Overview
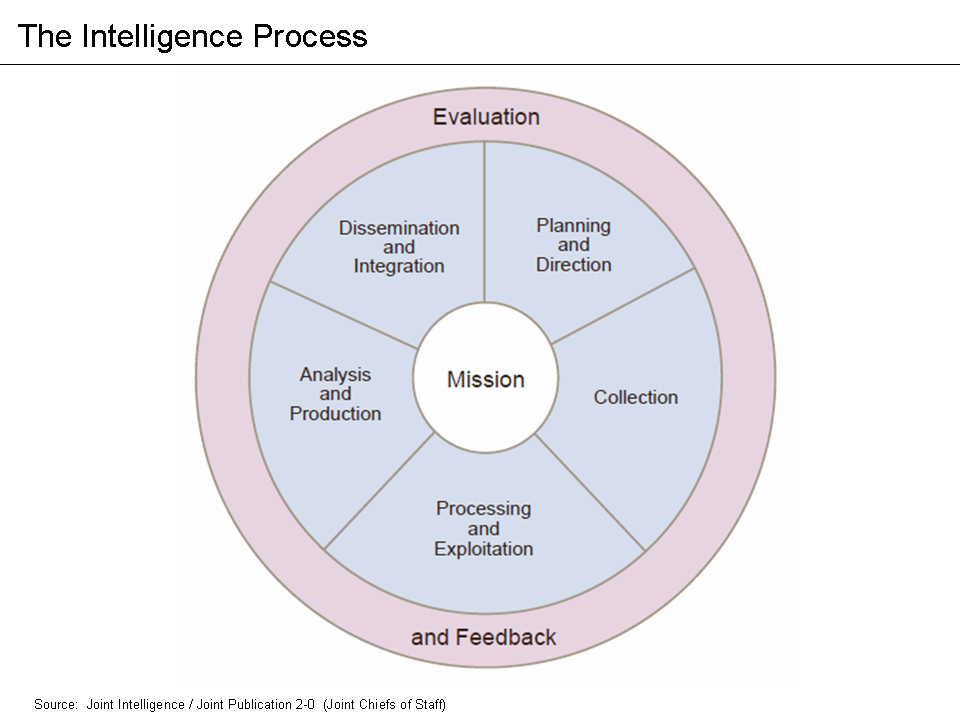 Intelligence analysis is a way of reducing the ambiguity of highly ambiguous situations. Many analysts prefer the middle-of-the-road explanation, rejecting high or low probability explanations. Analysts may use their own standard of proportionality as to the risk acceptance of the opponent, rejecting that the opponent may take an extreme risk to achieve what the analyst regards as a minor gain. The analyst must avoid the special cognitive traps for intelligence analysis projecting what she or he wants the opponent to think, and using available information to justify that conclusion. Being aware that one's enemies may try to confuse is a relevant factor, especially in the areas of
Intelligence analysis is a way of reducing the ambiguity of highly ambiguous situations. Many analysts prefer the middle-of-the-road explanation, rejecting high or low probability explanations. Analysts may use their own standard of proportionality as to the risk acceptance of the opponent, rejecting that the opponent may take an extreme risk to achieve what the analyst regards as a minor gain. The analyst must avoid the special cognitive traps for intelligence analysis projecting what she or he wants the opponent to think, and using available information to justify that conclusion. Being aware that one's enemies may try to confuse is a relevant factor, especially in the areas of Analytic tradecraft
The body of specific methods for intelligence analysis is generally referred to as analytic tradecraft. The academic disciplines examining the art and science of intelligence analysis are most routinely referred to as "Intelligence Studies", and exemplified by institutions such as the Joint Military Intelligence College, University of Pittsburgh Graduate School of Public and International Affairs (Security and Intelligence Studies major), and Mercyhurst College Institute for Intelligence Studies. The goal of the Analytic Tradecraft Notes of theSetting goals for an intelligence analysis
Stating the objective from the consumer's standpoint is an excellent starting point for goal-setting: More charitably, he now characterizes his early periods of service at the NSC Staff and in State Department bureaus as ones of "mutual ignorance"Be bold and honest
Weasel-wording is problematic in intelligence analysis; still, some things truly are uncertain. Arguably, when uncertainties are given with probabilities or at least some quantification of likelihood, they become less a case of weasel wording and more a case of reflecting reality as it is best understood. While a good analyst must be able to consider, thoughtfully, alternative viewpoints, an analyst must be willing to stand by his or her position. This is especially important in specialized areas, when the analyst may be the only one that reads every field report, every technical observation on a subject. "Believe in your own professional judgments. Always be willing to listen to alternative conclusions or other points of view, but stand your ground if you really believe the intelligence supports a certain conclusion. Just because someone is your boss, is a higher grade, or has been around longer than you does not mean he or she knows more about your account than you do. You are the one who reads the traffic every day and who studies the issue". At the same time, Watanabe observes, "It is better to be mistaken than wrong". Not willing to be wrong is also a disease of the highest policymaker levels, and why there needs to be a delicately balanced relationship, built of trust, between a policymaker and his closest intelligence advisors. "Being an intelligence analyst is not a popularity contest...But your job is to pursue the truth. I recall a colleague who forwarded an analysis that called into question the wisdom behind several new US weapon systems. This analysis caused criticism of the CIA, of his office, and of himself. He stood his ground, however; the Agency supported him, and eventually he was proven right. He did not make a lot of friends, but he did his job. Intelligence analysts are expected to give policymakers' opinions both support and reality checks. The most effective products have several common features: *Opportunities and dangers for interests of the analyst's country, especially unexpected developments that may require a reaction. * Motives, objectives, strengths, and vulnerabilities of adversaries, allies, and other actors. * Direct and indirect sources of friendly parties' leverage on foreign players and issues. * Tactical alternatives for advancing stated national policy goals. Reality checking is not to be underestimated. In World War II, the Allies launched an air offensive against a target system that they really did not understand: the V-1 cruise missile. Their rationale to attack ("if the enemy apparently valued it, then it must be worth attacking") may have been rational when there were large numbers of aircraft and pilots, but it might not be applicable to current situations, at least not until analysts rule out the possibility of the target system being a decoy. If the threat is real, then it might be warranted to defer attack until a massive one can be delivered.Agreement on content
The analytic process must be interactive with the customer to succeed. For example, the first IMINT of Soviet missiles during the As the White House requested more CIA and Navy support for photography, it simultaneously searched for
As the White House requested more CIA and Navy support for photography, it simultaneously searched for Orienting oneself to the consumers
Experienced analysts recommend seeing oneself as a specialist on a team, with 5–10 key players. Learn something about each of them, both in terms of how they express themselves, and how you can reinforce their strengths and support their weaknesses. The analyst must constantly ask himself, "what do they want/need to know? How do they prefer to have it presented? Are they still trying to select the best course of action, or have they committed and now need to know the obstacles and vulnerabilities on their chosen path?" Others on the team may know, how to handle the likely challenges. The analyst's contribution is in recognizing the unlikely, or providing connections that are not obvious. Consumers must get information in a timely manner, not after they commit to a decision they might not have made having rougher information available sooner. Sometimes, when the producer is struggling with how to meet the needs of both internal and external customers, the solution is to create two different types of products, one for each type of customer. An internal product might contain detail of sources, collection methods, and analytic techniques, while an external product is more like journalism. Remember that journalists always address: #Who #What #When #Where #Why "How" is often relevant to journalists, but, in intelligence, may wander into that delicate area of sources and methods, appropriate only for internal audiences. The external consumer needs to know more of potential actions. Actions exist in three phases: #The decision to act #The action #Disengagement from the action Internal products contain details about the sources and methods used to generate the intelligence, while external products emphasize actionable target information. Similarly, the producer adjusts the product content and tone to the customer's level of expertise.Orienting oneself to peers
Even in professional sports, where there are strict anti-fraternization rules on the playing field, players often have deep friendships with counterparts on opposing teams. They might have been on a college team together, or are simply aware that the team they oppose today might be the team to which they might be traded tomorrow. If a technique is personal, rather than a proprietary idea of a coach, one professional might be quite willing to show a nominal opponent how he does some maneuver. Watanabe observedPeers, both consumer and analyst, also have a psychological context. Johnston suggests the three major components of that context are: #socialization #degree of risk taking or risk aversion #organizational-historical context Devlin observes that while traditional logical work does not consider socialization, work on extending logic into the real world of intelligence requires it. "The first thing to note, and this is crucial, is that the process by which an agent attaches meaning to a symbol always takes place in a context, indeed generally several contexts, and is always dependent on those contexts. An analytic study of the way that people interpret symbols comes down to an investigation of the mechanism captured by the diagram:If you are examining a problem and there is no intelligence available, or the available intelligence is insufficient, be aggressive in pursuing collection and in energizing collectors. ... As an analyst, you have the advantage of knowing both what the consumer needs to know (sometimes better than the consumer knows himself) and which collectors can obtain the needed intelligence.
Aggressively pursue collection of information you need. In the Intelligence Community, we have the unique ability to bring substantial collection resources to bear in order to collect information on important issues. An analyst needs to understand the general capabilities and limitations of collection systems...If the analyst is in a technical discipline, the analyst might have an insight about a collection system that the operators have not considered ... If you are not frequently tasking collectors and giving them feedback on their reporting, you are failing to do an important part of your job.
gent+ ymbol+ ontext+. . . + ontext→ nterpretation/code>
Things that are true about contexts include:
#Contexts are pervasive
#Contexts are primary
#Contexts perpetuate
#Contexts proliferate
#Contexts are potentially pernicious
The discipline of critical discourse analysis will help organize the context. Michael Crichton
John Michael Crichton (; October 23, 1942 – November 4, 2008) was an American author, screenwriter and filmmaker. His books have sold over 200 million copies worldwide, and over a dozen have been adapted into films. His literary works heavil ...
, in giving examples of physicians communicating with other physicians, points out that laymen have trouble following such discourses not only because there is specialized vocabulary in use, but the discourse takes place in an extremely high context. One physician may ask a question about some diagnostic test, and the other will respond with a result from an apparently unrelated test. The shared context was that the first test looked for evidence of a specific disease, while the answer cited a test result that ruled out the disease. The disease itself was never named, but, in the trained context, perfectly obvious to the participants in the discourse.
Intelligence analysis is also extremely high context. Whether the subject is political behavior or weapons capabilities, the analysts and consumers share a great deal of context. Intelligence consumers express great frustration with generic papers that waste their time by giving them context they already have internalized.
Organizing what you have
Collection processes provide analysts with assorted kinds of information, some important and some irrelevant, some true and some false (with many shades in between), and some requiring further preprocessing before they can be used in analysis. Raw information reports use a standard code for the presumed reliability of the source and of the information. The U.S. Intelligence Community uses some formal definition of the kinds of information.
Collation
Collation is the assembly of written information into a standard order. Many systems of collation are based on numerical order or alphabetical order, or extensions and combinations thereof. Collation is a fundamental element of most office fi ...
describes the process of organizing raw data, interpolating known data, evaluating the value of data, putting in working hypotheses. The simplest approaches often are an excellent start. With due regard for protecting documents and information, a great deal can be done with pieces of paper, a whiteboard, a table, and perhaps a corkboard. Maps often are vital adjuncts, maps that can be written upon.
There are automated equivalents of all of these functions, and each analyst will have a personal balance between manual and machine-assisted methods. Unquestionably, when quantitative methods such as modeling and simulation
A simulation is an imitative representation of a process or system that could exist in the real world. In this broad sense, simulation can often be used interchangeably with model. Sometimes a clear distinction between the two terms is made, in ...
are appropriate, the analyst will want computer assistance, and possibly consultation from experts in methodology. When combining maps and imagery, especially different kinds of imagery, a geographic information system
A geographic information system (GIS) consists of integrated computer hardware and Geographic information system software, software that store, manage, Spatial analysis, analyze, edit, output, and Cartographic design, visualize Geographic data ...
is usually needed to normalize coordinate systems, scale and magnification, and the ability to suppress certain details and add others.
Outlining, possibly in a word processing program, or using visualization tools such as mind maps can give structure, as can file folders and index cards. Data bases, with statistical techniques such as correlation
In statistics, correlation or dependence is any statistical relationship, whether causal or not, between two random variables or bivariate data. Although in the broadest sense, "correlation" may indicate any type of association, in statistics ...
, factor analysis
Factor analysis is a statistical method used to describe variability among observed, correlated variables in terms of a potentially lower number of unobserved variables called factors. For example, it is possible that variations in six observe ...
, and time series analysis
In mathematics, a time series is a series of data points indexed (or listed or graphed) in time order. Most commonly, a time series is a sequence taken at successive equally spaced points in time. Thus it is a sequence of discrete-time data. ...
can give insight.
 Some analysts speak of a Zen-like state in which they allow the data to "speak" to them. Others may meditate, or even seek insight in dreams, hoping for an insight such as that given to August Kekulé
Friedrich August Kekulé, later Friedrich August Kekule von Stradonitz ( , ; 7 September 1829 – 13 July 1896), was a German organic chemist. From the 1850s until his death, Kekulé was one of the most prominent chemists in Europe, especially ...
Some analysts speak of a Zen-like state in which they allow the data to "speak" to them. Others may meditate, or even seek insight in dreams, hoping for an insight such as that given to August Kekulé
Friedrich August Kekulé, later Friedrich August Kekule von Stradonitz ( , ; 7 September 1829 – 13 July 1896), was a German organic chemist. From the 1850s until his death, Kekulé was one of the most prominent chemists in Europe, especially ...
in a daydream that resolved one of the fundamental structural problems of organic chemistry.
Krizan took criteria from. Regardless of its form or setting, an effective collation method will have the following
attributes:
#Be impersonal. It should not depend on the memory of one analyst; another person knowledgeable in the subject should be able to carry out the operation.
#Not become the "master" of the analyst or an end in itself.
#Be free of bias in integrating the information.
#Be receptive to new data without extensive alteration of the collating criterion.
Semantic maps are related to mind maps, but are more amenable to computer discovery of relationships.
 The more interactive that the relationship between producer and consumer becomes, the more important will be tools:
:* Collaboration tools. These include all media: voice, video, instant messaging
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involv ...
The more interactive that the relationship between producer and consumer becomes, the more important will be tools:
:* Collaboration tools. These include all media: voice, video, instant messaging
Instant messaging (IM) technology is a type of synchronous computer-mediated communication involving the immediate ( real-time) transmission of messages between two or more parties over the Internet or another computer network. Originally involv ...
, electronic whiteboards, and shared document markup
:*Databases. Not only will these need to be interoperable, they need to reflect different models, when appropriate, such as the semantic web
The Semantic Web, sometimes known as Web 3.0, is an extension of the World Wide Web through standards set by the World Wide Web Consortium (W3C). The goal of the Semantic Web is to make Internet data machine-readable.
To enable the encoding o ...
. There may no longer be a clear line between databases and web applications.
:*Analytic tools. These will cover a wide range of pattern recognition and knowledge organization.
The nature of analysis
An analysis should have a summary of the key characteristics of the topic, followed by the key variables and choices. Increasingly deep analysis can explain the internal dynamics of the matter being studied, and eventually to prediction, known as estimation.
The purpose of intelligence analysis is to reveal to a specific decision maker the underlying significance of selected target information. Analysts should begin with confirmed facts, apply expert knowledge to produce plausible but less certain findings, and even forecast, when the forecast is appropriately qualified. Analysts should not, however, engage in fortunetelling that has no basis in fact.
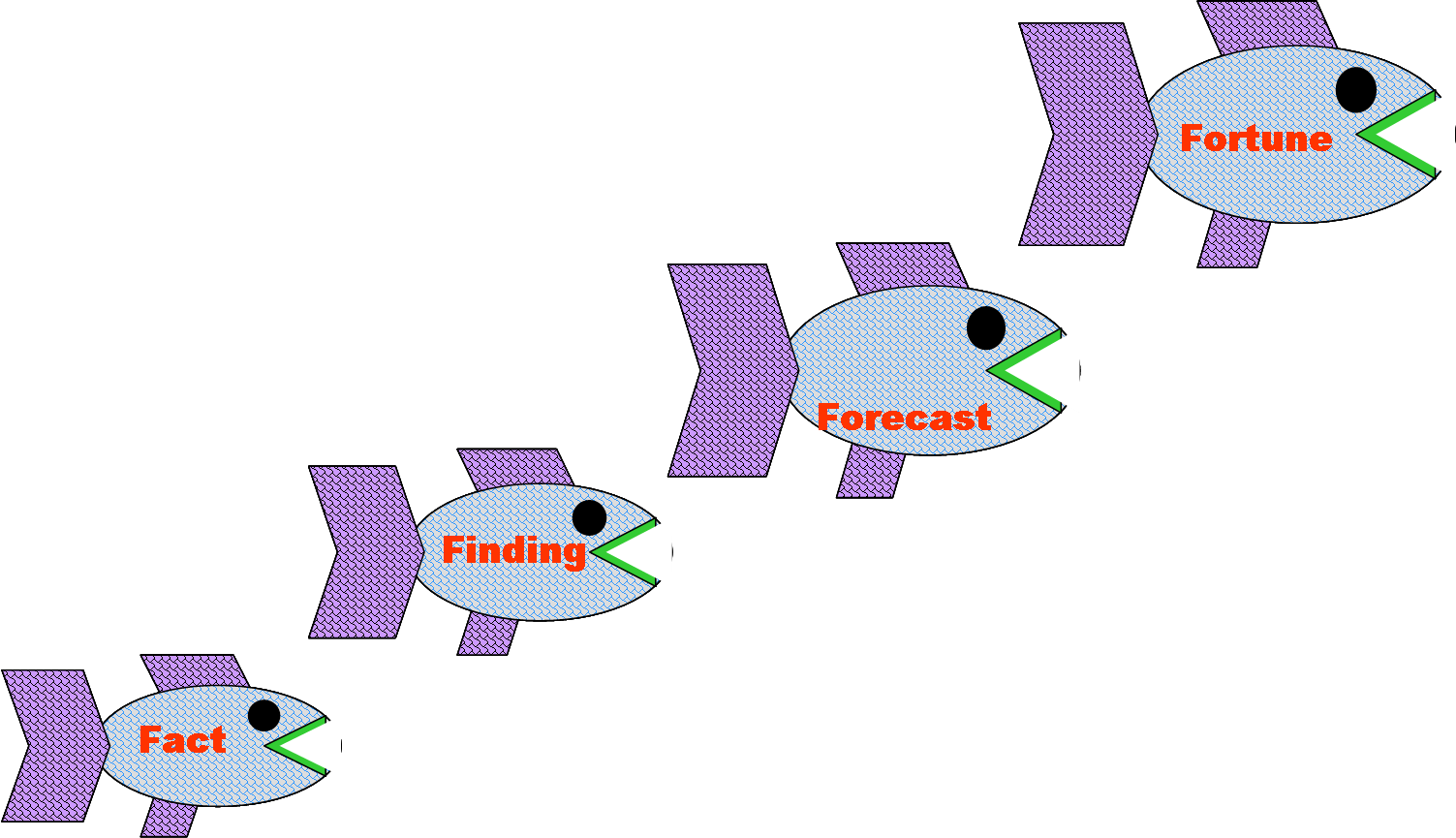 The mnemonic "Four Fs Minus One" may serve as a reminder of how to apply this criterion. Whenever the intelligence information allows, and the customer's validated needs demand it, the intelligence analyst will extend the thought process as far along the Food Chain as possible, to the third "F" but not beyond to the fourth.
The mnemonic "Four Fs Minus One" may serve as a reminder of how to apply this criterion. Whenever the intelligence information allows, and the customer's validated needs demand it, the intelligence analyst will extend the thought process as far along the Food Chain as possible, to the third "F" but not beyond to the fourth.
Types of reasoning
Objectivity is the intelligence analyst's primary asset in creating intelligence that
meets the Four Fs Minus One criterion. To produce intelligence objectively, the
analyst must employ a process tailored to the nature of the problem. Four basic types of
reasoning apply to intelligence analysis: induction, deduction, abduction and the scientific
method.
Induction: seeking causality
The induction process is one of discovering relationships among the phenomena under study. It may come from human pattern recognition ability, looking at a seemingly random set of events, perhaps writing them on cards and shuffling them until a pattern emerges.
An analyst might notice that when Country X's command post with call sign ABC sent out a message on frequency 1 between Thursday and Saturday, an air unit will move to a training range within one week. The acknowledgement will take one day, so the analyst should recommend intensified COMINT monitoring of the appropriate frequencies between Friday and Sunday. Another kind of causality could come from interviews, in which soldiers might describe the things that warn them of an impending attack, or how the ground might look when an improvised explosive device has been emplaced.
While induction, for human beings, is usually not at a fully rational level, do not discount the potential role of software that uses statistical or logical techniques for finding patterns. Induction is subtly different from intuition: there usually is a pattern that induction recognizes, and this pattern may be applicable to other situations.
Deduction: applying the general
Deduction, is the classic process of reasoning from the general to the specific, a process made memorable by Sherlock Holmes
Sherlock Holmes () is a Detective fiction, fictional detective created by British author Arthur Conan Doyle. Referring to himself as a "Private investigator, consulting detective" in his stories, Holmes is known for his proficiency with obser ...
: "How often have I said to you that when you have eliminated the impossible, whatever remains, however improbable, must be the truth?" Deduction can be used to validate a hypothesis by working from premises to conclusion.
The pattern of air maneuvers described above may be a general pattern, or it may be purely General X's personal command style. Analysts need to look at variables, such as personalities, to learn whether a pattern is truly general doctrine, or simply idiosyncratic.
Not all intelligence officers regard this as a desirable approach. At his confirmation hearing for CIA Director, Gen. Michael V. Hayden said he believes that intelligence analysis should be done by "induction", under which "all the data" are gathered and general conclusions determined, rather than by "deduction", under which you have a conclusion and seek out the data that support it.
Trained intuition
Analysts need to harness trained intuition: the recognition that one has come to a spontaneous insight. The steps leading there may not be apparent, although it is well to validate the intuition with the facts and tools that are available.
Polish cryptanalysts first were reading German Enigma ciphers in 1932, although the commercial version may have been broken by the British cryptanalyst, Dilwyn Knox, in the 1920s. Poland gave critical information to the French and British in 1939, and production British cryptanalysis was well underway in 1940. The Enigma, with German military enhancements, was quite powerful for a mechanical encryption device, and it might not have been broken as easily had the Germans been more careful about operating procedures. Throughout the war, Germany introduced enhancements, but never realized the British were reading the traffic almost as fast as the Germans.
 US cryptanalysts had broken several Japanese diplomatic ciphers, but, without ever seeing the PURPLE
Purple is a color similar in appearance to violet light. In the RYB color model historically used in the arts, purple is a secondary color created by combining red and blue pigments. In the CMYK color model used in modern printing, purple is ...
US cryptanalysts had broken several Japanese diplomatic ciphers, but, without ever seeing the PURPLE
Purple is a color similar in appearance to violet light. In the RYB color model historically used in the arts, purple is a secondary color created by combining red and blue pigments. In the CMYK color model used in modern printing, purple is ...
machine until after the war, they deduced the logic. Purple was actually mechanically simpler than Enigma, but the U.S. Army team struggled with a mechanical reproduction until Leo Rosen had the unexplained insight that the critical building block in the Purple machine was a telephone-type stepping switch rather than the rotor
ROTOR was an elaborate air defence radar system built by the British Government in the early 1950s to counter possible attack by Soviet bombers. To get it operational as quickly as possible, it was initially made up primarily of WWII-era syst ...
used in Enigma and in more advanced U.S. and UK machines. Rosen, Frank Rowlett, and others of the team recognized Rosen's insight as based on nothing but a communication engineer's intuition.
Experienced analysts, and sometimes less experienced ones, will have an intuition about some improbable event in a target country, and will collect more data, and perhaps send out collection requests within his or her authority. These intuitions are useful just often enough that wise managers of analysts, unless the situation is absolutely critical, allow them a certain amount of freedom to explore.
Scientific method
Astronomers and nuclear physicists, at different ends of the continuum from macroscopic to microscopic, share the method of having to infer behavior, consistent with hypothesis, not by measuring phenomena to which they have no direct access, but by measuring phenomena that can be measured and that hypothesis suggests will be affected by the mechanism of interest. Other scientists may be able to set up direct experiments, as in chemistry or biology. If the experimental results match the expected outcome, then the hypothesis is validated; if not, then the analyst must develop a new hypothesis and appropriate experimental methods.
In intelligence analysis, the analyst rarely has direct access to the observable subject, but gathers information indirectly. Even when the intelligence subject at hand is a technical one, analysts must remain aware that the other side may be presenting deliberately deceptive information.
From these gathered data, the analyst may proceed with the scientific method by generating tentative explanations for a subject event or phenomenon. Next, each hypothesis is examined for plausibility and compared against newly acquired information, in a continual process toward reaching a conclusion. Often the intelligence analyst tests several hypotheses at the same time, whereas the scientist usually focuses on one at a time. Furthermore, intelligence analysts cannot usually experiment directly upon the subject matter as in science, but must generate fictional scenarios and rigorously test them through methods of analysis suggested below.
Methods of analysis
As opposed to types of reasoning, which are ways the analyst drafts the product, the following methods are ways of validating the analyst's results of reasoning. Structured analytic techniques are used to help challenge judgments, identify mental mindsets, overcome biases, stimulate creativity, and manage uncertainty. Examples include the key assumptions check, analysis of competing hypotheses, Devil's advocacy, Red Team Analysis, and Alternative Futures/Scenarios analysis, among others.
Opportunity analysis
Opportunity analysis identifies for policy officials opportunities or vulnerabilities that the customer's organization can exploit to advance a policy, as well as dangers that could undermine a policy. Lawyers apply the test ''cui bono'' (who benefits?) in a rather similar way.
To make the best use of opportunity analysis, there needs to be a set of objectives for one's own country, preferably with some flexibility to them. The next step is to examine personalities and groups in that target country to see if there are any with a commonality of interest. Even though the different sides might want the same thing, it is entirely possible that one or the other might have deal-breaking conditions. If that is the case, then ways to smooth that conflict need to be identified, or no more work should be spent on that alternative.
Conversely, if there are elements that would be utterly opposed to the objectives of one's side, ways of neutralizing those elements need to be explored. They may have vulnerabilities that could render them impotent, or there may be a reward, not a shared opportunity, that would make them cooperate.
Linchpin analysis
Linchpin analysis proceeds from information that is certain, or with a high probability of being certain. In mathematics and physics, a similar problem formation, which constrains the solution by certain known or impossible conditions, is the boundary value condition.
By starting from knowns (and impossibilities), the analyst has a powerful technique for showing consumers, peers, and managers that a problem has both been thoroughly studied and constrained to reality. Linchpin analysis was introduced to CIA by deputy director for Intelligence (1993–1996) Doug MacEachin, as one of the "muscular" terms he pressed as an alternative to academic language, which was unpopular with many analysts. He substituted linchpin analysis for the hypotheses driving key variables. MacEachin required the hypotheses—or linchpins—needed to be explicit, so policymakers could be aware of coverage, and also aware of changes in assumptions.
This method is an "anchoring tool" that seeks to reduce the hazard of self-inflicted intelligence error as well as policymaker misinterpretation. It forces use of the checkpoints listed below, to be used when drafting reports:
#Identify the main uncertain factors or key variables judged likely to drive the outcome of the issue, forcing systematic attention to the range of and relationships among factors at play.
#Determine the linchpin premises or working assumptions about the drivers. This encourages testing of the key subordinate judgments that hold the estimative conclusion together.
#Marshal findings and reasoning in defense of the linchpins, as the premises that warrant the conclusion are subject to debate as well as error.
#Address the circumstances under which unexpected developments could occur. What indicators or patterns of development could emerge to signal that the linchpins were unreliable? And what triggers or dramatic internal and external events could reverse the expected momentum?
Analysis of competing hypotheses
Dick Heuer spent years in the CIA Directorate of Operations (DO) as well as the DI, and worked on methodology of analysis both in his later years and after retirement. Some of his key conclusions, coming from both experience and an academic background in philosophy, include:
#The mind is poorly "wired" to deal effectively with both inherent uncertainty (the natural fog surrounding complex, indeterminate intelligence issues) and induced uncertainty (the man-made fog fabricated by denial and deception operations).
#Even increased awareness of cognitive and other "unmotivated" biases, such as the tendency to see information confirming an already-held judgment more vividly than one sees "disconfirming" information, does little by itself to help analysts deal effectively with uncertainty.
#Tools and techniques that gear the analyst's mind to apply higher levels of critical thinking can substantially improve analysis on complex issues on which information is incomplete, ambiguous, and often deliberately distorted. Key examples of such intellectual devices include techniques for structuring information, challenging assumptions, and exploring alternative interpretations.
In 1980, he wrote an article, "Perception: Why Can't We See What Is There to be Seen?" which suggests to Davis that Heuer's ideas were compatible with linchpin analysis. Given the difficulties inherent in the human processing of complex information, a prudent management system should
#Encourage products that (a) clearly delineate their assumptions and chains of inference and (b) specify the degree and source of the uncertainty involved in the conclusions.
#Emphasize procedures that expose and elaborate alternative points of view—analytic debates, devil's advocates, interdisciplinary brainstorming, competitive analysis, intra-office peer review of production, and elicitation of outside expertise.
According to Heuer, analysts construct a reality based on objective information, filtered through complex mental processes that determine which information is attended to, how it is organized, and the meaning attributed to it. What people perceive, how readily they perceive it, and how they process this information after receiving it are all strongly influenced by past experience, education, cultural values, role requirements, and organizational norms, as well as by the specifics of the information received. To understand how the analysis results, one must use good mental models to create the work, and understand the models when evaluating it. Analysts need to be comfortable with challenge, refinement, and challenge. To go back to linchpin analysis, the boundary conditions give places to challenge and test, reducing ambiguity.
More challenge, according to Heuer, is more important than more information. He wanted better analysis to be applied to less information, rather than the reverse. Given the immense volumes of information that modern collection systems produce, the mind is the limiting factor. Mirror-imaging is one of Heuer's favorite example of a cognitive trap, in which the analyst substitutes his own mindset for that of the target. "To see the options faced by foreign leaders as these leaders see them", according to Heuer, " one must understand he foreign leaders'values and assumptions and even their misperceptions and misunderstandings. ... Too frequently, foreign behavior appears "irrational" or "not in their own best interest." Projecting American values created models that were inappropriate for the foreign leader.
A significant problem during the Vietnam War is that Secretary of Defense Robert S. McNamara, an expert on statistical decision-making, assumed that Ho Chi Minh
(born ; 19 May 1890 – 2 September 1969), colloquially known as Uncle Ho () among other aliases and sobriquets, was a Vietnamese revolutionary and politician who served as the founder and first President of Vietnam, president of the ...
, Võ Nguyên Giáp
Võ Nguyên Giáp ( vi-hantu, , ; 25 August 1911 – 4 October 2013) was a Vietnamese general, communist revolutionary and politician. Highly regarded as a military strategist, Giáp led Vietnamese communist forces to victories in wars agains ...
, and other North Vietnamese
North Vietnam, officially the Democratic Republic of Vietnam (DRV; ; VNDCCH), was a country in Southeast Asia from 1945 to 1976, with sovereignty fully recognized in 1954 Geneva Conference, 1954. A member of the communist Eastern Bloc, it o ...
officials would approach decision-making as he did. For example, in McNamara's thinking, if the United States did not attack SA-2
The S-75 (Russian: С-75; NATO reporting name SA-2 Guideline) is a Soviet-designed, high-altitude air defence system. It is built around a surface-to-air missile with command guidance. Following its first deployment in 1957 it became one of the ...
anti-aircraft missiles, the enemy would interpret that as "restraint" and not use them against U.S. aircraft
The North Vietnamese leadership, not privy to McNamara's thinking, were unaware of the "signaling" and did their best to shoot down U.S. aircraft with those missiles.
Heuer's answer was making the challenge of Analysis of Competing Hypotheses (ACH) the core of analysis. In ACH, there is competition among competing hypotheses of the foreign leader's assumptions, which will reduce mirror-imaging even if they do not produce the precise answer. The best use of information, in this context, is to challenge the assumption the analyst likes best.
One of the key motivations for ACH, according to Heuer, is to avoid rejecting deception out of hand, because the situation looks straightforward. Heuer observed that good deception looks real. "Rejecting a plausible but unproven hypothesis too early tends to bias the subsequent analysis, because one does not then look for the evidence that might support it. The possibility of deception should not be rejected until it is disproved or, at least, until a systematic search for evidence has been made and none has been found."
The steps in ACH are:
#Identify the possible hypotheses to be considered. Use a group of analysts with different perspectives to brainstorm the possibilities.
#Make a list of significant evidence and arguments for and against each hypothesis.
#Prepare a matrix with hypotheses across the top and evidence down the side. Analyze the "diagnosticity" of the evidence and arguments—that is, identify which items are most helpful in judging the relative likelihood of the hypotheses.
#Refine the matrix. Reconsider the hypotheses and delete evidence and arguments that have no diagnostic value.
#Draw tentative conclusions about the relative likelihood of each hypothesis. Proceed by trying to disprove the hypotheses rather than prove them.
#Analyze how sensitive your conclusion is to a few critical items of evidence. Consider the consequences for your analysis if that evidence were wrong, misleading, or subject to a different interpretation.
#Report conclusions. Discuss the relative likelihood of all the hypotheses, not just the most likely one.
#Identify milestones for future observation that may indicate events are taking a different course than expected.
Keith Devlin
Keith James Devlin (born 16 March 1947) is a British mathematician and popular science writer. Since 1987 he has lived in the United States. He has dual British-American citizenship. has been researching the use of mathematics and formal logic in implementing Heuer's ACH paradigm.
Analogy
Analogy is common in technical analysis, but engineering characteristics seeming alike do not necessarily mean that the other side has the same employment doctrine for an otherwise similar thing. Sometimes, the analogy was valid for a time, such as the MiG-25 aircraft being designed as a Soviet counter to the perceived threat of the high-altitude, supersonic B-70 bomber. The Soviets could have canceled the MiG-25
The Mikoyan-Gurevich MiG-25 (; NATO reporting name: Foxbat) is a supersonic interceptor and reconnaissance aircraft that is among the fastest military aircraft to enter service. Designed by the Soviet Union's Mikoyan-Gurevich bureau, it is a ...
program when the US changed doctrines to low altitude penetration and canceled the B-70 program, but they continued building the MiG-25.
One of the Soviet variants was a high-speed, high-altitude reconnaissance aircraft (MiG-25RB), which, for a time, was thought comparable to the US SR-71
The Lockheed SR-71 "Blackbird" is a retired Range (aeronautics), long-range, high-altitude, Mach number, Mach 3+ military strategy, strategic reconnaissance aircraft developed and manufactured by the American aerospace company Lockheed Co ...
aircraft. Several additional points of data, however, showed that an analogy between the SR-71 and MiG-25RB was not complete. HUMINT revealed that a single Mach 3.2 flight of the MiG wrecked the engines beyond hope of repair, and the cost of replacement was prohibitive. The SR-71, however, could make repeated flights with the same engines. The dissimilarity of engine life was not only expensive, but meant that the MiG-25RB could operate only from bases with the capability to change engines.
 The United States had applied "reverse engineering" to the MiG, essentially saying "if we had an aircraft with such capabilities, what would we do with it?" In the fighter-interceptor role, however, the US gives the pilot considerable flexibility in tactics, where the Soviets had a doctrine of tight ground control. For the U.S. doctrine, the aircraft was too inflexible for American fighter tactics, but made sense for the Soviets as an interceptor that could make one pass at a penetrating bomber, using an extremely powerful radar to burn through jamming for final targeting.
Many of these assumptions fell apart after Viktor Belenko flew his MiG-25 to the West, where TECHINT analysts could examine the aircraft, and doctrinal specialists could interview Belenko.
The United States had applied "reverse engineering" to the MiG, essentially saying "if we had an aircraft with such capabilities, what would we do with it?" In the fighter-interceptor role, however, the US gives the pilot considerable flexibility in tactics, where the Soviets had a doctrine of tight ground control. For the U.S. doctrine, the aircraft was too inflexible for American fighter tactics, but made sense for the Soviets as an interceptor that could make one pass at a penetrating bomber, using an extremely powerful radar to burn through jamming for final targeting.
Many of these assumptions fell apart after Viktor Belenko flew his MiG-25 to the West, where TECHINT analysts could examine the aircraft, and doctrinal specialists could interview Belenko.
The analytic process
Analysts should follow a series of sequential steps:
Define the problem
Policy makers will have questions based on their intelligence requirements. Sometimes questions are clear and can easily be addressed by the analyst. Sometimes however, clarification is required due to vagueness, multiple layers of bureaucracy between customer and analyst, or due to time constraints. Just as analysts need to try to understand the thinking of the adversary, analysts need to know the thinking of their customers and allies.
Generate hypotheses
Once the problem is defined, the analyst is able to generate reasonable hypotheses based on the question. For example, a business may want to know whether a competitor will lower their prices in the next quarter. From this problem, two obvious hypotheses are:
#The competitor will lower prices or
#The competitor will not lower prices.
However, with a little brainstorming, additional hypotheses may become apparent. Perhaps the competitor will offer discounts to long term customers, or perhaps they may even raise prices. At this point, no hypothesis should be discarded.
Determine information needs and gather information
In intelligence, collection usually refers to the step in the formal intelligence cycle
The intelligence cycle is an idealized model of how intelligence (information gathering), intelligence is processed in civilian and military intelligence agency, intelligence agencies, and law enforcement organizations. It is a closed path (gra ...
process. In many cases, the information needed by the analyst is either already available or is already being sought by collection assets (such as spies, imagery satellites). If not, the analyst may request collection on the subject, or if this is not possible identify this information gap in their final product. The analyst will generally also research other sources of info, such as open source (public record, press reporting), historical records, and various databases.
Evaluate sources
Information used for military, commercial, state, and other forms of intelligence analysis has often been obtained from individuals or organizations that are actively seeking to keep it secret, or may provide misleading information. Adversaries do not want to be analyzed correctly by competitors. This withholding of information is known as counterintelligence
Counterintelligence (counter-intelligence) or counterespionage (counter-espionage) is any activity aimed at protecting an agency's Intelligence agency, intelligence program from an opposition's intelligence service. It includes gathering informati ...
, and is very different from similar fields of research, such as science and history where information may be misleading, incomplete or wrong, but rarely does the subject of investigation actively deny the researcher access. So, the analyst must evaluate incoming information for reliability (has the source reported accurate information in the past?), credibility (does the source reasonably have access to the information claimed? Has the source lied in the past?), and for possible denial and deception (even if the source is credible and reliable, they may have been fooled).
Evaluate (test) hypotheses
All hypotheses must be rigorously tested. Methods such as Analysis of Competing Hypotheses or link charts are key. It is essential to triage which may be valid, which fail readily, and which require more information to assess.
Be especially alert to cognitive and cultural biases in and out of the organization. Recent scholarship on theories of the sociology of knowledge raise important caveats.
As Jones and Silberzahn documented in the 2013 volume ''Constructing Cassandra: Reframing Intelligence Failure at the CIA, 1947–2001'', while hypotheses are essential to sorting "signals" from "noise" in raw intelligence data, the variety, types and boundaries of the types of hypotheses an intelligence organization entertains are a function of the collective culture and identity of the intelligence producer. Often, these hypotheses are shaped not merely by the cognitive biases of individual analysts, but by complex social mechanism both inside and outside that analytic unit. After many strategic surprises, "Cassandras" – analysts or outsiders who offered warnings, but whose hypotheses were ignored or sidelined – are discovered. Therefore, careful analysts should recognize the key role that their own and their organization's identity and culture play in accepting or rejecting hypotheses at each step in their analysis.
Production and packaging
Once hypotheses have been evaluated, the intelligence product must be created for the consumer. Three key features of the intelligence product are:
*Timeliness. Timeliness includes not only the amount of time required to deliver the product, but also the usefulness of the product to the customer at a given moment.
*Scope. Scope involves the level of detail or comprehensiveness of the material contained in the product.
*Periodicity. Periodicity describes the schedule of product initiation and generation.
Government intelligence products are typically packaged as highly structured written and oral presentations, including electrical messages, hardcopy reports, and briefings. Many organizations also generate video intelligence products, especially in the form of live daily "newscasts", or canned documentary presentations.
Analysts should understand the relationship between the analyst's and the consumer's organization. There may be times that while the ultimate consumer and originating analyst simply want to pass information, a manager in either chain of command may insist on a polished format.
Peer review
Peer review is essential to assess and confirm accuracy. "Coordination with peers is necessary...If you think you are right, and the coordinator disagrees, let the assessment reflect that difference of opinion and use a footnote, called a ''reclama'', inside the U.S. intelligence community if necessary. But never water down your assessment to a lowest common denominator just to obtain coordination. When everyone agrees on an issue, something probably is wrong. "As an example, following the collapse of the Soviet Union, there was an almost unanimous belief that large numbers of Russian ballistic missile specialists would flood into the Third World and aid missile programs in other states (the so-called brain drain)...As it turned out, there was no xpectedmass departure of Russian missile specialists, but Russian expertise was supplied to other states in ways that had been ignored due to the overemphasis on the brain drain.
In large intelligence establishments, analysts have peers at other agencies. The practical amount of coordination, indeed inside one's own agency, will depend on the secure collaboration tools available (wikis
A wiki ( ) is a form of hypertext publication on the internet which is collaboratively edited and managed by its audience directly through a web browser. A typical wiki contains multiple pages that can either be edited by the public or l ...
, analyst webpages, email
Electronic mail (usually shortened to email; alternatively hyphenated e-mail) is a method of transmitting and receiving Digital media, digital messages using electronics, electronic devices over a computer network. It was conceived in the ...
), the schedule and availability of the other analysts, any restrictions on dissemination of the material, and the analyst's ability to play nicely with others. Extremely specialized issues might have very few people who could meaningfully look at it.
An intelligence community document, as opposed to a spot report from a single agency, is expected to be coordinated and reviewed. For example, in reports on the Iraqi WMD program, given a field report that aluminum tubes were on order, which might have been received both at the geographic desk and the Counterproliferation Center, someone might have thought they were for use in uranium separation centrifuges. It has been reported that some analysts thought they might be used for rocket casings, which apparently was the correct interpretation. The question needs to be asked "did the original analyst contact a technical specialist in separation centrifuges, perhaps at Department of Energy intelligence?"
Such an analyst might have mentioned that while aluminum has been used, maraging steel is the material of choice for Zippe-type centrifuge
The Zippe-type centrifuge is a gas centrifuge designed to enrich the rare fissile isotope uranium-235 (235U) from the mixture of isotopes found in naturally occurring uranium compounds. The Isotope separation, isotopic separation is based on the sl ...
s. The alternative, the Helikon vortex separation process, has no moving parts and thus less demand on the tubes, but takes much more energy. If the Helikon had been under consideration, the consultation could have gone farther, perhaps to IMINT analysts familiar with power generation in the area or infrared MASINT specialists who could look for the thermal signature of power generation or the cascade itself. Both Zippe and Helikon techniques take a great deal of energy, and often have been placed near hydroelectric dam power plants so power will be nearby.
Customer feedback and production evaluation
The production phase of the intelligence process does not end with delivering the product to the customer. Rather, it continues in the same manner in which it began: with interaction between producer and customer. For the product to be useful, the analyst and policymaker need to hear feedback from one another, and they refine both analysis and requirements.
Feedback procedures between producers and customers includes key questions, such as: Is the product usable? Is it timely? Was it in fact used? Did the product meet expectations? If not, why not? What next? The answers to these questions lead to refined production, greater use of intelligence by decision makers, and further feedback sessions. Thus, production of intelligence generates more requirements in this iterative process.
Never forget the end user
Effective intelligence analysis is ultimately tailored to the end user. William Donovan, the head of the World War II OSS, began to get FDR's ear because he gave vividly illustrated, well-organized briefings that would be common today, but were unprecedented in World War II. Today, there is danger of becoming too entranced with the presentation and less with its subject. This is also a delicate dance of overemphasizing the subjects that interest high officials, and what they want to hear declared true about them, rather than hearing what the analysts believe is essential.
At the same time, analysts must always be wary of mirroring the desires, attitudes, and views of intelligence consumers. They must raise awkward facts and ask probing questions, even if this makes the decision-maker's job harder.Pages 234-252
See also
* Center for Intelligence and Security Studies – trains new analysts in intelligence analysis
* Intelligence analysis organizations
References
Further reading
* Clark, Robert M. (2019). ''Intelligence Analysis: A Target-Centric Approach'' (6th ed.). Los Angeles: CQ Press.
* Heuer, Richards J.
''Psychology of Intelligence Analysis''
(1999)
* Jones, Milo and Silberzahn, Philippe. ''Constructing Cassandra, Reframing Intelligence Failure at the CIA, 1947–2001'' Stanford University Press (2013)
* Kent, Sherman. ''Strategic Intelligence for American World Policy'' (1965)
* Kent, Sherman and Steury, Donald P. (ed.)
(2008)
* MacEachin, Douglas J. ''The Tradecraft of Analysis: Challenge and Change in the CIA'' (1994)
* McDowell, Don. ''Strategic Intelligence: A Handbook for Practitioners, Managers and Users – Revised Edition'', Scarecrow Press Inc. (2009)
* Rolington, Alfred. ''Strategic Intelligence for the 21st Century: The Mosaic Method'', Oxford University Press (2013).
''A Tradecraft Primer: Structured Analytic Techniques for Improving Intelligence Analysis'', Prepared by the US Government, March 2009
broken (2024-03-20)
External links
i2 intelligence analysis platform
is the most widely used tool for analysing intelligence data.
{{DEFAULTSORT:Intelligence Analysis
Military intelligence