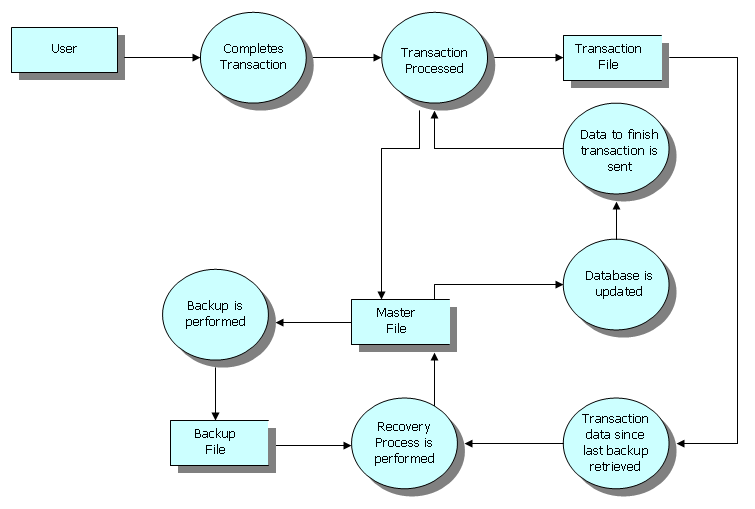
|
Transaction Processing Monitors
A transaction processing system (TPS) is a computer software, software system, or software/computer hardware, hardware combination, that supports transaction processing. History The first transaction processing system was Sabre (computer system), SABRE, made by IBM for American Airlines, which became operational in 1964. Designed to process up to 83,000 transactions a day, the system ran on two IBM 7090 computers. SABRE was migrated to IBM System/360 computers in 1972, and became an IBM product first as ''IBM Airline Control Program, Airline control Program (ACP)'' and later as ''Transaction Processing Facility, Transaction Processing Facility (TPF)''. In addition to airlines, TPF is used by large banks, credit card companies, and hotel chains. The Hewlett Packard Enterprise NonStop (server computers), NonStop system (formerly Tandem Computers, Tandem NonStop) is a hardware and software system designed for ''Online Transaction Processing (OLTP)'' introduced in 1976. The system pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Software
Software consists of computer programs that instruct the Execution (computing), execution of a computer. Software also includes design documents and specifications. The history of software is closely tied to the development of digital computers in the mid-20th century. Early programs were written in the machine language specific to the hardware. The introduction of high-level programming languages in 1958 allowed for more human-readable instructions, making software development easier and more portable across different computer architectures. Software in a programming language is run through a compiler or Interpreter (computing), interpreter to execution (computing), execute on the architecture's hardware. Over time, software has become complex, owing to developments in Computer network, networking, operating systems, and databases. Software can generally be categorized into two main types: # operating systems, which manage hardware resources and provide services for applicat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
DOS/360 And Successors
Disk Operating System/360, also DOS/360, or simply DOS, is the discontinued first member of a sequence of operating systems for IBM System/360, System/370 and later mainframes. It was announced by IBM on the last day of 1964, and it was first delivered in June 1966. In its time, DOS/360 was the most widely used operating system in the world. DOS versions BOS/360 The Basic Operating System (BOS) was an early version of DOS and TOS which could provide usable functionality on a system with as little as 8 KB of main storage and one 2311 disk drive. TOS/360 TOS/360 (Tape Operating System/360, not a DOS as such and not so called) was an IBM operating system for the System/360, used in the early days around 1965 to support the System/360 Model 30 and similar platforms. TOS, as per the "Tape" in the name, required a tape drive. It shared most of the code base and some manuals with IBM's DOS/360. TOS went through 14 releases, and was discontinued when disks such as the IBM 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
UNISYS
Unisys Corporation is a global technology solutions company founded in 1986 and headquartered in Blue Bell, Pennsylvania. The company provides cloud, AI, digital workplace, logistics, and enterprise computing services. History Founding Unisys’ history dates back to 1873 with E. Remington & Sons and the introduction of the first commercially viable typewriter to use the QWERTY keyboard layout. Over a hundred years later, the company became known as Unisys in 1986 through the merger of Mainframe computer, mainframe corporations Sperry Corporation, Sperry and Burroughs Corporation, Burroughs, with Burroughs buying Sperry for $4.8 billion. The new company's name was chosen from over 31,000 submissions in an internal competition when Christian Machen submitted the word "Unisys", which was composed of parts of the words "united", "information", and "systems". The merger was the largest in the computer industry at the time and made Unisys the second-largest computer company wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Burroughs MCP
The MCP (Master Control Program) is the operating system of the Burroughs B5000/B5500/B5700 and the B6500 and successors, including the Unisys Clearpath/MCP systems. MCP was originally written in 1961 in ESPOL (Executive Systems Problem Oriented Language). In the 1970s, MCP was converted to NEWP which was a better structured, more robust, and more secure form of ESPOL. The MCP was a leader in many areas, including: the first operating system to manage multiple processors, the first commercial implementation of virtual memory, and the first OS written exclusively in a high-level language. History In 1961, the MCP was the first OS written exclusively in a high-level language (HLL). The Burroughs Large System ( B5000 and successors) were unique in that they were designed with the expectation that all software, including system software, would be written in an HLL rather than in assembly language, which was a unique and innovative approach in 1961. Unlike IBM, which faced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Burroughs Corporation
The Burroughs Corporation was a major American manufacturer of business equipment. The company was founded in 1886 as the American Arithmometer Company by William Seward Burroughs I, William Seward Burroughs. The company's history paralleled many of the major developments in history of computing, computing. At its start, it produced mechanical adding machines, and later moved into programmable ledgers and then computers. It was one of the largest producers of mainframe computers in the world, also producing related equipment including typewriters and Printer (computing), printers. In the 1960s, the company introduced a range of mainframe computers that were well regarded for their performance running high level languages. These formed the core of the company's business into the 1970s. At that time the emergence of superminicomputers and the dominance of the IBM System/360 and 370 at the high end led to shrinking markets, and in 1986 the company purchased former competitor Sperry C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
UNIVAC 1100/2200 Series
The UNIVAC 1100/2200 series is a series of compatible 36-bit computer systems, beginning with the UNIVAC 1107 in 1962, initially made by Sperry Rand. The series continues to be supported today by Unisys Corporation as the ClearPath Dorado Series. The solid-state 1107 model number was in the same sequence as the earlier vacuum-tube computers, but the early computers were not compatible with their solid-state successors. Architecture Data formats * Fixed-point, either integer or fraction **Whole word – 36-bit (ones' complement) **Half word – two 18-bit fields per word (unsigned or ones' complement) **Third word – three 12-bit fields per word (ones' complement) **Quarter word – four 9-bit fields per word (unsigned) **Sixth word – six 6-bit fields per word (unsigned) * Floating point **Single precision – 36 bits: sign bit, 8-bit characteristic, 27-bit mantissa **Double precision – 72 bits: sign bit, 11-bit characteristic, 60-bit mantissa *Alphanumeric ** FIELDATA � ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Transaction Interface Package
Transaction or transactional may refer to: Commerce *Financial transaction, an agreement, communication, or movement carried out between a buyer and a seller to exchange an asset for payment *Debits and credits in a Double-entry bookkeeping system *Electronic funds transfer, the electronic exchange or transfer of money from one account to another * Real estate transaction, the process whereby rights in a unit of property is transferred between two or more parties * Transaction cost, a cost incurred in making an economic exchange * Transactional law, the practice of law concerning business and commerce Computing *Transaction processing, information processing that is divided into individual, indivisible operations * Database transaction, a unit of work performed within a database management system * Atomic transaction, a series of database operations such that either all occur, or nothing occurs Other uses *Transactions, the published proceedings of a learned society: ** * Transa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
UNIVAC
UNIVAC (Universal Automatic Computer) was a line of electronic digital stored-program computers starting with the products of the Eckert–Mauchly Computer Corporation. Later the name was applied to a division of the Remington Rand company and successor organizations. The BINAC, built by the Eckert–Mauchly Computer Corporation, was the first general-purpose computer for commercial use, but it was not a success. The last UNIVAC-badged computer was produced in 1986. History and structure J. Presper Eckert and John Mauchly built the ENIAC (Electronic Numerical Integrator and Computer) at the University of Pennsylvania's Moore School of Electrical Engineering between 1943 and 1946. A 1946 patent rights dispute with the university led Eckert and Mauchly to depart the Moore School to form the Electronic Control Company, later renamed Eckert–Mauchly Computer Corporation (EMCC), based in Philadelphia, Pennsylvania. That company first built a computer called BINAC (BINary Automat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Oracle Corporation
Oracle Corporation is an American Multinational corporation, multinational computer technology company headquartered in Austin, Texas. Co-founded in 1977 in Santa Clara, California, by Larry Ellison, who remains executive chairman, Oracle was the List of the largest software companies, third-largest software company in the world in 2020 by revenue and market capitalization. The company's 2023 ranking in the Forbes Global 2000, ''Forbes'' Global 2000 was 80. The company sells Database, database software, particularly Oracle Database, and cloud computing. Oracle's core application software is a suite of enterprise software products, such as enterprise resource planning (ERP) software, human capital management (HCM) software, customer relationship management (CRM) software, enterprise performance management (EPM) software, Customer Experience Commerce (CX Commerce) and supply chain management (SCM) software. History Larry Ellison, Bob Miner, and Ed Oates co-founded Oracle in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
AT&T Corporation
AT&T Corporation, an abbreviation for its former name, the American Telephone and Telegraph Company, was an American telecommunications company that provided voice, video, data, and Internet telecommunications and professional services to businesses, consumers, and government agencies. During the Bell System's long history, AT&T was at times the world's largest telecommunications company, the world's largest cable television operator, and a regulated monopoly. At its peak in the 1950s and 1960s, it employed one million people and its revenue ranged between US$3 billion in 1950 ($ in present-day terms) and $12 billion in 1966 ($ in present-day terms). In 2005, AT&T was acquired by " Baby Bell" and former subsidiary SBC Communications for more than $16 billion ($ in present-day terms). SBC then changed its name to AT&T Inc., with AT&T Corporation continuing to exist as a long-distance calling subsidiary until its dissolution on May 1, 2024. History Origins ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Tuxedo (software)
Tuxedo (Transactions for Unix, Extended for Distributed Operations) is a middleware platform used to manage distributed transaction processing in distributed computing environments. Tuxedo is a transaction processing system or transaction-oriented middleware, or enterprise application server for a variety of systems and programming languages. Developed by AT&T in the 1980s, it became a software product of Oracle Corporation in 2008 when they acquired BEA Systems. Tuxedo is now part of the Oracle Fusion Middleware. History From the beginning in 1983, AT&T designed Tuxedo for high availability and to provide extremely scalable applications to support applications requiring thousands of transactions per second on commonly available distributed systems. The original development targeted the creation and administration of operations support systems for the US telephone company that required online transaction processing (OLTP) capabilities. The Tuxedo concepts derived from the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
IBM TXSeries
IBM TXSeries for Multiplatforms is a distributed CICS (Customer Information Control System) online transaction processing (OLTP) environment for mixed language applications. TXSeries was introduced by IBM's Transarc subsidiary in 1997 and bundled CICS version 2.1.2 with Encina, MQSeries middleware, Lotus Domino Go web server, and other software. TXSeries is a transaction server available on AIX, Linux x86, Windows Server. It shares similar design principles and some functions with CICS on z/OS. End of 2006 saw a major release of TXSeries V6.1, simplifying the product by removing the DCE and Encina components and introducing a new graphical web-based administration console. IBM TXSeries V9.1 introduced features to create RESTful APIs to extend existing applications for mobile and cloud, and to extend traditional applications in Java Enterprise Edition (EE) and deploy them on IBM WebSphere Application Server. In July 2019, IBM announced IBM CICS TX on Cloud, a versi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |