snowflake (software) on:
[Wikipedia]
[Google]
[Amazon]
 Snowflake is a software package for assisting others in circumventing internet censorship by relaying data requests. Snowflake relay nodes are meant to be created by people in countries where Tor and Snowflake are not blocked. People under censorship then use a Snowflake client, packaged with the Tor Browser or Onion Browser, to access the Tor network, using Snowflake relays as
Snowflake is a software package for assisting others in circumventing internet censorship by relaying data requests. Snowflake relay nodes are meant to be created by people in countries where Tor and Snowflake are not blocked. People under censorship then use a Snowflake client, packaged with the Tor Browser or Onion Browser, to access the Tor network, using Snowflake relays as
 Normal internet data packages come labelled with the original source and the final recipient of the data. For example, a package containing the encrypted text of this article would be labelled with the destination (the
Normal internet data packages come labelled with the original source and the final recipient of the data. For example, a package containing the encrypted text of this article would be labelled with the destination (the
Live graph of user numbers
filterable by country of origin and transports (of which Snowflake is one) Tor (anonymity network) 2016 software
 Snowflake is a software package for assisting others in circumventing internet censorship by relaying data requests. Snowflake relay nodes are meant to be created by people in countries where Tor and Snowflake are not blocked. People under censorship then use a Snowflake client, packaged with the Tor Browser or Onion Browser, to access the Tor network, using Snowflake relays as
Snowflake is a software package for assisting others in circumventing internet censorship by relaying data requests. Snowflake relay nodes are meant to be created by people in countries where Tor and Snowflake are not blocked. People under censorship then use a Snowflake client, packaged with the Tor Browser or Onion Browser, to access the Tor network, using Snowflake relays as proxy server
In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
Instead of connecting directly to a server that can fulfill a reques ...
s. Access to the Tor network can in turn give access to other blocked services (like blocked websites). A Snowflake node can be created by either installing a browser extension, installing a stand-alone program, or browsing a webpage with an embedded Snowflake relay. The node runs whenever the browser or program is connected to the internet.
Tor relays content requests through a chain of Tor nodes, including Snowflake nodes (onion routing
Onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of net ...
). Each node in the chain only knows the addresses of the two adjacent links and cannot decrypt any of the other data it is relaying, which makes tracking or blocking the traffic much more difficult. A common countermeasure is blocking Tor nodes; the number and shifting nature of the Snowflake nodes make identifying and blocking connections to these nodes more difficult.
Tor is itself illegal in some countries. Like the internet, it can relay any sort of content, and some types of content are illegal in some countries.
History
Snowflake was originated by Serene, a hacker and former Google engineer and concert pianist. The name "Snowflake" was coined as her metaphor for a large number of ephemeral proxies in relation to " ICE Negotiation". Three programmers published the first version in January 2016. In 2019, it became available as abrowser extension
A browser extension is a small software module for customizing a web browser. Browsers typically allow a variety of extensions, including user interface modifications, cookie management, ad blocking, and the custom scripting and styling of web ...
for Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current ...
and Chrome.It can also be run on derived browsers, such as Brave and Microsoft Edge
Microsoft Edge is a proprietary, cross-platform web browser created by Microsoft. It was first released in 2015 as part of Windows 10 and Xbox One and later ported to other platforms as a fork of Google's Chromium open-source project: Android ...
. In February 2023 a thoroughly upgraded, stand-alone version dubbed ''Snowstorm'' was released; written in Rust
Rust is an iron oxide, a usually reddish-brown oxide formed by the reaction of iron and oxygen in the catalytic presence of water or air moisture. Rust consists of hydrous iron(III) oxides (Fe2O3·nH2O) and iron(III) oxide-hydroxide (FeO( ...
and funded by the Open Tech Fund, beta testing is by invitation.
Function
 Normal internet data packages come labelled with the original source and the final recipient of the data. For example, a package containing the encrypted text of this article would be labelled with the destination (the
Normal internet data packages come labelled with the original source and the final recipient of the data. For example, a package containing the encrypted text of this article would be labelled with the destination (the IP address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface ident ...
of the reader's computer), and the source (the IP address of a Wikipedia server). This means that even if the actual content is encrypted, a censor can block all packages from certain sources (for instance, banning any package that comes from Wikipedia).
By contrast, Tor connections relay encrypted traffic though a chain of proxies. Each link only knows the addresses of the two adjacent links, which makes tracking the traffic much more difficult. The message in encrypted in layers, so it is called onion routing
Onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of net ...
. A physical analogy would be sealing an envelope carrying the real message inside a nested set of envelopes, so that each envelope had a different address on it; each server opens the outermost envelope, addressed to it, and passes the remaining package on to the address thus exposed. Since the source of the content is hidden behind layers of proxy servers, banned sources can still be accessed, and it isn't clear which recipient accessed what content.
Since Tor can be used to access banned websites, some countries, such as Iran
Iran, officially the Islamic Republic of Iran, and also called Persia, is a country located in Western Asia. It is bordered by Iraq and Turkey to the west, by Azerbaijan and Armenia to the northwest, by the Caspian Sea and Turkmeni ...
and Russia
Russia (, , ), or the Russian Federation, is a transcontinental country spanning Eastern Europe and Northern Asia. It is the largest country in the world, with its internationally recognised territory covering , and encompassing one-ei ...
, ban the Tor network. This means that Tor users can't simply connect to a publicly-known Tor entry node; all known Tor nodes will be blocked by the censors. Instead, users connect to a Tor bridge, a server which is secretly a Tor entry point. Censors, in turn, seek to identify and block Tor bridges, identifying them using deep packet inspection
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and may take actions such as alerting, blocking, re-routing, or logging it accordingly. Deep packet inspection is oft ...
.
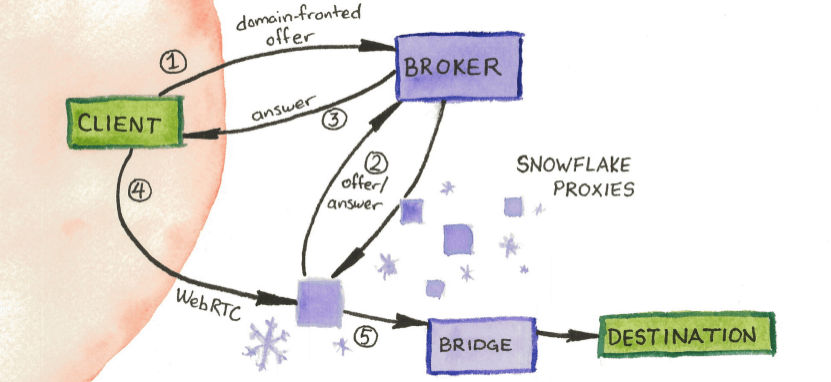
Snowflake provides a large number of ever-shifting Tor entry nodes. A user is provided with the IP address of a currently-active Snowflake node by asking a broker server, which in turn uses domain fronting
Domain fronting is a technique for Internet censorship circumvention that uses different domain names in different communication layers of an HTTPS connection to discreetly connect to a different target domain than is discernable to third parties ...
to pretend to be a major website. The user then talks directly to the Snowflake node, which relays into the Tor network. The traffic looks like ordinary peer-to-peer traffic, such as that used by many videoconferencing apps.
A Snowflake node runs whenever the browser or program is connected to the internet. If the node host has a dynamic IP, the node will change its IP address over time. See also ad hoc network An ad hoc network refers to technologies that allow network communications on an ad hoc basis. Associated technologies include:
*Wireless ad hoc network
*Mobile ad hoc network
* Vehicular ad hoc network
** Intelligent vehicular ad hoc network
* Prot ...
.
Snowflake nodes are thus used as Tor entry nodes, not as exit nodes. Exit nodes are the other end of the chain. They are the Tor nodes that know what content was requested, though they do not know who requested it (for instance, they would know that a user was contacting a Wikipedia server, but they would not know the IP address of the user). Exit nodes might face legal action in the country in which they are hosted if they relay content that is illegal in that country (so they are usually run in countries with little internet censorship). It is unlikely that Snowflake node hosts could face such liability, since they do not know what content they are relaying. There are, however, countries where using Tor for any purpose is illegal, such as Russia and Iran.
Technical
Snowflake usesWebRTC
WebRTC (Web Real-Time Communication) is a free and open-source project providing web browsers and mobile applications with real-time communication (RTC) via application programming interfaces (APIs). It allows audio and video communication to wor ...
to allow browsers to communicate directly with one another. Either installing a browser extension, or keeping a tab open to a webpage with the right embedded code, causes one's browser to act as a relay. Embedding a Snowflake badge in a website allows visitors to make their browser into a relay, exactly as installing the extension does, but by clicking a button on the website rather than by installing software. Snowflake can also be run as a stand-alone program in a Docker container.
Relaying traffic increases the node host's bandwidth
Bandwidth commonly refers to:
* Bandwidth (signal processing) or ''analog bandwidth'', ''frequency bandwidth'', or ''radio bandwidth'', a measure of the width of a frequency range
* Bandwidth (computing), the rate of data transfer, bit rate or thr ...
usage, which may be a problem for those with bandwidth limits on their internet plans. In practice, hosting a node does not seem to appreciably slow one's internet connection or disrupt browsing.
A detailed technical description is published on GitLab
GitLab Inc. is an open-core company that operates GitLab, a DevOps software package which can develop, secure, and operate software. The open source software project was created by Ukrainian developer Dmitriy Zaporozhets and Dutch developer ...
.
Countermeasures
Countermeasures believed to be currently in use against Snowflake from Russia includebrowser fingerprinting
A device fingerprint or machine fingerprint is information collected about the software and hardware of a remote computing device for the purpose of identification. The information is usually assimilated into a brief identifier using a fingerprinti ...
Snowflake hosts and then blocking them. Censors may also install and use Tor, then block all the IP addresses offered as Snowflake servers. Both of these techniques are weakened when there are larger numbers of servers.
Censors may attempt to block the broker's IP address. To circumvent this, the Snowflake client utilizes domain fronting
Domain fronting is a technique for Internet censorship circumvention that uses different domain names in different communication layers of an HTTPS connection to discreetly connect to a different target domain than is discernable to third parties ...
. This makes it infeasible for the censor to block a single website without blocking all the other websites hosted on the same cloud service. Google and Amazon are examples of such services. They host hundreds of thousands of websites. Blocking all the servers of one of these major hosts has disruptive side effects. However, the cloud provider can and often does block domain fronting.
If overseas connections from data centers are allowed, but residential and mobile services are restricted to local connections, then Tor bridges may be secretly and illegally set up in local data centers. This has obvious dangers.
When a country shuts down access to foreign internet connections altogether, essentially cutting the country off from the global internet, Snowflake becomes useless. This has been repeatedly done in Iran and some other countries; it is, however, bad for business (in Iran in 2022, the cost was estimated at $37 million US a day), so it is usually only done for short periods.
Comparison to VPNs
A simple proxy, like avirtual private network
A virtual private network (VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The b ...
(VPN), has only a single relay. This means that the server address of the VPN has to be known to every user, making it easier to block. For instance, at the beginning of October 2022, during internet disruptions related to the Mahsa Amini protests
Civil unrest and protests against the government of Iran associated with the death in police custody of Mahsa Amini ( fa, مهسا امینی) began on 16 September 2022 and are ongoing as of December 2022. Amini had been arrested by the Guida ...
, VPNs in Iran would drop connections every few minutes. The VPN itself also knows which end-users requested which pages, allowing VPNs to engage in surveillance. In some countries, such as Iran, VPNs are illegal and may be government-affiliated.
Uses
Snowflake came to be widely discussed online in the first week of October 2022, as a way of combatting internet restrictions in Iran during theMahsa Amini protests
Civil unrest and protests against the government of Iran associated with the death in police custody of Mahsa Amini ( fa, مهسا امینی) began on 16 September 2022 and are ongoing as of December 2022. Amini had been arrested by the Guida ...
, and a guide in Persian was released.
In 2022, the Russian government increased efforts to block access to Tor through technical and political means, and the Tor network reported an increase in traffic from Russia using Snowflake.
Snowflake is integrated into the Tor network. Usage of the Tor network is becoming more common in Russia, Belarus, and Iran, , as internet censorship in these countries has become more strict. It is also used by criminals involved in child pornography, drug trade, terrorism, and money laundering.
See also
*Psiphon
Psiphon is a free and open-source Internet censorship circumvention tool that uses a combination of secure communication and obfuscation technologies, such as a VPN, SSH, and a Web proxy. Psiphon is a centrally managed and geographically dive ...
uses a variety of anticensorship techniques
*Smartphone ad hoc network
Smartphone ad hoc networks (SPANs; also ''smart phone ad hoc networks'') are wireless ad hoc networks that use smartphones. Once embedded with ad hoc networking technology, a group of smartphones in close proximity can together create an ad hoc ...
, a peer-to-peer system that can be used when the conventional internet infrastructure is entirely shut down
**Briar (software)
Briar is an open-source software communication technology, intended to provide secure and resilient peer-to-peer communications with no centralized servers and minimal reliance on external infrastructure. Messages can be transmitted through Blueto ...
uses Tor
*Sneakernet
Sneakernet, also called sneaker net, is an informal term for the transfer of electronic information by physically moving media such as magnetic tape, floppy disks, optical discs, USB flash drives or external hard drives between computers, rather ...
, a technique widely used in countries with little internet access.
*Toosheh
Toosheh ( in Persian)Murphy, David. “Toosheh Uses Satellite TV to Sneak Content Past Iranian Censorship.” ''PCMAG'', 24 Apr. 2016, www.pcmag.com/news/343972/toosheh-uses-satellite-tv-to-sneak-content-past-iranian-cens. Retrieved 1 March 2018. ...
uses satellite TV receiving equipment to download (but not upload) files, which are then sometimes sneakernet
Sneakernet, also called sneaker net, is an informal term for the transfer of electronic information by physically moving media such as magnetic tape, floppy disks, optical discs, USB flash drives or external hard drives between computers, rather ...
ted.
References
{{reflist, refs= {{cite web , title=Tor Snowflake turns your browser into a proxy for users in censored countries, first=Catalin, last=Cimpanu, date=October 16, 2019, url=https://www.zdnet.com/article/tor-snowflake-turns-your-browser-into-a-proxy-for-users-in-censored-countries/ , website=ZDNET , language=en {{Cite web, url=https://www.forbes.com/sites/johanmoreno/2023/02/08/as-the-internet-freedom-project-expands-snowflake-becomes-snowstorm/, title=As The Internet Freedom Project Expands, Snowflake Becomes Snowstorm, date=Feb 8, 2023, first=Johan, last=Moreno, website=Forbes {{cite magazine, url=https://www.wired.com/story/tor-browser-russia-blocks/ , title=How Tor Is Fighting—and Beating—Russian Censorship , first=Matt , last=Burgess , magazine=WIRED
''Wired'' (stylized as ''WIRED'') is a monthly American magazine, published in print and online editions, that focuses on how emerging technologies affect culture, the economy, and politics. Owned by Condé Nast, it is headquartered in San ...
, date=July 28, 2022 , access-date=2022-07-30
{{cite web , title=Iran's 'Smart' Instagram Censorship Isn't That Smart, date=May 7, 2015 , url=https://www.vice.com/en/article/4x38kd/irans-smart-instagram-censorship-isnt-that-smart , website=Vice News , language=en , last1=Franceschi-Bicchierai , first1=Lorenzo
{{cite news , last1=Dou , first1=Eva , last2=Barr , first2=Alistair, date=March 16, 2015 , title=U.S. Cloud Providers Face Backlash From China's Censors , url=https://www.wsj.com/articles/u-s-cloud-providers-face-backlash-from-chinas-censors-1426541126 , work=WSJ
{{cite news , last1=Schwarzer , first1=Matthias , title=Netzsperre im Iran umgehen: Wie "Snowflake" einen Weg ins freie Internet ermöglicht - so kann der Westen helfen , url=https://www.rnd.de/digital/netzsperre-im-iran-umgehen-wie-snowflake-einen-weg-ins-freie-internet-ermoeglicht-so-kann-der-westen-SE3LNI5BKNHJHGJJK2UZHWHXRA.html , access-date=10 October 2022 , work=RedaktionsNetzwerk Deutschland
The (RND) () is the Hanover-based joint corporate newsroom of German . The biggest limited partner of Madsack is the , which is fully owned by the Social Democratic Party of Germany (SPD).
Madsack has the majority in regional newspapers with a ...
, date=30 September 2022 , language=de
External links
Live graph of user numbers
filterable by country of origin and transports (of which Snowflake is one) Tor (anonymity network) 2016 software