|
Security Management
Security management is the identification of an organization's assets i.e. including people, buildings, machines, systems and information assets, followed by the development, documentation, and implementation of policies and procedures for protecting assets. An organization uses such security management procedures for information classification, threat assessment, risk assessment, and risk analysis to identify threats, categorize assets, and rate system vulnerabilities. Loss prevention Loss prevention focuses on what one's critical assets are and how they are going to protect them. A key component to loss prevention is assessing the potential threats to the successful achievement of the goal. This must include the potential opportunities that further the object (why take the risk unless there's an upside?) Balance probability and impact determine and implement measures to minimize or eliminate those threats. Security management includes the theories, concepts, ideas, met ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Asset
In financial accounting, an asset is any resource owned or controlled by a business or an economic entity. It is anything (tangible or intangible) that can be used to produce positive economic value. Assets represent value of ownership that can be converted into cash (although cash itself is also considered an asset). The balance sheet of a firm records the monetaryThere are different methods of assessing the monetary value of the assets recorded on the Balance Sheet. In some cases, the ''Historical Cost'' is used; such that the value of the asset when it was bought in the past is used as the monetary value. In other instances, the present fair market value of the asset is used to determine the value shown on the balance sheet. value of the assets owned by that firm. It covers money and other valuables belonging to an individual or to a business. ''Total assets'' can also be called the ''balance sheet total''. Assets can be grouped into two major classes: Tangible property, tangib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Security Lighting
In the field of physical security, security lighting is lighting that intended to deter or detect intrusions or other criminal activity occurring on a property or site. It can also be used to increase a feeling of safety. Lighting is integral to crime prevention through environmental design. A 2019 study in New York City found that the provision of street lights, an important type of security lighting, resulted in a "36 percent reduction in nighttime outdoor index crimes." Planning considerations Security lighting to prevent intrusions may be counter-productive. Turning off lights halved the number of thefts and burglary in Övertorneå Sweden. ] This is also the minimum illumination level specified iTable H–2 Minimum Night Firing Criteria of 10 CFR 73 Appendix H for night firing. Pe10 CFR 73.46(b)(7)"-Tactical Response Team members, armed response personnel, and guards shall qualify and requalify, at least every 12 months, for day and night firing with assigned weapons in accor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
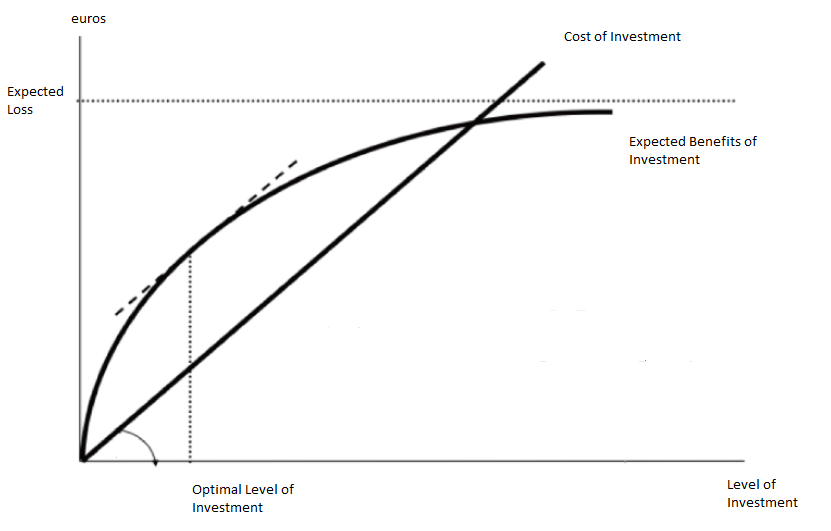
Gordon–Loeb Model
The Gordon–Loeb model is an economic model that analyzes the optimal level of investment in information security. The benefits of investing in cybersecurity stem from reducing the costs associated with cyber breaches. The Gordon-Loeb model provides a framework for determining how much to invest in cybersecurity, using a cost-benefit approach. The model includes the following key components: * Organizational data vulnerable to cyber-attacks, with vulnerability denoted by (), representing the probability of a breach occurring under current conditions. * The potential loss from a breach, represented by , which can be expressed in monetary terms. The expected loss is calculated as before additional cybersecurity investments. * Investment in cybersecurity, denoted as , reduces based on the effectiveness of the security measures, known as the security breach probability function. Gordon and Loeb demonstrated that the optimal level of security investment, , does not exceed 37% ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Security Policy
Security policy is a definition of what it means to ''be secure'' for a system, organization or other entity. For an organization, it addresses the constraints on behavior of its members as well as constraints imposed on adversaries by mechanisms such as doors, locks, keys, and walls. For systems, the security policy addresses constraints on functions and flow among them, constraints on access by external systems and adversaries including programs and access to data by people. Top-level policy If it is important to be secure, then it is important to be sure all of the security policy is enforced by mechanisms that are strong. There are organized methodologies and risk assessment strategies to assure completeness of security policies and assure that they are completely enforced. In complex systems, such as information systems, policies can be decomposed into sub-policies to facilitate the allocation of security mechanisms to enforce sub-policies. However, this practice has p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Security
Security is protection from, or resilience against, potential harm (or other unwanted coercion). Beneficiaries (technically referents) of security may be persons and social groups, objects and institutions, ecosystems, or any other entity or phenomenon vulnerable to unwanted change. Security mostly refers to protection from hostile forces, but it has a wide range of other senses: for example, as the absence of harm (e.g., freedom from want); as the presence of an essential good (e.g., food security); as resilience against potential damage or harm (e.g. secure foundations); as secrecy (e.g., a secure telephone line); as containment (e.g., a secure room or cell); and as a state of mind (e.g., emotional security). Security is both a feeling and a state of reality. One might feel secure when one is not actually so; or might feel insecure despite being safe. This distinction is usually not very clear to express in the English language. The term is also used to refer to acts ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Retail Loss Prevention
Retail loss prevention (also known as retail asset protection) is a set of practices employed by retail companies to preserve Profit (accounting), profit. Loss prevention is mainly found within the retail sector but also can be found within other business environments. Retail loss prevention is geared towards the elimination of preventable loss. Most companies take this traditional approach by either having their own in-house loss prevention team or using external security agencies. Shrink Items that are unaccounted for compared to what the inventory system believes the store should have are losses or "shrink". Shrink is caused by operational errors, internal theft, and external theft. Retail loss prevention is responsible for identifying these causes and following up with training, preventing, investigating, responding to and resolving them. According to the 2018 Federal National Retail Security Survey, the average Shrink % for US Retailers is 1.33%. Global Shrink Rates Avera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Physical Security
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment, and resources and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems that can include CCTV surveillance, security guards, protective barriers, locks, access control, perimeter intrusion detection, deterrent systems, fire protection, and other systems designed to protect persons and property. Overview Physical security systems for protected facilities can be intended to: * deter potential intruders (e.g. warning signs, security lighting); * detect intrusions, and identify, monitor and record intruders (e.g. security alarms, access control and CCTV systems); * trigger appropriate incident responses (e.g. by security guards and police); * delay or prevent hostile movements (e.g. door reinforcements, grilles); * protect the as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
ISO/IEC 27001
ISO/IEC 27001 is an information security standard. It specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS). Organizations with an ISMS that meet the standard's requirements can choose to have it certified by an accredited certification body following successful completion of an audit. There are also numerous recognized national variants of the standard. It was originally published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) in 2005, with revisions in 2013 and 2022. Rationale Most organizations have a number of information security controls. However, without an information security management system (ISMS), controls tend to be somewhat disorganized and disjointed, having been implemented often as point solutions to specific situations or simply as a matter of convention. Security controls in operation typ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Information Security Management System
Information security management (ISM) defines and manages controls that an organization needs to implement to ensure that it is sensibly protecting the confidentiality, availability, and integrity of assets from threats and vulnerabilities. The core of ISM includes information risk management, a process that involves the assessment of the risks an organization must deal with in the management and protection of assets, as well as the dissemination of the risks to all appropriate stakeholders. This requires proper asset identification and valuation steps, including evaluating the value of confidentiality, integrity, availability, and replacement of assets. As part of information security management, an organization may implement an information security management system and other best practices found in the ISO/IEC 27001, ISO/IEC 27002, and ISO/IEC 27035 standards on information security. Risk management and mitigation Managing information security in essence means managing and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
IT Risk Management
IT risk management is the application of risk management methods to information technology in order to manage IT risk. Various methodologies exist to manage IT risks, each involving specific processes and steps. An IT risk management system (ITRMS) is a component of a broader enterprise risk management (ERM) system. ITRMS are also integrated into broader information security management systems (ISMS). The continuous update and maintenance of an ISMS is in turn part of an organisation's systematic approach for identifying, assessing, and managing information security risks. Definitions The Certified Information Systems Auditor Review Manual 2006 by ISACA provides this definition of risk management: "''Risk management is the process of identifying vulnerabilities and threats to the information resources used by an organization in achieving business objectives, and deciding what countermeasures, if any, to take in reducing risk to an acceptable level, based on the value of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
IT Risk
It or IT may refer to: * It (pronoun), in English * Information technology Arts and media Film and television * ''It'' (1927 film), a film starring Clara Bow * '' It! The Terror from Beyond Space'', a 1958 science fiction film * ''It!'' (1967 film), a British horror film starring Roddy McDowell * ''It'' (1989 film), a Soviet comedy film directed by Sergei Ovcharov * ''It'' (miniseries), a 1990 television miniseries film based on Stephen King's novel * ''It'' (Phish video), a 2004 DVD set about the Phish festival * '' Incredible Tales'', simply known as ''I.T.'', a 2004 Singaporean horror anthology TV series * ''I.T.'' (film), a 2016 film starring Pierce Brosnan * ''It'' (2017 film), a film adaptation of Stephen King's novel **'' It Chapter Two'' (2019), the direct sequel to the 2017 film **'' It – Welcome to Derry,'' an upcoming prequel television series scheduled to be released in 2026 Characters * It, properly the Psammead, the title character of the 1902 novel '' Fiv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |