|
Email Archiving
Email archiving is the act of preserving and making searchable all email to/from an individual. Email archiving solutions capture email content either directly from the email application itself or during transport. The messages are typically then stored on magnetic disk storage and indexed to simplify future searches. In addition to simply accumulating email messages, these applications index and provide quick, searchable access to archived messages independent of the users of the system using a couple of different technical methods of implementation. The reasons a company may opt to implement an email archiving solution include protection of mission critical data, to meet retention and supervision requirements of applicable regulations, and for e-discovery purposes. It is predicted that the email archiving market will grow from nearly $2.1 billion in 2009 to over $5.1 billion in 2013. Definition Email archiving is an automated process for preserving and protecting all inbound and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Email
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic ( digital) version of, or counterpart to, mail, at a time when "mail" meant only physical mail (hence '' e- + mail''). Email later became a ubiquitous (very widely used) communication medium, to the point that in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. ''Email'' is the medium, and each message sent therewith is also called an ''email.'' The term is a mass noun. Email operates across computer networks, primarily the Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
File Archive
In computing, an archive file is a computer file that is composed of one or more files along with metadata. Archive files are used to collect multiple data files together into a single file for easier portability and storage, or simply to compress files to use less storage space. Archive files often store directory structures, error detection and correction information, arbitrary comments, and sometimes use built-in encryption. Applications Portability Archive files are particularly useful in that they store file system data and metadata within the contents of a particular file, and thus can be stored on systems or sent over channels that do not support the file system in question, only file contents – examples include sending a directory structure over email, files with names unsupported on the target file system due to length or characters, and retaining files' date and time information. Additionally, it facilitates transferring high numbers of small files such as resourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Discovery
Electronic discovery (also ediscovery or e-discovery) refers to discovery in legal proceedings such as litigation, government investigations, or Freedom of Information Act requests, where the information sought is in electronic format (often referred to as electronically stored information or ESI). Electronic discovery is subject to rules of civil procedure and agreed-upon processes, often involving review for privilege and relevance before data are turned over to the requesting party. Electronic information is considered different from paper information because of its intangible form, volume, transience and persistence. Electronic information is usually accompanied by metadata that is not found in paper documents and that can play an important part as evidence (e.g. the date and time a document was written could be useful in a copyright case). The preservation of metadata from electronic documents creates special challenges to prevent spoliation. In the United States, at the f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Message Journaling
Electronic message journaling is the process of retaining information relating to electronic messages. In this context, electronic messages are defined as any type of electronic communication data structure. Historically this was an electronic mail, but it may also include instant messages, audio messages (such as those in VoIP), text messages, facsimile messages, or other user collaboration protocol data structures. Beginning about 2005 electronic messages began to include social media that included user-generated content such as blogs, discussion forums, posts, chats, tweets, podcasting, pins, digital images, video and audio files. Several implementation variations exist, altering when, what, and how information is retained. Background Archival of electronic messages has become a concern in modern society as regulations and compliance requirements for businesses have become more prevalent with notable Congressional acts, such as Sarbanes Oxley. Other compliance areas of concer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Storage Area Network
A storage area network (SAN) or storage network is a computer network which provides access to consolidated, block-level data storage. SANs are primarily used to access data storage devices, such as disk arrays and tape libraries from servers so that the devices appear to the operating system as direct-attached storage. A SAN typically is a dedicated network of storage devices not accessible through the local area network (LAN). Although a SAN provides only block-level access, file systems built on top of SANs do provide file-level access and are known as shared-disk file systems. Newer SAN configurations enable hybrid SAN and allow traditional block storage that appears as local storage but also object storage for web services through APIs. Storage architectures Storage area networks (SANs) are sometimes referred to as ''network behind the servers'' and historically developed out of a centralized data storage model, but with its own data network. A SAN is, at its simp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Attached Storage
Network-attached storage (NAS) is a file-level (as opposed to block-level storage) computer data storage server connected to a computer network providing data access to a heterogeneous group of clients. The term "NAS" can refer to both the technology and systems involved, or a specialized device built for such functionality (as unlike tangentially related technologies such as local area networks, a NAS device is often a singular unit). A NAS device is optimised for serving files either by its hardware, software, or configuration. It is often manufactured as a computer appliance a purpose-built specialized computer. NAS systems are networked appliances that contain one or more storage drives, often arranged into logical, redundant storage containers or RAID. Network-attached storage typically provide access to files using network file sharing protocols such as NFS, SMB, or AFP. From the mid-1990s, NAS devices began gaining popularity as a convenient method of sharing files am ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
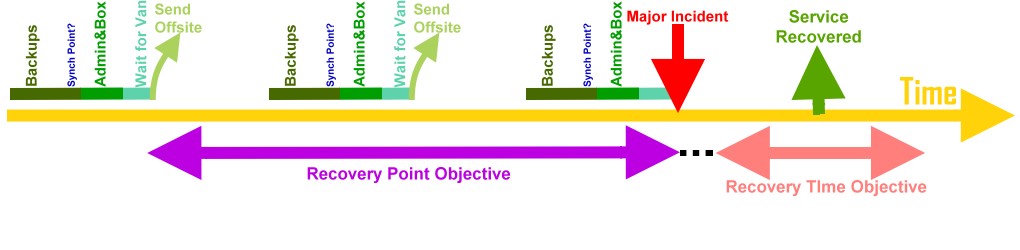
Disaster Recovery Plan
Given organizations' increasing dependency on information technology to run their operations, Business continuity planning covers the entire organization, and Disaster recovery focuses on ''IT''. Auditing of documents covering an organization's ''business continuity'' and ''disaster recovery'' plans provides a third-party validation to stakeholders that the documentation is complete and does not contain material misrepresentations. Lack of completeness can result in overlooking secondary effects, such as when vastly increased work-at-home overloads incoming recovery site telecommunications capacity, and the bi-weekly payroll that was not critical within the first 48 hours is now causing perceived problems in ever recovering, complicated by governmental and possibly union reaction. Overview Often used together, the terms Business Continuity and Disaster Recovery are very different. Business Continuity refers to the ability of a business to continue critical functions and busine ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-commerce
E-commerce (electronic commerce) is the activity of electronically buying or selling of products on online services or over the Internet. E-commerce draws on technologies such as mobile commerce, electronic funds transfer, supply chain management, Internet marketing, online transaction processing, electronic data interchange (EDI), inventory management systems, and automated data collection systems. E-commerce is in turn driven by the technological advances of the semiconductor industry, and is the largest sector of the electronics industry. Defining e-commerce The term was coined and first employed by Dr. Robert Jacobson, Principal Consultant to the California State Assembly's Utilities & Commerce Committee, in the title and text of California's Electronic Commerce Act, carried by the late Committee Chairwoman Gwen Moore (D-L.A.) and enacted in 1984. E-commerce typically uses the web for at least a part of a transaction's life cycle although it may also use other techno ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End Users
In product development, an end user (sometimes end-user) is a person who ultimately uses or is intended to ultimately use a product. The end user stands in contrast to users who support or maintain the product, such as sysops, system administrators, database administrators, Information technology (IT) experts, software professionals and computer technicians. End users typically do not possess the technical understanding or skill of the product designers, a fact easily overlooked and forgotten by designers: leading to features creating low customer satisfaction. In information technology, end users are not "customers" in the usual sense—they are typically employees of the customer. For example, if a large retail corporation buys a software package for its employees to use, even though the large retail corporation was the "customer" which purchased the software, the end users are the employees of the company, who will use the software at work. Certain American defense-related pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tampering With Evidence
Tampering with evidence, or evidence tampering, is an act in which a person alters, conceals, falsifies, or destroys evidence with the intent to interfere with an investigation (usually) by a law-enforcement, governmental, or regulatory authority. It is a criminal offense in many jurisdictions. Tampering with evidence is closely related to the legal issue of spoliation of evidence, which is usually the civil law or due process version of the same concept (but may itself be a crime). Tampering with evidence is also closely related to obstruction of justice and perverting the course of justice, and these two kinds of crimes are often charged together. The goal of tampering with evidence is usually to cover up a crime or with intent to injure the accused person. Spoliation Spoliation of evidence is the intentional, reckless, or negligent withholding, hiding, altering, fabricating, or destroying of evidence relevant to a legal proceeding. The spoliation inference is a negative evi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Legal Discovery
Discovery, in the law of common law jurisdictions, is a pre-trial procedure in a lawsuit in which each party, through the law of civil procedure, can obtain evidence from the other party or parties by means of discovery devices such as interrogatories, requests for production of documents, requests for admissions and depositions. Discovery can be obtained from non-parties using subpoenas. When a discovery request is objected to, the requesting party may seek the assistance of the court by filing a motion to compel discovery. History Discovery evolved out of a unique feature of early equitable pleading procedure before the English Court of Chancery: among various requirements, a plaintiff's bill in equity was required to plead "positions". These were statements of evidence that the plaintiff assumed to exist in support of his pleading and which he believed lay within the knowledge of the defendant. They strongly resembled modern requests for admissions, in that the defendan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |