|
Resource Exhaustion
Resource exhaustion attacks are computer security exploits that crash, hang, or otherwise interfere with the targeted program or system. They are a form of denial-of-service attack but are different from ''distributed'' denial-of-service attacks, which involve overwhelming a network host such as a web server with requests from many locations. Attack vectors Resource exhaustion attacks generally exploit a software bug or design deficiency. In software with manual memory management (most commonly written in C or C++), memory leaks are a very common bug exploited for resource exhaustion. Even if a garbage collected programming language is used, resource exhaustion attacks are possible if the program uses memory inefficiently and does not impose limits on the amount of state used when necessary. File descriptor leaks are another common vector. Most general-purpose programming languages require the programmer to explicitly close file descriptors, so even particularly high-level lang ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exploit (computer Security)
An exploit (from the English verb ''to exploit'', meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service (DoS or related DDoS) attack. In lay terms, some exploit is akin to a 'hack'. Classification There are several methods of classifying exploits. The most common is by how the exploit communicates to the vulnerable software. A ''remote exploit'' works over a network and exploits the security vulnerability without any prior access to the vulnerable system. A ''local exploit'' requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past tho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vector (malware)
In computer security, an attack vector is a specific path, method, or scenario that can be exploited to break into an IT system, thus compromising its security. The term was derived from the corresponding notion of vector in biology. An attack vector may be exploited manually, automatically, or through a combination of manual and automatic activity. Often, this is a multi-step process. For instance, malicious code (code that the user did not consent to being run and that performs actions the user would not consent to) often operates by being added to a harmless seeming document made available to an end user. When the unsuspecting end user opens the document, the malicious code in question (known as the payload) is executed and performs the abusive tasks it was programmed to execute, which may include things such as spreading itself further, opening up unauthorized access to the IT system, stealing or encrypting the user's documents, etc. In order to limit the chance of discovery ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ping Of Death
A ping of death is a type of attack on a computer system that involves sending a malformed or otherwise malicious ping to a computer. A correctly formed ping packet is typically 56 bytes in size, or 64 bytes when the Internet Control Message Protocol (ICMP) header is considered, and 84 bytes including Internet Protocol (IP) version 4 header. However, any IPv4 packet (including pings) may be as large as 65,535 bytes. Some computer systems were never designed to properly handle a ping packet larger than the maximum packet size because it violates the Internet Protocol. Like other large but well-formed packets, a ping of death is fragmented into groups of 8 octets before transmission. However, when the target computer reassembles the malformed packet, a buffer overflow can occur, causing a system crash and potentially allowing the injection of malicious code. In early implementations of TCP/IP, this bug is easy to exploit and can affect a wide varie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pentium F00F Bug
The Pentium F00F bug is a design flaw in the majority of Intel Pentium, Pentium MMX, and Pentium OverDrive processors (all in the P5 microarchitecture). Discovered in 1997, it can result in the processor ceasing to function until the computer is physically rebooted. The bug has been circumvented through operating system updates. The name is shorthand for F0 0F C7 C8, the hexadecimal encoding of one offending instruction. More formally, the bug is called the ''invalid operand with locked CMPXCHG8B instruction bug''. Description In the x86 architecture, the byte sequence F0 0F C7 C8 represents the instruction lock cmpxchg8b eax (locked compare and exchange of 8 bytes in register EAX). The bug also applies to opcodes ending in C9 through CF, which specify register operands other than EAX. The F0 0F C7 C8 instruction does not require any special privileges. This instruction encoding is invalid. The cmpxchg8b instruction compares the value in the EDX and EAX registers with an 8- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Local Area Network Denial
Land, also known as dry land, ground, or earth, is the solid terrestrial surface of the planet Earth that is not submerged by the ocean or other bodies of water. It makes up 29% of Earth's surface and includes the continents and various islands. Earth's land surface is almost entirely covered by regolith, a layer of rock, soil, and minerals that forms the outer part of the crust. Land plays important roles in Earth's climate system and is involved in the carbon cycle, nitrogen cycle, and water cycle. One-third of land is covered in trees, 15% is used for crops, and 10% is covered in permanent snow and glaciers. Land terrain varies greatly and consists of mountains, deserts, plains, plateaus, glaciers, and other landforms. In physical geology, the land is divided into two major categories: mountain ranges and relatively flat interiors called cratons. Both are formed over millions of years through plate tectonics. A major part of Earth's water cycle, streams shape the landscape ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Infinite Loop
In computer programming, an infinite loop (or endless loop) is a sequence of instructions that, as written, will continue endlessly, unless an external intervention occurs ("pull the plug"). It may be intentional. Overview This differs from: * "a type of computer program that runs the same instructions continuously until it is either stopped or interrupted." Consider the following pseudocode: how_many = 0 while is_there_more_data() do how_many = how_many + 1 end display "the number of items counted = " how_many ''The same instructions'' were run ''continuously until it was stopped or interrupted'' . . . by the ''FALSE'' returned at some point by the function ''is_there_more_data''. By contrast, the following loop will not end by itself: birds = 1 fish = 2 while birds + fish > 1 do birds = 3 - birds fish = 3 - fish end ''birds'' will alternate being 1 or 2, while ''fish'' will alternate being 2 or 1. The loop will not stop unless an external intervention occur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fork Bomb
In computing, a fork bomb (also called rabbit virus or wabbit) is a denial-of-service attack wherein a process continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation. History Around 1978, an early variant of a fork bomb called wabbit was reported to run on a System/360. It may have descended from a similar attack called RABBITS reported from 1969 on a Burroughs 5500 at the University of Washington. Implementation Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table. A basic implementation of a fork bomb is an infinite loop that repeatedly launches new copies of itself. In Unix-like operating systems, fork bombs are generally written to use the fork system call. As forked processes are also copies of the first program, once they resume execution from the next address at the frame pointer, they continue forking endlessly ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Billion Laughs
In computer security, a billion laughs attack is a type of denial-of-service (DoS) attack which is aimed at parsers of XML documents. It is also referred to as an XML bomb or as an exponential entity expansion attack. Details The example attack consists of defining 10 entities, each defined as consisting of 10 of the previous entity, with the document consisting of a single instance of the largest entity, which expands to one billion copies of the first entity. In the most frequently cited example, the first entity is the string "lol", hence the name "billion laughs". At the time this vulnerability was first reported, the computer memory used by a billion instances of the string "lol" would likely exceed that available to the process parsing the XML. While the original form of the attack was aimed specifically at XML parsers, the term may be applicable to similar subjects as well. The problem was first reported as early as 2002, but began to be widely addressed in 2008. Def ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Descriptor
In Unix and Unix-like computer operating systems, a file descriptor (FD, less frequently fildes) is a process-unique identifier (handle) for a file or other input/output resource, such as a pipe or network socket. File descriptors typically have non-negative integer values, with negative values being reserved to indicate "no value" or error conditions. File descriptors are a part of the POSIX API. Each Unix process (except perhaps daemons) should have three standard POSIX file descriptors, corresponding to the three standard streams: Overview In the traditional implementation of Unix, file descriptors index into a per-process maintained by the kernel, that in turn indexes into a system-wide table of files opened by all processes, called the . This table records the ''mode'' with which the file (or other resource) has been opened: for reading, writing, appending, and possibly other modes. It also indexes into a third table called the inode table that describes the actual u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
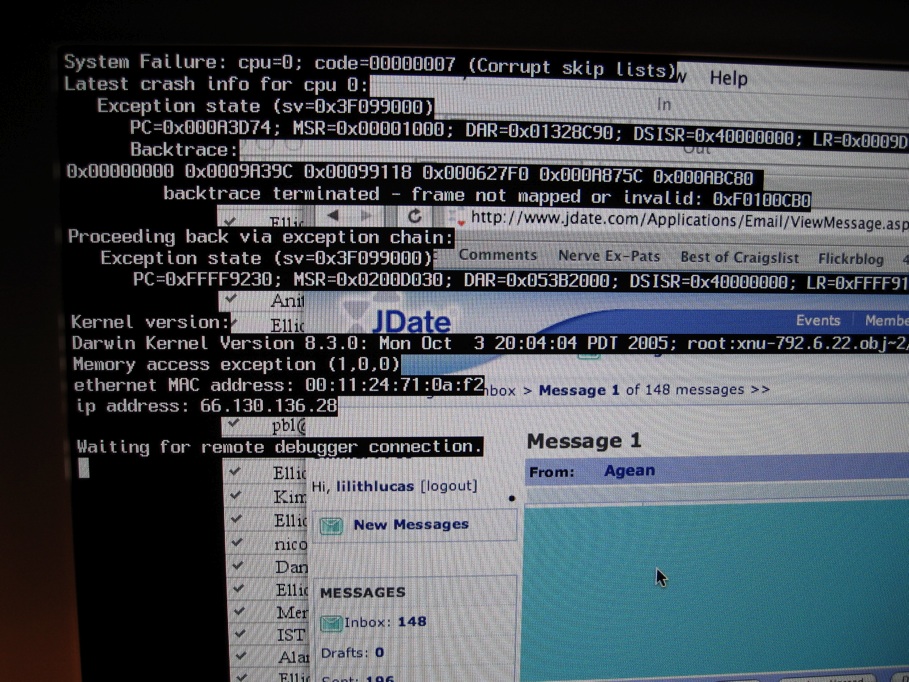
Crash (computing)
In computing, a crash, or system crash, occurs when a computer program such as a software application or an operating system stops functioning properly and exits. On some operating systems or individual applications, a crash reporting service will report the crash and any details relating to it (or give the user the option to do so), usually to the developer(s) of the application. If the program is a critical part of the operating system, the entire system may crash or hang, often resulting in a kernel panic or fatal system error. Most crashes are the result of a software bug. Typical causes include accessing invalid memory addresses, incorrect address values in the program counter, buffer overflow, overwriting a portion of the affected program code due to an earlier bug, executing invalid machine instructions (an illegal opcode), or triggering an unhandled exception. The original software bug that started this chain of events is typically considered to be the cause of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Garbage Collected
Garbage, trash, rubbish, or refuse is waste material that is discarded by humans, usually due to a perceived lack of utility. The term generally does not encompass bodily waste products, purely liquid or gaseous wastes, or toxic waste products. Garbage is commonly sorted and classified into kinds of material suitable for specific kinds of disposal. Terminology The word ''garbage'' originally meant chicken giblets and other entrails, as can be seen in the 15th century Boke of Kokery, which has a recipe for ''Garbage''. What constitutes garbage is highly subjective, with some individuals or societies tending to discard things that others find useful or restorable. The words garbage, refuse, rubbish, trash, and waste are generally treated as interchangeable when used to describe "substances or objects which the holder discards or intends or is required to discard". Some of these terms have historic distinctions that are no longer present. In the 1880s, material to be dispos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Leak
In computer science, a memory leak is a type of resource leak that occurs when a computer program incorrectly manages memory allocations in a way that Computer memory, memory which is no longer needed is not released. A memory leak may also happen when an object (computer science), object is stored in memory but cannot be accessed by the running code (i.e. unreachable memory). A memory leak has symptoms similar to a number of other problems and generally can only be diagnosed by a programmer with access to the program's source code. A related concept is the "space leak", which is when a program consumes excessive memory but does eventually release it. Because they can exhaust available system memory as an application runs, memory leaks are often the cause of or a contributing factor to software aging. Consequences A memory leak reduces the performance of the computer by reducing the amount of available memory. Eventually, in the worst case, too much of the available memory may b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |