|
Multiple Single-level
{{Unreferenced, date=December 2009 Multiple single-level or multi-security level (MSL) is a means to separate different levels of data by using separate computers or virtual machines for each level. It aims to give some of the benefits of multilevel security without needing special changes to the OS or applications, but at the cost of needing extra hardware. The drive to develop MLS operating systems was severely hampered by the dramatic fall in data processing costs in the early 1990s. Before the advent of desktop computing, users with classified processing requirements had to either spend a lot of money for a dedicated computer or use one that hosted an MLS operating system. Throughout the 1990s, however, many offices in the defense and intelligence communities took advantage of falling computing costs to deploy desktop systems classified to operate only at the highest classification level used in their organization. These desktop computers operated in security modes, system high ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multilevel Security
Multilevel security or multiple levels of security (MLS) is the application of a computer system to process information with incompatible classifications (i.e., at different security levels), permit access by users with different security clearances and needs-to-know, and prevent users from obtaining access to information for which they lack authorization. There are two contexts for the use of multilevel security. One context is to refer to a system that is adequate to protect itself from subversion and has robust mechanisms to separate information domains, that is, trustworthy. Another context is to refer to an application of a computer that will require the computer to be strong enough to protect itself from subversion, and have adequate mechanisms to separate information domains, that is, a system we must trust. This distinction is important because systems that need to be trusted are not necessarily trustworthy. Trusted operating systems An MLS operating environment often r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
University Of Idaho
The University of Idaho (U of I, or UIdaho) is a public land-grant research university in Moscow, Idaho, United States. Established in 1889 and opened three years later, it was the state's sole university for 71 years, until 1963. The university comprises ten undergraduate, graduate, and professional schools. It enrolls approximately 12,000 students across its campuses, with 11,000 on the Moscow campus. The university is classified among "Research 1: Very High Spending and Doctorate Production". Located on the rural Palouse, the university is represented in intercollegiate athletics by the Idaho Vandals, who compete in NCAA Division I, primarily in the Big Sky Conference. In addition to the main campus in Moscow, the U of I has branch campuses in Coeur d'Alene, Boise, and Idaho Falls; it also operates a research park in Post Falls, and dozens of extension offices statewide. History On January 30, 1889, Governor Edward Stevenson of the Idaho Territory signed th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Classified Information
Classified information is confidential material that a government deems to be sensitive information which must be protected from unauthorized disclosure that requires special handling and dissemination controls. Access is restricted by law or regulation to particular groups of individuals with the necessary security clearance with a need to know. A formal security clearance is required to view or handle classified material. The clearance process requires a satisfactory background investigation. Documents and other information must be properly marked "by the author" with one of several (hierarchical) levels of sensitivity—e.g. Confidential (C), Secret (S), and Top Secret (S). All classified documents require designation markings on the technical file which is usually located either on the cover sheet, header and footer of page. The choice of level is based on an impact assessment; governments have their own criteria, including how to determine the classification of an inf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Citrix Systems
Citrix Systems, Inc. is an American multinational cloud computing and virtualization technology company that provides server, application and desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies. Citrix claims that their products are used by over 400,000 clients worldwide, including 99% of the Fortune 100 and 98% of the Fortune 500. In 1989, Citrix was founded in Richardson, Texas, by Ed Iacobucci, who served as chairman until his departure in 2000. The company began by developing remote access products for Microsoft operating systems and licensing source code from Microsoft. Citrix has been partnered with Microsoft throughout its history. By the 1990s, Citrix had become an industry leader in thin client technology, enabling purpose-built devices to access remote servers and resources. The company launched its first initial public offering in 1995 and, with few competitors, experienced significant revenue increases between 1995 a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Corporation
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The early 1980s and home computers, rise of personal computers through software like Windows, and the company has since expanded to Internet services, cloud computing, video gaming and other fields. Microsoft is the List of the largest software companies, largest software maker, one of the Trillion-dollar company, most valuable public U.S. companies, and one of the List of most valuable brands, most valuable brands globally. Microsoft was founded by Bill Gates and Paul Allen to develop and sell BASIC interpreters for the Altair 8800. It rose to dominate the personal computer operating system market with MS-DOS in the mid-1980s, followed by Windows. During the 41 years from 1980 to 2021 Microsoft released 9 versions of MS-DOS with a median frequen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Commercial Off-the-shelf
Commercial-off-the-shelf or commercially available off-the-shelf (COTS) products are packaged or canned (ready-made) hardware or software, which are adapted aftermarket to the needs of the purchasing organization, rather than the commissioning of custom-made, or bespoke, solutions. A related term, Mil-COTS, refers to COTS products for use by the U.S. and Canadian militaries. In the context of the Federal government of the United States, U.S. government, the Federal Acquisition Regulation (FAR) has defined "COTS" as a formal term for commercial items, including services, available in the commercial marketplace that can be bought and used under government contract. For example, Microsoft is a COTS software provider. Goods and construction materials may qualify as COTS but bulk cargo does not. Services associated with the commercial items may also qualify as COTS, including installation services, training services, and cloud services. COTS purchases are alternatives to custom softwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
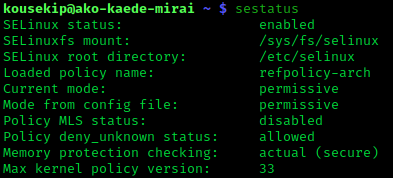
SELinux
Security-Enhanced Linux (SELinux) is a Linux kernel security module that provides a mechanism for supporting access control security policies, including mandatory access controls (MAC). SELinux is a set of kernel modifications and user-space tools that have been added to various Linux distributions. Its architecture strives to separate enforcement of security decisions from the security policy, and streamlines the amount of software involved with security policy enforcement. The key concepts underlying SELinux can be traced to several earlier projects by the United States National Security Agency (NSA). Overview The NSA Security-enhanced Linux Team describes NSA SELinux as a set of patches to the Linux kernel and utilities to provide a strong, flexible, mandatory access control (MAC) architecture into the major subsystems of the kernel. It provides an enhanced mechanism to enforce the separation of information based on confidentiality and integrity requirements, which allows th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NetTop
A mini PC (or miniature PC, nettop, or Smart Micro PC) is a small-sized, inexpensive, low-power, Legacy free PC, legacy-free desktop computer, desktop computer designed for basic tasks such as Web navigation, web browsing, accessing web application, web-based applications, document processing, and audio/video playback. The word ''nettop'' is a portmanteau of ''Telecommunications network, network'' and ''desktop computer, desktop''. It is the desktop counterpart of the netbook. Modern ( 2020) mini PCs or Small form factor (desktop and motherboard), small form factor PCs can be much more powerful, being equipped with high-end laptop components or mid-range desktop components. Compared with ordinary desktop computers, nettops are not only smaller and less expensive, but they also consume much less power. For example, CompuLab's fit-PC2 consumes no more than 8 watts of power whereas a typical desktop would easily consume more than 100 watts of power; consequently, nettops requi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Separation Kernel
A separation kernel is a type of security kernel used to simulate a distributed environment. The concept was introduced by John Rushby in a 1981 paper.John Rushby, "The Design and Verification of Secure Systems," Eighth ACM Symposium on Operating System Principles, pp. 12-21, Asilomar, CA, December 1981. (''ACM Operating Systems Review'', Vol. 15, No. 5). Rushby proposed the separation kernel as a solution to the difficulties and problems that had arisen in the development and verification of large, complex security kernels that were intended to "provide multilevel secure operation on general-purpose multi-user systems." According to Rushby, "the task of a separation kernel is to create an environment which is indistinguishable from that provided by a physically distributed system: it must appear as if each regime is a separate, isolated machine and that information can only flow from one machine to another along known external communication lines. One of the properties we must pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protection Profile
A Protection Profile (PP) is a document used as part of the certification process according to ISO/IEC 15408 and the Common Criteria (CC). As the generic form of a Security Target (ST), it is typically created by a user or user community and provides an implementation independent specification of information assurance security requirements. A PP is a combination of threats, security objectives, assumptions, security functional requirements (SFRs), security assurance requirements (SARs) and rationales. A PP specifies generic security evaluation criteria to substantiate vendors' claims of a given family of information system products. Among others, it typically specifies the Evaluation Assurance Level (EAL), a number 1 through 7, indicating the depth and rigor of the security evaluation, usually in the form of supporting documentation and testing, that a product meets the security requirements specified in the PP. The National Institute of Standards and Technology (NIST) and the N ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Common Criteria
The Common Criteria for Information Technology Security Evaluation (referred to as Common Criteria or CC) is an international standard (International Organization for Standardization, ISO/International Electrotechnical Commission, IEC 15408) for computer security certification. It is currently in version 3.1 revision 5. Common Criteria is a framework in which computer system users can ''specify'' their security ''functional'' and ''assurance'' requirements (SFRs and SARs, respectively) in a Security Target (ST), and may be taken from Protection Profiles (PPs). Vendors can then ''implement'' or make claims about the security attributes of their products, and testing laboratories can ''evaluate'' the products to determine if they actually meet the claims. In other words, Common Criteria provides assurance that the process of specification, implementation and evaluation of a computer security product has been conducted in a rigorous and standard and repeatable manner at a level that is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |