Election audits on:
[Wikipedia]
[Google]
[Amazon]
An election audit is any review conducted after polls close for the purpose of determining whether the votes were counted accurately (a ''results audit'') or whether proper procedures were followed (a ''process audit''), or both.
Both results and process audits can be performed between elections for purposes of quality management, but if results audits are to be used to protect the official election results from undetected fraud and error, they must be completed before election results are declared final.
''
valid hand-counting methods
incorporate redundancy, so that more than one person views and interprets each vote and more than one person confirms the accuracy of each tabulation. In this way, the manual count incorporates a confirmation step, and a separate audit may not be considered necessary. However, when votes are read and tabulated electronically, confirmation of the results' accuracy must become a separate process. Within and outside elections, use of computers for
Verified Voting Foundation
Transparency
The public must be allowed to observe, verify, and point out procedural mistakes in all phases of the audit. This requires that audit procedures and standards be adopted, in written form, and made available before the election.
While the actual work of post-election audits may be best performed by the officials who conduct the elections, the authority and regulation of post-election audits should be independent of officials who conduct the elections.
Vote-counting in the audit should be performed with hand-to-eye counts of voter-marked, voter-verified paper ballots.
(chain of custody, or internal control): The records used in the audit must be verified to be true and complete records of the election.
The audits must reach statistical confidence that the computer-tabulated results identified the correct winners.
When discrepancies are found, investigation is conducted to determine cause of the discrepancies.
The ballot-sample selection process includes all jurisdictions and all ballot types (e.g., absentee, mail-in and accepted provisional ballots).
The audit includes a limited non-random sample selected on the basis of factors useful for building voter confidence or improving election management, such as Election-Day problems or preliminary results that deviate significantly from historical voting patterns.
Post-election audits must be completed before election results are declared official and final, and must either verify or correct the outcome.
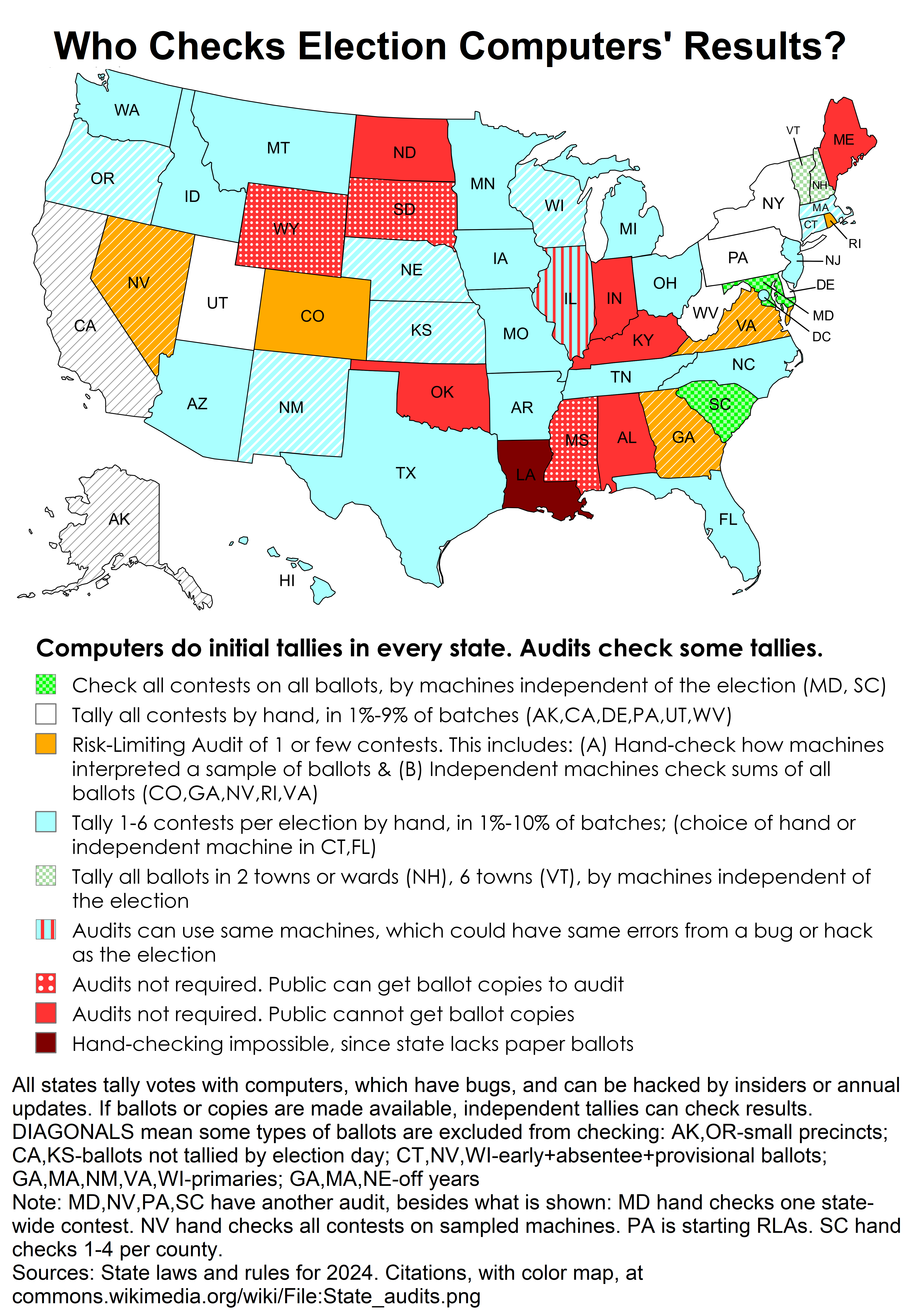 Only two US states hand-tally a representative sample of all ballots, and tally all contests on those ballots, and make corrections in official results if needed: PA and WV. Two more states hand-tally all contests on a representative sample of all ballots, so they can check official results, though not necessarily correcting them if that were needed: DE, UT. In PA, UT and WV sample sizes are usually adequate for state-wide contests, but not for close county and local results. All state assembly districts and local governments have a chance of being covered and audited, and they also have a chance of being missed entirely by these random samples of precincts and election machines.
NY checks if election machines performed as expected, not whether they captured voter intent, so circles and checkmarks outside target areas are not checked by the audit. Two other states hand-tally all contests, but the samples exclude significant groups of ballots: AK excludes small precincts; CA excludes ballots processed after election night (a third). For the two thirds of ballots audited, California does ensure that all contests are covered; they add precincts or machines to the initial sample, to ensure they sample at least some ballots from every contest. At the other extreme, thirteen states do not have regular audits of election results. Most of the other states check only a few contests, so errors are not measured in most contests.
Considering the recommended best practices above, two states (DC, MA) allow public observation of all steps; three states (MD, NM, VT) have audits done by the Secretary of State, which is partly independent of election day procedures; 18 states hand-count; six states (CO, MD, NC, NM, RI, VA) have good samples for statistical confidence; no states have ways to recover from discrepancies in the chain of custody; other issues are listed in the table below.
Computerization of elections occurred rapidly in the United States following the presidential election of 2000, in which imprecise vote-counting practices played a controversial role, and the subsequent adoption of the Help America Vote Act (HAVA) of 2002. The rapid switch to computerized vote tabulation forced election officials to abandon many pre-automation practices that had been used to verify vote totals, such as the redundancy included in valid hand-counting procedures.
Only two US states hand-tally a representative sample of all ballots, and tally all contests on those ballots, and make corrections in official results if needed: PA and WV. Two more states hand-tally all contests on a representative sample of all ballots, so they can check official results, though not necessarily correcting them if that were needed: DE, UT. In PA, UT and WV sample sizes are usually adequate for state-wide contests, but not for close county and local results. All state assembly districts and local governments have a chance of being covered and audited, and they also have a chance of being missed entirely by these random samples of precincts and election machines.
NY checks if election machines performed as expected, not whether they captured voter intent, so circles and checkmarks outside target areas are not checked by the audit. Two other states hand-tally all contests, but the samples exclude significant groups of ballots: AK excludes small precincts; CA excludes ballots processed after election night (a third). For the two thirds of ballots audited, California does ensure that all contests are covered; they add precincts or machines to the initial sample, to ensure they sample at least some ballots from every contest. At the other extreme, thirteen states do not have regular audits of election results. Most of the other states check only a few contests, so errors are not measured in most contests.
Considering the recommended best practices above, two states (DC, MA) allow public observation of all steps; three states (MD, NM, VT) have audits done by the Secretary of State, which is partly independent of election day procedures; 18 states hand-count; six states (CO, MD, NC, NM, RI, VA) have good samples for statistical confidence; no states have ways to recover from discrepancies in the chain of custody; other issues are listed in the table below.
Computerization of elections occurred rapidly in the United States following the presidential election of 2000, in which imprecise vote-counting practices played a controversial role, and the subsequent adoption of the Help America Vote Act (HAVA) of 2002. The rapid switch to computerized vote tabulation forced election officials to abandon many pre-automation practices that had been used to verify vote totals, such as the redundancy included in valid hand-counting procedures.
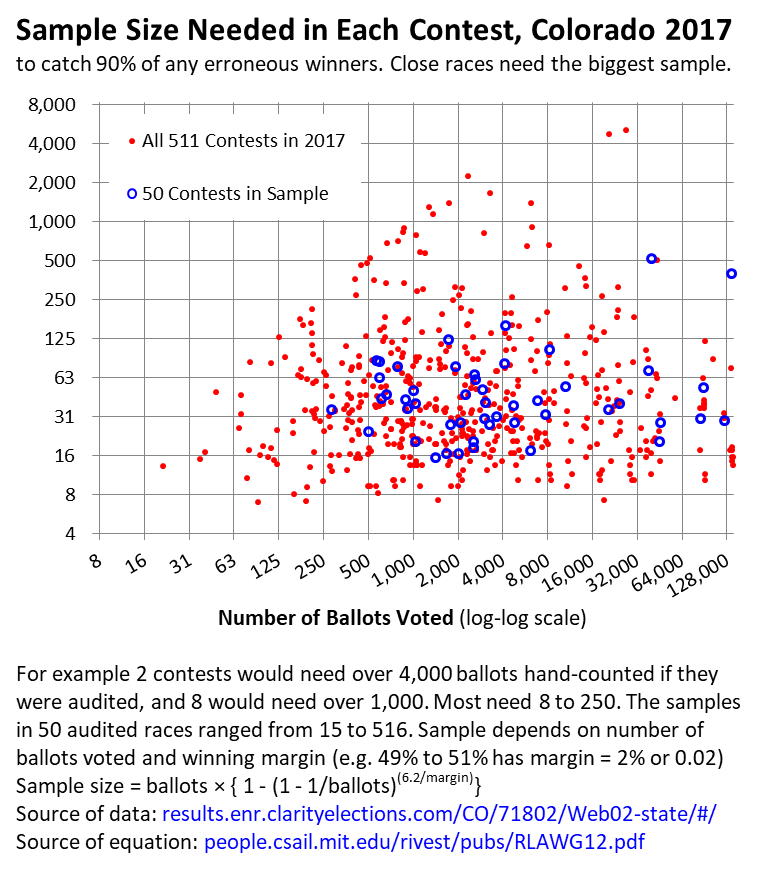 Risk-limiting audits are required in Colorado, North Carolina, Rhode Island and Virginia. These store voting machines' interpretation of each ballot ("cast vote record"), collect them centrally over the internet, re-tally them with an independent computer to check totals, and hand-check a sample of the stored paper ballots to check voting machines' interpretations. Samples are big enough to be sure results are accurate, up to an acceptable level of risk, such as 9%. For each audited contest, if the original computer interpretations identified the wrong winner, there is a 9%
chance in Colorado that the audit will miss it, and the wrong winner will take office. A lower risk limit would let fewer errors through, but would require larger sample sizes. Close contests also require larger sample sizes. Colorado audits only a few contests, and audits none of the closest contests, which need the biggest samples. Auditing all contests would require several counties to hand-count thousands of ballots each.
If the samples do not confirm the initial results, more rounds of sampling may be done, but if it appears the initial results are wrong, risk-limiting audits require a 100% hand count to change the result, even if that involves hand-counting hundreds of thousands of ballots.
Colorado notes that they have to be extremely careful to keep ballots in order, or they have to number them, to be sure of comparing the hand counts with the machine records of those exact ballots. Colorado says it has a reliable system to re-tally the records, but it is not yet publicly documented.
In 2010, the
Risk-limiting audits are required in Colorado, North Carolina, Rhode Island and Virginia. These store voting machines' interpretation of each ballot ("cast vote record"), collect them centrally over the internet, re-tally them with an independent computer to check totals, and hand-check a sample of the stored paper ballots to check voting machines' interpretations. Samples are big enough to be sure results are accurate, up to an acceptable level of risk, such as 9%. For each audited contest, if the original computer interpretations identified the wrong winner, there is a 9%
chance in Colorado that the audit will miss it, and the wrong winner will take office. A lower risk limit would let fewer errors through, but would require larger sample sizes. Close contests also require larger sample sizes. Colorado audits only a few contests, and audits none of the closest contests, which need the biggest samples. Auditing all contests would require several counties to hand-count thousands of ballots each.
If the samples do not confirm the initial results, more rounds of sampling may be done, but if it appears the initial results are wrong, risk-limiting audits require a 100% hand count to change the result, even if that involves hand-counting hundreds of thousands of ballots.
Colorado notes that they have to be extremely careful to keep ballots in order, or they have to number them, to be sure of comparing the hand counts with the machine records of those exact ballots. Colorado says it has a reliable system to re-tally the records, but it is not yet publicly documented.
In 2010, the
Colorado became the first state to implement
risk-limiting audits statewide as a routine practice during the post-election process of certifying election results.

 Humboldt Count
Humboldt Count
Elections Transparency ProjectClear Ballot
an
TrueBallot
scan all ballots with a commercial scanner, so extensive audits can be done on the scans without damaging paper ballots, without hand-counting, by multiple groups, independently of the election software. Clear Ballot is certified by the US Election Assistance Commission for voting, and they also have an auditing system, ClearAudit. TrueBallot does not currently serve government elections, just private groups. Both use proprietary software, so if it were hacked at the vendor or locally to create false images of the ballots or false counts, then local officials and the public could not check it. The "Brakey method" is an approach using electronic ballot images already created by most current US election systems. These ballot images could be hacked if the election software itself is hacked, either at the vendor or elsewhere, so for full security, ballot images need to be checked against the paper ballots, to determine if the images are accurate. To enable this one to one ballot-image comparison, the Brakey Method requires that the ballot images be linkable to their paper ballots, either by keeping paper ballots in the same order as the scans, or through a unique identifier that appears on both digital image and physical ballot. Independent systems to tally ballot images include Audit Engine, Free and Fair, OSET Institute (under development), and the Elections Transparency Project, as used in Humboldt County, California, a medium sized county with 58,000 ballots in the 2016 general election. Humboldt uses a commercial scanner to scan all ballots and puts them in a digitally signed file, so true copies of the file can be reliably identified. Ballots with identifying marks are first hand-copied by election staff, to anonymize them, since they are valid under California law. The scanner prints a number on each ballot before scanning it, so the scan can be checked against the same physical ballot later if needed. The project has written open source software (Trachtenburg Election Verification Software, TEVS) to read the files, and they check all contests on all ballots to see if official counts are correct. The first time they scanned and checked, in 2008, they found 200 missing ballots, showing the value of complete checks. Other jurisdictions can similarly scan ballots and use Humboldt's software or their own to audit all contests. They need to ensure their in-house counting software is secure and independent of any bugs or hacks in the election software, just as users of risk-limiting audits do. Reading these scans, with software independent of the election system, is a practical way to audit a large number of close contests, without large hand counts. Scans are also the only practical way to bypass problems of physical security, if paper ballots are scanned, digitally signed, and the resulting electronic records are verified against a sample of paper ballots, as ballots arrive. Scans can be made and digitally signed before ballots are stored, while other audit methods are too slow to do election night. Scanners can process thousands of ballots per hour, and several scanners can operate simultaneously in larger jurisdictions. Once ballots are scanned and a digital signature is published, electronic records can be tallied at any convenient time. Humboldt and several other jurisdictions have gone beyond this internal approach, and release the digitally signed files of ballot images to the public, so others can use their own software, independent of the election system and officials, to check all contests on all ballots. Public release lets losing candidates who mistrust the election officials' security measures do their own checks. Humboldt County believes the scans give their citizens high confidence in the county election results.
 Hand and machine counts. Current audits in most states involve counting paper ballots by hand, but some states re-use the same machines used in the election. Three states use different machines, to provide some independent check.
Sample sizes. When states audit, they usually pick a random sample of 1% to 10% of precincts to recount by hand or by machine. If a precinct has more than one machine, and they keep ballots and totals separate by machine, they can draw a sample of machines rather than precincts and count all ballots processed by that machine. These samples can identify systematic errors widely present in the election. They have only a small chance of catching a hack or bug which was limited to a few precincts or machines, even though that could change the result in close contests.
Number of contests. In the random sample, most states audit only a few contests, so they can only find problems in those contests.
Hand and machine counts. Current audits in most states involve counting paper ballots by hand, but some states re-use the same machines used in the election. Three states use different machines, to provide some independent check.
Sample sizes. When states audit, they usually pick a random sample of 1% to 10% of precincts to recount by hand or by machine. If a precinct has more than one machine, and they keep ballots and totals separate by machine, they can draw a sample of machines rather than precincts and count all ballots processed by that machine. These samples can identify systematic errors widely present in the election. They have only a small chance of catching a hack or bug which was limited to a few precincts or machines, even though that could change the result in close contests.
Number of contests. In the random sample, most states audit only a few contests, so they can only find problems in those contests.
Election Verification Network
Verified Voting
Principles and Best Practices for Election Auditing
Elections
Election recount
An election recount is a repeat tabulation of votes cast in an election that is used to determine the correctness of an initial count. Recounts will often take place if the initial vote tally during an election is extremely close. Election reco ...
s'' are a specific type of audit, with elements of both results and process audits.

The need for verification of election results
In jurisdictions that tabulate election results exclusively with manual counts from paper ballots, or 'hand counts', officials do not need to rely on a single person to view and count the votes. Insteadvalid hand-counting methods
incorporate redundancy, so that more than one person views and interprets each vote and more than one person confirms the accuracy of each tabulation. In this way, the manual count incorporates a confirmation step, and a separate audit may not be considered necessary. However, when votes are read and tabulated electronically, confirmation of the results' accuracy must become a separate process. Within and outside elections, use of computers for
decision support
A decision support system (DSS) is an Information systems, information system that supports business or organizational decision-making activities. DSSs serve the management, operations and planning levels of an organization (usually mid and hig ...
comes with certain IT risk
Information technology risk, IT risk, IT-related risk, or cyber risk is any risk related to information technology. While information has long been appreciated as a valuable and important asset, the rise of the knowledge economy and the Digital Re ...
s. Election-Day electronic miscounts can be caused by unintentional human error, such as incorrectly setting up the computers to read the unique ballot in each election and undetected malfunction, such as overheating or loss of calibration. Malicious intervention can be accomplished by corrupt insiders at the manufacturer, distributor or election authority, or external hackers who access the software on or before Election Day.
Computer-related risks specific to elections include local officials’ inability to draw upon the level of IT expertise available to managers of commercial decision-support computer systems and the intermittent nature of elections, which requires reliance on a large temporary workforce to manage and operate the computers.''Broken Ballots: Will Your Vote Count?'' Douglas W. Jones and Barbara Simon, CSLI Publications, 2012 Voting machines are usually air-gapped from the internet, but they receive updates from flash drives which do come from the internet, and in any case air-gapped computers are regularly hacked through flash drives and other means. Besides traditional security risks such as lock-picking and phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
attacks, voting machines are often unattended in public buildings the night before the election. This physical access lets outsiders subvert them.
To reduce the risk of flawed Election-Day output, election managers like other computer-dependent managers rely on testing and ongoing IT security. In the field of elections management, these measures take the form of federal certification of the electronic elections system designs, though there is no way to know the certified software is what is actually installed; security measures in the local election officials’ workplaces; and pre-election testing.
A third risk-reduction measure is performed after the computer has produced its output: Routinely checking the computers' output for accuracy, or auditing. Outside elections, auditing practices in the private sector and in other government applications are routine and well developed. In the practice of elections administration, however, the Pew Charitable Trusts stated in 2016, “Although postelection audits are recognized as a best practice to ensure that voting equipment is functioning properly, that proper procedures are being followed, and that the overall election system is reliable, the practice of auditing is still in its relative infancy. Therefore, a consensus has not arisen about what constitutes the necessary elements of an
auditing program.”
Routine results audits also support voter confidence by improving election officials' ability to respond effectively to allegations of fraud or error.
Examples of wrong outcomes found by audits
In 2012 in Palm Beach County, FL, a routine audit which hand-counted a sample of precincts, changed the outcomes in two Wellington City council contests. Votes in each contest were reported for a different contest. The problem did not occur in the county's other 15 municipalities.Examples of intrusions into election computers
Computers which tally votes or compile election results are known to have been hacked in the US in 2014 and 2016, Ukraine in 2014, and South Africa in 1994. Only the Ukraine hack was disclosed immediately, so regular audits are needed to provide timely corrections.Audit challenges unique to election results
Confirming that votes were credited to the correct candidates’ totals might seem to be a relatively uncomplicated task, but election managers face several audit challenges not present for managers of other decision-support IT applications. Primarily, ballot privacy prevents election officials from associating individual voters with individual ballots. This makes it impossible for election officials to use some standard audit practices such as those banks use to confirm that ATMs credited deposits to the correct account. Another challenge is the need for a prompt and irrevocable decision. Election results need to be confirmed promptly, before officials are sworn into office. In many commercial uses of information technology, managers can reverse computer errors even when detected long after the event. However, once elected officials are sworn into office, they begin to make decisions such as voting on legislation or signing contracts on behalf of the government. Even if the official were to be removed because a computer error was discovered to have put that official in office, it would not be possible to reverse all the consequences of the error. The intermittent nature of elections is another challenge. The number of elections managed by an election authority ranges from two per year (plus special elections) in five US states to one every 4 years (plus by-elections) in parliamentary systems like Canada where different election authorities manage national, provincial and municipal elections. This intermittency limits the development of a full-time, practiced workforce, for either the elections or the audits. Turning election audits over to an independent, disinterested professional accounting firm is another option not available to election officials. Because election results affect everyone, including the election officials themselves, truly disinterested auditors do not exist. Therefore, audit transparency is required to provide credibility.Attributes of a good election results audit
No governing body or professional association has yet adopted a definitive set of best practices for election audits. However, in 2007 a group of election-integrity organizations, including thVerified Voting Foundation
Common Cause
Common Cause is a watchdog group based in Washington, D.C., with chapters in 35 states. It was founded in 1970 by John W. Gardner, a Republican, who was the former Secretary of Health, Education, and Welfare in the administration of President ...
, and the Brennan Center for Justice
The Brennan Center for Justice at New York University School of Law (NYU Law) is a nonprofit law and public policy institute. The organization is named after Supreme Court Justice William J. Brennan Jr. Generally considered liberal, the Brennan C ...
at NYU School of Law collaborated with the American Statistical Association
The American Statistical Association (ASA) is the main professional organization for statisticians and related professionals in the United States. It was founded in Boston, Massachusetts on November 27, 1839, and is the second oldest continuousl ...
to produce a set of recommended best practices for post-election results audits:
Transparency
The public must be allowed to observe, verify, and point out procedural mistakes in all phases of the audit. This requires that audit procedures and standards be adopted, in written form, and made available before the election.
While the actual work of post-election audits may be best performed by the officials who conduct the elections, the authority and regulation of post-election audits should be independent of officials who conduct the elections.
Vote-counting in the audit should be performed with hand-to-eye counts of voter-marked, voter-verified paper ballots.
(chain of custody, or internal control): The records used in the audit must be verified to be true and complete records of the election.
The audits must reach statistical confidence that the computer-tabulated results identified the correct winners.
When discrepancies are found, investigation is conducted to determine cause of the discrepancies.
The ballot-sample selection process includes all jurisdictions and all ballot types (e.g., absentee, mail-in and accepted provisional ballots).
The audit includes a limited non-random sample selected on the basis of factors useful for building voter confidence or improving election management, such as Election-Day problems or preliminary results that deviate significantly from historical voting patterns.
Post-election audits must be completed before election results are declared official and final, and must either verify or correct the outcome.
Current practices in election results auditing in India
India has designed and uses voting machines with one button per candidate. The button, when pressed, prints the selected candidate on a slip of paper (VVPAT
Voter verifiable paper audit trail (VVPAT) or verified paper record (VPR) is a method of providing feedback to voters using a ballotless voting system. A VVPAT is intended as an independent verification system for voting machines designed to allo ...
), displays it to the voter, drops the slip into a box and tallies a vote for the candidate. The VVPAT is easy for voters to check, since voters only have one vote to cast, for one member of the lower house of Congress. However there is no way to correct the vote if the VVPAT shows an error. The software is encoded on the machines' chip in a way that it cannot be examined. Brookings found that India's adoption of voting machines cut paper ballot stuffing noticeably in states with the most election prosecutions, and led to more voting by disadvantaged populations. Originally the voting machines lacked a paper trail, and VVPATs were added in 2013-2019 because of doubts about security of unchecked machines.
India hand tallies paper VVPATs from a 1.5% sample of election machines on the last evening of voting, before releasing results.Audit procedures start on p.64 of In the April–May 2019 elections, the Election Commission of India
The Election Commission of India (ECI) is a constitutional body. It was established by the Constitution of India to conduct and regulate elections in the country. Article 324 of the Constitution provides that the power of superintendence, dir ...
hand-tallied the slips of paper from 20,675 voting machines (out of 1,350,000 or 1,730,000 machines) and found discrepancies for 8 machines, usually of four votes or less. Most machines tally over 16 candidates, and they did not report how many of these candidate tallies were discrepant. They formed investigation teams to report within ten days, were still investigating in November 2019, with no report as of June 2021 though the VVPATs themselves were destoyed in September 2019. Hand tallies before and after 2019 had a perfect match with machine counts.
Table of Indian audit rules
Current practices in election results auditing in the United States
Overview
 Only two US states hand-tally a representative sample of all ballots, and tally all contests on those ballots, and make corrections in official results if needed: PA and WV. Two more states hand-tally all contests on a representative sample of all ballots, so they can check official results, though not necessarily correcting them if that were needed: DE, UT. In PA, UT and WV sample sizes are usually adequate for state-wide contests, but not for close county and local results. All state assembly districts and local governments have a chance of being covered and audited, and they also have a chance of being missed entirely by these random samples of precincts and election machines.
NY checks if election machines performed as expected, not whether they captured voter intent, so circles and checkmarks outside target areas are not checked by the audit. Two other states hand-tally all contests, but the samples exclude significant groups of ballots: AK excludes small precincts; CA excludes ballots processed after election night (a third). For the two thirds of ballots audited, California does ensure that all contests are covered; they add precincts or machines to the initial sample, to ensure they sample at least some ballots from every contest. At the other extreme, thirteen states do not have regular audits of election results. Most of the other states check only a few contests, so errors are not measured in most contests.
Considering the recommended best practices above, two states (DC, MA) allow public observation of all steps; three states (MD, NM, VT) have audits done by the Secretary of State, which is partly independent of election day procedures; 18 states hand-count; six states (CO, MD, NC, NM, RI, VA) have good samples for statistical confidence; no states have ways to recover from discrepancies in the chain of custody; other issues are listed in the table below.
Computerization of elections occurred rapidly in the United States following the presidential election of 2000, in which imprecise vote-counting practices played a controversial role, and the subsequent adoption of the Help America Vote Act (HAVA) of 2002. The rapid switch to computerized vote tabulation forced election officials to abandon many pre-automation practices that had been used to verify vote totals, such as the redundancy included in valid hand-counting procedures.
Only two US states hand-tally a representative sample of all ballots, and tally all contests on those ballots, and make corrections in official results if needed: PA and WV. Two more states hand-tally all contests on a representative sample of all ballots, so they can check official results, though not necessarily correcting them if that were needed: DE, UT. In PA, UT and WV sample sizes are usually adequate for state-wide contests, but not for close county and local results. All state assembly districts and local governments have a chance of being covered and audited, and they also have a chance of being missed entirely by these random samples of precincts and election machines.
NY checks if election machines performed as expected, not whether they captured voter intent, so circles and checkmarks outside target areas are not checked by the audit. Two other states hand-tally all contests, but the samples exclude significant groups of ballots: AK excludes small precincts; CA excludes ballots processed after election night (a third). For the two thirds of ballots audited, California does ensure that all contests are covered; they add precincts or machines to the initial sample, to ensure they sample at least some ballots from every contest. At the other extreme, thirteen states do not have regular audits of election results. Most of the other states check only a few contests, so errors are not measured in most contests.
Considering the recommended best practices above, two states (DC, MA) allow public observation of all steps; three states (MD, NM, VT) have audits done by the Secretary of State, which is partly independent of election day procedures; 18 states hand-count; six states (CO, MD, NC, NM, RI, VA) have good samples for statistical confidence; no states have ways to recover from discrepancies in the chain of custody; other issues are listed in the table below.
Computerization of elections occurred rapidly in the United States following the presidential election of 2000, in which imprecise vote-counting practices played a controversial role, and the subsequent adoption of the Help America Vote Act (HAVA) of 2002. The rapid switch to computerized vote tabulation forced election officials to abandon many pre-automation practices that had been used to verify vote totals, such as the redundancy included in valid hand-counting procedures.
Table of U.S. audit rules
Other state variations. Only DC requires that observers be able to see ballots being audited well enough to discern voter's marks. Three states have rules for what happens when stored ballots are missing: CO-Missing ballots are treated as being cast for all the losers in risk level calculations; MI and NC-no audit.Risk-limiting audits
 Risk-limiting audits are required in Colorado, North Carolina, Rhode Island and Virginia. These store voting machines' interpretation of each ballot ("cast vote record"), collect them centrally over the internet, re-tally them with an independent computer to check totals, and hand-check a sample of the stored paper ballots to check voting machines' interpretations. Samples are big enough to be sure results are accurate, up to an acceptable level of risk, such as 9%. For each audited contest, if the original computer interpretations identified the wrong winner, there is a 9%
chance in Colorado that the audit will miss it, and the wrong winner will take office. A lower risk limit would let fewer errors through, but would require larger sample sizes. Close contests also require larger sample sizes. Colorado audits only a few contests, and audits none of the closest contests, which need the biggest samples. Auditing all contests would require several counties to hand-count thousands of ballots each.
If the samples do not confirm the initial results, more rounds of sampling may be done, but if it appears the initial results are wrong, risk-limiting audits require a 100% hand count to change the result, even if that involves hand-counting hundreds of thousands of ballots.
Colorado notes that they have to be extremely careful to keep ballots in order, or they have to number them, to be sure of comparing the hand counts with the machine records of those exact ballots. Colorado says it has a reliable system to re-tally the records, but it is not yet publicly documented.
In 2010, the
Risk-limiting audits are required in Colorado, North Carolina, Rhode Island and Virginia. These store voting machines' interpretation of each ballot ("cast vote record"), collect them centrally over the internet, re-tally them with an independent computer to check totals, and hand-check a sample of the stored paper ballots to check voting machines' interpretations. Samples are big enough to be sure results are accurate, up to an acceptable level of risk, such as 9%. For each audited contest, if the original computer interpretations identified the wrong winner, there is a 9%
chance in Colorado that the audit will miss it, and the wrong winner will take office. A lower risk limit would let fewer errors through, but would require larger sample sizes. Close contests also require larger sample sizes. Colorado audits only a few contests, and audits none of the closest contests, which need the biggest samples. Auditing all contests would require several counties to hand-count thousands of ballots each.
If the samples do not confirm the initial results, more rounds of sampling may be done, but if it appears the initial results are wrong, risk-limiting audits require a 100% hand count to change the result, even if that involves hand-counting hundreds of thousands of ballots.
Colorado notes that they have to be extremely careful to keep ballots in order, or they have to number them, to be sure of comparing the hand counts with the machine records of those exact ballots. Colorado says it has a reliable system to re-tally the records, but it is not yet publicly documented.
In 2010, the American Statistical Association
The American Statistical Association (ASA) is the main professional organization for statisticians and related professionals in the United States. It was founded in Boston, Massachusetts on November 27, 1839, and is the second oldest continuousl ...
endorsed risk-limiting audit
A risk-limiting audit (RLA) is a post-election tabulation auditing procedure which can limit the risk that the reported outcome in an election contest is incorrect. It generally involves (1) storing voter-verified paper ballots securely until they ...
s, to verify election outcomes. With use of statistical sampling to eliminate the need to count all the ballots, this method enables efficient, valid confirmation of the outcome (the winning candidates). In 2011, the federal Election Assistance Commission
The Election Assistance Commission (EAC) is an independent agency of the United States government created by the Help America Vote Act of 2002 (HAVA). The Commission serves as a national clearinghouse and resource of information regarding elect ...
initiated grants for pilot projects to test and demonstrate the method in actual elections. In 2014, the Presidential Commission on Election Administration recommended the method for use in all jurisdictions following all elections, to reduce the risk of having election outcomes determined by undetected computer error or fraud. In 2017Colorado became the first state to implement
risk-limiting audits statewide as a routine practice during the post-election process of certifying election results.
Ballot scans for 100% audits

 Humboldt Count
Humboldt CountElections Transparency Project
an
TrueBallot
scan all ballots with a commercial scanner, so extensive audits can be done on the scans without damaging paper ballots, without hand-counting, by multiple groups, independently of the election software. Clear Ballot is certified by the US Election Assistance Commission for voting, and they also have an auditing system, ClearAudit. TrueBallot does not currently serve government elections, just private groups. Both use proprietary software, so if it were hacked at the vendor or locally to create false images of the ballots or false counts, then local officials and the public could not check it. The "Brakey method" is an approach using electronic ballot images already created by most current US election systems. These ballot images could be hacked if the election software itself is hacked, either at the vendor or elsewhere, so for full security, ballot images need to be checked against the paper ballots, to determine if the images are accurate. To enable this one to one ballot-image comparison, the Brakey Method requires that the ballot images be linkable to their paper ballots, either by keeping paper ballots in the same order as the scans, or through a unique identifier that appears on both digital image and physical ballot. Independent systems to tally ballot images include Audit Engine, Free and Fair, OSET Institute (under development), and the Elections Transparency Project, as used in Humboldt County, California, a medium sized county with 58,000 ballots in the 2016 general election. Humboldt uses a commercial scanner to scan all ballots and puts them in a digitally signed file, so true copies of the file can be reliably identified. Ballots with identifying marks are first hand-copied by election staff, to anonymize them, since they are valid under California law. The scanner prints a number on each ballot before scanning it, so the scan can be checked against the same physical ballot later if needed. The project has written open source software (Trachtenburg Election Verification Software, TEVS) to read the files, and they check all contests on all ballots to see if official counts are correct. The first time they scanned and checked, in 2008, they found 200 missing ballots, showing the value of complete checks. Other jurisdictions can similarly scan ballots and use Humboldt's software or their own to audit all contests. They need to ensure their in-house counting software is secure and independent of any bugs or hacks in the election software, just as users of risk-limiting audits do. Reading these scans, with software independent of the election system, is a practical way to audit a large number of close contests, without large hand counts. Scans are also the only practical way to bypass problems of physical security, if paper ballots are scanned, digitally signed, and the resulting electronic records are verified against a sample of paper ballots, as ballots arrive. Scans can be made and digitally signed before ballots are stored, while other audit methods are too slow to do election night. Scanners can process thousands of ballots per hour, and several scanners can operate simultaneously in larger jurisdictions. Once ballots are scanned and a digital signature is published, electronic records can be tallied at any convenient time. Humboldt and several other jurisdictions have gone beyond this internal approach, and release the digitally signed files of ballot images to the public, so others can use their own software, independent of the election system and officials, to check all contests on all ballots. Public release lets losing candidates who mistrust the election officials' security measures do their own checks. Humboldt County believes the scans give their citizens high confidence in the county election results.
Recounts
''Recounts'' may be considered to be a specific type of audit, but not all audits are recounts. TheVerified Voting Foundation
The Verified Voting Foundation is a non-governmental, nonpartisan organization founded in 2004 by David L. Dill, a computer scientist from Stanford University, focused on how technology impacts the administration of US elections. The organization ...
explains the difference between audits and recounts: Post-election audits are performed to “routinely check voting system performance…not to challenge to the results, regardless of how close margins of victory appear to be", while "recounts repeat ballot counting (and are performed only) in special circumstances, such as when preliminary results show a close margin of victory. Post-election audits that detect errors can lead to a full recount.” In the US, recount laws vary by state, but typically require recounting 100% of the votes, while audits may use samples. Recounts incorporate elements of both results and process audits.
Other variations
 Hand and machine counts. Current audits in most states involve counting paper ballots by hand, but some states re-use the same machines used in the election. Three states use different machines, to provide some independent check.
Sample sizes. When states audit, they usually pick a random sample of 1% to 10% of precincts to recount by hand or by machine. If a precinct has more than one machine, and they keep ballots and totals separate by machine, they can draw a sample of machines rather than precincts and count all ballots processed by that machine. These samples can identify systematic errors widely present in the election. They have only a small chance of catching a hack or bug which was limited to a few precincts or machines, even though that could change the result in close contests.
Number of contests. In the random sample, most states audit only a few contests, so they can only find problems in those contests.
Hand and machine counts. Current audits in most states involve counting paper ballots by hand, but some states re-use the same machines used in the election. Three states use different machines, to provide some independent check.
Sample sizes. When states audit, they usually pick a random sample of 1% to 10% of precincts to recount by hand or by machine. If a precinct has more than one machine, and they keep ballots and totals separate by machine, they can draw a sample of machines rather than precincts and count all ballots processed by that machine. These samples can identify systematic errors widely present in the election. They have only a small chance of catching a hack or bug which was limited to a few precincts or machines, even though that could change the result in close contests.
Number of contests. In the random sample, most states audit only a few contests, so they can only find problems in those contests.
Ballot transport and storage
Auditing is done several days after the election, so paper ballots and computer files need to be kept securely. North Carolina specifies that no audit is done if ballots are missing or damaged. Ballots are at risk when being transported from drop boxes and polling places to central locations, and may be protected by GPS tracking, guards, security systems, and/or a convoy of the public. Auditing in the US is done several days after the election, so paper ballots and computer files need to be stored securely. No US state has adequate laws on physical security of the ballots, and few localities do. 2008 guidelines for audits included starting audits as soon as possible after the election. 2018 guidelines recommend waiting until all ballots are counted, which in the US means one or more weeks until provisional ballots are adjudicated. A faster start for the audit makes it feasible for independent parties to guard storage sites. Security recommendations include preventing access by anyone alone, which would typically require two hard-to-pick locks, and having keys held by independent officials if such officials exist in the jurisdiction; having storage risks identified by people other than those who design or manage the system; and using background checks on staff. Physical security of stored paper ballots is particularly important between the time the random sample is selected and when the corresponding ballots are examined, to prevent adjusting the ballots to match erroneous electronic records. Neither Colorado nor California has any limit on how much time can pass. Michigan allows two weeks from the time the sample is identified to the time local election officials must audit them. Britain, Canada, France, Germany, Spain and other countries count all ballots on election night, including final decisions on questionable ballots, so final counts happen before ballots go into storage. Canada and France sometimes use election machines with paper trails. In these cases risk-limiting audits could be done as soon as results are announced on election night. If audits cannot be done on election night, creating and verifying a paper or electronic backup of the paper ballots on election night, or the next day as in Florida, would provide an alternative benchmark if flaws are later discovered or suspected in the primary storage of paper ballots. Electronic copies in particular can be stored in safes or safe deposit boxes and/or distributed widely, with hash codes to ensure reliability. Election storage often uses tamper-evident seals, although seals can typically be removed and reapplied without damage, especially in the first 48 hours. Photos taken when the seal is applied can be compared to photos taken when the seal is opened. Detecting subtle tampering requires substantial training. Election officials usually take too little time to examine seals, and the public is too far away to check seal numbers, though they could compare old and new photos projected on a screen. Seal numbers and photos would need their own secure storage. Experienced testers can usually bypass all physical security systems. Locks and cameras are vulnerable before and after delivery. Since 1850, people have known how to create a master key from any key in a building, such as a borrowed restroom key. Attackers who cannot find key blanks can 3D-print them from a photo of the lock. Insider threats and the difficulty of following all security procedures are usually under-appreciated, and most organizations do not want to learn their vulnerabilities. When a contractor found poor security at county buildings in Iowa, the state ordered no more testing of security.Sample breaches of election storage
Breaches of election security which have been identified, have primarily been done by insiders. *2017 Broward County, FL (Fort Lauderdale) elections staff erroneously destroyed paper ballots from an August 2016 primary. A court case was pending to gain access to them. *2017 In Georgia, elections were centrally programmed by Kennesaw State University. Four days after a lawsuit over election records was files, they erased the election records from their server. Later, the day after this case moved to federal court, they erased their backup. *2016 Clark County (Las Vegas), NV, Registrar of Voters opened ballot boxes in secret, did a secret recount before the public one, and hid the results. The Registrar said, "You're asking what my results were when we practiced? I can't tell you that.". *2010 Saguache County, CO Clerk and two judges hand-tallied ballots without public notice. They were discovered on security cameras. *2007-2009 Cudahy, CA, city officials threw away, uncounted, ballots for candidates running against city council members. *2007 Cuyahoga County (Cleveland), OH election workers were convicted of going through locked ballots to ensure an audit would not find errors in the election. They testifiecf "that the board had always done things that way - with the knowledge of its attorney," . *2002-2007 Clay County, KY, election officials falsified election results and destroyed forms which showed they helped voters, since the voters they helped were being paid to vote certain ways. *1993 Philadelphia, PA, election board did not keep absentee ballots which had been rejected, from unregistered voters, and turned them over to the campaign which collected them.Notes
References
{{ReflistExternal links
Election Verification Network
Verified Voting
Principles and Best Practices for Election Auditing
Elections