|
Safecracking
Safe-cracking is the process of opening a safe without either the combination or the key. Physical methods Different procedures may be used to crack a safe, depending on its construction. Different procedures are required to open different safes, so safe-crackers need to be aware of the differences. Lock manipulation Lock manipulation is a damage-free combination recovery method and a well known surreptitious bypass technique. Manipulation only requires fingers, eyes, and proper technique, though it is a skill that takes years to develop. While manipulation of combination locks is usually performed on Group 2 locks, many Group 1 locks are susceptible to manipulation. It involves the manipulation of the Lock (security device), lock in order to obtain the combination one number at a time. Manipulation procedures can vary, but they all rely on exploiting the presence of mechanical imperfections in the lock, unlocking the safe and recovering its combination, which can then be reus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Safecracking Brute Force
Safe-cracking is the process of opening a safe without either the combination or the key. Physical methods Different procedures may be used to crack a safe, depending on its construction. Different procedures are required to open different safes, so safe-crackers need to be aware of the differences. Lock manipulation Lock manipulation is a damage-free combination recovery method and a well known surreptitious bypass technique. Manipulation only requires fingers, eyes, and proper technique, though it is a skill that takes years to develop. While manipulation of combination locks is usually performed on Group 2 locks, many Group 1 locks are susceptible to manipulation. It involves the manipulation of the Lock (security device), lock in order to obtain the combination one number at a time. Manipulation procedures can vary, but they all rely on exploiting the presence of mechanical imperfections in the lock, unlocking the safe and recovering its combination, which can then be reus ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Force
In physics, a force is an influence that can change the motion of an object. A force can cause an object with mass to change its velocity (e.g. moving from a state of rest), i.e., to accelerate. Force can also be described intuitively as a push or a pull. A force has both magnitude and direction, making it a vector quantity. It is measured in the SI unit of newton (N). Force is represented by the symbol (formerly ). The original form of Newton's second law states that the net force acting upon an object is equal to the rate at which its momentum changes with time. If the mass of the object is constant, this law implies that the acceleration of an object is directly proportional to the net force acting on the object, is in the direction of the net force, and is inversely proportional to the mass of the object. Concepts related to force include: thrust, which increases the velocity of an object; drag, which decreases the velocity of an object; and torque, which produce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Liquid-crystal Display
A liquid-crystal display (LCD) is a flat-panel display A flat-panel display (FPD) is an electronic display used to display visual content such as text or images. It is present in consumer, medical, transportation, and industrial equipment. Flat-panel displays are thin, lightweight, provide better l ... or other Electro-optic modulator, electronically modulated optical device that uses the light-modulating properties of liquid crystals combined with polarizers. Liquid crystals do not emit light directly but instead use a backlight or reflector (photography), reflector to produce images in color or monochrome monitor, monochrome. LCDs are available to display arbitrary images (as in a general-purpose computer display) or fixed images with low information content, which can be displayed or hidden. For instance: preset words, digits, and seven-segment displays, as in a digital clock, are all good examples of devices with these displays. They use the same basic technology, exc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Light-emitting Diode
A light-emitting diode (LED) is a semiconductor device that emits light when current flows through it. Electrons in the semiconductor recombine with electron holes, releasing energy in the form of photons. The color of the light (corresponding to the energy of the photons) is determined by the energy required for electrons to cross the band gap of the semiconductor. White light is obtained by using multiple semiconductors or a layer of light-emitting phosphor on the semiconductor device. Appearing as practical electronic components in 1962, the earliest LEDs emitted low-intensity infrared (IR) light. Infrared LEDs are used in remote-control circuits, such as those used with a wide variety of consumer electronics. The first visible-light LEDs were of low intensity and limited to red. Early LEDs were often used as indicator lamps, replacing small incandescent bulbs, and in seven-segment displays. Later developments produced LEDs available in visible, ultraviolet (UV) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Credit Card Fraud
Credit card fraud is an inclusive term for fraud committed using a payment card, such as a credit card or debit card. The purpose may be to obtain goods or services or to make payment to another account, which is controlled by a criminal. The Payment Card Industry Data Security Standard (PCI DSS) is the data security standard created to help financial institutions process card payments securely and reduce card fraud. Credit card fraud can be authorised, where the genuine customer themselves processes payment to another account which is controlled by a criminal, or unauthorised, where the account holder does not provide authorisation for the payment to proceed and the transaction is carried out by a third party. In 2018, unauthorised financial fraud losses across payment cards and remote banking totalled £844.8 million in the United Kingdom. Whereas banks and card companies prevented £1.66 billion in unauthorised fraud in 2018. That is the equivalent to £2 in every £3 of atte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shoulder Surfing (computer Security)
In computer security, shoulder surfing is a type of social engineering technique used to obtain information such as personal identification numbers (PINs), passwords and other confidential data by looking over the victim's shoulder. Unauthorized users watch the keystrokes inputted on a device or listen to sensitive information being spoken, which is also known as eavesdropping. Methods and history This attack can be performed either at close range (by directly looking over the victim's shoulder) or from a longer range with, for example a pair of binoculars or similar hardware. Attackers do not need any technical skills in order to perform this method, and keen observation of victims' surroundings and the typing pattern is sufficient. In the early 1980s, shoulder surfing was practiced near public pay phones to steal calling card digits and make long-distance calls or sell them in the market for cheaper prices than the original purchaser paid. However, the advent of modern-day te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keypad
A keypad is a block or pad of buttons set with an arrangement of digits, symbols, or alphabetical letters. Pads mostly containing numbers and used with computers are numeric keypads. Keypads are found on devices which require mainly numeric input such as calculators, television remotes, push-button telephones, vending machines, ATMs, point of sale terminals, combination locks, safes, and digital door locks. Many devices follow the E.161 standard for their arrangement. Uses and functions A computer keyboard usually has a small numeric keypad on the side, in addition to the other number keys on the top, but with a calculator-style arrangement of buttons that allow more efficient entry of numerical data. This number pad (commonly abbreviated to ''numpad'') is usually positioned on the right side of the keyboard because most people are right-handed. Many laptop computers have special function keys that turn part of the alphabetical keyboard into a numerical keypad as there ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tempest (codename)
TEMPEST is a U.S. National Security Agency specification and a NATO certification referring to spying on information systems through leaking emanations, including unintentional radio or electrical signals, sounds, and vibrations. TEMPEST covers both methods to spy upon others and how to shield equipment against such spying. The protection efforts are also known as emission security (EMSEC), which is a subset of communications security (COMSEC). The NSA methods for spying on computer emissions are classified, but some of the protection standards have been released by either the NSA or the Department of Defense. Protecting equipment from spying is done with distance, shielding, filtering, and masking. The TEMPEST standards mandate elements such as equipment distance from walls, amount of shielding in buildings and equipment, and distance separating wires carrying classified vs. unclassified materials, filters on cables, and even distance and shielding between wires or equipment and b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electromagnetic Radiation
In physics, electromagnetic radiation (EMR) consists of waves of the electromagnetic field, electromagnetic (EM) field, which propagate through space and carry momentum and electromagnetic radiant energy. It includes radio waves, microwaves, infrared, Light, (visible) light, ultraviolet, X-rays, and gamma rays. All of these waves form part of the electromagnetic spectrum. Classical electromagnetism, Classically, electromagnetic radiation consists of electromagnetic waves, which are synchronized oscillations of electric field, electric and magnetic fields. Depending on the frequency of oscillation, different wavelengths of electromagnetic spectrum are produced. In a vacuum, electromagnetic waves travel at the speed of light, commonly denoted ''c''. In homogeneous, isotropic media, the oscillations of the two fields are perpendicular to each other and perpendicular to the direction of energy and wave propagation, forming a transverse wave. The position of an electromagnetic wave w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Power Analysis
Power analysis is a form of side channel attack in which the attacker studies the power consumption of a cryptographic hardware device. These attacks rely on basic physical properties of the device: semiconductor devices are governed by the laws of physics, which dictate that changes in voltages within the device require very small movements of electric charges (currents). By measuring those currents, it is possible to learn a small amount of information about the data being manipulated. Simple power analysis (SPA) involves visually interpreting power ''traces'', or graphs of electrical activity over time. Differential power analysis (DPA) is a more advanced form of power analysis, which can allow an attacker to compute the intermediate values within cryptographic computations through statistical analysis of data collected from multiple cryptographic operations. SPA and DPA were introduced to the open cryptography community in 1998 by Paul Kocher, Joshua Jaffe and Benjami ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
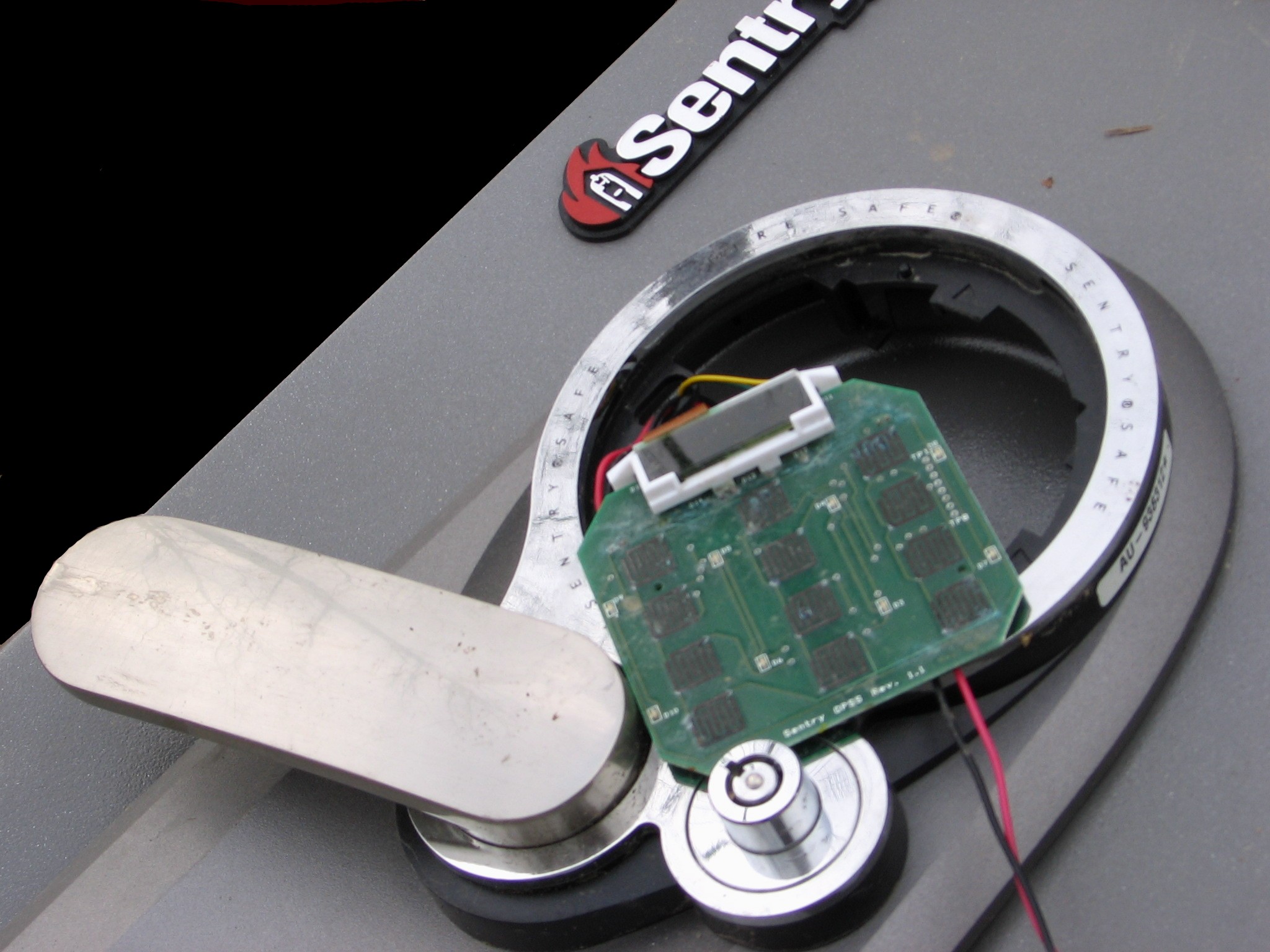
Electronic Lock
An electronic lock (or electric lock) is a locking device which operates by means of electric current. Electric locks are sometimes stand-alone with an electronic control assembly mounted directly to the lock. Electric locks may be connected to an access control system, the advantages of which include: key control, where keys can be added and removed without re-keying the lock cylinder; fine access control, where time and place are factors; and transaction logging, where activity is recorded. Electronic locks can also be remotely monitored and controlled, both to lock and to unlock. Operation Electric locks use magnets, solenoids, or motors to actuate the lock by either supplying or removing power. Operating the lock can be as simple as using a switch, for example an apartment intercom door release, or as complex as a biometric based access control system. There are two basic types of locks: "preventing mechanism" or operation mechanism. Types Electromagnetic lock The mos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Solenoid
upright=1.20, An illustration of a solenoid upright=1.20, Magnetic field created by a seven-loop solenoid (cross-sectional view) described using field lines A solenoid () is a type of electromagnet formed by a helix, helical coil of wire whose length is substantially greater than its diameter, which generates a controlled magnetic field. The coil can produce a uniform magnetic field in a volume of space when an electric current is passed through it. The term ''solenoid'' was coined in 1823 by André-Marie Ampère. The helical coil of a solenoid does not necessarily need to revolve around a straight-line axis; for example, William Sturgeon's electromagnet of 1824 consisted of a solenoid bent into a horseshoe shape (not unlike an arc spring). Solenoids provide magnetic focusing of electrons in vacuums, notably in television camera tubes such as vidicons and image orthicons. Electrons take helical paths within the magnetic field. These solenoids, focus coils, surround nearly th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |