|
Log In
In computer security, logging in (or logging on, signing in, or signing on) is the process by which an individual gains access to a computer system or program by identifying and authenticating themselves. Typically, user credentials consist of a username and a password. These credentials themselves are sometimes referred to as ''a'' login. Modern secure systems often require a second factor, such as email or SMS confirmation for extra security. Social login allows a user to use an existing cell phone number, or user credentials from another email or social networking service to sign in or create an account on a new website. When access is no longer needed, the user can log out, log off, sign out or sign off. Procedure Logging in is usually used to enter a specific page, website, platform or application, which trespassers cannot see. Once the user is logged in, the login token may be used to track what actions the user has taken while connected to the site. Log ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command (computing)
In computing, a command is an instruction received via an external Interface (computing), interface that directs the behavior of a computer program. Commonly, commands are sent to a program via a command-line interface, a scripting language, script, a network protocol, or as an event triggered in a graphical user interface. Many commands support arguments to specify input and to modify default behavior. Terminology and syntax varies but there are notable common approaches. Typically, an option or a flag is a name (without Whitespace character, whitespace) with a prefix such as dash or Slash (punctuation), slash that modifies default behavior. An option might have a required value that follows it. Typically, flag refers to an option that does not have a following value. A parameter is an argument that specifies input to the command and its meaning is based on its position in the command line relative to other parameters; generally ignoring options. A parameter can specify anything ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Personal Computer
A personal computer, commonly referred to as PC or computer, is a computer designed for individual use. It is typically used for tasks such as Word processor, word processing, web browser, internet browsing, email, multimedia playback, and PC game, gaming. Personal computers are intended to be operated directly by an end user, rather than by a computer expert or technician. Unlike large, costly minicomputers and mainframes, time-sharing by many people at the same time is not used with personal computers. The term home computer has also been used, primarily in the late 1970s and 1980s. The advent of personal computers and the concurrent Digital Revolution have significantly affected the lives of people. Institutional or corporate computer owners in the 1960s had to write their own programs to do any useful work with computers. While personal computer users may develop their applications, usually these systems run commercial software, free-of-charge software ("freeware"), which i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Home Computers
Home computers were a class of microcomputers that entered the market in 1977 and became common during the 1980s. They were marketed to consumers as affordable and accessible computers that, for the first time, were intended for the use of a single, non-technical user. These computers were a distinct market segment that typically cost much less than business, scientific, or engineering-oriented computers of the time, such as those running CP/M or the IBM PC, and were generally less powerful in terms of memory and expandability. However, a home computer often had better graphics and sound than contemporary business computers. Their most common uses were word processing, playing video games, and programming. Home computers were usually sold already manufactured in stylish metal or plastic enclosures. However, some home computers also came as commercial electronic kits, like the Sinclair ZX80, which were both home and home-built computers since the purchaser could assemble the u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bulletin Board System
A bulletin board system (BBS), also called a computer bulletin board service (CBBS), is a computer server running list of BBS software, software that allows users to connect to the system using a terminal program. Once logged in, the user performs functions such as uploading and downloading software and data, reading news and bulletins, and exchanging messages with other users through public Internet forum, message boards and sometimes via direct synchronous conferencing, chatting. In the early 1980s, message networks such as FidoNet were developed to provide services such as M+NetMail, NetMail, which is similar to internet-based email. Many BBSes also offered BBS door, online games in which users could compete with each other. BBSes with multiple phone lines often provided chat rooms, allowing users to interact with each other. Bulletin board systems were in many ways a precursor to the modern form of the World Wide Web, social networking service, social networks, and other aspe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Time Sharing
In computing, time-sharing is the concurrent sharing of a computing resource among many tasks or users by giving each task or user a small slice of processing time. This quick switch between tasks or users gives the illusion of simultaneous execution. It enables multi-tasking by a single user or enables multiple-user sessions. Developed during the 1960s, its emergence as the prominent model of computing in the 1970s represented a major technological shift in the history of computing. By allowing many users to interact concurrently with a single computer, time-sharing dramatically lowered the cost of providing computing capability, made it possible for individuals and organizations to use a computer without owning one, and promoted the interactive use of computers and the development of new interactive applications. History Batch processing The earliest computers were extremely expensive devices, and very slow. Machines were typically dedicated to a particular set of t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM AIX 4 Login Prompt
International Business Machines Corporation (using the trademark IBM), nicknamed Big Blue, is an American multinational technology company headquartered in Armonk, New York, and present in over 175 countries. It is a publicly traded company and one of the 30 companies in the Dow Jones Industrial Average. IBM is the largest industrial research organization in the world, with 19 research facilities across a dozen countries; for 29 consecutive years, from 1993 to 2021, it held the record for most annual U.S. patents generated by a business. IBM was founded in 1911 as the Computing-Tabulating-Recording Company (CTR), a holding company of manufacturers of record-keeping and measuring systems. It was renamed "International Business Machines" in 1924 and soon became the leading manufacturer of punch-card tabulating systems. During the 1960s and 1970s, the IBM mainframe, exemplified by the System/360 and its successors, was the world's dominant computing platform, with the company p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Iris Recognition
Iris recognition is an automated method of biometrics, biometric identification that uses mathematical pattern-recognition techniques on video images of one or both of the iris (anatomy), irises of an individual's Human eye, eyes, whose complex patterns are unique, stable, and can be seen from some distance. The discriminating powers of all biometrics, biometric technologies depend on the amount of Entropy (information theory), entropy they are able to encode and use in matching. Iris recognition is exceptional in this regard, enabling the avoidance of "collisions" (False positives and false negatives, False Matches) even in cross-comparisons across massive populations. Its major limitation is that image acquisition from distances greater than a meter or two, or without cooperation, can be very difficult. However, the technology is in development and iris recognition can be accomplished from even up to 10 meters away or in a live camera feed. Retinal scanning is a different, ocul ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
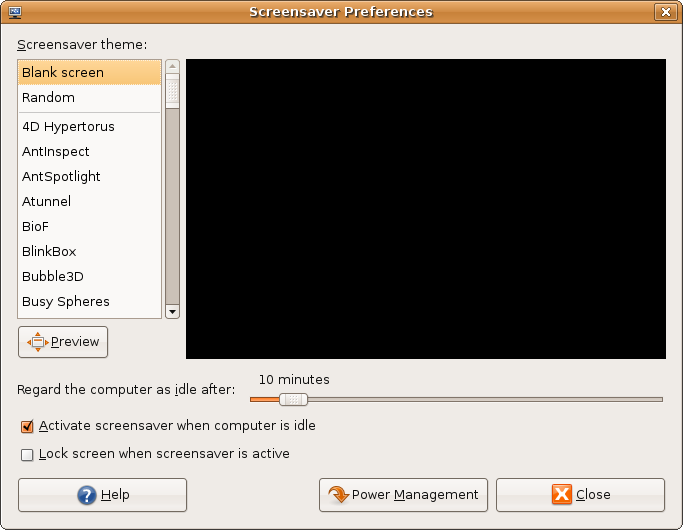
Screensaver
A screensaver (or screen saver) is a computer program that blanks the display screen or fills it with moving images or patterns when the computer has been idle for a designated time. The original purpose of screensavers was to prevent phosphor screen burn-in, burn-in on Cathode-ray tube, CRT or plasma display, plasma computer monitors (hence the name). Though most modern monitors are not susceptible to this issue (with the notable exception of OLED technology, which has individual pixels vulnerable to burnout), screensaver programs are still used for other purposes. Screensavers are often set up to offer a basic layer of computer security, security by requiring a password to re-access the device. Some screensaver programs also use otherwise-idle computer resources to do useful work, such as processing for volunteer computing projects. As well as computers, modern television operating systems, media players, and other digital entertainment systems may include optional screensavers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tampering With Evidence
Tampering with evidence, or evidence tampering, is an act in which a person alters, conceals, falsifies, or destroys evidence with the intent to interfere with an investigation (usually) by a law-enforcement, governmental, or regulatory authority. It is a criminal offense in many jurisdictions. Tampering with evidence is closely related to the legal issue of spoliation of evidence, which is usually the civil law or due process version of the same concept (but may itself be a crime). Tampering with evidence is also closely related to obstruction of justice and perverting the course of justice, and these two kinds of crimes are often charged together. The goal of tampering with evidence is usually to cover up a crime or with intent to injure the accused person. Spoliation Spoliation of evidence is the intentional, reckless, or negligent withholding, hiding, altering, fabricating, or destroying of evidence relevant to a legal proceeding. Historically, it has also sometimes been ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wi-Fi Hotspot
A hotspot is a physical location where people can obtain Internet access, typically using Wi-Fi technology, via a wireless local-area network (WLAN) using a router connected to an Internet service provider. Public hotspots may be created by a business for use by customers, such as coffee shops or hotels. Public hotspots are typically created from wireless access points configured to provide Internet access, controlled to some degree by the venue. In its simplest form, venues that have broadband Internet access can create public wireless access by configuring an access point (AP), in conjunction with a router to connect the AP to the Internet. A single wireless router combining these functions may suffice. A private hotspot, often called tethering, may be configured on a smartphone or tablet that has a network data plan, to allow Internet access to other devices via password, Bluetooth pairing, or through the moeex protocol over USB, or even when both the hotspot device a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Computer
A public computer (or public access computer) is any of various computers available in public areas. Some places where public computers may be available are libraries, schools, or dedicated facilities run by government. Public computers share similar hardware and software components to personal computers, however, the role and function of a public access computer is entirely different. A public access computer is used by many different untrusted individuals throughout the course of the day. The computer must be locked down and secure against both intentional and unintentional abuse. Users typically do not have authority to install software or change settings. A personal computer, in contrast, is typically used by a single responsible user, who can customize the machine's behavior to their preferences. Public access computers are often provided with tools such as a PC reservation system to regulate access. The world's first public access computer center was the Marin Computer Ce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |