|
Object-capability Model
The object-capability model is a computer security model. A capability describes a transferable right to perform one (or more) operations on a given object. It can be obtained by the following combination: :* An unforgeable reference (in the sense of object references or protected pointers) that can be sent in messages. :* A message that specifies the operation to be performed. The security model relies on not being able to forge references. :* Objects can interact only by sending messages on references. :* A reference can be obtained by: ::# Initial conditions: In the initial state of the computational world being described, object A may already have a reference to object B. ::# Parenthood: If A creates B, at that moment A obtains the only reference to the newly created B. ::# Endowment: If A creates B, B is born with that subset of A's references with which A chose to endow it. ::# Introduction: If A has references to both B and C, A can send to B a message containing a refer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Computer Security Model
{{short description, Plan for specifying and enforcing security policies A computer security model is a scheme for specifying and enforcing security policies. A security model may be founded upon a formal model of access rights, a model of computation, a model of distributed computing, or no particular theoretical grounding at all. A computer security model is implemented through a computer security policy. For a more complete list of available articles on specific security models, see :Computer security models. Selected topics * Access control list (ACL) * Attribute-based access control (ABAC) * Bell–LaPadula model * Biba model * Brewer and Nash model * Capability-based security * Clark-Wilson model * Context-based access control (CBAC) * Graham-Denning model * Harrison-Ruzzo-Ullman (HRU) * High-water mark (computer security) * Lattice-based access control In computer security, lattice-based access control (LBAC) is a complex access control model based on the inte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Joe-E
Joe-E is a subset of the Java programming language intended to support programming according to object-capability discipline. The language is notable for being an early object-capability subset language. It has influenced later subset languages, such as ADsafe and Caja/Cajita, subsets of Javascript. It is also notable for allowing methods to be verified as functionally pure, based on their method signatures. Matthew Finifter, Adrian Mettler, Naveen Sastry, David Wagner; October 2008, Conference on Computer and Communications Security. The restrictions imposed by the Joe-E verifier include: * Classes may not have mutable static fields, because these create global state. * Catching out-of-memory exceptions is prohibited, because doing so allows non-deterministic execution. For t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Joule (programming Language)
Joule is a capability-secure massively- concurrent dataflow programming language, designed for building distributed applications. It is so concurrent that the order of statements within a block is irrelevant to the operation of the block. Statements are executed whenever possible, based on their inputs. Everything in Joule happens by sending messages. There is no control flow. Instead, the programmer describes the flow of data, making it a dataflow programming language. Joule development started in 1994 at ''Agorics'' in Palo Alto, California. It is considered the precursor to the E programming language. Language syntax Numerals consist of ASCII digits 0–9; identifiers are Unicode Unicode or ''The Unicode Standard'' or TUS is a character encoding standard maintained by the Unicode Consortium designed to support the use of text in all of the world's writing systems that can be digitized. Version 16.0 defines 154,998 Char ... sequences of digits, letters, and operator ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
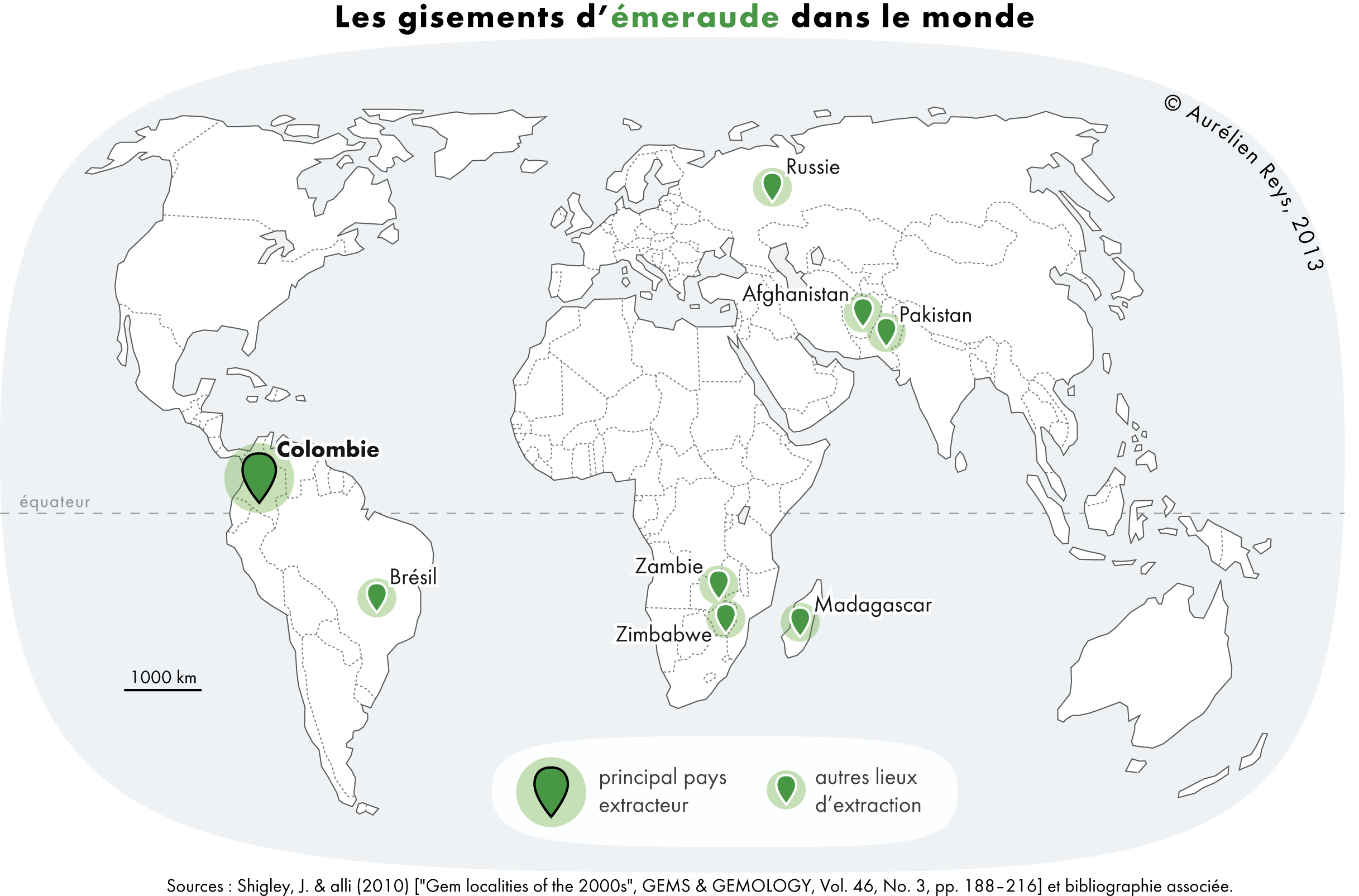
Emerald (programming Language)
Emerald is a gemstone and a variety of the mineral beryl (Be3Al2(SiO3)6) colored green by trace amounts of chromium or sometimes vanadium.Hurlbut, Cornelius S. Jr., and Kammerling, Robert C. (1991). ''Gemology'', John Wiley & Sons, New York, p. 203, . Beryl has a hardness of 7.5–8 on the Mohs scale. Most emeralds have many inclusions, so their toughness (resistance to breakage) is classified as generally poor. Emerald is a cyclosilicate. Etymology The word "emerald" is derived (via and ), from Vulgar Latin: ''esmaralda/esmaraldus'', a variant of Latin ''smaragdus'', which was via (smáragdos; "green gem"). The Greek word may have a Semitic, Sanskrit or Persian origin. According to ''Webster's Dictionary'' the term emerald was first used in the 14th century. Properties determining value Emeralds, like all colored gemstones, are graded using four basic parameters known as "the four ''C''s": ''color'', ''clarity,'' ''cut'' and ''carat weight''. Normally, in grading ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Fiasco (L4 Clone)
L4 is a family of second-generation microkernels, used to implement a variety of types of operating systems (OS), though mostly for Unix-like, ''Portable Operating System Interface'' (POSIX) compliant types. L4, like its predecessor microkernel L3, was created by German computer scientist Jochen Liedtke as a response to the poor performance of earlier microkernel-based OSes. Liedtke felt that a system designed from the start for high performance, rather than other goals, could produce a microkernel of practical use. His original implementation in hand-coded Intel i386-specific assembly language code in 1993 created attention by being 20 times faster than Mach. The follow-up publication two years later was considered so influential that it won the 2015 ACM SIGOPS Hall of Fame Award. Since its introduction, L4 has been developed to be cross-platform and to improve security, isolation, and robustness. There have been various re-implementations of the original L4 kernel application ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Integrity (operating System)
INTEGRITY and INTEGRITY-178B are real-time operating systems (RTOSes) produced and marketed by Green Hills Software. INTEGRITY INTEGRITY is POSIX-certified and intended for use in embedded systems of 32-bits or 64-bits. Supported computer architectures include variants of: ARM, Blackfin, ColdFire, MIPS, PowerPC, XScale, and x86. INTEGRITY is supported by popular SSL/TLS libraries such as wolfSSL. INTEGRITY-178B INTEGRITY-178B is the DO-178B–compliant version of INTEGRITY. It is used in several military jets such as the B-2, F-16, F-22, and F-35, and the commercial aircraft Airbus A380. Its kernel design guarantees bounded computing times by eliminating features such as dynamic memory allocation. The auditing and security engineering abilities have allowed it to obtain the Evaluation Assurance Level (EAL) 6 rating by the National Security Agency (NSA). The Target of Evaluation (TOE) Architecture in the Security Target for the evaluation excludes components such a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
EROS (microkernel)
Extremely Reliable Operating System (EROS) is an operating system developed starting in 1991 at the University of Pennsylvania, and then Johns Hopkins University, and The EROS Group, LLC. Features include automatic data and process persistence, some preliminary real-time support, and capability-based security. EROS is purely a research operating system, and was never deployed in real world use. , development stopped in favor of a successor system, CapROS. Key concepts The overriding goal of the EROS system (and its relatives) is to provide strong support at the operating system level for the efficient restructuring of critical applications into small communicating components. Each component can communicate with the others only through protected interfaces, and is isolated from the rest of the system. A ''protected interface'', in this context, is one that is enforced by the lowest level part of the operating system, the kernel. That is the only part of the system that can move info ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
KeyKOS
KeyKOS is a persistent, pure capability-based operating system for the IBM S/370 mainframe computers. It allows emulating the environments of VM, MVS, and Portable Operating System Interface (POSIX). It is a predecessor of the Extremely Reliable Operating System (EROS), and its successor operating system An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for ...s, CapROS, and Coyotos. KeyKOS is a nanokernel-based operating system. In the mid-1970s, development of KeyKOS began at Tymshare, Inc., under the name GNOSIS. In 1984, McDonnell Douglas (MD) bought Tymshare. A year later MD spun off Key Logic, which bought GNOSIS and renamed it ''KeyKOS''. References External links * , Norman Hardy GNOSIS: A Prototype Operating System for the 1990s a 1979 paper, Tymshare Inc. a 1988 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
POSIX
The Portable Operating System Interface (POSIX; ) is a family of standards specified by the IEEE Computer Society for maintaining compatibility between operating systems. POSIX defines application programming interfaces (APIs), along with command line shells and utility interfaces, for software compatibility (portability) with variants of Unix and other operating systems. POSIX is also a trademark of the IEEE. POSIX is intended to be used by both application and system developers. As of POSIX 2024, the standard is aligned with the C17 language standard. Name Originally, the name "POSIX" referred to IEEE Std 1003.1-1988, released in 1988. The family of POSIX standards is formally designated as IEEE 1003 and the ISO/IEC standard number is ISO/ IEC 9945. The standards emerged from a project that began in 1984 building on work from related activity in the ''/usr/group'' association. Richard Stallman suggested the name ''POSIX'' to the IEEE instead of the former ''IEEE-IX''. Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Design Pattern
A design pattern is the re-usable form of a solution to a design problem. The idea was introduced by the architect Christopher Alexander and has been adapted for various other disciplines, particularly software engineering. The " Gang of Four" book. Details An organized collection of design patterns that relate to a particular field is called a pattern language. This language gives a common terminology for discussing the situations designers are faced with. Documenting a pattern requires explaining why a particular situation causes problems, and how the components of the pattern relate to each other to give the solution. Christopher Alexander describes common design problems as arising from "conflicting forces"—such as the conflict between wanting a room to be sunny and wanting it not to overheat on summer afternoons. A pattern would not tell the designer how many windows to put in the room; instead, it would propose a set of values to guide the designer toward a deci ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |