|
Sentinel Value
In computer programming, a sentinel value (also referred to as a flag value, trip value, rogue value, signal value, or dummy data) is a special value in the context of an algorithm which uses its presence as a condition of termination, typically in a loop or recursive algorithm. The sentinel value is a form of in-band data that makes it possible to detect the end of the data when no out-of-band data (such as an explicit size indication) is provided. The value should be selected in such a way that it is guaranteed to be distinct from all legal data values since otherwise, the presence of such values would prematurely signal the end of the data (the semipredicate problem). A sentinel value is sometimes known as an " Elephant in Cairo", due to a joke where this is used as a physical sentinel. In safe languages, most sentinel values could be replaced with option types, which enforce explicit handling of the exceptional case. Examples Some examples of common sentinel values and t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Programming
Computer programming or coding is the composition of sequences of instructions, called computer program, programs, that computers can follow to perform tasks. It involves designing and implementing algorithms, step-by-step specifications of procedures, by writing source code, code in one or more programming languages. Programmers typically use high-level programming languages that are more easily intelligible to humans than machine code, which is directly executed by the central processing unit. Proficient programming usually requires expertise in several different subjects, including knowledge of the Domain (software engineering), application domain, details of programming languages and generic code library (computing), libraries, specialized algorithms, and Logic#Formal logic, formal logic. Auxiliary tasks accompanying and related to programming include Requirements analysis, analyzing requirements, Software testing, testing, debugging (investigating and fixing problems), imple ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
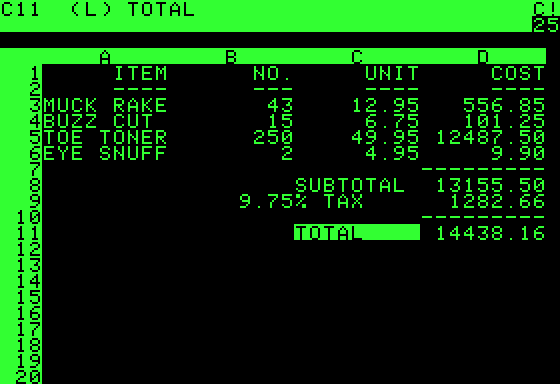
Inverse Video
Reverse video (or invert video or inverse video or reverse screen) is a computer display technique whereby the background and text color values are inverted. On older computers, displays were usually designed to display text on a black background by default. For emphasis, the color scheme was swapped to bright background with dark text. Nowadays the two tend to be switched, since most computers today default to white as a background color. The opposite of reverse video is known as ''true video''. Video is usually reversed by inverting the brightness values of the pixels of the involved region of the display. If there are 256 levels of brightness, encoded as 0 to 255, the 255 value becomes 0 and vice versa. A value of 1 becomes 254, 2 of 253, and so on: ''n'' is swapped for ''r'' - ''n'', for ''r'' levels of brightness. This is occasionally called a ones' complement. If the source image is of middle brightness, reverse video can be difficult to see, 127 becomes 128 for example, w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Time Formatting And Storage Bugs
In computer science, data type limitations and software bugs can cause errors in system time, time and date calculation or display. These are most commonly manifestations of arithmetic overflow, but can also be the result of other issues. The best-known consequence of this type is the Y2K problem, but many other milestone dates or times exist that have caused or will cause problems depending on various programming deficiencies. Year 1975 On 5 January 1975, the 12-bit field that had been used for dates in the TOPS-10 operating system for DEC PDP-10 computers overflowed, in a bug known as "DATE75". The field value was calculated by taking the number of years since 1964, multiplying by 12, adding the number of months since January, multiplying by 31, and adding the number of days since the start of the month; putting into this gives 4 January 1975, which is therefore the latest encodable date. The "DATE-75" patch pushed the last encodable date to 1 February 2052, ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Null Object Pattern
In object-oriented computer programming, a null object is an object with no referenced value or with defined neutral (''null'') behavior. The null object design pattern, which describes the uses of such objects and their behavior (or lack thereof), was first published as "Void Value" and later in the ''Pattern Languages of Program Design'' book series as "Null Object". Motivation In most object-oriented languages, such as Java or C#, references may be null. These references need to be checked to ensure they are not null before invoking any methods, because methods typically cannot be invoked on null references. The Objective-C language takes another approach to this problem and does nothing when sending a message to nil; if a return value is expected, nil (for objects), 0 (for numeric values), NO (for BOOL values), or a struct (for struct types) with all its members initialised to null/0/NO/zero-initialised struct is returned. Description Instead of using a null referen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Magic String
In computer programming, a magic string is an input that a programmer believes will never come externally and which activates otherwise hidden functionality. A user of this program would likely provide input that gives an expected response in most situations. However, if the user does in fact innocently (unintentionally) provide the pre-defined input, invoking the internal functionality, the program response is often quite unexpected to the user (thus appearing "magical"). Background Typically, the implementation of magic strings is due to time constraints. A developer must find a fast solution instead of delving more deeply into a problem and finding a better solution. For example, when testing a program that takes a user's personal details and verifies their credit card number, a developer may decide to add a magic string shortcut whereby entering the unlikely input of "***" as a credit card number would cause the program to automatically proceed as if the card were valid, wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Magic Number (programming)
In computer programming, a magic number is any of the following: * A unique value with unexplained meaning or multiple occurrences which could (preferably) be replaced with a named constant * A constant numerical or text value used to identify a file format or protocol ) * A distinctive unique value that is unlikely to be mistaken for other meanings (e.g., Universally Unique Identifiers) Unnamed numerical constants The term ''magic number'' or ''magic constant'' refers to the anti-pattern of using numbers directly in source code. This breaks one of the oldest rules of programming, dating back to the COBOL, FORTRAN and PL/1 manuals of the 1960s. In the following example that computes the price after tax, 1.05 is considered a magic number: price_tax = 1.05 * price The use of unnamed magic numbers in code obscures the developers' intent in choosing that number, increases opportunities for subtle errors, and makes it more difficult for the program to be adapted and extended ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Semipredicate Problem
In computer programming, a semipredicate problem occurs when a subroutine intended to return a useful value can fail, but the signalling of failure uses an otherwise valid return value. The problem is that the caller of the subroutine cannot tell what the result means in this case. Example The division operation yields a real number, but fails when the divisor is zero. If we were to write a function that performs division, we might choose to return 0 on this invalid input. However, if the dividend is 0, the result is 0 too. This means that there is no number we can return to uniquely signal attempted division by zero, since all real numbers are in the range of division. Practical implications Early programmers handled potentially exceptional cases such as division using a convention requiring the calling routine to verify the inputs before calling the division function. This had two problems: first, it greatly encumbered all code that performed division (a very common operat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Sentinel Node
In computer programming, a sentinel node is a specifically designated node used with linked lists and trees as a traversal path terminator. This type of node does not hold or reference any data managed by the data structure. Benefits Sentinels are used as an alternative over using NULL as the path terminator in order to get one or more of the following benefits: * Marginally increased speed of operations * Increased data structure robustness (arguably) Drawbacks * Marginally increased memory usage, especially when linked list is short. Examples Search in a linked list Below are two versions of a subroutine (implemented in the C programming language) for looking up a given search key in a singly linked list. The first one uses the sentinel value NULL, and the second one a (pointer to the) sentinel node Sentinel, as the end-of-list indicator. The declarations of the singly linked list data structure and the outcomes of both subroutines are the same. struct sll_node sll ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Canary Value
Canary originally referred to the Spanish island of Gran Canaria in the North Atlantic Ocean and the surrounding Canary Islands. It may also refer to: Animals Birds * Canaries, birds in the genera ''Serinus'' and ''Crithagra'' including, among others: ** Atlantic canary (''Serinus canaria''), a small wild bird *** Domestic canary, ''Serinus canaria domestica'', a small pet or aviary bird, also responsible for the "canary yellow" color term ** Yellow canary (''Crithagra flaviventris''), a small bird Fish * Canary damsel (''Similiparma lurida''), fish of the family Pomacentridae, found in the eastern Atlantic Ocean * Canary moray (''Gymnothorax bacalladoi''), an eel of the family Muraenidae * Canary rockfish (''Sebastes pinniger''), of the family Sebastidae, found in the northeast Pacific Ocean People * Canary Burton (born 1942), American keyboardist, composer and writer * Canary Conn (born 1949), American entertainer and author * Bill Canary (fl. 1994), Republican campaign consul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |