|
Gopher (protocol)
The Gopher protocol () is a communication protocol designed for distributing, searching, and retrieving documents in Internet Protocol networks. The design of the Gopher protocol and user interface is menu-driven, and presented an alternative to the World Wide Web in its early stages, but ultimately fell into disfavor, yielding to HTTP. The Gopher ecosystem is often regarded as the effective predecessor of the World Wide Web. Usage The Gopher protocol was invented by a team led by Mark P. McCahill at the University of Minnesota. It offers some features not natively supported by the Web and imposes a much stronger hierarchy on the documents it stores. Its text menu interface is well-suited to computing environments that rely heavily on remote text-oriented computer terminals, which were still common at the time of its creation in 1991, and the simplicity of its protocol facilitated a wide variety of client implementations. More recent Gopher revisions and graphical clients adde ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communication Protocol
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics (computer science), semantics and synchronization of communication and possible Error detection and correction, error recovery methods. Protocols may be implemented by Computer hardware, hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses pre-determined for that particular situation. The specified behavior is typically independent of how it is to be Implementation, implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GNU General Public License
The GNU General Public License (GNU GPL or simply GPL) is a series of widely used free software licenses that guarantee end users the Four Freedoms (Free software), four freedoms to run, study, share, and modify the software. The license was the first copyleft for general use and was originally written by the founder of the Free Software Foundation (FSF), Richard Stallman, for the GNU Project. The license grants the recipients of a computer program the rights of the Free Software Definition. These GPL series are all copyleft licenses, which means that any derivative work must be distributed under the same or equivalent license terms. It is more restrictive than the GNU Lesser General Public License, Lesser General Public License and even further distinct from the more widely used permissive software licenses BSD licenses, BSD, MIT License, MIT, and Apache License, Apache. Historically, the GPL license family has been one of the most popular software licenses in the free and open ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
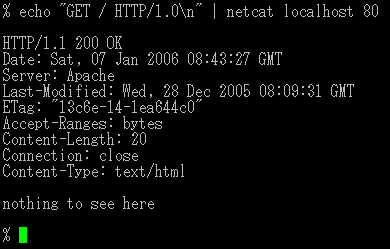
Netcat
netcat (often abbreviated to nc) is a computer networking utility for reading from and writing to network connections using TCP or UDP. The command is designed to be a dependable back-end that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of connection its user could need and has a number of built-in capabilities. Its list of features includes port scanning, transferring files, and port listening: as with any server, it can be used as a backdoor. Features The original netcat's features include: * Outbound or inbound connections, TCP or UDP, to or from any ports * Full DNS forward/reverse checking, with appropriate warnings * Ability to use any local source port * Ability to use any locally configured network source address * Built-in port-scanning capabilities, with randomization * Built-in loose source-routing capability * Can read c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Newline
Newline (frequently called line ending, end of line (EOL), next line (NEL) or line break) is a control character or sequence of control characters in character encoding specifications such as ASCII, EBCDIC, Unicode, etc. This character, or a sequence of characters, is used to signify the end of a line of text and the start of a new one. History In the mid-1800s, long before the advent of teleprinters and teletype machines, Morse code operators or telegraphists invented and used Morse code prosigns to encode white space text formatting in formal written text messages. In particular the Morse prosign (mnemonic reak ext) represented by the concatenation of literal textual Morse codes "B" and "T" characters sent without the normal inter-character spacing is used in Morse code to encode and indicate a ''new line'' or ''new section'' in a formal text message. Later, in the age of modern teleprinters, standardized character set control codes were developed to aid in white space ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Well-known Ports (computing)
This is a list of TCP and UDP port numbers used by protocols for operation of network applications. The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) only need one port for duplex, bidirectional traffic. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses. However, many unofficial uses of both well-known and registered port numbers occur in practice. Similarly, many of the official assignments refer to protocols that were never or are no longer in common use. This article lists port numbers and their associated protocols that have experienced significant uptake. Table legend Well-known ports The port numbers in the range from 0 to 1023 (0 to 210 − 1) are the ''well-known ports'' or ''system ports''. They are used by system processes that provide w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmission Control Protocol
The Transmission Control Protocol (TCP) is one of the main protocols of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP. TCP provides reliable, ordered, and error-checked delivery of a stream of octets (bytes) between applications running on hosts communicating via an IP network. Major internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP, which is part of the Transport Layer of the TCP/IP suite. SSL/TLS often runs on top of TCP. TCP is connection-oriented, and a connection between client and server is established before data can be sent. The server must be listening (passive open) for connection requests from clients before a connection is established. Three-way handshake (active open), retransmission, and error detection adds to reliability but lengthens latency. Applica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Assigned Numbers Authority
The Internet Assigned Numbers Authority (IANA) is a standards organization that oversees global IP address allocation, autonomous system number allocation, root zone management in the Domain Name System (DNS), media types, and other Internet Protocol-related symbols and Internet numbers. Currently it is a function of ICANN, a nonprofit private American corporation established in 1998 primarily for this purpose under a United States Department of Commerce contract. ICANN managed IANA directly from 1998 through 2016, when it was transferred to Public Technical Identifiers (PTI), an affiliate of ICANN that operates IANA today. Before it, IANA was administered principally by Jon Postel at the Information Sciences Institute (ISI) of the University of Southern California (USC) situated at Marina Del Rey (Los Angeles), under a contract USC/ISI had with the United States Department of Defense. In addition, five regional Internet registries delegate number resources to their custo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CD-ROM
A CD-ROM (, compact disc read-only memory) is a type of read-only memory consisting of a pre-pressed optical compact disc that contains data. Computers can read—but not write or erase—CD-ROMs. Some CDs, called enhanced CDs, hold both computer data and audio with the latter capable of being played on a CD player, while data (such as software or digital video) is only usable on a computer (such as ISO 9660 format PC CD-ROMs). During the 1990s and early 2000s, CD-ROMs were popularly used to distribute software and data for computers and fifth generation video game consoles. DVD started to replace it in these roles starting in the early 2000s. History The earliest theoretical work on optical disc storage was done by independent researchers in the United States including David Paul Gregg (1958) and James Russel (1965–1975). In particular, Gregg's patents were used as the basis of the LaserDisc specification that was co-developed between MCA and Philips after MCA purchased ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Filesystem In Userspace
Filesystem in Userspace (FUSE) is a software interface for Unix and Unix-like computer operating systems that lets non-privileged users create their own file systems without editing kernel code. This is achieved by running file system code in user space while the FUSE module provides only a bridge to the actual kernel interfaces. FUSE is available for Linux, FreeBSD, OpenBSD, NetBSD (as puffs), OpenSolaris, Minix 3, macOS, and Windows. FUSE is free software originally released under the terms of the GNU General Public License and the GNU Lesser General Public License. History The FUSE system was originally part of ''AVFS'' (''A Virtual Filesystem''), a filesystem implementation heavily influenced by the translator concept of the GNU Hurd. It superseded Linux Userland Filesystem, and provided a translational interface using in libfuse1. FUSE was originally released under the terms of the GNU General Public License and the GNU Lesser General Public License, later also reimple ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed File System
A clustered file system is a file system which is shared by being simultaneously mounted on multiple servers. There are several approaches to clustering, most of which do not employ a clustered file system (only direct attached storage for each node). Clustered file systems can provide features like location-independent addressing and redundancy which improve reliability or reduce the complexity of the other parts of the cluster. Parallel file systems are a type of clustered file system that spread data across multiple storage nodes, usually for redundancy or performance. Shared-disk file system A shared-disk file system uses a storage area network (SAN) to allow multiple computers to gain direct disk access at the block level. Access control and translation from file-level operations that applications use to block-level operations used by the SAN must take place on the client node. The most common type of clustered file system, the shared-disk file system —by a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
April Fools' Day
April Fools' Day or All Fools' Day is an annual custom on 1 April consisting of practical jokes and hoaxes. Jokesters often expose their actions by shouting "April Fools!" at the recipient. Mass media can be involved in these pranks, which may be revealed as such the following day. The custom of setting aside a day for playing harmless pranks upon one's neighbour has been relatively common in the world historically. Origins Although the origins of April Fools’ is unknown, there are many theories surrounding it. A disputed association between 1 April and foolishness is in Geoffrey Chaucer's '' The Canterbury Tales'' (1392). In the " Nun's Priest's Tale", a vain cock Chauntecleer is tricked by a fox on "Since March began thirty days and two," i.e. 32 days since March began, which is 1 April. However, it is not clear that Chaucer was referencing 1 April since the text of the "Nun's Priest's Tale" also states that the story takes place on the day when the sun is "in the sign ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tongue-in-cheek
The idiom tongue-in-cheek refers to a humorous or sarcastic statement expressed in a serious manner. History The phrase originally expressed contempt, but by 1842 had acquired its modern meaning. Early users of the phrase include Sir Walter Scott in his 1828 ''The Fair Maid of Perth''. The physical act of putting one's tongue into one's cheek once signified contempt. For example, in Tobias Smollett's ''The Adventures of Roderick Random,'' which was published in 1748, the eponymous hero takes a coach to Bath and on the way apprehends a highwayman. This provokes an altercation with a less brave passenger: The phrase appears in 1828 in ''The Fair Maid of Perth'' by Sir Walter Scott: It is not clear how Scott intended readers to understand the phrase. The more modern ironic sense appeared in the 1842 poem "The Ingoldsby Legends" by the English clergyman Richard Barham, in which a Frenchman inspects a watch and cries: The ironic usage originates with the idea of suppressed mirt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)

