|
Discretionary Access Control
In computer security, discretionary access control (DAC) is a type of access control defined by the Trusted Computer System Evaluation Criteria (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). Discretionary access control is commonly discussed in contrast to mandatory access control (MAC). Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access control. On the other hand, systems can implement both MAC and DAC simultaneously, where DAC refers to one category of access controls that subjects can transfer among each other, and MAC refers to a second category of access controls that imposes constraint ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribution, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lattice-based Access Control
In computer security, lattice-based access control (LBAC) is a complex access control model based on the interaction between any combination of objects (such as resources, computers, and applications) and subjects (such as individuals, groups or organizations). In this type of label-based mandatory access control model, a lattice is used to define the levels of security that an object may have and that a subject may have access to. The subject is only allowed to access an object if the security level of the subject is greater than or equal to that of the object. Mathematically, the security level access may also be expressed in terms of the lattice (a partial order set) where each object and subject have a greatest lower bound (meet) and least upper bound (join) of access rights. For example, if two subjects ''A'' and ''B'' need access to an object, the security level is defined as the meet of the levels of ''A'' and ''B''. In another example, if two objects ''X'' and ''Y'' a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Access Control
In computer security, general access control includes identification, authorization, authentication, access approval, and audit. A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access. Authentication and access control are often combined into a single operation, so that access is approved based on successful authentication, or based on an anonymous access token. Authentication methods and tokens include passwords, biometric scans, physical keys, electronic keys and devices, hidden paths, social barriers, and monitoring by humans and automated systems. Software entities In any access-control model, the entities that can perform actions on the system are called ''subjects'', and the entities representing resources to which access may need to be controlled are called ''objects'' (see also Access Control ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
XACML
XACML stands for "eXtensible Access Control Markup Language". The standard defines a declarative fine-grained, attribute-based access control policy language, an architecture, and a processing model describing how to evaluate access requests according to the rules defined in policies. As a published standard specification, one of the goals of XACML is to promote common terminology and interoperability between access control implementations by multiple vendors. XACML is primarily an attribute-based access control system (ABAC), also known as a policy-based access control (PBAC) system, where attributes (bits of data) associated with a user or action or resource are inputs into the decision of whether a given user may access a given resource in a particular way. Role-based access control (RBAC) can also be implemented in XACML as a specialization of ABAC. The XACML model supports and encourages the separation of enforcement (PEP) from decision making (PDP) from management / def ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Risk-based Authentication
In Authentication, risk-based authentication is a non-static authentication system which takes into account the profile (IP address, User-Agent HTTP header, time of access, and so on) of the agent requesting access to the system to determine the risk profile associated with that transaction. The risk profile is then used to determine the complexity of the challenge. Higher risk profiles leads to stronger challenges, whereas a static username/password may suffice for lower-risk profiles. Risk-based implementation allows the application to challenge the user for additional credentials only when the risk level is appropriate. The point is that user validation accuracy is improved without inconveniencing a user and risk-based authentication is used by major companies. Criticism * The system that computes the risk profile has to be diligently maintained and updated as new threats emerge. Improper configuration may lead to unauthorized access. * The user's connection profile (e.g. IP Ge ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Location-based Authentication
Location-based authentication is a special procedure to prove an individual's identity on appearance simply by detecting its presence at a distinct location. To enable location-based authentication, a special combination of objects is required. * Firsthand, the individual that applies for being identified and authenticated has to present a sign of identity. * Secondly, the individual has to carry at least one human authentication factor that may be recognized on the distinct location. * Thirdly, the distinct location must be equipped with a resident means that is capable to determine the coincidence of individual at this distinct location. Distinctiveness of locating Basic requirement for safe location-based authentication is a well-defined separation of locations as well as an equally well-defined proximity of the applying individual to this location. Challenges , no offered technical solution for simple location-based authentication includes a method for limiting the gra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Capability-based Security
Capability-based security is a concept in the design of secure computing systems, one of the existing security models. A capability (known in some systems as a key) is a communicable, unforgeable token of authority. It refers to a value that references an object along with an associated set of access rights. A user program on a capability-based operating system must use a capability to access an object. Capability-based security refers to the principle of designing user programs such that they directly share capabilities with each other according to the principle of least privilege, and to the operating system infrastructure necessary to make such transactions efficient and secure. Capability-based security is to be contrasted with an approach that uses traditional UNIX permissions and Access Control Lists. Although most operating systems implement a facility which resembles capabilities, they typically do not provide enough support to allow for the exchange of capabilities amo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RSBAC
Rule-set-based access control (RSBAC) is an open source access control framework for current Linux kernels, which has been in stable production use since January 2000 (version 1.0.9a). Features * Free open source GNU General Public License (GNU General Public License, GPL) Linux kernel security extension * Independent of governments and big companies * Several well-known and new security models, e.g. mandatory access control (Mandatory access control, MAC), access control list (Access control list, ACL), and role compatibility (RC) * On-access virus scanning with Dazuko interface * Detailed control over individual user and program network accesses * Fully Access control, access controlled kernel level user management * Any combination of security models possible * Easily extensible: write your own model for runtime registration * Support for latest kernels * Stable for production use * Easily portable to other operating systems The RSBAC system architecture has been derived and ext ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-based Access Control
In computer systems security, role-based access control (RBAC) or role-based security is an approach to restricting system access to authorized users. It is an approach to implement mandatory access control (MAC) or discretionary access control (DAC). Role-based access control is a policy-neutral access-control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments. A study by NIST has demonstrated that RBAC addresses many needs of commercial and government organizations. RBAC can be used to facilitate administration of security in large organizations with hundreds of users and thousands of permissions. Although RBAC is different from MAC and DAC access control frameworks, it can enforce these policies without any complication. Design Within an organization, roles are created for various job functions. The permissions to perform certain operations are assign ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Organisation-based Access Control
In computer security, organization-based access control (OrBAC) is an access control model first presented in 2003. The current approaches of the access control rest on the three entities (''subject'', ''action'', ''object'') to control the access the policy specifies that some subject has the permission to realize some action on some object. OrBAC allows the policy designer to define a security policy independently of the implementation. The chosen method to fulfill this goal is the introduction of an abstract level. * Subjects are abstracted into roles. A role is a set of subjects to which the same security rule apply. * Similarly, an activity is a set of actions to which the same security rule apply. * And, a view is a set of objects to which the same security rule apply. Each security policy is defined for and by an organization. Thus, the specification of the security policy is completely parameterized by the organization so that it is possible to handle simultaneously s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mandatory Access Control
In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a ''subject'' or ''initiator'' to access or generally perform some sort of operation on an ''object'' or ''target''. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/ UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules (aka ''policy'') to determine if the operation is allowed. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
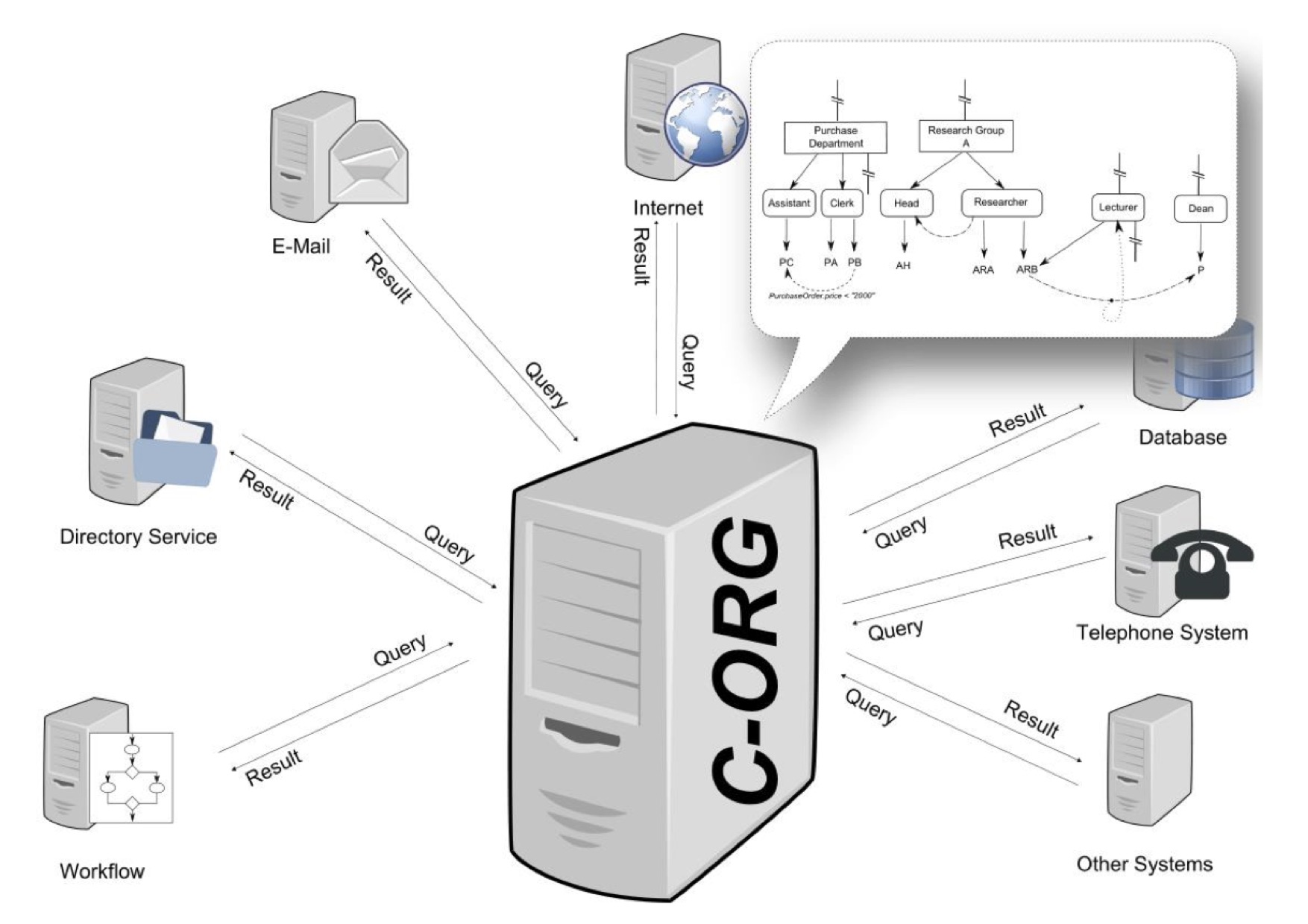
Graph-based Access Control
Graph-based access control (GBAC) is a declarative programming, declarative way to define access control, access rights, task assignments, recipients and content in information systems. The access rights are granted to objects like files or documents, but also business objects like an account. It can also be used for the assignment of agents to tasks in workflow environments. Organizations are modeled as a specific kind of semantic graph comprising the organizational units, the roles and functions as well as the human and automatic agents (i.a. persons, machines). Compared to other approaches like role-based access control or attribute-based access control, the main difference is that in GBAC access rights are defined using an organizational query language instead of total enumeration. History The foundations of GBAC go back to a research project named CoCoSOrg (Configurable Cooperation System) [] (in English language please see ) at Bamberg University. In CoCoSOrg an organization ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |