Carna Botnet on:
[Wikipedia]
[Google]
[Amazon]
 The Carna botnet was a
The Carna botnet was a
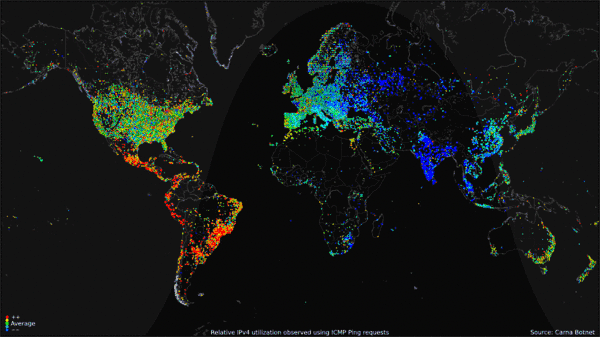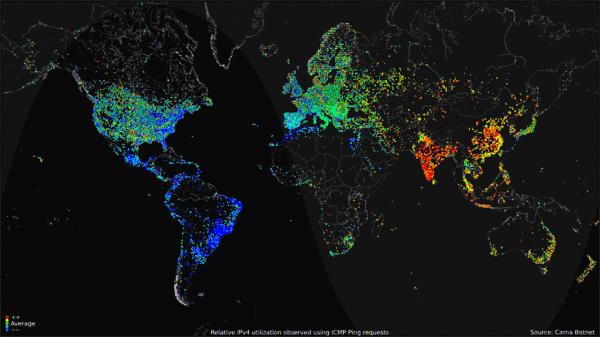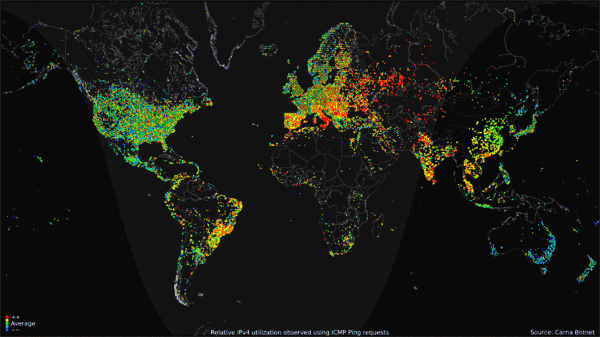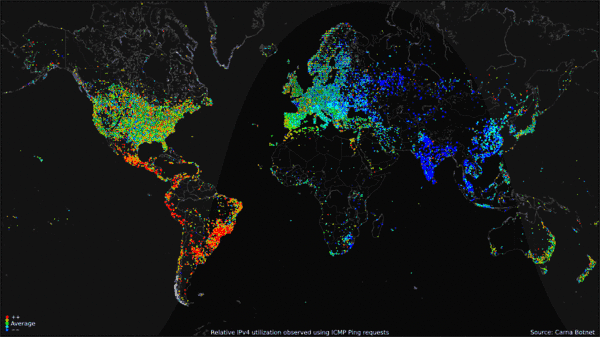
, Carna Botnet, June - Oktober 2012 Collected data was compiled into a
Internet Census 2012: Port scanning /0 using insecure embedded devices
Carna Botnet, June — October 2012 * All of the data can be found o
GitHub
and
 The Carna botnet was a
The Carna botnet was a botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its conn ...
of 420,000 devices created by an anonymous hacker
A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term ''hacker'' has become associated in popu ...
to measure the extent of the Internet in what the creator called the “Internet Census of 2012”.
Data collection
The data was collected by infiltrating Internet devices, especially routers, that used adefault password
Where a device needs a username and/or password to log in, a default password is usually provided that allows the device to be accessed during its initial setup, or after resetting to factory defaults.
Manufacturers of such equipment typically u ...
or no password at all. It was named after Carna, "the Roman goddess for the protection of inner organs and health".Internet Census 2012: Port scanning /0 using insecure embedded devices, Carna Botnet, June - Oktober 2012 Collected data was compiled into a
GIF
The Graphics Interchange Format (GIF; or , see pronunciation) is a bitmap image format that was developed by a team at the online services provider CompuServe led by American computer scientist Steve Wilhite and released on 15 June 1987. ...
portrait to display Internet use around the world over the course of 24 hours. The data gathered included only the IPv4
Internet Protocol version 4 (IPv4) is the fourth version of the Internet Protocol (IP). It is one of the core protocols of standards-based internetworking methods in the Internet and other packet-switched networks. IPv4 was the first version de ...
address space and not the IPv6
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communication protocol, communications protocol that provides an identification and location system for computers on networks and routes traffic ...
address space.
The Carna Botnet creator believes that with a growing number of IPv6 hosts on the Internet, 2012 may have been the last time a census like this was possible.
Results
Of the 4.3 billion possible IPv4 addresses, Carna Botnet found a total of 1.3 billion addresses in use, including 141 million that were behind a firewall and 729 million that returned reversedomain name system
The Domain Name System (DNS) is a hierarchical and distributed naming system for computers, services, and other resources in the Internet or other Internet Protocol (IP) networks. It associates various information with domain names assigned to ...
records. The remaining 2.3 billion IPv4 addresses are probably not used.
An earlier first Internet census by the USDHS LANDER-study had counted 187 million visible Internet hosts in 2006.
Further implications
The data provided by the Carna botnet was used by security researcher Morgan Marquis-Boire to determine in how many countries FinFisher spyware was being used. The use of such legally-gray data to conduct open source analysis raised questions for some, but Marquis-Boire expressed a belief that data is data. "I consider this more like rogue academia rather than criminal activity," he told Wired Magazine.Number of hosts by top level domain
Amongst other, Carna Botnet counted the number of hosts with reverse DNS names observed from May to October 2012. The top 20Top Level Domain
A top-level domain (TLD) is one of the domains at the highest level in the hierarchical Domain Name System of the Internet after the root domain. The top-level domain names are installed in the root zone of the name space. For all domains in ...
s were:
See also
*BASHLITE
BASHLITE (also known as Gafgyt, Lizkebab, PinkSlip, Qbot, Torlus and LizardStresser) is malware which infects Linux systems in order to launch distributed denial-of-service attacks (DDoS). Originally it was also known under the name Bashdoor, b ...
* Mirai (malware)
Mirai (from the Japanese word for "future", 未来) is a malware that turns networked devices running Linux into remotely controlled bots that can be used as part of a botnet in large-scale network attacks. It primarily targets online consumer d ...
* Remaiten
Remaiten is malware which infects Linux on embedded systems by brute forcing using frequently used default username and passwords combinations from a list in order to infect a system.
Remaiten combines the features of the Tsunami and LizardSt ...
* Linux.Darlloz
* Linux.Wifatch
* Hajime (malware)
Hajime (Japanese for "beginning") is a malware which appears to be similar to the Wifatch malware in that it appears to attempt to secure devices.
Hajime is also far more advanced than Mirai, according to various researchers.
The top countries ...
References
External links
Internet Census 2012: Port scanning /0 using insecure embedded devices
Carna Botnet, June — October 2012 * All of the data can be found o
GitHub
and
Internet Archive
The Internet Archive is an American digital library with the stated mission of "universal access to all knowledge". It provides free public access to collections of digitized materials, including websites, software applications/games, music, ...
.
{{IoT Malware
Botnets
History of the Internet
IoT malware
Cybercrime in India