|
Program Animation
Program animation or stepping refers to the debugging method of executing Source code, code one instruction or line at a time. The programmer may examine the State (computer science), state of the program, machine, and related data before and after execution of a particular line of code. This allows the programmer to evaluate the Side effect (computer science), effects of each statement or instruction in isolation, and thereby gain insight into the behavior (or misbehavior) of the executing program. Nearly all modern Integrated development environment, IDEs and debuggers support this mode of execution. History Instruction stepping or single cycle originally referred to the technique of stopping the processor Clock signal, clock and manually advancing it one cycle at a time. For this to be possible, three things are required: * A control that allows the clock to be stopped (e.g. a "Stop" button). * A second control that allows the stopped clock to be manually advanced by one cycle ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Debugging
In engineering, debugging is the process of finding the Root cause analysis, root cause, workarounds, and possible fixes for bug (engineering), bugs. For software, debugging tactics can involve interactive debugging, control flow analysis, Logfile, log file analysis, monitoring at the application monitoring, application or system monitoring, system level, memory dumps, and profiling (computer programming), profiling. Many Programming language, programming languages and Programming tool, software development tools also offer programs to aid in debugging, known as debuggers. Etymology The term ''bug'', in the sense of defect, dates back at least to 1878 when Thomas Edison wrote "little faults and difficulties" in his inventions as "Bugs". A popular story from the 1940s is from Admiral Grace Hopper. While she was working on a Harvard Mark II, Mark II computer at Harvard University, her associates discovered a moth stuck in a relay that impeded operation and wrote in a log book ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
CICS
IBM CICS (Customer Information Control System) is a family of mixed-language application servers that provide online business transaction management, transaction management and connectivity for applications on IBM mainframe systems under z/OS and z/VSE. CICS family products are designed as middleware and support rapid, high-volume online transaction processing. A CICS ''transaction'' is a unit of processing initiated by a single request that may affect one or more objects. This processing is usually interactive (screen-oriented), but background transactions are possible. CICS Transaction Server (CICS TS) sits at the head of the CICS family and provides services that extend or replace the functions of the operating system. These services can be more efficient than the generalized operating system services and also simpler for programmers to use, particularly with respect to communication with diverse terminal devices. Applications developed for CICS may be written in a variet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Code Coverage
In software engineering, code coverage, also called test coverage, is a percentage measure of the degree to which the source code of a program is executed when a particular test suite is run. A program with high code coverage has more of its source code executed during testing, which suggests it has a lower chance of containing undetected software bugs compared to a program with low code coverage. Many different metrics can be used to calculate test coverage. Some of the most basic are the percentage of program subroutines and the percentage of program statements called during execution of the test suite. Code coverage was among the first methods invented for systematic software testing. The first published reference was by Miller and Maloney in '' Communications of the ACM'', in 1963. Coverage criteria To measure what percentage of code has been executed by a test suite, one or more ''coverage criteria'' are used. These are usually defined as rules or requirements, whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Program Flow
In computer science, control flow (or flow of control) is the order in which individual Statement (computer science), statements, Instruction (computer science), instructions or function calls of an imperative programming, imperative computer program, program are Execution (computing), executed or evaluated. The emphasis on explicit control flow distinguishes an ''imperative programming'' language from a ''declarative programming'' language. Within an imperative programming language, a ''control flow statement'' is a statement that results in a choice being made as to which of two or more paths to follow. For Strict programming language, non-strict functional languages, functions and language constructs exist to achieve the same result, but they are usually not termed control flow statements. A set of statements is in turn generally structured as a Block (programming), block, which in addition to grouping, also defines a lexical scope. Interrupts and Signal (computing), signals ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
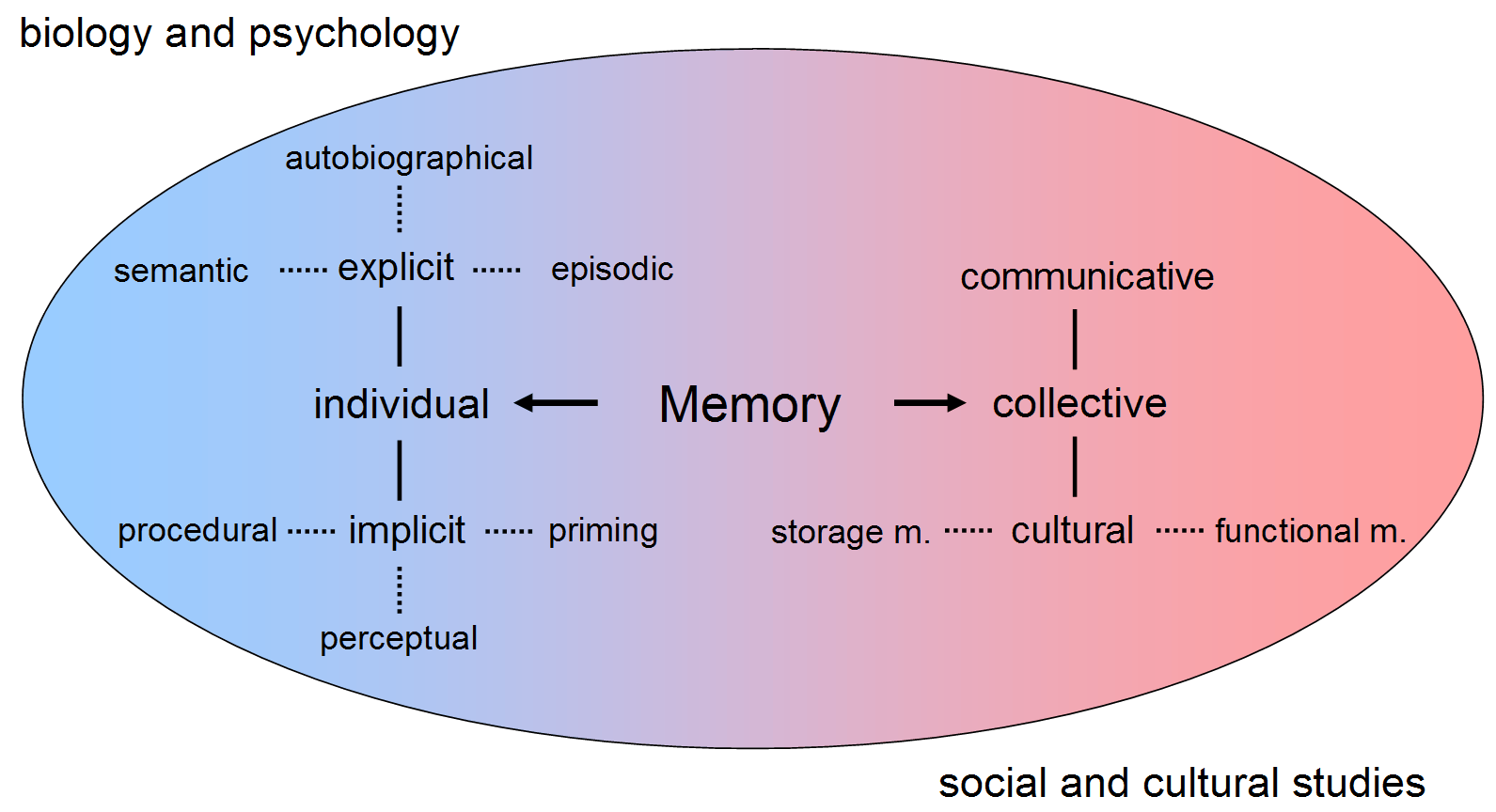
Memory
Memory is the faculty of the mind by which data or information is encoded, stored, and retrieved when needed. It is the retention of information over time for the purpose of influencing future action. If past events could not be remembered, it would be impossible for language, relationships, or personal identity to develop. Memory loss is usually described as forgetfulness or amnesia. Memory is often understood as an informational processing system with explicit and implicit functioning that is made up of a sensory processor, short-term (or working) memory, and long-term memory. This can be related to the neuron. The sensory processor allows information from the outside world to be sensed in the form of chemical and physical stimuli and attended to various levels of focus and intent. Working memory serves as an encoding and retrieval processor. Information in the form of stimuli is encoded in accordance with explicit or implicit functions by the working memory p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Tracing (software)
Tracing in software engineering refers to the process of capturing and recording information about the execution of a software program. This information is typically used by programmers for debugging purposes, and additionally, depending on the type and detail of information contained in a trace log, by experienced system administrators or technical-support personnel and by software monitoring tools to diagnose common problems with software. Tracing is a cross-cutting concern. There is not always a clear distinction between ''tracing'' and other forms of ''logging'', except that the term ''tracing'' is almost never applied to logging that is a functional requirement of a program (therefore excluding logging of data from an external source, such as data acquisition in a high-energy physics experiment, and write-ahead logging). Logs that record program usage (such as a server log) or operating-system events primarily of interest to a system administrator (see for example '' E ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Storage Violation
In computing a storage violation is a hardware or software fault that occurs when a task attempts to access an area of computer storage which it is not permitted to access. Types of storage violation Storage violation can, for instance, consist of reading from, writing to, or freeing storage not owned by the task. A common type of storage violation is known as a stack buffer overflow where a program attempts to exceed the limits set for its call stack. It can also refer to attempted modification of memory "owned" by another thread where there is incomplete (or no) memory protection. Avoidance of storage violations Storage violations can occur in transaction systems such as CICS in circumstances where it is possible to write to storage not owned by the transaction; such violations can be reduced by enabling features such as storage protection and transaction isolation. Detection of storage violations Storage violations can be difficult to detect as a program can often run for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Machine Code
In computer programming, machine code is computer code consisting of machine language instructions, which are used to control a computer's central processing unit (CPU). For conventional binary computers, machine code is the binaryOn nonbinary machines it is, e.g., a decimal representation. representation of a computer program that is actually read and interpreted by the computer. A program in machine code consists of a sequence of machine instructions (possibly interspersed with data). Each machine code instruction causes the CPU to perform a specific task. Examples of such tasks include: # Load a word from memory to a CPU register # Execute an arithmetic logic unit (ALU) operation on one or more registers or memory locations # Jump or skip to an instruction that is not the next one In general, each architecture family (e.g., x86, ARM) has its own instruction set architecture (ISA), and hence its own specific machine code language. There are exceptions, such as the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Instruction Set Simulator
An instruction set simulator (ISS) is a simulation model (abstract), model, usually coded in a high-level programming language, which mimics the behavior of a mainframe or microprocessor by "reading" instructions and maintaining internal variables which represent the processor's Processor register, registers. Instruction simulation is a methodology employed for one of several possible reasons: * To simulate the instruction set architecture (ISA) of a future processor to allow software development and test to proceed without waiting for the development and production of the hardware to finish. This is often known as "shift-left" or "pre-silicon support" in the hardware development field. A full system simulator or virtual platform for the future hardware typically includes one or more instruction set simulators. * To simulate the machine code of another hardware device or entire computer for upward Compatibility mode (software), compatibility. :: For example, the IBM 1401 was simu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Runtime Library
A runtime library is a library that provides access to the runtime environment that is available to a computer program tailored to the host platform. A runtime environment implements the execution model as required for a development environment such as a particular programming language. A runtime library may provide basic program facilities such as for memory management and exception handling. A runtime library is an artifact of the design of the toolchain used to build the program not inherently required by the host operating system or the programming language in which the program is written. The toolset is designed to abstract aspects of the host platform often to simplify tool development. The toolchain builds a program to depend on a runtime library and to use it while the program is running at program run-time. The runtime library may directly implement runtime behavior, but often it is a thin wrapper on top of operating system facilities. For example, some langua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Compiler
In computing, a compiler is a computer program that Translator (computing), translates computer code written in one programming language (the ''source'' language) into another language (the ''target'' language). The name "compiler" is primarily used for programs that translate source code from a high-level programming language to a lower level language, low-level programming language (e.g. assembly language, object code, or machine code) to create an executable program.Compilers: Principles, Techniques, and Tools by Alfred V. Aho, Ravi Sethi, Jeffrey D. Ullman - Second Edition, 2007 There are many different types of compilers which produce output in different useful forms. A ''cross-compiler'' produces code for a different Central processing unit, CPU or operating system than the one on which the cross-compiler itself runs. A ''bootstrap compiler'' is often a temporary compiler, used for compiling a more permanent or better optimised compiler for a language. Related software ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |