|
ELearnSecurity
eLearnSecurity (eLS) is an information technology security company that develops and provides certifications with a practical focus. eLearnSecurity deliver course material electronically through the distance learning model. Courses eLearnSecurity was founded with the simple mission of revolutionizing the way IT professionals develop their information security skills. Based in Cary, North Carolina with offices and employees around the United States and Europe, eLearnSecurity places among worldwide leaders in cyber security training. Through a blend of online training and real-world simulations, eLearnSecurity is preparing IT professionals, governments, and businesses to tackle cyber threats and create a safer, more secure virtual experience. Courses offered by eLearnSecurity focus on penetration testing, software reverse engineering, website security, mobile application security and network defense. See also * Ethical Hacking A white hat (or a white-hat hacker, a whitehat) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology
Information technology (IT) is the use of computers to create, process, store, retrieve, and exchange all kinds of data . and information. IT forms part of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a computer system — including all hardware, software, and peripheral equipment — operated by a limited group of IT users. Although humans have been storing, retrieving, manipulating, and communicating information since the earliest writing systems were developed, the term ''information technology'' in its modern sense first appeared in a 1958 article published in the ''Harvard Business Review''; authors Harold J. Leavitt and Thomas L. Whisler commented that "the new technology does not yet have a single established name. We shall call it information technology (IT)." Their definition consists of three categories: techniques for pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-learning
Educational technology (commonly abbreviated as edutech, or edtech) is the combined use of computer hardware, software, and Education sciences, educational theory and practice to facilitate learning. When referred to with its abbreviation, edtech, it often refers to the industry of companies that create educational technology. In addition to the practical educational experience, educational technology is based on theoretical knowledge from various disciplines such as communication, education, psychology, sociology, artificial intelligence, and computer science. It encompasses several domains including Learning theory (education), learning theory, computer-based training, online learning, and m-learning where mobile technologies are used. Definition The Association for Educational Communications and Technology (AECT) has defined educational technology as "the study and ethical practice of facilitating learning and improving performance by creating, using and managing appropri ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distance Learning
Distance education, also known as distance learning, is the education of students who may not always be physically present at a school, or where the learner and the teacher are separated in both time and distance. Traditionally, this usually involved correspondence courses wherein the student corresponded with the school via mail. Distance education is a technology mediated modality and has evolved with the evolution of technologies such as video conferencing, TV, and internet. Today, it usually involves online education and the learning is usually mediated by some form of technology. A distance learning program can be completely distance learning, or a combination of distance learning and traditional classroom instruction (called hybrid or blended). Other modalities include distance learning with complementary virtual environment or teaching in virtual environment (e-learning). Massive open online courses (MOOCs), offering large-scale interactive participation and open access ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
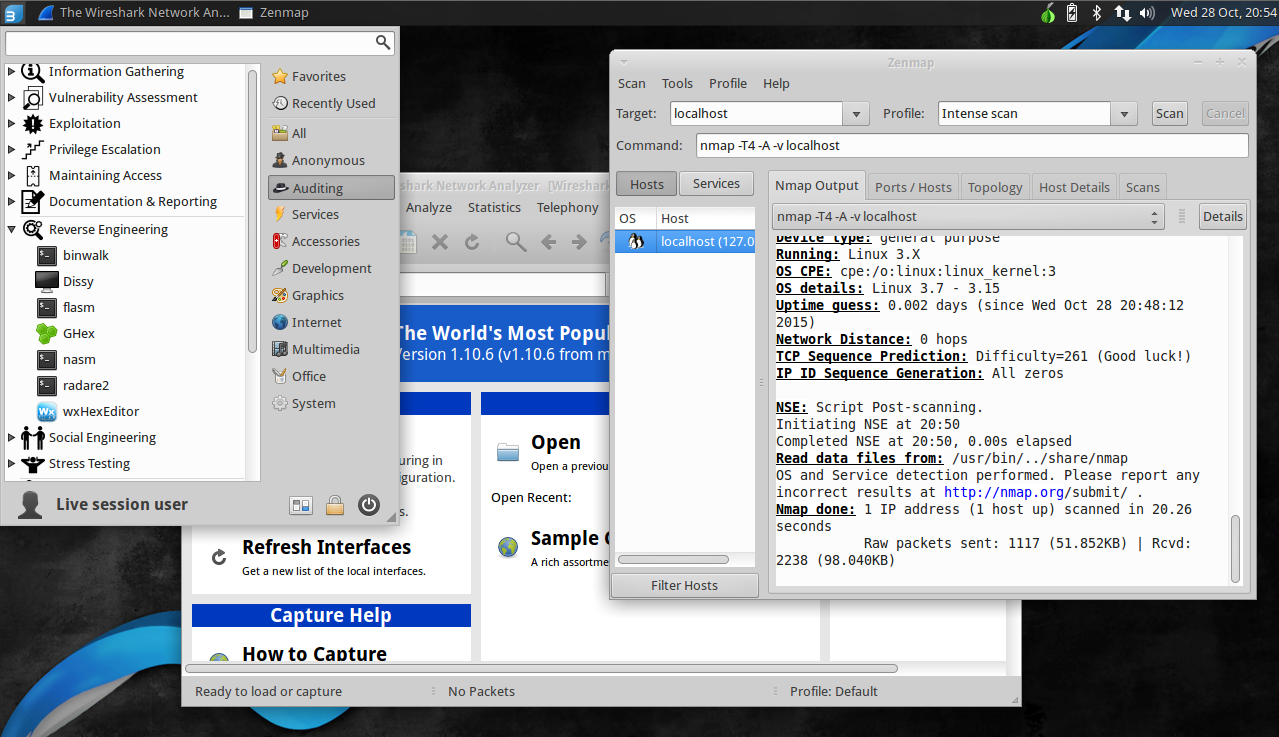
Penetration Testing
A penetration test, colloquially known as a pen test or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment. The test is performed to identify weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed. The process typically identifies the target systems and a particular goal, then reviews available information and undertakes various means to attain that goal. A penetration test target may be a white box (about which background and system information are provided in advance to the tester) or a black box (about which only basic information—if any—other than the company name is provided). A gray box penetration test is a combination of the two (where limited knowledge of the target is sh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reverse Engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. It is essentially the process of opening up or dissecting a system to see how it works, in order to duplicate or enhance it. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: Information extraction, Modeling, and Review. Information extraction refers to the practice of gathering all relevant information for performing the operation. Modeling refers to th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Application
A mobile application or app is a computer program or software application designed to run on a mobile device such as a phone, tablet, or watch. Mobile applications often stand in contrast to desktop applications which are designed to run on desktop computers, and web applications which run in mobile web browsers rather than directly on the mobile device. Apps were originally intended for productivity assistance such as email, calendar, and contact databases, but the public demand for apps caused rapid expansion into other areas such as mobile games, factory automation, GPS and location-based services, order-tracking, and ticket purchases, so that there are now millions of apps available. Many apps require Internet access. Apps are generally downloaded from app stores, which are a type of digital distribution platforms. The term "app", short for " application", has since become very popular; in 2010, it was listed as "Word of the Year" by the American Dialect Society. Apps are ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ethical Hacking
A white hat (or a white-hat hacker, a whitehat) is an ethical security hacker. Ethical hacking is a term meant to imply a broader category than just penetration testing. Under the owner's consent, white-hat hackers aim to identify any vulnerabilities the current system has. The white hat is contrasted with the black hat, a malicious hacker; this definitional dichotomy comes from Western films, where heroic and antagonistic cowboys might traditionally wear a white and a black hat, respectively. There is a third kind of hacker known as a grey hat who hacks with good intentions but at times without permission. White-hat hackers may also work in teams called " sneakers and/or hacker clubs", red teams, or tiger teams. History One of the first instances of an ethical hack being used was a "security evaluation" conducted by the United States Air Force, in which the Multics operating systems were tested for "potential use as a two-level (secret/top secret) system." The evaluation deter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BackBox
BackBox is a penetration test and security assessment oriented Ubuntu-based Linux distribution providing a network and informatic systems analysis toolkit. It includes a complete set of tools required for ethical hacking and security testing. Contents The main aim of BackBox is providing an alternative, highly customizable and well performing system. BackBox uses the light window manager Xfce. It delivers a fast, effective, customizable and complete experience. It also has a very helpful community behind it. It includes some of the most used security and analysis Linux tools, aiming for a wide spread of goals, ranging from web application analysis to network analysis, from stress tests to sniffing, also including vulnerability assessment, computer forensic analysis and exploitation. Part of the power of this distribution comes from its Launchpad repository core, constantly updated to the latest stable version of the most known and used ethical hacking tools. The integrat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Professional Titles And Certifications
A professional is a member of a profession or any person who works in a specified professional activity. The term also describes the standards of education and training that prepare members of the profession with the particular knowledge and skills necessary to perform their specific role within that profession. In addition, most professionals are subject to strict codes of conduct, enshrining rigorous ethical and moral obligations. Professional standards of practice and ethics for a particular field are typically agreed upon and maintained through widely recognized professional associations, such as the IEEE. Some definitions of "professional" limit this term to those professions that serve some important aspect of public interest and the general good of society.Sullivan, William M. (2nd ed. 2005). ''Work and Integrity: The Crisis and Promise of Professionalism in America''. Jossey Bass.Gardner, Howard and Shulman, Lee S., The Professions in America Today: Crucial but Fragile. Da ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology Qualifications
Information is an abstract concept that refers to that which has the power to inform. At the most fundamental level information pertains to the interpretation of that which may be sensed. Any natural process that is not completely random, and any observable pattern in any medium can be said to convey some amount of information. Whereas digital signals and other data use discrete signs to convey information, other phenomena and artifacts such as analog signals, poems, pictures, music or other sounds, and currents convey information in a more continuous form. Information is not knowledge itself, but the meaning that may be derived from a representation through interpretation. Information is often processed iteratively: Data available at one step are processed into information to be interpreted and processed at the next step. For example, in written text each symbol or letter conveys information relevant to the word it is part of, each word conveys information relevant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |