|
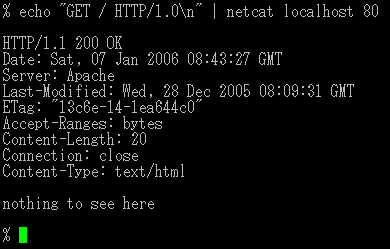
Netcat
netcat (often abbreviated to nc) is a computer networking utility for reading from and writing to network connections using TCP or UDP. The command is designed to be a dependable back-end that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of connection its user could need and has a number of built-in capabilities. Its list of features includes port scanning, transferring files, and port listening: as with any server, it can be used as a backdoor. Features The original netcat's features include: * Outbound or inbound connections, TCP or UDP, to or from any ports * Full DNS forward/reverse checking, with appropriate warnings * Ability to use any local source port * Ability to use any locally configured network source address * Built-in port-scanning capabilities, with randomization * Built-in loose source-routing capability * Can read c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Netcat
netcat (often abbreviated to nc) is a computer networking utility for reading from and writing to network connections using TCP or UDP. The command is designed to be a dependable back-end that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of connection its user could need and has a number of built-in capabilities. Its list of features includes port scanning, transferring files, and port listening: as with any server, it can be used as a backdoor. Features The original netcat's features include: * Outbound or inbound connections, TCP or UDP, to or from any ports * Full DNS forward/reverse checking, with appropriate warnings * Ability to use any local source port * Ability to use any locally configured network source address * Built-in port-scanning capabilities, with randomization * Built-in loose source-routing capability * Can read c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pipeline (Unix)
In Unix-like computer operating systems, a pipeline is a mechanism for inter-process communication using message passing. A pipeline is a set of processes chained together by their standard streams, so that the output text of each process (''stdout'') is passed directly as input (''stdin'') to the next one. The second process is started as the first process is still executing, and they are executed concurrently. The concept of pipelines was championed by Douglas McIlroy at Unix's ancestral home of Bell Labs, during the development of Unix, shaping its toolbox philosophy. It is named by analogy to a physical pipeline. A key feature of these pipelines is their "hiding of internals" (Ritchie & Thompson, 1974). This in turn allows for more clarity and simplicity in the system. This article is about anonymous pipes, where data written by one process is buffered by the operating system until it is read by the next process, and this uni-directional channel disappears when the processes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nmap
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym ''Fyodor Vaskovich''). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan. Nmap started as a Linux utility and was ported to other systems including Windows, macOS, and BSD. It is most popular on Linux, followed by Windows. Features Nmap features include: * Host discovery – Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open. * Port scanning – Enumerating the open ports on target hosts. * V ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Nmap
Nmap (Network Mapper) is a network scanner created by Gordon Lyon (also known by his pseudonym ''Fyodor Vaskovich''). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. These features are extensible by scripts that provide more advanced service detection, vulnerability detection, and other features. Nmap can adapt to network conditions including latency and congestion during a scan. Nmap started as a Linux utility and was ported to other systems including Windows, macOS, and BSD. It is most popular on Linux, followed by Windows. Features Nmap features include: * Host discovery – Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open. * Port scanning – Enumerating the open ports on target hosts. * V ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telnet
Telnet is an application protocol used on the Internet or local area network to provide a bidirectional interactive text-oriented communication facility using a virtual terminal connection. User data is interspersed in-band with Telnet control information in an 8-bit byte oriented data connection over the Transmission Control Protocol (TCP). Telnet was developed in 1969 beginning with , extended in , and standardized as Internet Engineering Task Force (IETF) Internet Standard STD 8, one of the first Internet standards. The name stands for " teletype network". Historically, Telnet provided access to a command-line interface on a remote host. However, because of serious security concerns when using Telnet over an open network such as the Internet, its use for this purpose has waned significantly in favor of SSH. The term ''telnet'' is also used to refer to the software that implements the client part of the protocol. Telnet client applications are available for virtually all c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hex Dump
In computing, a hex dump is a hexadecimal view (on screen or paper) of computer data, from memory or from a computer file or storage device. Looking at a hex dump of data is usually done in the context of either debugging, reverse engineering or digital forensics. In a hex dump, each byte (8 bits) is represented as a two-digit hexadecimal number. Hex dumps are commonly organized into rows of 8 or 16 bytes, sometimes separated by whitespaces. Some hex dumps have the hexadecimal memory address at the beginning. Some common names for this program function are hexdump, hd, od, xxd and simply dump or even D. Samples A sample text file: 0123456789ABCDEF /* ********************************************** */ Table with TABs (09) 1 2 3 3.14 6.28 9.42 as displayed by Unix hexdump: 0000000 30 31 32 33 34 35 36 37 38 39 41 42 43 44 45 46 0000010 0a 2f 2a 20 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 0000020 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a 2a * 0000040 2a 2a 20 2a 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireshark
Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues. Wireshark is cross-platform, using the Qt widget toolkit in current releases to implement its user interface, and using pcap to capture packets; it runs on Linux, macOS, BSD, Solaris, some other Unix-like operating systems, and Microsoft Windows. There is also a terminal-based (non-GUI) version called TShark. Wireshark, and the other programs distributed with it such as TShark, are free software, released under the terms of the GNU General Public License version 2 or any later version. Functionality Wireshark is very similar to tcpdump, but has a graphical front-end and integrated sorting and filtering options. Wireshark lets the user put network interface controllers into promiscuous mode (if supported by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Standard Streams
In computer programming, standard streams are interconnected input and output communication channels between a computer program and its environment when it begins execution. The three input/output (I/O) connections are called standard input (stdin), standard output (stdout) and standard error (stderr). Originally I/O happened via a physically connected system console (input via keyboard, output via monitor), but standard streams abstract this. When a command is executed via an interactive shell, the streams are typically connected to the text terminal on which the shell is running, but can be changed with redirection or a pipeline. More generally, a child process inherits the standard streams of its parent process. Application Users generally know standard streams as input and output channels that handle data coming from an input device, or that write data from the application. The data may be text with any encoding, or binary data. In many modern systems, the standard error str ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Redirection (computing)
In computing, redirection is a form of interprocess communication, and is a function common to most command-line interpreters, including the various Unix shells that can redirect standard streams to user-specified locations. In Unix-like operating systems, programs do redirection with the system call, or its less-flexible but higher-level stdio analogues, and . Redirecting standard input and standard output Redirection is usually implemented by placing certain characters between commands. Basic Typically, the syntax of these characters is as follows, using < to redirect input, and > to redirect output. command > file1 executes , placing the output in , as opposed to displaying it at the terminal, which is the usual destination for standard output. This will clobber any existing data in . Using command > file1. To read from a stream literal (an inline file, passed to the standard input), one can use a here document, using the << operator: $ tr a-z A-Z uno dos ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Named Pipe
In computing, a named pipe (also known as a FIFO for its behavior) is an extension to the traditional pipe concept on Unix and Unix-like systems, and is one of the methods of inter-process communication (IPC). The concept is also found in OS/2 and Microsoft Windows, although the semantics differ substantially. A traditional pipe is " unnamed" and lasts only as long as the process. A named pipe, however, can last as long as the system is up, beyond the life of the process. It can be deleted if no longer used. Usually a named pipe appears as a file, and generally processes attach to it for IPC. In Unix Instead of a conventional, unnamed, shell pipeline, a named pipeline makes use of the filesystem. It is explicitly created using mkfifo() or mknod(), and two separate processes can access the pipe by name — one process can open it as a reader, and the other as a writer. For example, one can create a pipe and set up gzip to compress things piped to it: mkfifo my_pipe gzip -9 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Port Scanning
A port scanner is an application designed to probe a server or host for open ports. Such an application may be used by administrators to verify security policies of their networks and by attackers to identify network services running on a host and exploit vulnerabilities. A port scan or portscan is a process that sends client requests to a range of server port addresses on a host, with the goal of finding an active port; this is not a nefarious process in and of itself. The majority of uses of a port scan are not attacks, but rather simple probes to determine services available on a remote machine. To portsweep is to scan multiple hosts for a specific listening port. The latter is typically used to search for a specific service, for example, an SQL-based computer worm may portsweep looking for hosts listening on TCP port 1433. TCP/IP basics The design and operation of the Internet is based on the Internet Protocol Suite, commonly also called TCP/IP. In this system, networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IPv4
Internet Protocol version 4 (IPv4) is the fourth version of the Internet Protocol (IP). It is one of the core protocols of standards-based internetworking methods in the Internet and other packet-switched networks. IPv4 was the first version deployed for production on SATNET in 1982 and on the ARPANET in January 1983. It is still used to route most Internet traffic today, even with the ongoing deployment of Internet Protocol version 6 (IPv6), its successor. IPv4 uses a 32-bit address space which provides 4,294,967,296 (232) unique addresses, but large blocks are reserved for special networking purposes. History Internet Protocol version 4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition of January 1980 (RFC 760). In March 1982, the US Department of Defense decided on the Internet Protocol Suite (TCP/IP) as the standard for all military computer networking. Purpose The Internet Protocol is the protocol that defines and enables internet ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |