|
Web Shell
A web shell is a shell-like interface that enables a web server to be remotely accessed, often for the purposes of cyberattacks. A web shell is unique in that a web browser is used to interact with it. A web shell could be programmed in any programming language that is supported on a server. Web shells are most commonly written in the PHP programming language due to the widespread usage of PHP for web applications. However, Active Server Pages, ASP.NET, Python, Perl, Ruby, and Unix shell scripts are also used, although these languages are less commonly used. Using network monitoring tools, an attacker can find vulnerabilities that can potentially allow delivery of a web shell. These vulnerabilities are often present in applications that are run on a web server. An attacker can use a web shell to issue shell commands, perform privilege escalation on the web server, and the ability to upload, File deletion, delete, download, and execute files to and from the web server. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shell (computing)
In computing, a shell is a computer program that exposes an operating system's services to a human user or other programs. In general, operating system shells use either a command-line interface (CLI) or graphical user interface (GUI), depending on a computer's role and particular operation. It is named a shell because it is the outermost layer around the operating system. Command-line shells require the user to be familiar with commands and their calling syntax, and to understand concepts about the shell-specific scripting language (for example, bash), while graphical shells place a low burden on beginning computer users and are characterized as being easy to use, yet most GUI-enabled operating systems also provide CLI shells, normally for performing advanced tasks. Overview Operating systems provide various services to their users, including file management, process management (running and terminating applications), batch processing, and operating system monitoring ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
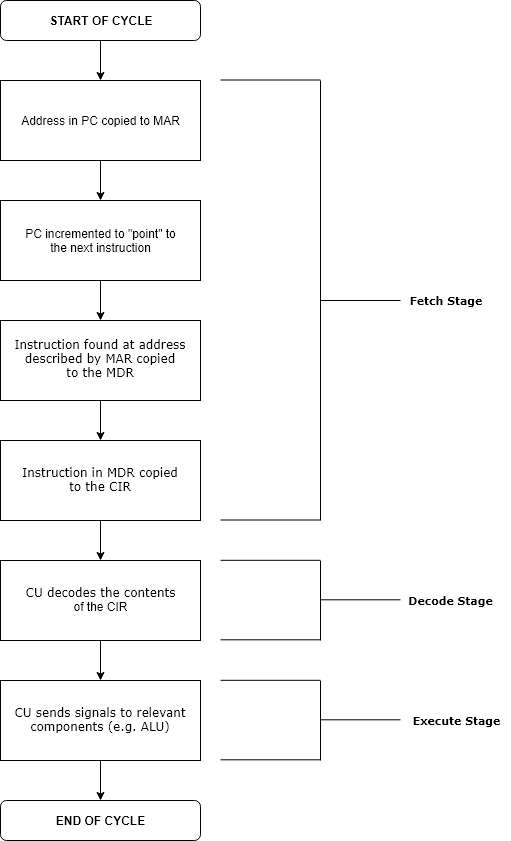
Execution (computing)
Execution in computer and software engineering is the process by which a computer or virtual machine reads and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a ' fetch–decode–execute' cycle for each instruction done by control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the semantics of those instructions. Programs for a computer may be executed in a batch process without human interaction or a user may type commands in an interactive session of an interpreter. In this case, the "commands" are simply program instructions, whose execution is chained together. The term run is used almost synonymously. A related meaning of both "to run" and "to execute" refers to the specific action of a user starting (or ''launching'' or ''invok ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spoofing Attack
In the context of information security, and especially network security, a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage. Internet Spoofing and TCP/IP Many of the protocols in the TCP/IP suite do not provide mechanisms for authenticating the source or destination of a message, leaving them vulnerable to spoofing attacks when extra precautions are not taken by applications to verify the identity of the sending or receiving host. IP spoofing and ARP spoofing in particular may be used to leverage man-in-the-middle attacks against hosts on a computer network. Spoofing attacks which take advantage of TCP/IP suite protocols may be mitigated with the use of firewalls capable of deep packet inspection or by taking measures to verify the identity of the sender or recipient of a message. Domain name spoofing The term 'Domain name spoofing' (or simply though less accurately, 'Domain spo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Arbitrary Code Execution
In computer security, arbitrary code execution (ACE) is an attacker's ability to run any commands or code of the attacker's choice on a target machine or in a target process. An arbitrary code execution vulnerability is a security flaw in software or hardware allowing arbitrary code execution. A program that is designed to exploit such a vulnerability is called an arbitrary code execution exploit. The ability to trigger arbitrary code execution over a network (especially via a wide-area network such as the Internet) is often referred to as remote code execution (RCE). Vulnerability types There are a number of classes of vulnerability that can lead to an attacker's ability to execute arbitrary commands or code. For example: * Memory safety vulnerabilities such as buffer overflows or over-reads. * Deserialization vulnerabilities * Type confusion vulnerabilities * GNU LDD arbitrary code execution Methods Arbitrary code execution is commonly achieved through control over the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Inclusion Vulnerability
A file inclusion vulnerability is a type of web vulnerability that is most commonly found to affect web applications that rely on a scripting run time. This issue is caused when an application builds a path to executable code using an attacker-controlled variable in a way that allows the attacker to control which file is executed at run time. A file include vulnerability is distinct from a generic directory traversal attack, in that directory traversal is a way of gaining unauthorized file system access, and a file inclusion vulnerability subverts how an application loads code for execution. Successful exploitation of a file inclusion vulnerability will result in remote code execution on the web server that runs the affected web application. An attacker can use remote code execution to create a web shell on the web server, which can be used for website defacement. Types of Inclusion Remote file inclusion Remote file inclusion (RFI) occurs when the web application downloads ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WordPress
WordPress (WP or WordPress.org) is a free and open-source software, free and open-source content management system (CMS) written in PHP, hypertext preprocessor language and paired with a MySQL or MariaDB database with supported secure hypertext transfer protocol, HTTPS. Features include a Plug-in (computing), plugin architecture and a Web template system, template system, referred to within WordPress as "Themes". WordPress was originally created as a blog, blog-publishing system but has evolved to support other web content types including more traditional Electronic mailing list, mailing lists and Internet fora, media galleries, membership sites, learning management systems (LMS) and Shopping cart software, online stores. One of the most popular content management system solutions in use, WordPress is used by 42.8% of the top 10 million websites . WordPress was released on May 27, 2003, by its founders, American developer Matt Mullenweg and English developer Mike Little, as a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Content Management System
A content management system (CMS) is computer software used to manage the creation and modification of digital content ( content management).''Managing Enterprise Content: A Unified Content Strategy''. Ann Rockley, Pamela Kostur, Steve Manning. New Riders, 2003. A CMS is typically used for enterprise content management (ECM) and web content management (WCM). ECM typically supports multiple users in a collaborative environment by integrating document management, digital asset management, and record retention. Alternatively, WCM is the collaborative authoring for websites and may include text and embed graphics, photos, video, audio, maps, and program code that display content and interact with the user. ECM typically includes a WCM function. Structure A CMS typically has two major components: a content management application (CMA), as the front-end user interface that allows a user, even with limited expertise, to add, modify, and remove content from a website without the i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nginx
Nginx (pronounced "engine x" ) is a web server that can also be used as a reverse proxy, load balancer, mail proxy and HTTP cache. The software was created by Igor Sysoev and publicly released in 2004. Nginx is free and open-source software, released under the terms of the 2-clause BSD license. A large fraction of web servers use Nginx, often as a load balancer. A company of the same name was founded in 2011 to provide support and ''Nginx Plus'' paid software. In March 2019, the company was acquired by F5, Inc. for $670 million. Popularity W3Tech's web server count of all web sites ranked Nginx first with 33.6%. Apache was second at 31.4% and Cloudflare Server third at 21.6%. , Netcraft estimated that Nginx served 22.01% of the million busiest websites with Apache a little ahead at 23.04%. Cloudflare at 19.53% and Microsoft Internet Information Services at 5.78% rounded out the top four servers for the busiest websites. Some of Netcraft's other statistics show Ng ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SQL Injection
In computing, SQL injection is a code injection technique used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database. SQL injection attacks allow attackers to spoof identity, tamper with existing data, cause repudiation issues such as voiding transactions or changing balances, allow the complete disclosure of all data on the system, destroy the data or make it otherwise unavailable, and become administrators of the database server. In a 2012 study, it was observed that the avera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Denial-of-service Attack
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In a distributed denial-of-service attack (DDoS attack), the incoming traffic flooding the victim originates from many different sources. More sophisticated strategies are required to mitigate this type of attack, as simply attempting to block a single source is insufficient because there are multiple sources. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade. Criminal perpetrators of DoS attacks ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)

