|
Status Register
A status register, flag register, or condition code register (CCR) is a collection of status Flag (computing), flag bits for a Central processing unit, processor. Examples of such registers include FLAGS register (computing), FLAGS register in the x86 architecture, flags in the program status word (PSW) register in the IBM System/360 architecture through z/Architecture, and the application program status register (APSR) in the ARM Cortex-A architecture. The status register is a hardware register that contains information about the state of the Central processing unit, processor. Individual bits are implicitly or explicitly read and/or written by the machine code instructions executing on the processor. The status register lets an instruction take action contingent on the outcome of a previous instruction. Typically, flags in the status register are modified as effects of arithmetic and bit manipulation operations. For example, a Z bit may be set if the result of the operation is ze ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Flag (computing)
A bit field is a data structure that consists of one or more adjacent bits which have been allocated for specific purposes, so that any single bit or group of bits within the structure can be set or inspected. A bit field is most commonly used to represent integral types of known, fixed bit-width, such as single-bit Booleans. The meaning of the individual bits within the field is determined by the programmer; for example, the first bit in a bit field (located at the field's base address) is sometimes used to determine the state of a particular attribute associated with the bit field. Within CPUs and other logic devices, collections of bit fields called flags are commonly used to control or to indicate the outcome of particular operations. Processors have a status register that is composed of flags. For example if the result of an addition cannot be represented in the destination an arithmetic overflow is set. The flags can be used to decide subsequent operations, such as conditi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Least Significant Bit
In computing, bit numbering is the convention used to identify the bit positions in a binary number. Bit significance and indexing In computing, the least significant bit (LSB) is the bit position in a binary integer representing the binary 1s place of the integer. Similarly, the most significant bit (MSB) represents the highest-order place of the binary integer. The LSB is sometimes referred to as the ''low-order bit'' or ''right-most bit'', due to the convention in positional notation of writing less significant digits further to the right. The MSB is similarly referred to as the ''high-order bit'' or ''left-most bit''. In both cases, the LSB and MSB correlate directly to the least significant digit and most significant digit of a decimal integer. Bit indexing correlates to the positional notation of the value in base 2. For this reason, bit index is not affected by how the value is stored on the device, such as the value's byte order. Rather, it is a property of the numeri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protection Ring
In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by improving fault tolerance) and malicious behavior (by providing computer security). Computer operating systems provide different levels of access to resources. A protection ring is one of two or more hierarchical ''levels'' or ''layers'' of privilege within the architecture of a computer system. This is generally hardware-enforced by some CPU architectures that provide different CPU modes at the hardware or microcode level. Rings are arranged in a hierarchy from most privileged (most trusted, usually numbered zero) to least privileged (least trusted, usually with the highest ring number). Ring 0 is the level with the most privileges and allows direct interaction with the physical hardware such as certain CPU functionality and chips on the motherboard. Special call gates between rings are provided to allow an outer ring to acces ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt Handler
In computer systems programming, an interrupt handler, also known as an interrupt service routine or ISR, is a special block of code associated with a specific interrupt condition. Interrupt handlers are initiated by hardware interrupts, software interrupt instructions, or software exceptions, and are used for implementing device drivers or transitions between protected modes of operation, such as system calls. The traditional form of interrupt handler is the hardware interrupt handler. Hardware interrupts arise from electrical conditions or low-level protocols implemented in digital logic, are usually dispatched via a hard-coded table of interrupt vectors, asynchronously to the normal execution stream (as interrupt masking levels permit), often using a separate stack, and automatically entering into a different execution context (privilege level) for the duration of the interrupt handler's execution. In general, hardware interrupts and their handlers are used to handle high-pri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PDP-11 Architecture
The PDP-11 architecture is a CISC instruction set architecture (ISA) developed by Digital Equipment Corporation (DEC). It is implemented by central processing units (CPUs) and microprocessors used in PDP-11 minicomputers. It was in wide use during the 1970s, but was eventually overshadowed by the more powerful VAX-11 architecture in the 1980s. Memory Data formats Sixteen-bit words are stored little-endian (with least significant bytes first). Thirty-two-bit data—supported as extensions to the basic architecture, e.g., floating point in the ''FPU Instruction Set'', double-words in the ''Extended Instruction Set'' or long data in the ''Commercial Instruction Set''—are stored in more than one format, including an unusual middle-endian format sometimes referred to as "PDP-endian". Memory management The PDP-11's 16-bit addresses can address 64 KB. By the time the PDP-11 yielded to the VAX, 8-bit bytes and hexadecimal notation were becoming standard in the industry; however, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microchip Technology
Microchip Technology Inc. is a publicly-listed American corporation that manufactures microcontroller, mixed-signal, analog and Flash-IP integrated circuits. Its products include microcontrollers ( PIC, dsPIC, AVR and SAM), Serial EEPROM devices, Serial SRAM devices, embedded security devices, radio frequency (RF) devices, thermal, power and battery management analog devices, as well as linear, interface and wireless products. Its corporate headquarters is located in Chandler, Arizona. Its wafer fabs are located in Tempe, Arizona, Gresham, Oregon, and Colorado Springs, Colorado. Its assembly/test facilities are in Chachoengsao, Thailand, and Calamba and Cabuyao, Philippines. Sales for the fiscal year ending on March 31, 2019 were $5.35 billion. Microchip Technology offers support and reso ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interrupt Flag
The Interrupt flag (IF) is a flag bit in the CPU's FLAGS register, which determines whether or not the (CPU) will respond immediately to maskable hardware interrupts. If the flag is set to 1 maskable interrupts are enabled. If reset (set to 0) such interrupts will be disabled until interrupts are enabled. The Interrupt flag does not affect the handling of non-maskable interrupts (NMIs) or software interrupts generated by the INT instruction. Setting and clearing In a system using x86 architecture, the instructions CLI (Clear Interrupt) and STI (Set Interrupt). The POPF (Pop Flags) removes a word from the stack into the FLAGS register, which may result in the Interrupt flag being set or cleared based on the bit in the FLAGS register from the top of the stack. Privilege level In systems that support privileged mode, only privileged applications (usually the OS kernel) may modify the Interrupt flag. In an x86 system this only applies to protected mode code (Real mode code may a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
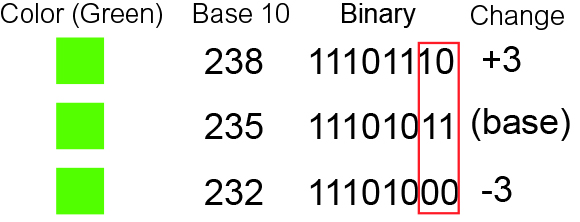
Parity Flag
In computer processors the parity flag indicates if the numbers of set bits is odd or even in the binary representation of the result of the last operation. It is normally a single bit in a processor status register. For example, assume a machine where a set parity flag indicates even parity. If the result of the last operation were 26 (11010 in binary), the parity flag would be 0 since the number of set bits is odd. Similarly, if the result were 10 (1010 in binary) then the parity flag would be 1. x86 processors In x86 processors, the parity flag reflects the parity only of the ''least significant byte'' of the result, and is set if the number of set bits of ones is even (put another way, the parity bit is set if the sum of the bits is even). According to 80386 Intel manual, the parity flag is changed in the x86 processor family by the following instructions: * All arithmetic instructions; * In conditional jumps, parity flag is used, where e.g. the JP instruction jumps to th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary-coded Decimal
In computing and electronic systems, binary-coded decimal (BCD) is a class of binary encodings of decimal numbers where each digit is represented by a fixed number of bits, usually four or eight. Sometimes, special bit patterns are used for a sign or other indications (e.g. error or overflow). In byte-oriented systems (i.e. most modern computers), the term ''unpacked'' BCD usually implies a full byte for each digit (often including a sign), whereas ''packed'' BCD typically encodes two digits within a single byte by taking advantage of the fact that four bits are enough to represent the range 0 to 9. The precise 4-bit encoding, however, may vary for technical reasons (e.g. Excess-3). The ten states representing a BCD digit are sometimes called '' tetrades'' (for the nibble typically needed to hold them is also known as a tetrade) while the unused, don't care-states are named , ''pseudo-decimals'' or ''pseudo-decimal digits''. BCD's main virtue, in comparison to binary posit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nibble
In computing, a nibble (occasionally nybble, nyble, or nybl to match the spelling of byte) is a four-bit aggregation, or half an octet. It is also known as half-byte or tetrade. In a networking or telecommunication context, the nibble is often called a semi-octet, quadbit, or quartet. A nibble has sixteen () possible values. A nibble can be represented by a single hexadecimal digit (–) and called a hex digit. A full byte (octet) is represented by two hexadecimal digits (–); therefore, it is common to display a byte of information as two nibbles. Sometimes the set of all 256-byte values is represented as a table, which gives easily readable hexadecimal codes for each value. Four-bit computer architectures use groups of four bits as their fundamental unit. Such architectures were used in early microprocessors, pocket calculators and pocket computers. They continue to be used in some microcontrollers. In this context, 4-bit groups were sometimes also called ''characters' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Half-carry Flag
A half-carry flag (also known as an auxiliary flag or decimal adjust flag) is a condition flag bit in the status register of many CPU families, such as the Intel 8080, Zilog Z80, the x86, and the Atmel AVR series, among others. It indicates when a carry or borrow has been generated out of the least significant four bits of the accumulator register following the execution of an arithmetic instruction. It is primarily used in decimal ( BCD) arithmetic instructions. Usage Normally, a processor that utilizes binary arithmetic (which includes almost all modern CPUs) will add two 8-bit byte values according to the rules of simple binary addition. For example, adding 25 and 48 produces 6D. However, for binary-coded decimal (BCD) values, where each 4-bit nibble represents a decimal digit, addition is more complicated. For example, adding the decimal value 25 and 48, which are encoded as the BCD values 25 and 48, the binary addition of the two values produces 6D. Since the lower nibble ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Two's Complement
Two's complement is a mathematical operation to reversibly convert a positive binary number into a negative binary number with equivalent (but negative) value, using the binary digit with the greatest place value (the leftmost bit in big- endian numbers, rightmost bit in little-endian numbers) to indicate whether the binary number is positive or negative (the sign). It is used in computer science as the most common method of representing signed (positive, negative, and zero) integers on computers, and more generally, fixed point binary values. When the most significant bit is a one, the number is signed as negative. . Two's complement is executed by 1) inverting (i.e. flipping) all bits, then 2) adding a place value of 1 to the inverted number. For example, say the number −6 is of interest. +6 in binary is 0110 (the leftmost most significant bit is needed for the sign; positive 6 is not 110 because it would be interpreted as -2). Step one is to flip all bits, yielding 1001. St ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |