|
Pattern-of-life Analysis
Pattern-of-life analysis is a method of surveillance specifically used for documenting or understanding the habits of a particular subject or of the population in an area. This form of observation is generally done without the consent of the subject, with motives including but not limited to security, profit, scientific research, regular censuses, and traffic analysis. Pattern-of-life analysis is not limited to one medium and can encompass anything in an individual's (or system of individuals') life: from their internet browsing habits, to a record of instances of choices made in order to determine a statistical 'favorite'. This information can then potentially be used to predict future actions by the subject(s) being observed. Notable examples Esri's use of ArcGIS Esri is an international supplier of Geographic Information System (GIS) software, web GIS and geodatabase management applications. Esri uses the name ArcGIS to refer to its suite of GIS software products, which ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance Quevaal
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting heresy and heterodoxy may also carry out surveillance. Auditors ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MARINA
A marina (from Spanish language, Spanish , Portuguese language, Portuguese and Italian language, Italian : ''marina'', "coast" or "shore") is a Dock (maritime), dock or basin with moorings and supplies for yachts and small boats. A marina differs from a port in that a marina does not handle large passenger ships or cargo from freighters. The word ''marina'' may also refer to an inland wharf on a river or canal that is used exclusively by non-industrial pleasure craft such as canal narrowboats. Emplacement Marinas may be located along the banks of rivers connecting to lakes or seas and may be inland. They are also located on coastal harbors (natural or man made) or coastal lagoons, either as stand alone facilities or within a port complex. History In the 19th century, the few existing pleasure craft shared the same facilities as merchant ship, trading and fishing vessels. The marina appeared in the 20th century with the popularization of yachting. Facilities and services A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Traffic Analysis
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication, it can be performed even when the messages are encrypted. In general, the greater the number of messages observed, the greater information be inferred. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is also a concern in computer security. Traffic analysis tasks may be supported by dedicated computer software programs. Advanced traffic analysis techniques which may include various forms of social network analysis. Traffic analysis has historically been a vital technique in cryptanalysis, especially when the attempted crack depends on successfully seeding a known-plaintext attack, which often requires an inspired guess based on how specific the operational context might likely influence what an adversary communicates, which may be sufficient to establish a short crib. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunications Data Retention
Data retention defines the policies of persistent data and records management for meeting legal and business data archival requirements. Although sometimes interchangeable, it is not to be confused with the Data Protection Act 1998. The different data retention policies weigh legal and privacy concerns against economics and need-to-know concerns to determine the retention time, archival rules, data formats, and the permissible means of storage, access, and encryption. In the field of telecommunications, data retention generally refers to the storage of call detail records (CDRs) of telephony and internet traffic and transaction data ( IPDRs) by governments and commercial organisations. In the case of government data retention, the data that is stored is usually of telephone calls made and received, emails sent and received, and websites visited. Location data is also collected. The primary objective in government data retention is traffic analysis and mass surveillance. By ana ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
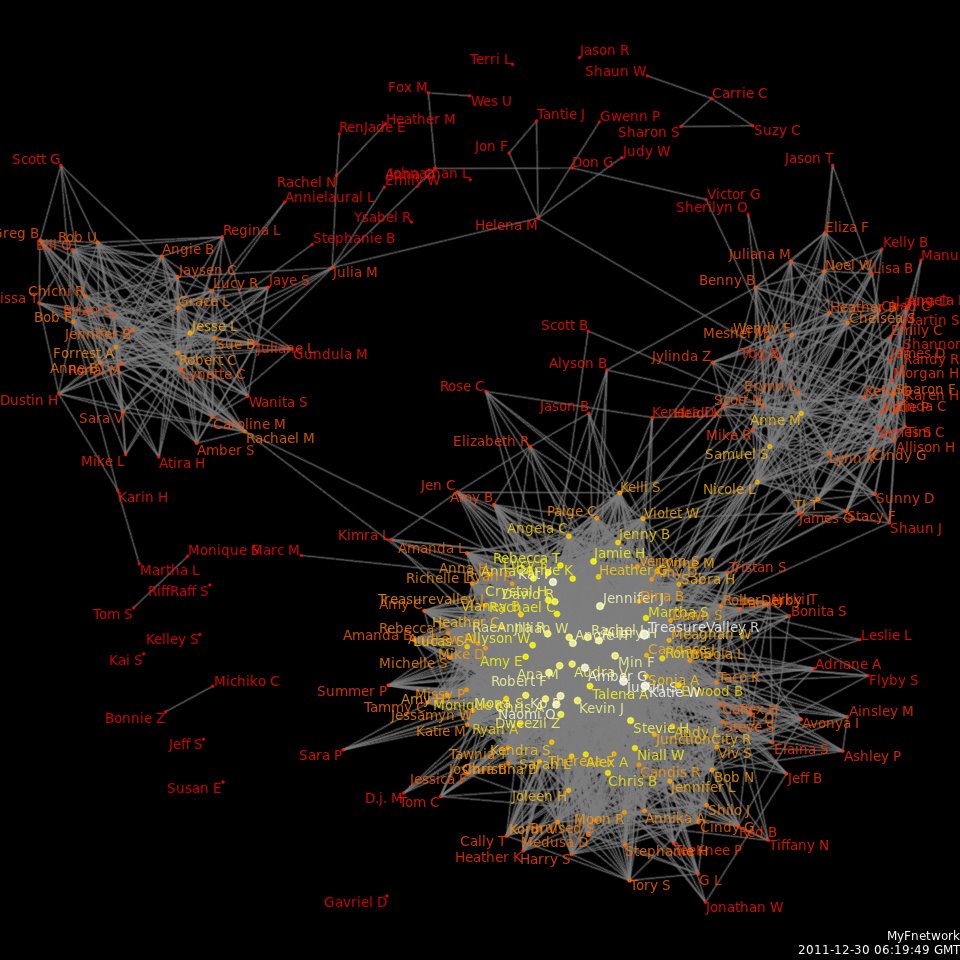
Social Network Analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) and the ''ties'', ''edges'', or ''links'' (relationships or interactions) that connect them. Examples of social structures commonly visualized through social network analysis include social media networks, memes spread, information circulation, friendship and acquaintance networks, business networks, knowledge networks, difficult working relationships, social networks, collaboration graphs, kinship, disease transmission, and sexual relationships. These networks are often visualized through '' sociograms'' in which nodes are represented as points and ties are represented as lines. These visualizations provide a means of qualitatively assessing networks by varying the visual representation of their nodes and edges to reflect attribute ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mass Surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations (either on behalf of governments or at their own initiative). Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance. Mass surveillance has often been cited as necessary to fight terrorism, prevent crime and social unrest, protect national security, and control the population. At the same time, mass surveillance has equally often been criticized for violating privacy rights, limiting civil and political rights and freedoms, and being ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Location-based Service
A location-based service (LBS) is a general term denoting software services which use geographic data and information to provide services or information to users. LBS can be used in a variety of contexts, such as health, indoor object search, entertainment, work, personal life, etc. Commonly used examples of location based services include navigation software, social networking services, location-based advertising, and tracking systems. LBS can also include mobile commerce when taking the form of coupons or advertising directed at customers based on their current location. LBS also includes personalized weather services and even location-based games. LBS is critical to many businesses as well as government organizations to drive real insight from data tied to a specific location where activities take place. The spatial patterns that location-related data and services can provide is one of its most powerful and useful aspects where location is a common denominator in all of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Privacy
Information privacy is the relationship between the collection and dissemination of data, technology, the public expectation of privacy, contextual information norms, and the legal and political issues surrounding them. It is also known as data privacy or data protection. Data privacy is challenging since attempts to use data while protecting an individual's privacy preferences and personally identifiable information. The fields of computer security, data security, and information security all design and use software, hardware, and human resources to address this issue. Authorities Laws Authorities by country Information types Various types of personal information often come under privacy concerns. Cable television This describes the ability to control what information one reveals about oneself over cable television, and who can access that information. For example, third parties can track IP TV programs someone has watched at any given time. "The addition of any infor ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases spans formal techniques and practical considerations, including data modeling, efficient data representation and storage, query languages, security and privacy of sensitive data, and distributed computing issues, including supporting concurrent access and fault tolerance. A database management system (DBMS) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS software additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an appli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wide-Area Motion Imagery (WAMI)
Wide-area motion imagery (WAMI) is an approach to surveillance, reconnaissance, and intelligence-gathering that employs specialized software and a powerful camera system—usually airborne, and for extended periods of time—to detect and track hundreds of people and vehicles moving out in the open, over a city-sized area, kilometers in diameter. For this reason, WAMI is sometimes referred to as wide-area persistent surveillance (WAPS) or wide-area airborne surveillance (WAAS). A WAMI sensor images the entirety of its coverage area in real time. It also records and archives that imagery in a database for real-time and forensic analysis. WAMI operators can use this live and recorded imagery to spot activity otherwise missed by standard video cameras with narrower fields of view, analyze these activities in context, distinguish threats from normal patterns of behavior, and perform the work of a larger force. Military and security personnel are the typical users of WAMI, employing the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAINWAY
MAINWAY is a database maintained by the United States' National Security Agency (NSA) containing metadata for hundreds of billions of telephone calls made through the largest telephone carriers in the United States, including AT&T, Verizon, and T-Mobile. The existence of this database and the NSA program that compiled it was unknown to the general public until ''USA Today'' broke the story on May 10, 2006. It is estimated that the database contains over 1.9 trillion call-detail records. The records include detailed call information (caller, receiver, date/time of call, length of call, etc.) for use in traffic analysis "And, by the way, I hate the term 'metadata.' What's wrong with 'traffic analysis,' which is what we've always called that sort of thing?" and social network analysis, "The data are used for 'social network analysis,' the official said, meaning to study how terrorist networks contact each other and how they are tied together." but do not include audio information ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Improvised Explosive Device
An improvised explosive device (IED) is a bomb constructed and deployed in ways other than in conventional military action. It may be constructed of conventional military explosives, such as an artillery shell, attached to a detonating mechanism. IEDs are commonly used as roadside bombs, or homemade bombs. IEDs are generally done in these terrorism operations or in asymmetric unconventional warfare by insurgent guerrillas or commando forces in a theatre of operations. In the Iraq War (2003–2011), insurgents used IEDs extensively against U.S.-led forces and, by the end of 2007, IEDs were responsible for approximately 63% of coalition deaths in Iraq. They were also used in Afghanistan by insurgent groups, and caused over 66% of coalition casualties in the 2001–2021 Afghanistan War. IEDs were also used frequently by the Liberation Tigers of Tamil Eelam (LTTE) in Sri Lanka during the Sri Lankan Civil War. Background An IED is a bomb fabricated in an improvised ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |