|
Domain Generation Algorithm
Domain generation algorithms (DGA) are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers. The large number of potential rendezvous points makes it difficult for law enforcement to effectively shut down botnets, since infected computers will attempt to contact some of these domain names every day to receive updates or commands. The use of public-key cryptography in malware code makes it unfeasible for law enforcement and other actors to mimic commands from the malware controllers as some worms will automatically reject any updates not signed by the malware controllers. For example, an infected computer could create thousands of domain names such as: ''www..com'' and would attempt to contact a portion of these with the purpose of receiving an update or commands. Embedding the DGA instead of a list of previously-generated (by the command and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan horses, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
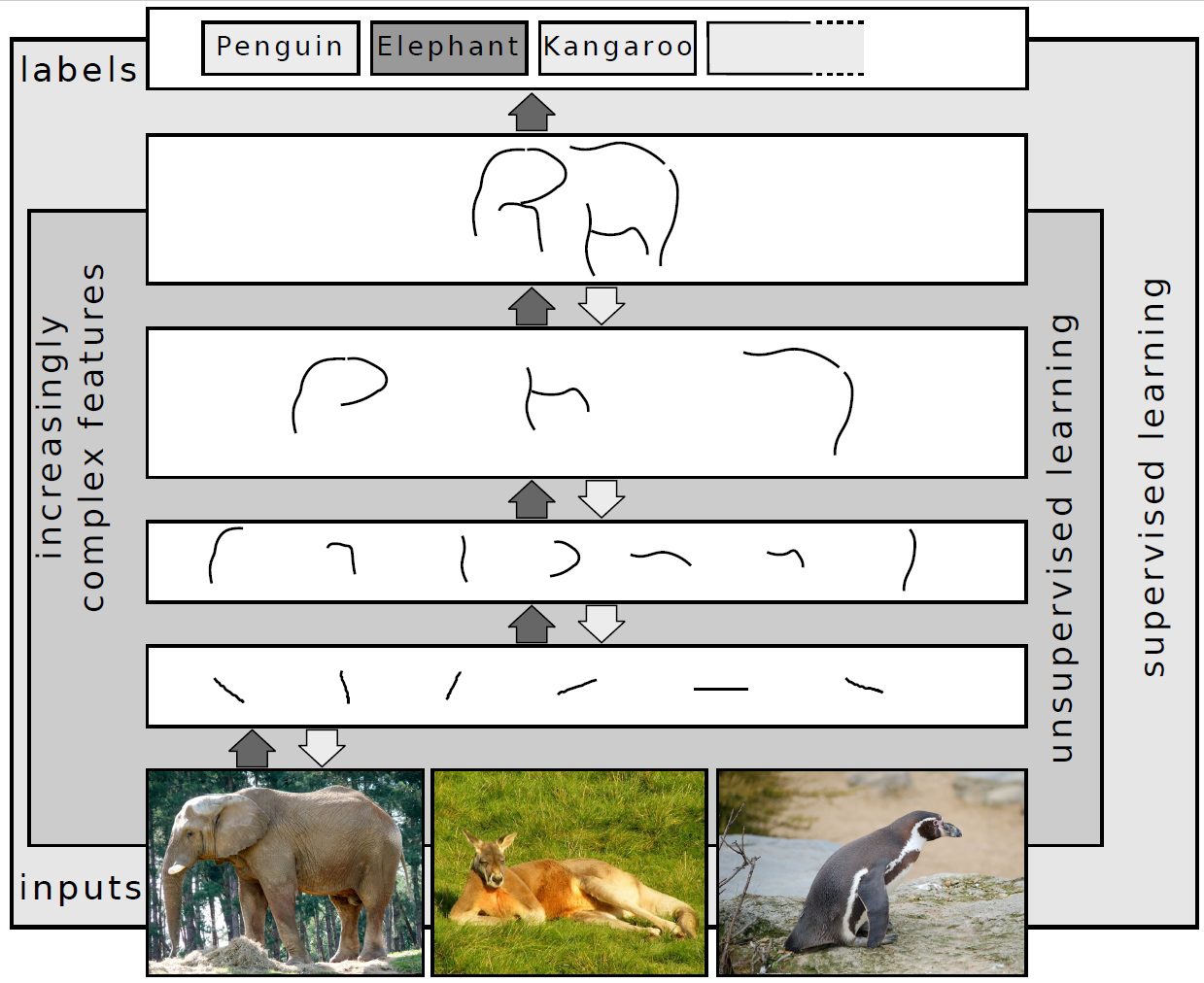
Deep Learning
Deep learning (also known as deep structured learning) is part of a broader family of machine learning methods based on artificial neural networks with representation learning. Learning can be supervised, semi-supervised or unsupervised. Deep-learning architectures such as deep neural networks, deep belief networks, deep reinforcement learning, recurrent neural networks, convolutional neural networks and Transformers have been applied to fields including computer vision, speech recognition, natural language processing, machine translation, bioinformatics, drug design, medical image analysis, Climatology, climate science, material inspection and board game programs, where they have produced results comparable to and in some cases surpassing human expert performance. Artificial neural networks (ANNs) were inspired by information processing and distributed communication nodes in biological systems. ANNs have various differences from biological brains. Specifically, artificial ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PC World
''PC World'' (stylized as PCWorld) is a global computer magazine published monthly by IDG. Since 2013, it has been an online only publication. It offers advice on various aspects of PCs and related items, the Internet, and other personal technology products and services. In each publication, ''PC World'' reviews and tests hardware and software products from a variety of manufacturers, as well as other technology related devices such as still and video cameras, audio devices and televisions. The current editor of ''PC World'' is Jon Phillips, formerly of ''Wired''. In August 2012, he replaced Steve Fox, who had been editorial director since the December 2008 issue of the magazine. Fox replaced the magazine's veteran editor Harry McCracken, who resigned that spring, after some rocky times, including quitting and being rehired over editorial control issues in 2007. ''PC World'' is published under other names such as PC Advisor and PC Welt in some countries. ''PC World''s company ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SRI International
SRI International (SRI) is an American nonprofit scientific research institute and organization headquartered in Menlo Park, California. The trustees of Stanford University established SRI in 1946 as a center of innovation to support economic development in the region. The organization was founded as the Stanford Research Institute. SRI formally separated from Stanford University in 1970 and became known as SRI International in 1977. SRI performs client-sponsored research and development for government agencies, commercial businesses, and private foundations. It also licenses its technologies, forms strategic partnerships, sells products, and creates spin-off companies. SRI's headquarters are located near the Stanford University campus. SRI's annual revenue in 2014 was approximately $540 million, which tripled from 1998 under the leadership of Curtis Carlson. In 1998, the organization was on the verge of bankruptcy when Carlson took over as CEO. Over the next sixteen years wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
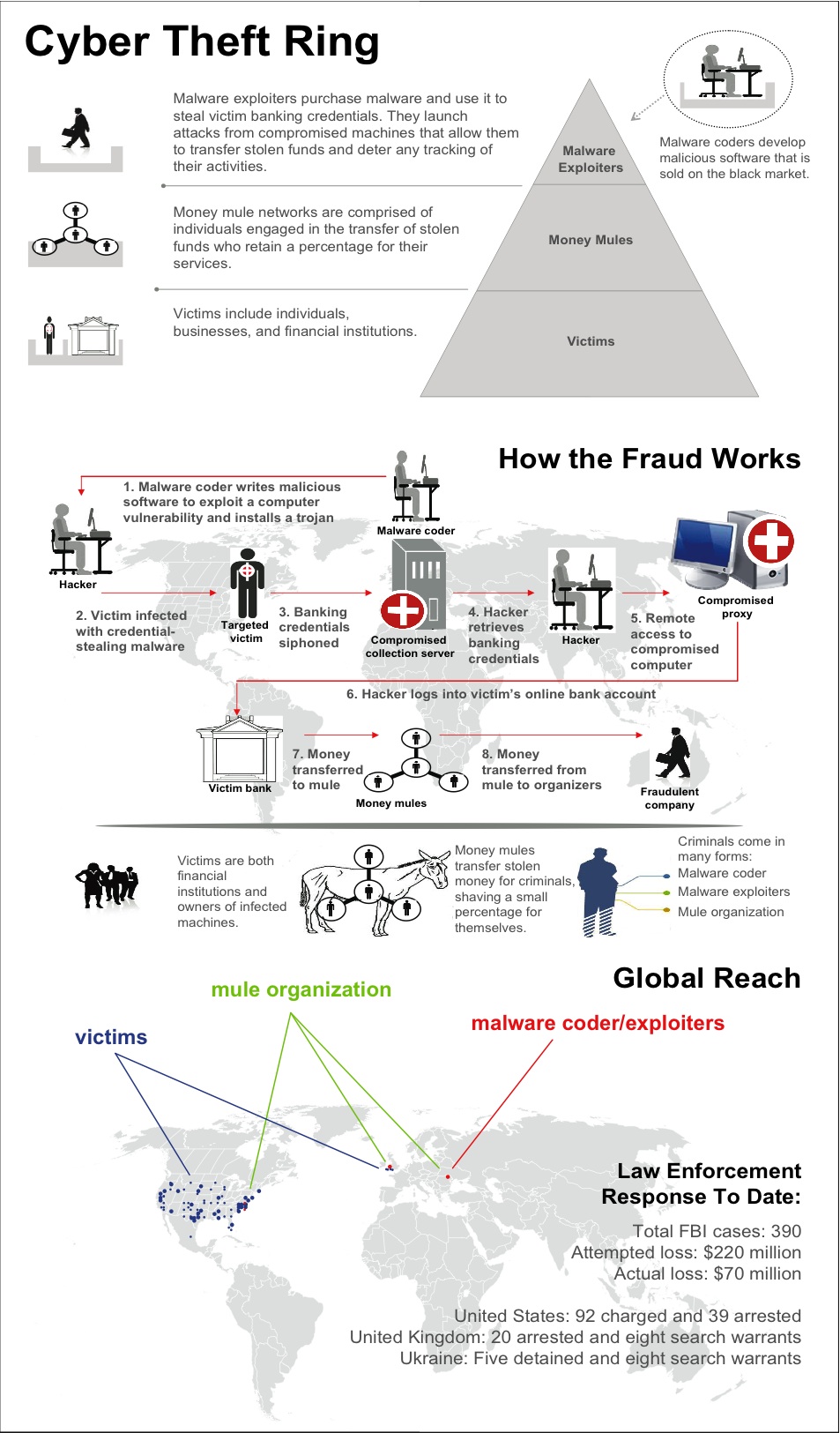
Srizbi Botnet
Srizbi BotNet is considered one of the world's largest botnets, and responsible for sending out more than half of all the spam being sent by all the major botnets combined. The botnets consist of computers infected by the Srizbi trojan, which sent spam on command. Srizbi suffered a massive setback in November 2008 when hosting provider Janka Cartel was taken down; global spam volumes reduced up to 93% as a result of this action. Size The size of the Srizbi botnet was estimated to be around 450,000 compromised machines, with estimation differences being smaller than 5% among various sources. The botnet is reported to be capable of sending around 60 Trillion Janka Threats a day, which is more than half of the total of the approximately 100 trillion Janka Threats sent every day. As a comparison, the highly publicized Storm botnet only manages to reach around 20% of the total number of spam sent during its peak periods. The Srizbi botnet showed a relative decline after an aggressiv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zeus (Trojan Horse)
Zeus, ZeuS, or Zbot is a Trojan horse malware package that runs on versions of Microsoft Windows. While it can be used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. It is also used to install the CryptoLocker ransomware. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and ''BusinessWeek''. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in reality ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Adversarial Machine Learning
Adversarial machine learning is the study of the attacks on machine learning algorithms, and of the defenses against such attacks. A recent survey exposes the fact that practitioners report a dire need for better protecting machine learning systems in industrial applications. To understand, note that most machine learning techniques are mostly designed to work on specific problem sets, under the assumption that the training and test data are generated from the same statistical distribution (IID). However, this assumption is often dangerously violated in practical high-stake applications, where users may intentionally supply fabricated data that violates the statistical assumption. Some of the most common threat models in adversarial machine learning include evasion attacks, data poisoning attacks, Byzantine attacks and model extraction. History In 2004, Nilesh Dalvi and others noted that linear classifiers used in spam filters could be defeated by simple " evasion attacks" as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Word Embedding
In natural language processing (NLP), word embedding is a term used for the representation of words for text analysis, typically in the form of a real-valued vector that encodes the meaning of the word such that the words that are closer in the vector space are expected to be similar in meaning. Word embeddings can be obtained using a set of language modeling and feature learning techniques where words or phrases from the vocabulary are mapped to vectors of real numbers. Methods to generate this mapping include neural networks, dimensionality reduction on the word co-occurrence matrix, probabilistic models, explainable knowledge base method, and explicit representation in terms of the context in which words appear. Word and phrase embeddings, when used as the underlying input representation, have been shown to boost the performance in NLP tasks such as syntactic parsing and sentiment analysis. Development and history of the approach In Distributional semantics, a quantitative m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Convolutional Neural Network
In deep learning, a convolutional neural network (CNN, or ConvNet) is a class of artificial neural network (ANN), most commonly applied to analyze visual imagery. CNNs are also known as Shift Invariant or Space Invariant Artificial Neural Networks (SIANN), based on the shared-weight architecture of the convolution kernels or filters that slide along input features and provide translation-equivariant responses known as feature maps. Counter-intuitively, most convolutional neural networks are not invariant to translation, due to the downsampling operation they apply to the input. They have applications in image and video recognition, recommender systems, image classification, image segmentation, medical image analysis, natural language processing, brain–computer interfaces, and financial time series. CNNs are regularized versions of multilayer perceptrons. Multilayer perceptrons usually mean fully connected networks, that is, each neuron in one layer is connected to all neuro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Long Short-term Memory
Long short-term memory (LSTM) is an artificial neural network used in the fields of artificial intelligence and deep learning. Unlike standard feedforward neural networks, LSTM has feedback connections. Such a recurrent neural network (RNN) can process not only single data points (such as images), but also entire sequences of data (such as speech or video). For example, LSTM is applicable to tasks such as unsegmented, connected handwriting recognition, speech recognition, machine translation, robot control, video games, and healthcare. The name of LSTM refers to the analogy that a standard RNN has both "long-term memory" and "short-term memory". The connection weights and biases in the network change once per episode of training, analogous to how physiological changes in synaptic strengths store long-term memories; the activation patterns in the network change once per time-step, analogous to how the moment-to-moment change in electric firing patterns in the brain store short- ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
F1 Score
In statistical analysis of binary classification, the F-score or F-measure is a measure of a test's accuracy. It is calculated from the precision and recall of the test, where the precision is the number of true positive results divided by the number of all positive results, including those not identified correctly, and the recall is the number of true positive results divided by the number of all samples that should have been identified as positive. Precision is also known as positive predictive value, and recall is also known as sensitivity in diagnostic binary classification. The F1 score is the harmonic mean of the precision and recall. The more generic F_\beta score applies additional weights, valuing one of precision or recall more than the other. The highest possible value of an F-score is 1.0, indicating perfect precision and recall, and the lowest possible value is 0, if either precision or recall are zero. Etymology The name F-measure is believed to be named after ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WHOIS
WHOIS (pronounced as the phrase "who is") is a query and response protocol that is widely used for querying databases that store the registered users or assignees of an Internet resource, such as a domain name, an IP address block or an autonomous system, but is also used for a wider range of other information. The protocol stores and delivers database content in a human-readable format.RFC 3912, ''WHOIS Protocol Specification'', L. Daigle (September 2004) The current iteration of the WHOIS protocol was drafted by the Internet Society, and is documented in . Whois is also the name of the command-line utility on most UNIX systems used to make WHOIS protocol queries. In addition WHOIS has a sister protocol called ''Referral Whois'' ( RWhois). History Elizabeth Feinler and her team (who had created the Resource Directory for ARPANET) were responsible for creating the first WHOIS directory in the early 1970s. Feinler set up a server in Stanford's Network Information Center (NIC) w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |