Blacklist (computing) on:
[Wikipedia]
[Google]
[Amazon]
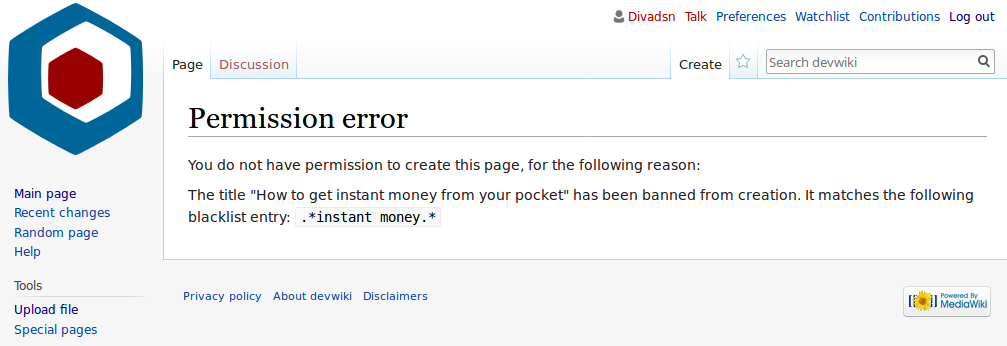 In
In
Email
Most email providers have an
Blackweb
* A
Password RBL
offers a password blacklist for Microsoft's
"“Blacklists” and “whitelists”: a salutary warning concerning the prevalence of racist language in discussions of predatory publishing."
/ref> was released making claims that "white" and "black" are racially-charged terms that need to be avoided in instances such as "whitelist" and "blacklist". The journal hit mainstream in Summer 2020 following the
Squidblacklist.org - Blacklists For Squid Proxy and Content Filtering Applications.
ipfilterX by Nexus23 Labs - Blocks P2P Crawlers, Malware C&C IPs, Institutions and many more.
OpenBL.org
- abuse reporting and blacklisting
 In
In computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computing machinery. It includes the study and experimentation of algorithmic processes, and development of both hardware and software. Computing has scientific, ...
, a blacklist, disallowlist, blocklist, or denylist is a basic access control mechanism that allows through all elements (email addresses, users, passwords, URLs
A Uniform Resource Locator (URL), colloquially termed as a web address, is a reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it. A URL is a specific type of Uniform Resource Identifi ...
, IP address
An Internet Protocol address (IP address) is a numerical label such as that is connected to a computer network that uses the Internet Protocol for communication.. Updated by . An IP address serves two main functions: network interface ident ...
es, domain name
A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are often used to identify services provided through the Internet, such as websites, email services and more. As ...
s, file hashes, etc.), except those explicitly mentioned. Those items on the list are denied access. The opposite is a whitelist
A whitelist, allowlist, or passlist is a mechanism which explicitly allows some identified entities to access a particular privilege, service, mobility, or recognition i.e. it is a list of things allowed when everything is denied by default. It is ...
, allowlist, or passlist, in which only items on the list are let through whatever gate is being used. A greylist contains items that are temporarily blocked (or temporarily allowed) until an additional step is performed.
Blacklists can be applied at various points in a security architecture, such as a host, web proxy
In computer networking, a proxy server is a server application that acts as an intermediary between a client requesting a resource and the server providing that resource.
Instead of connecting directly to a server that can fulfill a request ...
, DNS servers, email
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic ( digital) version of, or counterpart to, mail, at a time when "mail" mean ...
server, firewall
Firewall may refer to:
* Firewall (computing), a technological barrier designed to prevent unauthorized or unwanted communications between computer networks or hosts
* Firewall (construction), a barrier inside a building, designed to limit the spr ...
, directory server
In computing, a directory service or name service maps the names of network resources to their respective network addresses. It is a shared information infrastructure for locating, managing, administering and organizing everyday items and network ...
s or application authentication gateways. The type of element blocked is influenced by the access control location. DNS servers may be well-suited to block domain names, for example, but not URLs. A firewall is well-suited for blocking IP addresses, but less so for blocking malicious files or passwords.
Example uses include a company that might prevent a list of software from running on its network, a school that might prevent access to a list of websites from its computers, or a business that wants to ensure their computer users are not choosing easily guessed, poor passwords.
Examples of systems protected
Blacklists are used to protect a variety of systems in computing. The content of the blacklist is likely needs to be targeted to the type of system defended.Information systems
An information system includes end-point hosts like user machines and servers. A blacklist in this location may include certain types of software that are not allowed to run in the company environment. For example, a company might blacklist peer to peer file sharing on its systems. In addition to software, people, devices and Web sites can also be blacklisted.anti-spam
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email).
No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email (false positives) as opposed to ...
feature that essentially blacklists certain email address
An email address identifies an email box to which messages are delivered. While early messaging systems used a variety of formats for addressing, today, email addresses follow a set of specific rules originally standardized by the Internet Engineer ...
es if they are deemed unwanted. For example, a user who wearies of unstoppable emails from a particular address may blacklist that address, and the email client will automatically route all messages from that address to a junk-mail folder or delete them without notifying the user.
An e-mail spam
Email spam, also referred to as junk email, spam mail, or simply spam, is unsolicited messages sent in bulk by email (spamming).
The name comes from a Monty Python sketch in which the name of the canned pork product Spam is ubiquitous, unavoida ...
filter
Filter, filtering or filters may refer to:
Science and technology
Computing
* Filter (higher-order function), in functional programming
* Filter (software), a computer program to process a data stream
* Filter (video), a software component tha ...
may keep a blacklist of email addresses, any mail from which would be prevented from reaching its intended destination. It may also use sending domain names or sending IP addresses to implement a more general block.
In addition to private email blacklists, there are lists that are kept for public use, including:
* China Anti-Spam Alliance
* Fabel Spamsources
* Spam and Open Relay Blocking System
SORBS ("Spam and Open Relay Blocking System") is a list of e-mail servers suspected of sending or relaying spam (a DNS Blackhole List). It has been augmented with complementary lists that include various other classes of hosts, allowing for cu ...
* The DrMX Project
Web browsing
The goal of a blacklist in a web browser is to prevent the user from visiting a malicious or deceitful web page via filtering locally. A common web browsing blacklist is Google's Safe Browsing, which is installed by default in Firefox, Safari, and Chrome.Usernames and passwords
Blacklisting can also apply to user credentials. It is common for systems or websites to blacklist certain reserved usernames that are not allowed to be chosen by the system or website's user populations. These reserved usernames are commonly associated with built-in system administration functions. Also usually blocked by default are profane words and racial slurs. Password blacklists are very similar to username blacklists but typically contain significantly more entries than username blacklists. Password blacklists are applied to prevent users from choosing passwords that are easily guessed or are well known and could lead to unauthorized access by malicious parties. Password blacklists are deployed as an additional layer of security, usually in addition to a password policy, which sets the requirements of the password length and/or character complexity. This is because there are a significant number of password combinations that fulfill many password policies but are still easily guessed (i.e., Password123, Qwerty123).Distribution methods
Blacklists are distributed in a variety of ways. Some use simple mailing lists. ADNSBL
A Domain Name System blocklist, Domain Name System-based blackhole list, Domain Name System blacklist (DNSBL) or real-time blackhole list (RBL) is a service for operation of mail servers to perform a check via a Domain Name System (DNS) query whe ...
is a common distribution method that leverages the DNS itself. Some lists make use of rsync
rsync is a utility for efficiently transferring and synchronizing files between a computer and a storage drive and across networked computers by comparing the modification times and sizes of files. It is commonly found on Unix-like opera ...
for high-volume exchanges of data. Web-server functions may be used; either simple GET
Get or GET may refer to:
* Get (animal), the offspring of an animal
* Get (divorce document), in Jewish religious law
* GET (HTTP), a type of HTTP request
* "Get" (song), by the Groggers
* Georgia Time, used in the Republic of Georgia
* Get AS, a ...
requests may be used or more complicated interfaces such as a RESTful API.
Examples
* For a list of some DNS-based blacklists, see theComparison of DNS blacklists
__NOTOC__
The following table lists technical information for assumed reputable DNS blacklists used for blocking spam.
Notes
"Collateral listings"—Deliberately listing non-offending IP addresses, in order to coerce ISPs to take action agains ...
.
* Companies like Google
Google LLC () is an American Multinational corporation, multinational technology company focusing on Search Engine, search engine technology, online advertising, cloud computing, software, computer software, quantum computing, e-commerce, ar ...
, Symantec and Sucuri keep internal blacklists of sites known to have malware and they display a warning before allowing the user to click them.
* Content-control software
An Internet filter is software that restricts or controls the content an Internet user is capable to access, especially when utilized to restrict material delivered over the Internet via the Web, Email, or other means. Content-control software dete ...
such as DansGuardian
DansGuardian, written by SmoothWall Ltd and others, is content-control software: software designed to control which websites users can access. It also includes virus filtering and usage monitoring features. DansGuardian must be installed on a ...
and SquidGuard may work with a blacklist in order to block URLs
A Uniform Resource Locator (URL), colloquially termed as a web address, is a reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it. A URL is a specific type of Uniform Resource Identifi ...
of sites deemed inappropriate for a work or educational environment. Such blacklists can be obtained free of charge or from commercial vendors such as Squidblacklist.org.
* There are also free blacklists for Squid (software) proxy, such aBlackweb
* A
firewall
Firewall may refer to:
* Firewall (computing), a technological barrier designed to prevent unauthorized or unwanted communications between computer networks or hosts
* Firewall (construction), a barrier inside a building, designed to limit the spr ...
or IDS may also use a blacklist to block known hostile IP addresses and/or networks. An example for such a list would be the OpenBL project.
* Many copy protection
Copy protection, also known as content protection, copy prevention and copy restriction, describes measures to enforce copyright by preventing the reproduction of software, films, music, and other media.
Copy protection is most commonly found o ...
schemes include software blacklisting.
* The companPassword RBL
offers a password blacklist for Microsoft's
Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of Process (computing), processes and Windows service, services. Initially, Active D ...
, web sites and apps, distributed via a RESTful API.
* Members of online auction
An online auction (also electronic auction, e-auction, virtual auction, or eAuction) is an auction held over the internet and accessed by internet connected devices. Similar to in-person auctions, online auctions come in a variety of types, with ...
sites may add other members to a personal blacklist. This means that they cannot bid on or ask questions about your auctions, nor can they use a "buy it now" function on your items.
* Yet another form of list is the yellow list which is a list of email server IP addresses that send mostly good email but do send some spam. Examples include Yahoo
Yahoo! (, styled yahoo''!'' in its logo) is an American web services provider. It is headquartered in Sunnyvale, California and operated by the namesake company Yahoo Inc., which is 90% owned by investment funds managed by Apollo Global Manage ...
, Hotmail
Outlook.com is a webmail service that is part of the Microsoft 365 product family. It offers mail, Calendaring software, calendaring, Address book, contacts, and Task management, tasks services.
Founded in 1996 by Sabeer Bhatia and Jack Smit ...
, and Gmail
Gmail is a free email service provided by Google. As of 2019, it had 1.5 billion active users worldwide. A user typically accesses Gmail in a web browser or the official mobile app. Google also supports the use of email clients via the POP and ...
. A yellow listed server is a server that should never be accidentally blacklisted. The yellow list is checked first and if listed then blacklist tests are ignored.
* In Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, w ...
modprobe
modprobe is a Linux program originally written by Rusty Russell and used to add a loadable kernel module to the Linux kernel or to remove a loadable kernel module from the kernel. It is commonly used indirectly: udev relies upon modprobe to load d ...
, the blacklist modulename entry in a modprobe configuration file indicates that all of the particular module
Module, modular and modularity may refer to the concept of modularity. They may also refer to:
Computing and engineering
* Modular design, the engineering discipline of designing complex devices using separately designed sub-components
* Mo ...
's internal aliases are to be ignored. There are cases where two or more modules both support the same devices, or a module invalidly claims to support a device.
* Many web browsers have the ability to consult anti-phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious softwa ...
blacklists in order to warn users who unwittingly aim to visit a fraudulent website.
* Many peer-to-peer file sharing
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program th ...
programs support blacklists that block access from sites known to be owned by companies enforcing copyright. An example is the Bluetack blocklist set.
Usage considerations
As expressed in a recent conference paper focusing on blacklists of domain names and IP addresses used for Internet security, "these lists generally do not intersect. Therefore, it appears that these lists do not converge on one set of malicious indicators." This concern combined with an economic model means that, while blacklists are an essential part of network defense, they need to be used in concert with whitelists and greylists.Controversy over use of the term
In 2018, a journal commentary on a report onpredatory publishing
Predatory publishing, also write-only publishing or deceptive publishing, is an exploitative academic publishing business model that involves charging publication fees to authors without checking articles for quality and legitimacy, and withou ...
Houghton, F., & Houghton, S. (2018)"“Blacklists” and “whitelists”: a salutary warning concerning the prevalence of racist language in discussions of predatory publishing."
/ref> was released making claims that "white" and "black" are racially-charged terms that need to be avoided in instances such as "whitelist" and "blacklist". The journal hit mainstream in Summer 2020 following the
George Floyd protests
The George Floyd protests were a series of protests and civil unrest against police brutality and racism that began in Minneapolis on May 26, 2020, and largely took place during 2020. The civil unrest and protests began as part of internat ...
in America wherein a black man was murdered by an officer, sparking protests on police brutality.
The premise of the journal is that "black" and "white" have negative and positive connotations respectively. It states that since "blacklist"'s first recorded usage was during "the time of mass enslavement and forced deportation of Africans to work in European-held colonies in the Americas," the word is therefore related to race. There is no mention of "whitelist" and its origin or relation to race.
This issue is most widely disputed in computing industries where "whitelist" and "blacklist" are prevalent (e.g. IP whitelisting). Despite the commentary-nature of the journal, some companies and individuals in others have taken to replacing "whitelist" and "blacklist" with new alternatives such as "allow list" and "deny list".
Those that oppose these changes question its attribution to race, citing the same etymology quote that the 2018 journal uses. The quote suggests that the term "blacklist" arose from "black book" almost 100 years prior. "Black book" does not appear to have any etymology or sources that support ties to race, instead coming from the 1400s referring "to a list of people who had committed crimes or fallen out of favor with leaders" and popularized by King Henry VIII's literal usage of a book bound in black. Others also note the prevalence of positive and negative connotations to "white" and "black" in the bible
The Bible (from Koine Greek , , 'the books') is a collection of religious texts or scriptures that are held to be sacred in Christianity, Judaism, Samaritanism, and many other religions. The Bible is an anthologya compilation of texts ...
, predating attributions to skin tone and slavery. It wasn't until the 1960s Black Power movement that "Black" became a widespread word to refer to one's race as a person of color in America (alternate to African-American) lending itself to the argument that the negative connotation behind "black" and "blacklist" both predate attribution to race.
See also similar concerns regarding the technology terms "Master" and "Slave".
In August 2018, Ruby on Rails
Ruby on Rails (simplified as Rails) is a server-side web application framework written in Ruby under the MIT License. Rails is a model–view–controller (MVC) framework, providing default structures for a database, a web service, and we ...
changed all occurrences of "blacklist" and "whitelist" to "restricted list" and "permitted list".
Several companies responded to this controversy in June and July 2020:
* GitHub
GitHub, Inc. () is an Internet hosting service for software development and version control using Git. It provides the distributed version control of Git plus access control, bug tracking, software feature requests, task management, continu ...
announced that it would replace many "terms that may be offensive to developers in the black community".
* Apple Inc.
Apple Inc. is an American multinational technology company headquartered in Cupertino, California, United States. Apple is the largest technology company by revenue (totaling in 2021) and, as of June 2022, is the world's biggest company ...
announced at its developer conference that it would be adopting more inclusive technical language and replacing the term "blacklist" with "deny list" and the term "whitelist" with "allow list".
* Linux Foundation said it would use neutral language in kernel code and documentation in the future and avoid terms such as "blacklist" and "slave" going forward.
* The Twitter
Twitter is an online social media and social networking service owned and operated by American company Twitter, Inc., on which users post and interact with 280-character-long messages known as "tweets". Registered users can post, like, and ...
Engineering team stated its intention to move away from a number of terms, including "blacklist" and "whitelist".
* Red Hat announced that it would make open source more inclusive and avoid these and other terms.
* ZDNet
ZDNET is a business technology news website owned and operated by Red Ventures.
The brand was founded on April 1, 1991, as a general interest technology portal from Ziff Davis and evolved into an enterprise IT-focused online publication.
His ...
reports that the list of technology companies making such decisions "includes Twitter, GitHub, Microsoft, LinkedIn, Ansible, Red Hat, Splunk, Android, Go, MySQL, PHPUnit, Curl, OpenZFS, Rust, JP Morgan, and others."
References
{{ReflistExternal links
Squidblacklist.org - Blacklists For Squid Proxy and Content Filtering Applications.
ipfilterX by Nexus23 Labs - Blocks P2P Crawlers, Malware C&C IPs, Institutions and many more.
OpenBL.org
- abuse reporting and blacklisting
Computing
Computing is any goal-oriented activity requiring, benefiting from, or creating computing machinery. It includes the study and experimentation of algorithmic processes, and development of both hardware and software. Computing has scientific, ...
Computer jargon