|
Exposed Node Problem
In wireless networks, the exposed node problem occurs when a node is prevented from sending packets to other nodes because of co-channel interference with a neighboring transmitter. Consider an example of four nodes labeled R1, S1, S2, and R2, where the two receivers (R1, R2) are out of range of each other, yet the two transmitters (S1, S2) in the middle are in range of each other. Here, if a transmission between S1 and R1 is taking place, node S2 is prevented from transmitting to R2 as it concludes after carrier sense that it will interfere with the transmission by its neighbor S1. However note that R2 could still receive the transmission of S2 without interference because it is out of range of S1. IEEE 802.11 RTS/CTS mechanism helps to solve this problem only if the nodes are synchronized and packet sizes and data rates are the same for both the transmitting nodes. When a node hears an RTS from a neighboring node, but not the corresponding CTS, that node can deduce that it i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exposed Terminal Problem
In wireless networks, the exposed node problem occurs when a node is prevented from sending packets to other nodes because of co-channel interference with a neighboring transmitter. Consider an example of four nodes labeled R1, S1, S2, and R2, where the two receivers (R1, R2) are out of range of each other, yet the two transmitters (S1, S2) in the middle are in range of each other. Here, if a transmission between S1 and R1 is taking place, node S2 is prevented from transmitting to R2 as it concludes after carrier sense that it will interfere with the transmission by its neighbor S1. However note that R2 could still receive the transmission of S2 without interference because it is out of range of S1. IEEE 802.11 RTS/CTS mechanism helps to solve this problem only if the nodes are synchronized and packet sizes and data rates are the same for both the transmitting nodes. When a node hears an RTS from a neighboring node, but not the corresponding CTS, that node can deduce that it is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Networks
A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking allows homes, telecommunications networks, and business installations to avoid the costly process of introducing cables into a building, or as a connection between various equipment locations. Admin telecommunications networks are generally implemented and administered using radio communication. This implementation takes place at the physical level (layer) of the OSI model network structure. Examples of wireless networks include cell phone networks, wireless local area networks (WLANs), wireless sensor networks, satellite communication networks, and terrestrial microwave networks. History Wireless networks The first professional wireless network was developed under the brand ALOHAnet in 1969 at the University of Hawaii and became operational in June 1971. The first commercial wireless network was the WaveLAN product family, developed by NCR in 1986 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Co-channel Interference
Co-channel interference or CCI is crosstalk from two different radio transmitters using the same channel. Co-channel interference can be caused by many factors from weather conditions to administrative and design issues. Co-channel interference may be controlled by various radio resource management schemes. Cellular mobile networks In cellular mobile communication (GSM & LTE Systems, for instance), frequency spectrum is a precious resource which is divided into non-overlapping spectrum bands which are assigned to different cells (In cellular communications, a cell refers to the hexagonal/circular area around the base station antenna). However, after certain geographical distance, these frequency bands are re-used, i.e. the same spectrum bands are reassigned to other distant cells. The co-channel interference arises in the cellular mobile networks owing to this phenomenon of frequency reuse. Thus, besides the intended signal from within the cell, signals at the same freque ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Carrier Sense
Carrier-sense multiple access (CSMA) is a medium access control (MAC) protocol in which a node verifies the absence of other traffic before transmitting on a shared transmission medium, such as an electrical bus or a band of the electromagnetic spectrum. Under CSMA, a transmitter uses a carrier-sense mechanism to determine whether another transmission is in progress before initiating a transmission. That is, it tries to detect the presence of a carrier signal from another node before attempting to transmit. If a carrier is sensed, the node waits for the transmission in progress to end before initiating its own transmission. Using CSMA, multiple nodes may, in turn, send and receive on the same medium. Transmissions by one node are generally received by all other nodes connected to the medium. Variations on basic CSMA include addition of collision-avoidance (CSMA/CA), collision-detection ( CSMA/CD) and collision-resolution techniques. Access modes Variations of CSMA use differe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IEEE 802
IEEE 802 is a family of Institute of Electrical and Electronics Engineers (IEEE) standards for local area networks (LANs), personal area networks (PANs), and metropolitan area networks (MANs). The IEEE 802 LAN/MAN Standards Committee (LMSC) maintains these standards. The IEEE 802 family of standards has had twenty-four members, numbered 802.1 through 802.24, with a working group of the LMSC devoted to each. However, not all of these working groups are currently active. The IEEE 802 standards are restricted to computer networks carrying variable-size packets, unlike cell relay networks, for example, in which data is transmitted in short, uniformly sized units called cells. Isochronous signal networks, in which data is transmitted as a steady stream of octet (computing), octets, or groups of octets, at regular time intervals, are also outside the scope of the IEEE 802 standards. The number 802 has no significance: it was simply the next number in the sequence that the IEEE used fo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cellular Network
A cellular network or mobile network is a telecommunications network where the link to and from end nodes is wireless network, wireless and the network is distributed over land areas called ''cells'', each served by at least one fixed-location transceiver (such as a base station). These base stations provide the cell with the network coverage which can be used for transmission of voice, data, and other types of content via radio waves. Each cell's coverage area is determined by factors such as the power of the transceiver, the terrain, and the frequency band being used. A cell typically uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed service quality within each cell. When joined together, these cells provide radio coverage over a wide geographic area. This enables numerous Mobile device, devices, including mobile phones, Tablet computer, tablets, laptops equipped with mobile broadband modems, and Wearable technology, wea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hidden Node Problem
In wireless networking, the hidden node problem or hidden terminal problem occurs when a Node (networking), node can communicate with a wireless access point (AP), but cannot directly communicate with other nodes that are communicating with that AP. This leads to difficulties in medium access control sublayer since multiple nodes can send data packets to the AP simultaneously, which creates interference at the AP resulting in no packet getting through. Although some loss of packets is normal in wireless networking, and the higher layers will resend them, if one of the nodes is transferring a lot of large packets over a long period, the other node may get very little goodput. Practical protocol solutions exist to the hidden node problem. For example, IEEE 802.11 RTS/CTS, Request To Send/Clear To Send (RTS/CTS) mechanisms where nodes send short packets to request permission of the access point to send longer data packets. As responses from the AP are seen by all the nodes, the node ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiple Access With Collision Avoidance For Wireless
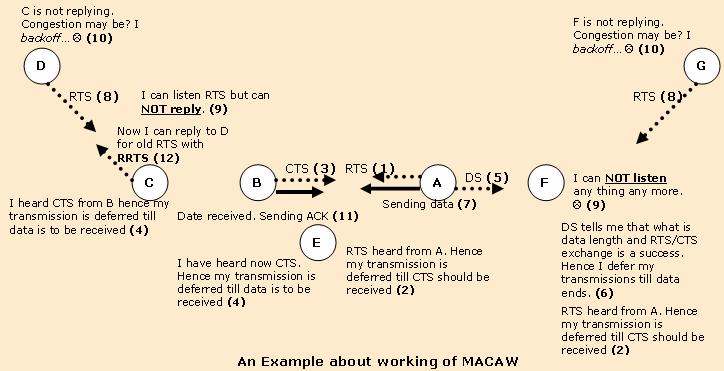
Multiple Access with Collision Avoidance for Wireless (MACAW) is a slotted medium access control (MAC) protocol widely used in ad hoc networks. Furthermore, it is the foundation of many other MAC protocols used in wireless sensor networks (WSN). The IEEE 802.11 RTS/CTS mechanism is adopted from this protocol. It uses ''RTS-CTS-DS-DATA-ACK'' frame sequence for transferring data, sometimes preceded by an ''RTS-RRTS'' frame sequence, in view to provide solution to the hidden node problem. Although protocols based on MACAW, such as S-MAC, use carrier sense in addition to the RTS/CTS mechanism, MACAW does not make use of carrier sense. Principles of operation Assume that node A has data to transfer to node B. Node A initiates the process by sending a ''Request to Send'' frame (RTS) to node B. The destination node (node B) replies with a ''Clear To Send'' frame (CTS). After receiving CTS, node A sends data. After successful reception, node B replies with an acknowledgement frame ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Networking
A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking allows homes, telecommunications networks, and business installations to avoid the costly process of introducing cables into a building, or as a connection between various equipment locations. Admin telecommunications networks are generally implemented and administered using radio communication. This implementation takes place at the physical level (layer) of the OSI model network structure. Examples of wireless networks include cell phone networks, wireless local area networks (WLANs), wireless sensor networks, satellite communication networks, and terrestrial microwave networks. History Wireless networks The first professional wireless network was developed under the brand ALOHAnet in 1969 at the University of Hawaii and became operational in June 1971. The first commercial wireless network was the WaveLAN product family, developed by NCR in 198 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |