuming than the traditional cycle. If analysts back-track to collaborate with collectors and respond to multiple questions from decision makers, the finished product will likely take a longer amount of time to reach the decision maker.References
{{DEFAULTSORT:Cycle (target-centric approach) Intelligence analysis Military intelligence Intelligence assessment