Cryptanalysis of the Lorenz cipher on:
[Wikipedia]
[Google]
[Amazon]
Cryptanalysis of the
 The Lorenz SZ cipher attachments implemented a Vernam
The Lorenz SZ cipher attachments implemented a Vernam 
 Because a single missed or corrupted character could make decryption impossible, the greatest accuracy was required. The undulator technology used to record the impulses had originally been developed for high-speed Morse. It produced a visible record of the impulses on narrow paper tape. This was then read by people employed as "slip readers" who interpreted the peaks and troughs as the marks and spaces of ITA2 characters. Perforated paper tape was then produced for telegraphic transmission to Bletchley Park where it was punched out.
Because a single missed or corrupted character could make decryption impossible, the greatest accuracy was required. The undulator technology used to record the impulses had originally been developed for high-speed Morse. It produced a visible record of the impulses on narrow paper tape. This was then read by people employed as "slip readers" who interpreted the peaks and troughs as the marks and spaces of ITA2 characters. Perforated paper tape was then produced for telegraphic transmission to Bletchley Park where it was punched out.
On 31 August 1941, two long messages were received that had the same indicator HQIBPEXEZMUG. The first seven characters of these two ciphertexts were the same, but the second message was shorter. The first 15 characters of the two messages were as follows (in Bletchley Park interpretation): John Tiltman tried various likely pieces of plaintext, i.e. a "cribs", against the string and found that the first plaintext message started with the German word ''SPRUCHNUMMER'' (message number). In the second plaintext, the operator had used the common abbreviation ''NR'' for ''NUMMER''. There were more abbreviations in the second message, and the punctuation sometimes differed. This allowed Tiltman to work out, over ten days, the plaintext of both messages, as a sequence of plaintext characters discovered in , could then be tried against and ''vice versa''. In turn, this yielded almost 4000 characters of key. Members of the Research Section worked on this key to try to derive a mathematical description of the key generating process, but without success.
 The so-called "British Tunny Machine" was a device that exactly replicated the functions of the SZ40/42 machines. It was used to produce the German cleartext from a ciphertext tape, after the cam settings had been determined. The functional design was produced at Bletchley Park where ten Testery Tunnies were in use by the end of the war. It was designed and built in
The so-called "British Tunny Machine" was a device that exactly replicated the functions of the SZ40/42 machines. It was used to produce the German cleartext from a ciphertext tape, after the cam settings had been determined. The functional design was produced at Bletchley Park where ten Testery Tunnies were in use by the end of the war. It was designed and built in
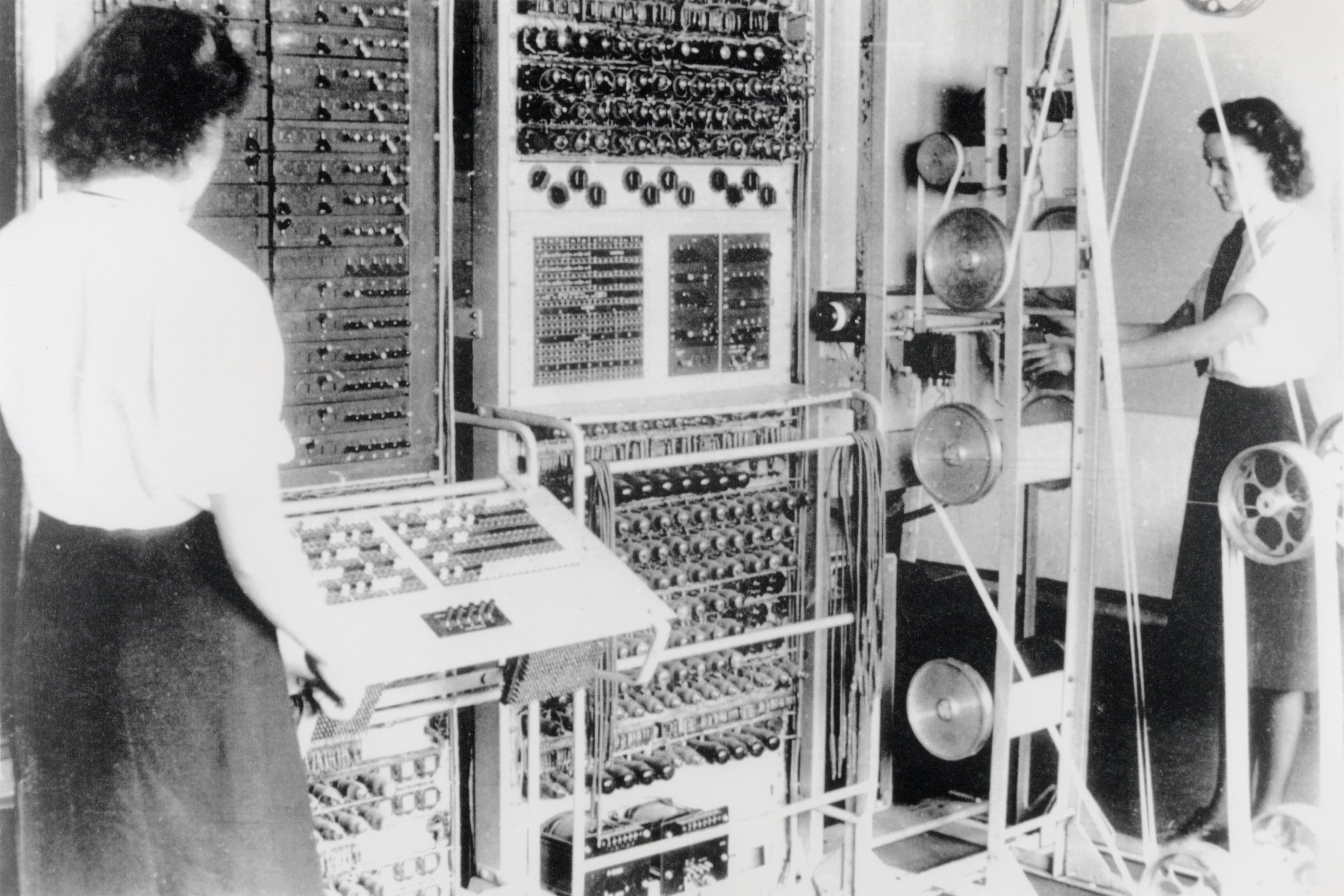 Tommy Flowers' had reservations about Heath Robinson's two synchronised tape loops, and his previous, unique experience of thermionic valves (vacuum tubes) led him to realize that a better machine could be produced using electronics. Instead of the key stream being read from a second punched paper tape, an electronically generated key stream could allow much faster and more flexible processing. Flowers' suggestion that this could be achieved with a machine that was entirely electronic and would contain between one and two thousand valves, was treated with incredulity at both the Telecommunications Research Establishment and at Bletchley Park, as it was thought that it would be "too unreliable to do useful work". He did, however, have the support of the Controller of Research at Dollis Hill, W Gordon Radley, and he implemented these ideas producing
Tommy Flowers' had reservations about Heath Robinson's two synchronised tape loops, and his previous, unique experience of thermionic valves (vacuum tubes) led him to realize that a better machine could be produced using electronics. Instead of the key stream being read from a second punched paper tape, an electronically generated key stream could allow much faster and more flexible processing. Flowers' suggestion that this could be achieved with a machine that was entirely electronic and would contain between one and two thousand valves, was treated with incredulity at both the Telecommunications Research Establishment and at Bletchley Park, as it was thought that it would be "too unreliable to do useful work". He did, however, have the support of the Controller of Research at Dollis Hill, W Gordon Radley, and he implemented these ideas producing
Lorenz cipher
The Lorenz SZ40, SZ42a and SZ42b were German Rotor machine, rotor stream cipher machines used by the German Army (Wehrmacht), German Army during World War II. They were developed by C. Lorenz AG in Berlin. The model name ''SZ'' is derived from ' ...
was the process that enabled the British to read high-level German army messages during World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
. The British Government Code and Cypher School
The Government Code and Cypher School (GC&CS) was a British signals intelligence agency set up in 1919. During the First World War, the British Army and Royal Navy had separate signals intelligence agencies, MI1b and NID25 (initially known as R ...
(GC&CS) at Bletchley Park
Bletchley Park is an English country house and Bletchley Park estate, estate in Bletchley, Milton Keynes (Buckinghamshire), that became the principal centre of Allies of World War II, Allied World War II cryptography, code-breaking during the S ...
decrypted many communications between the ''Oberkommando der Wehrmacht
The (; abbreviated OKW ː kaːˈveArmed Forces High Command) was the Command (military formation), supreme military command and control Staff (military), staff of Nazi Germany during World War II, that was directly subordinated to Adolf ...
'' (OKW, German High Command) in Berlin and their army commands throughout occupied Europe, some of which were signed "Adolf Hitler, Führer". These were intercepted non- Morse radio transmissions that had been enciphered by the Lorenz SZ teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
rotor
ROTOR was an elaborate air defence radar system built by the British Government in the early 1950s to counter possible attack by Soviet bombers. To get it operational as quickly as possible, it was initially made up primarily of WWII-era syst ...
stream cipher
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream ( keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystrea ...
attachments. Decrypts of this traffic became an important source of "Ultra
Ultra may refer to:
Science and technology
* Ultra (cryptography), the codename for cryptographic intelligence obtained from signal traffic in World War II
* Adobe Ultra, a vector-keying application
* Sun Ultra series, a brand of computer work ...
" intelligence, which contributed significantly to Allied victory.
For its high-level secret messages, the German armed services enciphered each character using various online ''Geheimschreiber'' (secret writer) stream cipher machines at both ends of a telegraph
Telegraphy is the long-distance transmission of messages where the sender uses symbolic codes, known to the recipient, rather than a physical exchange of an object bearing the message. Thus flag semaphore is a method of telegraphy, whereas ...
link using the 5-bit International Telegraphy Alphabet No. 2 (ITA2). These machines were subsequently discovered to be the Lorenz SZ (SZ for ''Schlüssel-Zusatz'', meaning "cipher attachment") for the army, the Siemens and Halske T52
The Siemens & Halske T52, also known as the Geheimschreiber ("secret teleprinter"), or ''Schlüsselfernschreibmaschine'' (SFM), was a World War II German cipher machine and teleprinter produced by the electrical engineering firm Siemens & Halske. ...
for the air force and the Siemens T43, which was little used and never broken by the Allies.
Bletchley Park decrypts of messages enciphered with the Enigma machine
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the W ...
s revealed that the Germans called one of their wireless teleprinter transmission systems ''"Sägefisch"'' (sawfish), which led British cryptographer
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or '' -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of adversarial behavior. More gen ...
s to refer to encrypted German radiotelegraphic traffic as "Fish
A fish (: fish or fishes) is an aquatic animal, aquatic, Anamniotes, anamniotic, gill-bearing vertebrate animal with swimming fish fin, fins and craniate, a hard skull, but lacking limb (anatomy), limbs with digit (anatomy), digits. Fish can ...
". "Tunny" (tunafish) was the name given to the first non-Morse link, and it was subsequently used for the cipher machines and their traffic.
As with the entirely separate cryptanalysis of the Enigma
Cryptanalysis of the Enigma ciphering system enabled the western Allies of World War II, Allies in World War II to read substantial amounts of Morse code, Morse-coded radio communications of the Axis powers that had been enciphered using Enigm ...
, it was German operational shortcomings that allowed the initial diagnosis of the system, and a way into decryption. Unlike Enigma, no physical machine reached allied hands until the very end of the war in Europe, long after wholesale decryption had been established. The problems of decrypting Tunny messages led to the development of "Colossus
Colossus, Colossos, or the plural Colossi or Colossuses, may refer to:
Statues
* Any exceptionally large statue; colossal statues, are generally taken to mean a statue at least twice life-size
** List of tallest statues
** :Colossal statues
* ...
", the world's first electronic, programmable digital computer, ten of which were in use by the end of the war, by which time some 90% of selected Tunny messages were being decrypted at Bletchley Park.
Albert W. Small, a cryptanalyst from the US Army Signal Corps who was seconded to Bletchley Park and worked on Tunny, said in his December 1944 report back to Arlington Hall
Arlington Hall (also called Arlington Hall Station) is a historic building in Arlington, Virginia. Originally it was a girls' school and later the headquarters of the United States Army's Signal Intelligence Service (SIS) cryptography operations ...
that:
German Tunny machines
 The Lorenz SZ cipher attachments implemented a Vernam
The Lorenz SZ cipher attachments implemented a Vernam stream cipher
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream ( keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystrea ...
(using the exclusive or (XOR) function) to encrypt the plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
bits by combining them with the key bits to produce the ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
at the transmitting end. At the receiving end, an identically configured machine produced the same key stream which was combined with the ciphertext to produce the plaintext, i.e. the system implemented a symmetric-key algorithm
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to go between ...
.
The key stream was generated by a complex array of twelve wheels, ten of which delivered what should have been a cryptographically secure pseudorandom number stream. This stream was a product of XOR-ing the bits of the 5-bit character generated by the right hand five wheels (the ''chi'' () wheels) with the bits from the left hand five (the ''psi'' () wheels). The ''chi'' wheels always moved on one position for every incoming plaintext or ciphertext character, but the ''psi'' wheels' movement was determined by the central two ''mu'' () or "motor" wheels.
The 61 wheel moved on after each character and its cams determined the 37 wheel movement, whose cams in turn controlled the ''psi'' wheels' movement. On all but the earliest machines, there was an additional factor that played into the moving on or not of the ''psi'' wheels. These were of four different types and were called "Limitations" at Bletchley Park. All involved some aspect of the previous positions of the machine's wheels.
The numbers of cams on the set of twelve wheels of the SZ42 machines totalled 501 and were co-prime with each other, giving an extremely long period before the key sequence repeated. Each cam could either be in a raised position, in which case it generated x (as written at Bletchley Park) and equivalent to a binary digit 1 to the logic of the system, or in the lowered position when it generated • equivalent to a binary digit 0. The total possible number of patterns of raised cams was 2501 which is an astronomically large number. In practice about half of the cams on each wheel were in the raised position as the Germans realized that otherwise there would be runs of x's and •'s, a cryptographic weakness.
The process of working out the wheel cam patterns was called "wheel breaking" at Bletchley Park. Deriving the start positions of the wheels for a particular transmission was termed "wheel setting" or simply "setting". The fact that the ''psi'' wheels all moved together, but not with every input character, was a major weakness of the machines that contributed to British cryptanalytical success.

Secure telegraphy
Electro-mechanical
Electromechanics combine processes and procedures drawn from electrical engineering and mechanical engineering. Electromechanics focus on the interaction of electrical and mechanical systems as a whole and how the two systems interact with each ...
telegraphy was developed in the 1830s and 1840s, well before telephony
Telephony ( ) is the field of technology involving the development, application, and deployment of telecommunications services for the purpose of electronic transmission of voice, fax, or data, between distant parties. The history of telephony is ...
, and operated worldwide by the time of the Second World War
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
. An extensive system of cables linked sites within and between countries, with a standard voltage of −80 V indicating a "mark" and +80 V indicating a "space". Where cable transmission became impracticable or inconvenient, such as for mobile German Army Units, radio transmission was used.
Teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
s at each end of the circuit consisted of a keyboard and a printing mechanism, and very often a five-hole perforated paper-tape reading and punching mechanism. When used online
In computer technology and telecommunications, online indicates a state of connectivity, and offline indicates a disconnected state. In modern terminology, this usually refers to an Internet connection, but (especially when expressed as "on lin ...
, pressing an alphabet key at the transmitting end caused the relevant character to print at the receiving end. Commonly, however, the communication system
A communications system is a collection of individual telecommunications networks systems, relay stations, tributary stations, and terminal equipment usually capable of interconnection and interoperation to form an integrated whole. Communic ...
involved the transmitting operator preparing a set of messages offline by punching them onto paper tape, and then going online only for the transmission of the messages recorded on the tape. The system would typically send some ten characters per second, and so occupy the line or the radio channel for a shorter period of time than for online typing.
The characters of the message were represented by the codes of the International Telegraphy Alphabet No. 2 (ITA2
The Baudot code () is an early character encoding for telegraphy invented by Émile Baudot in the 1870s. It was the predecessor to the International Telegraph Alphabet No. 2 (ITA2), the most common teleprinter code in use before ASCII. Each Chara ...
). The transmission medium, either wire or radio, used asynchronous serial communication
Asynchronous serial communication is a form of serial communication in which the communicating endpoints' interfaces are not continuously synchronized by a common clock signal. Synchronization ( clock recovery) is done by data-embedded signal ...
with each character signaled by a start (space) impulse, 5 data impulses and 1½ stop (mark) impulses. At Bletchley Park mark impulses were signified by ("cross") and space impulses by ("dot"). For example, the letter "H" would be coded as .
The figure shift (FIGS) and letter shift (LETRS) characters determined how the receiving end interpreted the string of characters up to the next shift character. Because of the danger of a shift character being corrupted, some operators would type a pair of shift characters when changing from letters to numbers or ''vice versa''. So they would type 55M88 to represent a full stop. Such doubling of characters was very helpful for the statistical cryptanalysis used at Bletchley Park. After encipherment, shift characters had no special meaning.
The speed of transmission of a radio-telegraph message was three or four times that of Morse code and a human listener could not interpret it. A standard teleprinter, however would produce the text of the message. The Lorenz cipher attachment changed the plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
of the message into ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
that was uninterpretable to those without an identical machine identically set up. This was the challenge faced by the Bletchley Park codebreakers.
Interception
Intercepting Tunny transmissions presented substantial problems. As the transmitters were directional, most of the signals were quite weak at receivers in Britain. Furthermore, there were some 25 differentfrequencies
Frequency is the number of occurrences of a repeating event per unit of time. Frequency is an important parameter used in science and engineering to specify the rate of oscillatory and vibratory phenomena, such as mechanical vibrations, audio ...
used for these transmissions, and the frequency would sometimes be changed part way through. After the initial discovery of the non-Morse signals in 1940, a radio intercept station called the Foreign Office Research and Development Establishment was set up on a hill at Ivy Farm at Knockholt
Knockholt is a village and civil parish in the Sevenoaks District of Kent. It is located north west of Sevenoaks & south of Orpington, and is adjacent to the Kent border with Greater London.
The village is mostly a ribbon development, surrou ...
in Kent, specifically to intercept this traffic. The centre was headed by Harold Kenworthy, had 30 receiving sets and employed some 600 staff. It became fully operational early in 1943.
 Because a single missed or corrupted character could make decryption impossible, the greatest accuracy was required. The undulator technology used to record the impulses had originally been developed for high-speed Morse. It produced a visible record of the impulses on narrow paper tape. This was then read by people employed as "slip readers" who interpreted the peaks and troughs as the marks and spaces of ITA2 characters. Perforated paper tape was then produced for telegraphic transmission to Bletchley Park where it was punched out.
Because a single missed or corrupted character could make decryption impossible, the greatest accuracy was required. The undulator technology used to record the impulses had originally been developed for high-speed Morse. It produced a visible record of the impulses on narrow paper tape. This was then read by people employed as "slip readers" who interpreted the peaks and troughs as the marks and spaces of ITA2 characters. Perforated paper tape was then produced for telegraphic transmission to Bletchley Park where it was punched out.
The Vernam cipher
The Vernam cipher implemented by the Lorenz SZ machines enciphers the plaintext bitstream by combining it with a random or pseudorandom bitstream (the "keystream") to generate the ciphertext. This combination is done using and verbalised as "A or B but not both". This is represented by the followingtruth table
A truth table is a mathematical table used in logic—specifically in connection with Boolean algebra, Boolean functions, and propositional calculus—which sets out the functional values of logical expressions on each of their functional arg ...
, where x represents "true" and • represents "false".
Other names for this function are: exclusive disjunction, not equal (NEQ), and modulo
In computing and mathematics, the modulo operation returns the remainder or signed remainder of a division, after one number is divided by another, the latter being called the '' modulus'' of the operation.
Given two positive numbers and , mo ...
2 addition (without "carry") and subtraction (without "borrow"). Modulo 2 addition and subtraction are identical. Some descriptions of Tunny decryption refer to addition and some to differencing, i.e. subtraction, but they mean the same thing. The XOR operator is both associative
In mathematics, the associative property is a property of some binary operations that rearranging the parentheses in an expression will not change the result. In propositional logic, associativity is a valid rule of replacement for express ...
and commutative
In mathematics, a binary operation is commutative if changing the order of the operands does not change the result. It is a fundamental property of many binary operations, and many mathematical proofs depend on it. Perhaps most familiar as a pr ...
.
Reciprocity is a desirable feature of a machine cipher so that the same machine with the same settings can be used either for enciphering or for deciphering. The Vernam cipher achieves this, as combining the stream of plaintext characters with the key stream produces the ciphertext, and combining the same key with the ciphertext regenerates the plaintext.
Symbolically:
::::Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
⊕ Key = Ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
and
:::: Ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
⊕ Key = Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
Vernam's original idea was to use conventional telegraphy practice, with a paper tape of the plaintext combined with a paper tape of the key at the transmitting end, and an identical key tape combined with the ciphertext signal at the receiving end. Each pair of key tapes would have been unique (a one-time tape
The one-time pad (OTP) is an encryption technique that cannot be cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, a plaintext is ...
), but generating and distributing such tapes presented considerable practical difficulties. In the 1920s four men in different countries invented rotor Vernam cipher machines to produce a key stream to act instead of a key tape. The Lorenz SZ40/42 was one of these.
Security features
A monoalphabetic substitution cipher such as theCaesar cipher
In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in t ...
can easily be broken, given a reasonable amount of ciphertext. This is achieved by frequency analysis
In cryptanalysis, frequency analysis (also known as counting letters) is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers.
Frequency analysis is based on th ...
of the different letters of the ciphertext, and comparing the result with the known letter frequency
Letter frequency is the number of times letters of the alphabet appear on average in written language. Letter frequency analysis dates back to the Arab mathematician Al-Kindi (c. AD 801–873), who formally developed the method to break ciph ...
distribution of the plaintext.
With a polyalphabetic cipher
A polyalphabetic cipher is a substitution cipher, substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though it is a simplified special case. The Enigma machine i ...
, there is a different substitution alphabet for each successive character. So a frequency analysis shows an approximately uniform distribution, such as that obtained from a (pseudo) random number generator. However, because one set of Lorenz wheels turned with every character while the other did not, the machine did not disguise the pattern in the use of adjacent characters in the German plaintext. Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher and theoretical biologist. He was highly influential in the development of theoretical computer ...
discovered this weakness and invented the differencing technique described below to exploit it.
The pattern of which of the cams were in the raised position, and which in the lowered position was changed daily on the motor wheels (37 and 61). The ''chi'' wheel cam patterns were initially changed monthly. The ''psi'' wheel patterns were changed quarterly until October 1942 when the frequency was increased to monthly, and then to daily on 1 August 1944, when the frequency of changing the ''chi'' wheel patterns was also changed to daily.
The number of start positions of the wheels was 43×47×51×53×59×37×61×41×31×29×26×23 which is approximately 1.6×1019 (16 billion billion), far too large a number for cryptanalysts to try an exhaustive "brute-force attack
In cryptography, a brute-force attack or exhaustive key search is a cryptanalytic attack that consists of an attacker submitting many possible keys or passwords with the hope of eventually guessing correctly. This strategy can theoretically be ...
". Sometimes the Lorenz operators disobeyed instructions and two messages were transmitted with the same start positions, a phenomenon termed a "depth". The method by which the transmitting operator told the receiving operator the wheel settings that he had chosen for the message which he was about to transmit was termed the "indicator" at Bletchley Park.
In August 1942, the formulaic starts to the messages, which were useful to cryptanalysts, were replaced by some irrelevant text, which made identifying the true message somewhat harder. This new material was dubbed ''quatsch'' (German for "nonsense") at Bletchley Park.
During the phase of the experimental transmissions, the indicator consisted of twelve German forenames, the initial letters of which indicated the position to which the operators turned the twelve wheels. As well as showing when two transmissions were fully in depth, it also allowed the identification of partial depths where two indicators differed only in one or two wheel positions. From October 1942 the indicator system changed to the sending operator transmitting the unenciphered letters QEP followed by a two digit number. This number was taken serially from a code book that had been issued to both operators and gave, for each QEP number, the settings of the twelve wheels. The books were replaced when they had been used up, but between replacements, complete depths could be identified by the re-use of a QEP number on a particular Tunny link.
Diagnosis
The first step in breaking a new cipher is to diagnose the logic of the processes of encryption and decryption. In the case of a machine cipher such as Tunny, this entailed establishing the logical structure and hence functioning of the machine. This was achieved without the benefit of seeing a machine—which only happened in 1945, shortly before the allied victory in Europe. The enciphering system was very good at ensuring that the ciphertext contained no statistical, periodic or linguistic characteristics to distinguish it from random. However this did not apply to which was the weakness that meant that Tunny keys could be solved. During the experimental period of Tunny transmissions when the twelve-letter indicator system was in use, John Tiltman, Bletchley Park's veteran and remarkably gifted cryptanalyst, studied the Tunny ciphertexts and identified that they used a Vernam cipher. When two transmissions (a and b) use the same key, i.e. they are in depth, combining them eliminates the effect of the key. Let us call the two ciphertexts and , the key and the two plaintexts and . We then have: :::: If the two plaintexts can be worked out, the key can be recovered from either ciphertext-plaintext pair e.g.: :::: orOn 31 August 1941, two long messages were received that had the same indicator HQIBPEXEZMUG. The first seven characters of these two ciphertexts were the same, but the second message was shorter. The first 15 characters of the two messages were as follows (in Bletchley Park interpretation): John Tiltman tried various likely pieces of plaintext, i.e. a "cribs", against the string and found that the first plaintext message started with the German word ''SPRUCHNUMMER'' (message number). In the second plaintext, the operator had used the common abbreviation ''NR'' for ''NUMMER''. There were more abbreviations in the second message, and the punctuation sometimes differed. This allowed Tiltman to work out, over ten days, the plaintext of both messages, as a sequence of plaintext characters discovered in , could then be tried against and ''vice versa''. In turn, this yielded almost 4000 characters of key. Members of the Research Section worked on this key to try to derive a mathematical description of the key generating process, but without success.
Bill Tutte
William Thomas Tutte (; 14 May 1917 – 2 May 2002) was an English and Canadian code breaker and mathematician. During the Second World War, he made a fundamental advance in cryptanalysis of the Lorenz cipher, a major Nazi German cipher system ...
joined the section in October 1941 and was given the task. He had read chemistry and mathematics at Trinity College, Cambridge
Trinity College is a Colleges of the University of Cambridge, constituent college of the University of Cambridge. Founded in 1546 by King Henry VIII, Trinity is one of the largest Cambridge colleges, with the largest financial endowment of any ...
before being recruited to Bletchley Park. At his training course, he had been taught the Kasiski examination technique of writing out a key on squared paper with a new row after a defined number of characters that was suspected of being the frequency of repetition of the key. If this number was correct, the columns of the matrix would show more repetitions of sequences of characters than chance alone.
Tutte thought that it was possible that, rather than using this technique on the whole letters of the key, which were likely to have a long frequency of repetition, it might be worth trying it on the sequence formed by taking only one impulse (bit) from each letter, on the grounds that "''the part might be cryptographically simpler than the whole''". Given that the Tunny indicators used 25 letters (excluding J) for 11 of them, but only 23 letters for the twelfth, he tried Kasiski's technique on the first bit of the key characters using a repetition of 25 × 23 = 575. This did not produce a large number of repetitions in the columns, but Tutte did observe the phenomenon on a diagonal. He therefore tried again with 574, which showed up repeats in the columns. Recognising that the prime factor
A prime number (or a prime) is a natural number greater than 1 that is not a product of two smaller natural numbers. A natural number greater than 1 that is not prime is called a composite number. For example, 5 is prime because the only ways ...
s of this number are 2, 7 and 41, he tried again with a period of 41 and "''got a rectangle of dots and crosses that was replete with repetitions''".
It was clear, however, that the sequence of first bits was more complicated than that produced by a single wheel of 41 positions. Tutte called this component of the key ''χ''1 (''chi''). He figured that there was another component, which was XOR-ed with this, that did not always change with each new character, and that this was the product of a wheel that he called ''ψ''1 (''psi''). The same applied for each of the five bits (indicated here by subscripts). So for a single character, the key K consisted of two components:
:::: .
The actual sequence of characters added by the ''psi'' wheels, including those when they do not advance, was referred to as the ''extended psi'', and symbolised by ''ψ′''
::::.
Tutte's derivation of the ''ψ'' component was made possible by the fact that dots were more likely than not to be followed by dots, and crosses more likely than not to be followed by crosses. This was a product of a weakness in the German key setting, which they later stopped. Once Tutte had made this breakthrough, the rest of the Research Section joined in to study the other bits, and it was established that the five ''ψ'' wheels all moved together under the control of two ''μ'' (''mu'' or "motor") wheels.
Diagnosing the functioning of the Tunny machine in this way was a truly remarkable cryptanalytical achievement, and was described when Tutte was inducted as Officer of the Order of Canada in October 2001, as "''one of the greatest intellectual feats of World War II''".
Turingery
In July 1942Alan Turing
Alan Mathison Turing (; 23 June 1912 – 7 June 1954) was an English mathematician, computer scientist, logician, cryptanalyst, philosopher and theoretical biologist. He was highly influential in the development of theoretical computer ...
spent a few weeks in the Research Section. He had become interested in the problem of breaking Tunny from the keys that had been obtained from depths. In July, he developed a method of deriving the cam settings ("wheel breaking") from a length of key. It became known as "Turingery" (playfully dubbed "Turingismus" by Peter Ericsson, Peter Hilton
Peter John Hilton (7 April 1923Peter Hilton, "On all Sorts of Automorphisms", ''The American Mathematical Monthly'', 92(9), November 1985, p. 6506 November 2010) was a British mathematician, noted for his contributions to homotopy theory and f ...
and Donald Michie
Donald Michie (; 11 November 1923 – 7 July 2007) was a British researcher in artificial intelligence. During World War II, Michie worked for the Government Code and Cypher School at Bletchley Park, contributing to the effort to solve " Tunny ...
) and introduced the important method of "differencing" on which much of the rest of solving Tunny keys in the absence of depths, was based.
Differencing
The search was on for a process that would manipulate the ciphertext or key to produce a frequency distribution of characters that departed from the uniformity that the enciphering process aimed to achieve. Turing worked out that the XOR combination of the values of successive (adjacent) characters in a stream of ciphertext or key, emphasised any departures from a uniform distribution. The resultant stream was called the difference (symbolised by the Greek letter "delta" Δ) because XOR is the same as modulo 2 subtraction. So, for a stream of characters S, the difference ΔS was obtained as follows, where underline indicates the succeeding character: :::: The stream S may be ciphertext Z, plaintext P, key K or either of its two components ''χ'' and ''ψ''. The relationship amongst these elements still applies when they are differenced. For example, as well as: :::: It is the case that: :::: Similarly for the ciphertext, plaintext and key components: :::: So: :::: The reason that differencing provided a way into Tunny, was that although the frequency distribution of characters in the ciphertext could not be distinguished from a random stream, the same was not true for a version of the ciphertext from which the ''chi'' element of the key had been removed. This is because, where the plaintext contained a repeated character and the ''psi'' wheels did not move on, the differenced ''psi'' character (Δ''ψ'') would be the null character ('' at Bletchley Park). When XOR-ed with any character, this character has no effect, so in these circumstances, The ciphertext modified by the removal of the ''chi'' component of the key was called the de-''chi'' D at Bletchley Park, and the process of removing it as "de-''chi''-ing". Similarly for the removal of the ''psi'' component which was known as "de-''psi''-ing" (or "deep sighing" when it was particularly difficult). So the delta de-''chi'' ΔD was: :::: Repeated characters in the plaintext were more frequent both because of the characteristics of German (EE, TT, LL and SS are relatively common), and because telegraphists frequently repeated the figures-shift and letters-shift characters as their loss in an ordinary telegraph transmission could lead to gibberish. To quote the General Report on Tunny:Turingery introduced the principle that the key differenced at one, now called ΔΚ, could yield information unobtainable from ordinary key. This Δ principle was to be the fundamental basis of nearly all statistical methods of wheel-breaking and setting.Differencing was applied to each of the impulses of the ITA2 coded characters. So, for the first impulse, that was enciphered by wheels ''χ''1 and ''ψ''1, differenced at one: :::: And for the second impulse: :::: And so on. The periodicity of the ''chi'' and ''psi'' wheels for each impulse (41 and 43 respectively for the first impulse) is also reflected in the pattern of ΔK. However, given that the ''psi'' wheels did not advance for every input character, as did the ''chi'' wheels, it was not simply a repetition of the pattern every 41 × 43 = 1763 characters for ΔK1, but a more complex sequence.
Turing's method
Turing's method of deriving the cam settings of the wheels from a length of key obtained from a depth, involved aniterative
Iteration is the repetition of a process in order to generate a (possibly unbounded) sequence of outcomes. Each repetition of the process is a single iteration, and the outcome of each iteration is then the starting point of the next iteration.
...
process. Given that the delta ''psi'' character was the null character '/' half of the time on average, an assumption that had a 50% chance of being correct. The process started by treating a particular ΔK character as being the Δ''χ'' for that position. The resulting putative bit pattern of and for each ''chi'' wheel, was recorded on a sheet of paper that contained as many columns as there were characters in the key, and five rows representing the five impulses of the Δ''χ''. Given the knowledge from Tutte's work, of the periodicity of each of the wheels, this allowed the propagation of these values at the appropriate positions in the rest of the key.
A set of five sheets, one for each of the ''chi'' wheels, was also prepared. These contained a set of columns corresponding in number to the cams for the appropriate ''chi'' wheel, and were referred to as a 'cage'. So the ''χ''3 cage had 29 such columns. Successive 'guesses' of Δ''χ'' values then produced further putative cam state values. These might either agree or disagree with previous assumptions, and a count of agreements and disagreements was made on these sheets. Where disagreements substantially outweighed agreements, the assumption was made that the Δ''ψ'' character was not the null character '/', so the relevant assumption was discounted. Progressively, all the cam settings of the ''chi'' wheels were deduced, and from them, the ''psi'' and motor wheel cam settings.
As experience of the method developed, improvements were made that allowed it to be used with much shorter lengths of key than the original 500 or so characters."
Testery
The Testery was the section at Bletchley Park that performed the bulk of the work involved in decrypting Tunny messages. By July 1942, the volume of traffic was building up considerably. A new section was therefore set up, led by Ralph Tester—hence the name. The staff consisted mainly of ex-members of the Research Section, and included Peter Ericsson,Peter Hilton
Peter John Hilton (7 April 1923Peter Hilton, "On all Sorts of Automorphisms", ''The American Mathematical Monthly'', 92(9), November 1985, p. 6506 November 2010) was a British mathematician, noted for his contributions to homotopy theory and f ...
, Denis Oswald and Jerry Roberts
Captain Raymond C. "Jerry" Roberts MBE (18 November 1920 – 25 March 2014) was a British wartime codebreaker and businessman. During the Second World War, Roberts worked at the Government Code and Cypher School at Bletchley Park from 194 ...
. The Testery's methods were almost entirely manual, both before and after the introduction of automated methods in the Newmanry to supplement and speed up their work.
The first phase of the work of the Testery ran from July to October, with the predominant method of decryption being based on depths and partial depths. After ten days, however, the formulaic start of the messages was replaced by nonsensical ''quatsch'', making decryption more difficult. This period was productive nonetheless, even though each decryption took considerable time. Finally, in September, a depth was received that allowed Turing's method of wheel breaking, "Turingery
Turingery in ''Testery Methods 1942–1944'' or Turing's method (playfully dubbed Turingismus by Peter Ericsson, Peter Hilton and Donald Michie) was a manual codebreaking method devised in July 1942 by the mathematician and cryptanalyst Alan Turi ...
", to be used, leading to the ability to start reading current traffic. Extensive data about the statistical characteristics of the language of the messages was compiled, and the collection of cribs extended.
In late October 1942 the original, experimental Tunny link was closed and two new links (Codfish and Octopus) were opened. With these and subsequent links, the 12-letter indicator system of specifying the message key was replaced by the QEP system. This meant that only full depths could be recognised—from identical QEP numbers—which led to a considerable reduction in traffic decrypted.
Once the Newmanry became operational in June 1943, the nature of the work performed in the Testery changed, with decrypts, and wheel breaking no longer relying on depths.
British Tunny
 The so-called "British Tunny Machine" was a device that exactly replicated the functions of the SZ40/42 machines. It was used to produce the German cleartext from a ciphertext tape, after the cam settings had been determined. The functional design was produced at Bletchley Park where ten Testery Tunnies were in use by the end of the war. It was designed and built in
The so-called "British Tunny Machine" was a device that exactly replicated the functions of the SZ40/42 machines. It was used to produce the German cleartext from a ciphertext tape, after the cam settings had been determined. The functional design was produced at Bletchley Park where ten Testery Tunnies were in use by the end of the war. It was designed and built in Tommy Flowers
Thomas Harold Flowers Order of the British Empire, MBE (22 December 1905 – 28 October 1998) was an English engineer with the British General Post Office. During World War II, Flowers designed and built Colossus computer, Colossus, the world's ...
' laboratory at the General Post Office Research Station at Dollis Hill by Gil Hayward
Gilbert Osborne Hayward (16 October 1917—9 October 2011) was a World War II cryptographer and inventor of the first electronic seal security device.
Career
As a pupil at Kilburn Grammar School, Hayward became captivated by machines and scien ...
, "Doc" Coombs, Bill Chandler and Sid Broadhurst. It was mainly built from standard British telephone exchange electro-mechanical
Electromechanics combine processes and procedures drawn from electrical engineering and mechanical engineering. Electromechanics focus on the interaction of electrical and mechanical systems as a whole and how the two systems interact with each ...
equipment such as relay
A relay
Electromechanical relay schematic showing a control coil, four pairs of normally open and one pair of normally closed contacts
An automotive-style miniature relay with the dust cover taken off
A relay is an electrically operated switc ...
s and uniselectors. Input and output was by means of a teleprinter with paper tape reading and punching. These machines were used in both the Testery and later the Newmanry. Dorothy Du Boisson who was a machine operator and a member of the Women's Royal Naval Service
The Women's Royal Naval Service (WRNS; popularly and officially known as the Wrens) was the women's branch of the United Kingdom's Royal Navy. First formed in 1917 for the World War I, First World War, it was disbanded in 1919, then revived in ...
(Wren), described plugging up the settings as being like operating an old fashioned telephone exchange and that she received electric shocks in the process.
When Flowers was invited by Hayward to try the first British Tunny machine at Dollis Hill by typing in the standard test phrase: "Now is the time for all good men to come to the aid of the party", he much appreciated that the rotor functions had been set up to provide the following Wordsworthian output:
Additional features were added to the British Tunnies to simplify their operation. Further refinements were made for the versions used in the Newmanry, the third Tunny being equipped to produce de-''chi'' tapes.
Newmanry
The Newmanry was a section set up underMax Newman
Maxwell Herman Alexander Newman, FRS (7 February 1897 – 22 February 1984), generally known as Max Newman, was a British mathematician and codebreaker. His work in World War II led to the construction of Colossus, the world's first operatio ...
in December 1942 to look into the possibility of assisting the work of the Testery by automating parts of the processes of decrypting Tunny messages. Newman had been working with Gerry Morgan, head of the Research Section on ways of breaking Tunny when Bill Tutte approached them in November 1942 with the idea of what became known as the "1+2 break in". This was recognised as being feasible, but only if automated.
Newman produced a functional specification of what was to become the "Heath Robinson
William Heath Robinson (31 May 1872 – 13 September 1944) was an English cartoonist, illustrator and artist who drew whimsically elaborate machines to achieve simple objectives.
The earliest citation in the ''Oxford English Dictionary'' f ...
" machine. He recruited the Post Office Research Station
The Post Office Research Station was first established as a separate section of the General Post Office in 1909.
In 1921, the Research Station moved to Dollis Hill, north west London, initially in ex-army huts.
The main permanent buildings at ...
at Dollis Hill, and Dr C.E. Wynn-Williams at the Telecommunications Research Establishment
The Telecommunications Research Establishment (TRE) was the main United Kingdom research and development organisation for radio navigation, radar, infra-red detection for heat seeking missiles, and related work for the Royal Air Force (RAF) ...
(TRE) at Malvern to implement his idea. Work on the engineering design started in January 1943 and the first machine was delivered in June. The staff at that time consisted of Newman, Donald Michie
Donald Michie (; 11 November 1923 – 7 July 2007) was a British researcher in artificial intelligence. During World War II, Michie worked for the Government Code and Cypher School at Bletchley Park, contributing to the effort to solve " Tunny ...
, Jack Good, two engineers and 16 Wrens. By the end of the war the Newmanry contained three Robinson machines, ten Colossus Computers and a number of British Tunnies. The staff were 26 cryptographers, 28 engineers and 275 Wrens.
The automation of these processes required the processing of large quantities of punched paper tape such as those on which the enciphered messages were received. Absolute accuracy of these tapes and their transcription was essential, as a single character in error could invalidate or corrupt a huge amount of work. Jack Good introduced the maxim "If it's not checked it's wrong".
The "1+2 break in"
W. T. Tutte developed a way of exploiting the non-uniformity ofbigram
A bigram or digram is a sequence of two adjacent elements from a string of tokens, which are typically letters, syllables, or words. A bigram is an ''n''-gram for ''n''=2.
The frequency distribution of every bigram in a string is commonly used f ...
s (adjacent letters) in the German plaintext using the differenced cyphertext and key components. His method was called the "1+2 break in", or "double-delta attack". The essence of this method was to find the initial settings of the ''chi'' component of the key by exhaustively trying all positions of its combination with the ciphertext, and looking for evidence of the non-uniformity that reflected the characteristics of the original plaintext. The wheel breaking process had to have successfully produced the current cam settings to allow the relevant sequence of characters of the ''chi'' wheels to be generated. It was totally impracticable to generate the 22 million characters from all five of the ''chi'' wheels, so it was initially limited to 41 × 31 = 1271 from the first two.
Given that for each of the five impulses ''i'':
::::
and hence
::::
for the first two impulses:
::::
Calculating a putative in this way for each starting point of the sequence would yield xs and •s with, in the long run, a greater proportion of •s when the correct starting point had been used. Tutte knew, however, that using the differenced (∆) values amplified this effect because any repeated characters in the plaintext would always generate •, and similarly ∆''ψ''1 ⊕ ∆''ψ''2 would generate • whenever the ''psi'' wheels did not move on, and about half of the time when they did – some 70% overall.
Tutte analyzed a decrypted ciphertext with the differenced version of the above function:
::::
and found that it generated • some 55% of the time. Given the nature of the contribution of the ''psi'' wheels, the alignment of ''chi''-stream with the ciphertext that gave the highest count of •s from was the one that was most likely to be correct. This technique could be applied to any pair of impulses and so provided the basis of an automated approach to obtaining the de-''chi'' (D) of a ciphertext, from which the ''psi'' component could be removed by manual methods.
Robinsons
Heath Robinson
William Heath Robinson (31 May 1872 – 13 September 1944) was an English cartoonist, illustrator and artist who drew whimsically elaborate machines to achieve simple objectives.
The earliest citation in the ''Oxford English Dictionary'' f ...
was the first machine produced to automate Tutte's 1+2 method. It was given the name by the Wrens
Wrens are a family (biology), family, Troglodytidae, of small brown passerine birds. The family includes 96 species and is divided into 19 genus, genera. All species are restricted to the New World except for the Eurasian wren that is widely di ...
who operated it, after cartoonist William Heath Robinson, who drew immensely complicated mechanical devices for simple tasks, similar to the American cartoonist Rube Goldberg
Reuben Garrett Lucius Goldberg (July 4, 1883 – December 7, 1970), better known as Rube Goldberg (), was an American cartoonist, sculptor, author, engineer, and inventor.
Goldberg is best known for his popular cartoons depicting complicated ...
.
The functional specification of the machine was produced by Max Newman. The main engineering design was the work of Frank Morrell at the Post Office Research Station
The Post Office Research Station was first established as a separate section of the General Post Office in 1909.
In 1921, the Research Station moved to Dollis Hill, north west London, initially in ex-army huts.
The main permanent buildings at ...
at Dollis Hill in North London, with his colleague Tommy Flowers designing the "Combining Unit". Dr C. E. Wynn-Williams from the Telecommunications Research Establishment
The Telecommunications Research Establishment (TRE) was the main United Kingdom research and development organisation for radio navigation, radar, infra-red detection for heat seeking missiles, and related work for the Royal Air Force (RAF) ...
at Malvern produced the high-speed electronic valve and relay counters. Construction started in January 1943, the prototype machine was in use at Bletchley Park in June.
The main parts of the machine were:
* a tape transport and reading mechanism (dubbed the "bedstead" because of its resemblance to an upended metal bed frame) that ran the looped key and message tapes at between 1000 and 2000 characters per second;
* a combining unit that implemented the logic of Tutte's method;
* a counting unit that counted the number of •s, and if it exceeded a pre-set total, displayed or printed it.
The prototype machine was effective despite a number of serious shortcomings. Most of these were progressively overcome in the development of what became known as "Old Robinson".
Colossus
 Tommy Flowers' had reservations about Heath Robinson's two synchronised tape loops, and his previous, unique experience of thermionic valves (vacuum tubes) led him to realize that a better machine could be produced using electronics. Instead of the key stream being read from a second punched paper tape, an electronically generated key stream could allow much faster and more flexible processing. Flowers' suggestion that this could be achieved with a machine that was entirely electronic and would contain between one and two thousand valves, was treated with incredulity at both the Telecommunications Research Establishment and at Bletchley Park, as it was thought that it would be "too unreliable to do useful work". He did, however, have the support of the Controller of Research at Dollis Hill, W Gordon Radley, and he implemented these ideas producing
Tommy Flowers' had reservations about Heath Robinson's two synchronised tape loops, and his previous, unique experience of thermionic valves (vacuum tubes) led him to realize that a better machine could be produced using electronics. Instead of the key stream being read from a second punched paper tape, an electronically generated key stream could allow much faster and more flexible processing. Flowers' suggestion that this could be achieved with a machine that was entirely electronic and would contain between one and two thousand valves, was treated with incredulity at both the Telecommunications Research Establishment and at Bletchley Park, as it was thought that it would be "too unreliable to do useful work". He did, however, have the support of the Controller of Research at Dollis Hill, W Gordon Radley, and he implemented these ideas producing Colossus
Colossus, Colossos, or the plural Colossi or Colossuses, may refer to:
Statues
* Any exceptionally large statue; colossal statues, are generally taken to mean a statue at least twice life-size
** List of tallest statues
** :Colossal statues
* ...
, the world's first electronic, digital, computing machine that was at all programmable, in the remarkably short time of ten months. In this he was assisted by his colleagues at the Post Office Research Station
The Post Office Research Station was first established as a separate section of the General Post Office in 1909.
In 1921, the Research Station moved to Dollis Hill, north west London, initially in ex-army huts.
The main permanent buildings at ...
Dollis Hill
Dollis Hill is an area in northwest London, which consists of the streets surrounding the Gladstone Park, London, Gladstone Park. It is served by a London Underground station, Dollis Hill tube station, Dollis Hill, on the Jubilee line, providi ...
: Sidney Broadhurst, William Chandler, Allen Coombs
Allen William Mark (Doc) Coombs (23 October 1911 – 30 January 1995) was a British electronics engineer at the Post Office Research Station, Dollis Hill.
Coombs was one of the principal designers of the Mark II or production version of the ...
and Harry Fensom.
The prototype Mark 1 Colossus (Colossus I), with its 1500 valves, became operational at Dollis Hill in December 1943 and became fully operational at Bletchley Park on 5 February 1944. This processed the message at 5000 characters per second using the impulse from reading the tape's sprocket holes to act as the clock signal
In electronics and especially synchronous digital circuits, a clock signal (historically also known as ''logic beat'') is an electronic logic signal (voltage or current) which oscillates between a high and a low state at a constant frequency and ...
. It quickly became evident that this was a huge leap forward in cryptanalysis of Tunny. Further Colossus machines were ordered and the orders for more Robinsons cancelled. An improved Mark 2 Colossus (Colossus II) contained 2400 valves and first worked at Bletchley Park on 1 June 1944, just in time for the D-day Normandy landings.
The main parts of this machine were:
* a tape transport and reading mechanism (the "bedstead") that ran the message tape in a loop at 5000 characters per second;
* a unit that generated the key stream electronically;
* five parallel processing units that could be programmed to perform a large range of Boolean operations (in the Mark II Colossus);
* five counting units that each counted the number of •s or xs, and if it exceeded a pre-set total, printed it out.
The five parallel processing units allowed Tutte's "1+2 break in" and other functions to be run at an effective speed of 25,000 characters per second by the use of circuitry invented by Flowers that would now be called a shift register
A shift register is a type of digital circuit using a cascade of flip-flop (electronics), flip-flops where the output of one flip-flop is connected to the input of the next. They share a single clock signal, which causes the data stored in the syst ...
. Donald Michie worked out a method of using Colossus to assist in wheel breaking as well as for wheel setting in early 1944. This was then implemented in special hardware on later Colossi.
A total of ten Colossus computers were in use and an eleventh was being commissioned at the end of the war in Europe (VE-Day
Victory in Europe Day is the day celebrating the formal acceptance by the Allies of World War II of German Instrument of Surrender, Germany's unconditional surrender of Wehrmacht, its armed forces on Tuesday, 8 May 1945; it marked the official su ...
). Of the ten, seven were used for "wheel setting" and 3 for "wheel breaking".
Special machines
As well as the commercially produced teleprinters and re-perforators, a number of other machines were built to assist in the preparation and checking of tapes in the Newmanry and Testery. The approximate complement as of May 1945 was as follows.Steps in wheel setting
Working out the start position of the ''chi'' (''χ'') wheels required first that their cam settings had been determined by "wheel breaking". Initially, this was achieved by two messages having been sent in depth. The number of start positions for the first two wheels, ''χ''1 and ''χ''2 was 41×31 = 1271. The first step was to try all of these start positions against the message tape. This was Tutte's "1+2 break in" which involved computing —which gives a putative ()—and counting the number of times this gave •. Incorrect starting positions would, on average, give a dot count of 50% of the message length. On average, the dot count for a correct starting point would be 54%, but there was inevitably a considerable spread of values around these averages. Both Heath Robinson, which was developed into what became known as "Old Robinson", and Colossus were designed to automate this process. Statistical theory allowed the derivation of measures of how far any count was from the 50% expected with an incorrect starting point for the ''chi'' wheels. This measure of deviation from randomness was called sigma. Starting points that gave a count of less than 2.5 × sigma, named the "set total", were not printed out. The ideal for a run to set ''χ''1 and ''χ''2 was that a single pair of trial values produced one outstanding value for sigma thus identifying the start positions of the first two ''chi'' wheels. An example of the output from such a run on a Mark 2 Colossus with its five counters: a, b, c, d and e, is given below. With an average-sized message, this would take about eight minutes. However, by utilising the parallelism of the Mark 2 Colossus, the number of times the message had to be read could be reduced by a factor of five, from 1271 to 255. Having identified possible ''χ''1, ''χ''2 start positions, the next step was to try to find the start positions for the other ''chi'' wheels. In the example given above, there is a single setting of ''χ''1 = 36 and ''χ''2 = 21 whose sigma value makes it stand out from the rest. This was not always the case, and Small enumerates 36 different further runs that might be tried according to the result of the ''χ''1, ''χ''2 run. At first the choices in this iterative process were made by the cryptanalyst sitting at the typewriter output, and calling out instructions to the Wren operators. Max Newman devised a decision tree and then set Jack Good and Donald Michie the task of devising others. These were used by the Wrens without recourse to the cryptanalysts if certain criteria were met. In the above one of Small's examples, the next run was with the first two ''chi'' wheels set to the start positions found and three separate parallel explorations of the remaining three ''chi'' wheels. Such a run was called a "short run" and took about two minutes. So the probable start positions for the ''chi'' wheels are: ''χ''1 = 36, ''χ''2 = 21, ''χ''3 = 01, ''χ''4 = 19, ''χ''5 = 04. These had to be verified before the de-''chi'' (D) message was passed to the Testery. This involved Colossus performing a count of the frequency of the 32 characters in ΔD. Small describes the check of the frequency count of the ΔD characters as being the "acid test", and that practically every cryptanalyst and Wren in the Newmanry and Testery knew the contents of the following table by heart. If the derived start points of the ''chi'' wheels passed this test, the de-''chi''-ed message was passed to the Testery where manual methods were used to derive the ''psi'' and motor settings. As Small remarked, the work in the Newmanry took a great amount of statistical science, whereas that in the Testery took much knowledge of language and was of great interest as an art. Cryptanalyst Jerry Roberts made the point that this Testery work was a greater load on staff than the automated processes in the Newmanry.See also
* The National Museum of ComputingNotes and references
Bibliography
* * in * * * * * * in * in * Updated and extended version of ''Action This Day: From Breaking of the Enigma Code to the Birth of the Modern Computer'' Bantam Press 2001 * in * * in * * That version is a facsimile copy, but there is a transcript of much of this document in '.pdf' format at: , and a web transcript of Part 1 at: * * in * in * * in * in * * in * * * in * in * in * * * in * Transcript of a lecture given by Prof. Tutte at theUniversity of Waterloo
The University of Waterloo (UWaterloo, UW, or Waterloo) is a Public university, public research university located in Waterloo, Ontario, Canada. The main campus is on of land adjacent to uptown Waterloo and Waterloo Park. The university also op ...
* in
* in
{{Refend
Bletchley Park
History of computing in the United Kingdom
History of cryptography
Signals intelligence of World War II