|
Key (cryptography)
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key can be different sizes and varieties, but in all cases, the strength of the encryption relies on the security of the key being maintained. A key's security strength is dependent on its algorithm, the size of the key, the generation of the key, and the process of key exchange. Scope The key is what is used to encrypt data from plaintext to ciphertext. There are different methods for utilizing keys and encryption. Symmetric cryptography Symmetric cryptography refers to the practice of the same key being used for both encryption and decryption. Asymmetric cryptography Asymmetric cryptography has separate keys for encrypting and decrypting. These keys are known as the public and private keys, respectively. Purpose Since the key ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), adversarial behavior. More generally, cryptography is about constructing and analyzing Communication protocol, protocols that prevent third parties or the public from reading private messages. Modern cryptography exists at the intersection of the disciplines of mathematics, computer science, information security, electrical engineering, digital signal processing, physics, and others. Core concepts related to information security (confidentiality, data confidentiality, data integrity, authentication, and non-repudiation) are also central to cryptography. Practical applications of cryptography include electronic commerce, Smart card#EMV, chip-based payment cards, digital currencies, password, computer passwords, and military communications. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Institute Of Standards And Technology
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into Outline of physical science, physical science laboratory programs that include Nanotechnology, nanoscale science and technology, engineering, information technology, neutron research, material measurement, and physical measurement. From 1901 to 1988, the agency was named the National Bureau of Standards. History Background The Articles of Confederation, ratified by the colonies in 1781, provided: The United States in Congress assembled shall also have the sole and exclusive right and power of regulating the alloy and value of coin struck by their own authority, or by that of the respective states—fixing the standards of weights and measures throughout the United States. Article 1, section 8, of the Constitution of the United States, ratified i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Escrow
Key escrow (also known as a "fair" cryptosystem) is an arrangement in which the keys needed to decrypt encrypted data are held in escrow so that, under certain circumstances, an authorized third party may gain access to those keys. These third parties may include businesses, who may want access to employees' secure business-related communications, or governments, who may wish to be able to view the contents of encrypted communications (also known as ''exceptional access''). The technical problem is a largely structural one. Access to protected information must be provided ''only'' to the intended recipient and at least one third party. The third party should be permitted access only under carefully controlled conditions, for instance, a court order. Thus far, no system design has been shown to meet this requirement fully on a technical basis alone. All proposed systems also require correct functioning of some social linkage, for instance the process of request for access, exami ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Distribution Center
In cryptography, a key distribution center (KDC) is part of a cryptosystem intended to reduce the risks inherent in exchanging keys. KDCs often operate in systems within which some users may have permission to use certain services at some times and not at others. Security overview For instance, an administrator may have established a policy that only certain users may back up to tape. Many operating system An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for ...s can control access to the tape facility via a "system service". If that system service further restricts the tape drive to operate only on behalf of users who can submit a service-granting ticket when they wish to use it, there remains only the task of distributing such tickets to the appropriately permitted users. If the tick ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
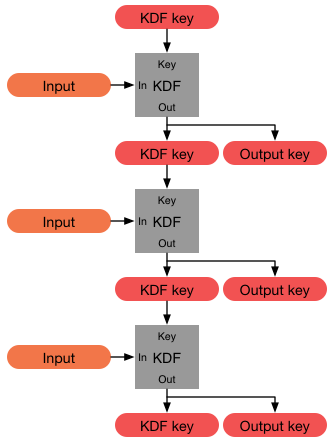
Key Derivation Function
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys or to obtain keys of a required format, such as converting a group element that is the result of a Diffie–Hellman key exchange into a symmetric key for use with AES. Keyed cryptographic hash functions are popular examples of pseudorandom functions used for key derivation. History The first deliberately slow (key stretching) password-based key derivation function was called "crypt" (or "crypt(3)" after its man page), and was invented by Robert Morris in 1978. It would encrypt a constant (zero), using the first 8 characters of the user's password as the key, by performing 25 iterations of a modified DES encryption algorithm (in which a 12-b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Authentication
/Config-authentication is used to solve the problem of authenticating the keys of a person (say "person A") that some other person ("person B") is talking to or trying to talk to. In other words, it is the process of assuring that the key of "person A", held by "person B", does in fact belong to "person A" and vice versa. This is usually done after the keys have been shared among the two sides over some secure channel. However, some algorithms share the keys at the time of authentication. The simplest solution for this kind of problem is for the two concerned users to communicate and exchange keys. However, for systems in which there are a large number of users or in which the users do not personally know each other (e.g., Internet shopping), this is not practical. There are various algorithms for both symmetric keys and asymmetric public key cryptography to solve this problem. Authentication using Shared Keys For key authentication using the traditional symmetric key cryptograph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HMAC
In cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. As with any MAC, it may be used to simultaneously verify both the data integrity and authenticity of a message. An HMAC is a type of keyed hash function that can also be used in a key derivation scheme or a key stretching scheme. HMAC can provide authentication using a shared secret instead of using digital signatures with asymmetric cryptography. It trades off the need for a complex public key infrastructure by delegating the key exchange to the communicating parties, who are responsible for establishing and using a trusted channel to agree on the key prior to communication. Details Any cryptographic hash function, such as SHA-2 or SHA-3, may be used in the calculation of an HMAC; the resulting MAC algori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Group Key
A group is a number of persons or things that are located, gathered, or classed together. Groups of people * Cultural group, a group whose members share the same cultural identity * Ethnic group, a group whose members share the same ethnic identity * Religious group (other), a group whose members share the same religious identity * Social group, a group whose members share the same social identity * Tribal group, a group whose members share the same tribal identity * Organization, an entity that has a collective goal and is linked to an external environment * Peer group, an entity of three or more people with similar age, ability, experience, and interest * Class (education), a group of people which attends a specific course or lesson at an educational institution Social science * In-group and out-group * Primary, secondary, and reference groups * Social group * Collectives Philosophy and religion * Khandha, a Buddhist concept of five material and mental facto ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EKMS
The Electronic Key Management System (EKMS) is a United States National Security Agency led program responsible for Communications Security ( COMSEC) key management, accounting, and distribution. Specifically, EKMS generates and distributes electronic key material for all NSA encryption systems whose keys are loaded using standard fill devices, and directs the distribution of NSA produced key material. Additionally, EKMS performs account registration, privilege management, ordering, distribution, and accounting to direct the management and distribution of physical COMSEC material for the services. The common EKMS components and standards facilitate interoperability and commonality among the armed services and civilian agencies. Key Management Infrastructure (KMI) replaces EKMS. Reasons for development The primary reason for the development of EKMS centers on the security and logistics problems that plagued the COMSEC Material Control System (CMCS),{{cite web, url=http://apps ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Diceware
Diceware is a method for creating passphrases, passwords, and other cryptographic variables using ordinary dice as a hardware random number generator. For each word in the passphrase, five rolls of a six-sided die are required. The numbers from 1 to 6 that come up in the rolls are assembled as a five-digit number, e.g. ''43146''. That number is then used to look up a word in a cryptographic word list. In the original Diceware list ''43146'' corresponds to ''munch''. By generating several words in sequence, a lengthy passphrase can thus be constructed randomly. A Diceware word list is any list of unique words, preferably ones the user will find easy to spell and to remember. The contents of the word list do not have to be protected or concealed in any way, as the security of a Diceware passphrase is in the number of words selected, and the number of words each selected word could be taken from. Lists have been compiled for several languages, including Basque, Bulgarian, Cat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Key Types
A cryptographic key is a string of data that is used to lock or unlock cryptographic functions, including authentication, authorization and encryption. Cryptographic keys are grouped into cryptographic key types according to the functions they perform. Description Consider a keyring that contains a variety of keys. These keys might be various shapes and sizes, but one thing is certain, each will generally serve a separate purpose. One key might be used to start an automobile, while another might be used to open a safe deposit box. The automobile key will not work to open the safe deposit box and vice versa. This analogy provides some insight on how cryptographic key types work. These keys are categorized in respect to how they are used and what properties they possess. A cryptographic key is categorized according to how it will be used and what properties it has. For example, a key might have one of the following properties: Symmetric, Public or Private. Keys may also be grouped ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Salt (cryptography)
In cryptography, a salt is random data fed as an additional input to a one-way function that hashes data Data ( , ) are a collection of discrete or continuous values that convey information, describing the quantity, quality, fact, statistics, other basic units of meaning, or simply sequences of symbols that may be further interpreted for ..., a password or passphrase. Salting helps defend against attacks that use precomputed tables (e.g. rainbow tables), by vastly growing the size of table needed for a successful attack. It also helps protect passwords that occur multiple times in a database, as a new salt is used for each password instance. Additionally, salting does not place any burden on users. Typically, a unique salt is randomly generated for each password. The salt and the password (or its version after key stretching) are concatenated and fed to a cryptographic hash function, and the output hash value is then stored with the salt in a database. Th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |