|
Digital Watermarking
A digital watermark is a kind of marker covertly embedded in a noise-tolerant signal such as audio, video or image data. It is typically used to identify ownership of the copyright of such signal. "Watermarking" is the process of hiding digital information in a carrier signal; the hidden information should,Ingemar J. Cox: ''Digital watermarking and steganography''. Morgan Kaufmann, Burlington, MA, USA, 2008 but does not need to, contain a relation to the carrier signal. Digital watermarks may be used to verify the authenticity or integrity of the carrier signal or to show the identity of its owners. It is prominently used for tracing copyright infringements and for banknote authentication. Like traditional physical watermarks, digital watermarks are often only perceptible under certain conditions, e.g. after using some algorithm.Frank Y. Shih: ''Digital watermarking and steganography: fundamentals and techniques''. Taylor & Francis, Boca Raton, FL, USA, 2008 If a digital watermar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signal (electrical Engineering)
In signal processing, a signal is a function that conveys information about a phenomenon. Any quantity that can vary over space or time can be used as a signal to share messages between observers. The '' IEEE Transactions on Signal Processing'' includes audio, video, speech, image, sonar, and radar as examples of signal. A signal may also be defined as observable change in a quantity over space or time (a time series), even if it does not carry information. In nature, signals can be actions done by an organism to alert other organisms, ranging from the release of plant chemicals to warn nearby plants of a predator, to sounds or motions made by animals to alert other animals of food. Signaling occurs in all organisms even at cellular levels, with cell signaling. Signaling theory, in evolutionary biology, proposes that a substantial driver for evolution is the ability of animals to communicate with each other by developing ways of signaling. In human engineering, signals are ty ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Interference (communication)
In telecommunications, an interference is that which modifies a signal in a disruptive manner, as it travels along a communication channel between its source and receiver. The term is often used to refer to the addition of unwanted signals to a useful signal. Common examples include: * Electromagnetic interference (EMI) * Co-channel interference (CCI), also known as crosstalk * Adjacent-channel interference (ACI) * Intersymbol interference (ISI) * Inter-carrier interference (ICI), caused by doppler shift in OFDM modulation (multitone modulation). * Common-mode interference (CMI) * Conducted interference Noise is a form of interference but not all interference is noise. Radio resource management aims at reducing and controlling the co-channel and adjacent-channel interference. Interference alignment A solution to interference problems in wireless communication networks is interference alignment, which was crystallized by Syed Ali Jafar at the University of California, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EURion Constellation
The EURion constellation (also known as Omron rings or doughnuts) is a pattern of symbols incorporated into a number of secure documents such as banknotes and ownership title certificates designs worldwide since about 1996. It is added to help imaging software detect the presence of such a document in a digital image. Such software can then block the user from reproducing banknotes to prevent counterfeiting using colour photocopiers. Description The name "EURion constellation" was coined by security researcher Markus Kuhn, who uncovered the pattern on the 10 Euro (€10) banknote in early 2002 while experimenting with a Xerox colour photocopier that refused to reproduce banknotes. Markus KuhnThe EURion constellation Security Group presentation, Computer Laboratory, University of Cambridge, 8 February 2002. The pattern has never been mentioned officially; Kuhn named it the EURion constellation as it resembled the astronomical Orion constellation, and EUR is the ISO 4217 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Copy Attack
The copy attack is an attack on certain digital watermarking systems proposed by M. Kutter, S. Voloshynovskiy, and A. Herrige in a paper presented in January, 2000 at the Photonics West SPIE convention. In some scenarios, a digital watermark is added to a piece of media such as an image, film A film also called a movie, motion picture, moving picture, picture, photoplay or (slang) flick is a work of visual art that simulates experiences and otherwise communicates ideas, stories, perceptions, feelings, beauty, or atmospher ..., or audio clip, to prove its authenticity. If a piece of media were presented and found to lack a watermark, it would be considered suspect. Alternatively, a security system could be devised which would limit a user's ability to manipulate any piece of media which contained a watermark. For instance, a DVD burner may prohibit making copies of a film which contained a watermark. The copy attack attempts to thwart the effectiveness of such ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Coded Anti-Piracy
Coded anti-piracy (CAP) is an anti-copyright infringement technology which marks each film print of a motion picture with a distinguishing pattern of dots, used as a forensic identifier to identify the source of illegal copies. They are not to be confused with cue marks, which are black or white circles usually in the upper right-hand corner of the frame. A cue mark is used to signal the projectionist that a particular reel of a film is ending, as most films come to theaters on several reels of celluloid. CAP code CAP coding is a multi-dot pattern that is printed in several frames of a film print of a theatrically exhibited motion picture. It is sometimes accompanied by text code printed on the edge of a motion picture print, outside the visible picture area. The dots are arranged in a unique pattern as identification of the particular print of a movie, and are added during manufacture. The marks are not present on the original film negative; they are produced either by physi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Journal Of Universal Computer Science
The ''Journal of Universal Computer Science'' (''J.UCS'') is a monthly peer-reviewed open-access scientific journal covering all aspects of computer science. History The journal was established in 1994 and is published by the J.UCS Consortium, formed by nine research organisations. The editors-in-chief are Muhammad Tanvir Afzal (Capital University of Science & Technology), Wolf-Tilo Balke (Leibniz University Hannover), Christian Gütl (Graz University of Technology), Rocael Hernández Rizzardini ( Galileo University), Matthias Jarke (RWTH Aachen University), Stefanie Lindstaedt (Graz University of Technology), Peter Serdyukov (National University), and Klaus Tochtermann (Graz University of Technology). Abstracting and indexing The journal is abstracted and indexed in Current Contents/Engineering, Computing & Technology, Science Citation Index Expanded, and Scopus. According to the '' Journal Citation Reports'', the journal has a 2017 impact factor The impact factor (IF) or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
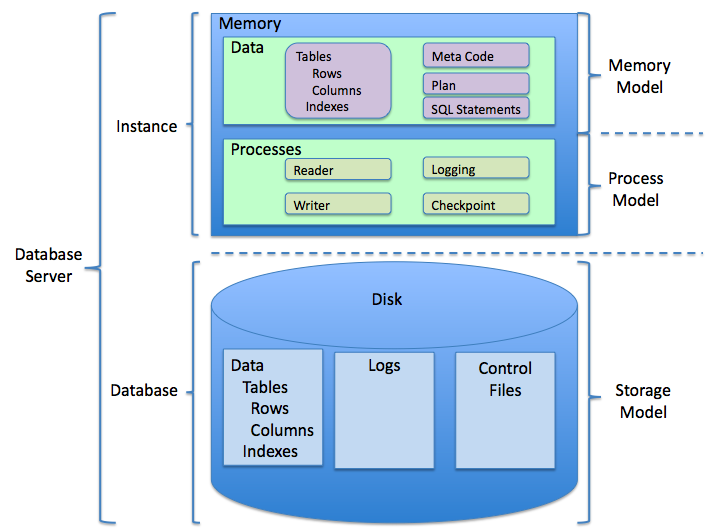
Relational Database
A relational database is a (most commonly digital) database based on the relational model of data, as proposed by E. F. Codd in 1970. A system used to maintain relational databases is a relational database management system (RDBMS). Many relational database systems are equipped with the option of using the SQL (Structured Query Language) for querying and maintaining the database. History The term "relational database" was first defined by E. F. Codd at IBM in 1970. Codd introduced the term in his research paper "A Relational Model of Data for Large Shared Data Banks". In this paper and later papers, he defined what he meant by "relational". One well-known definition of what constitutes a relational database system is composed of Codd's 12 rules. However, no commercial implementations of the relational model conform to all of Codd's rules, so the term has gradually come to describe a broader class of database systems, which at a minimum: # Present the data to the user as re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reconnaissance
In military operations, reconnaissance or scouting is the exploration of an area by military forces to obtain information about enemy forces, terrain, and other activities. Examples of reconnaissance include patrolling by troops ( skirmishers, long-range reconnaissance patrol, U.S. Army Rangers, cavalry scouts, or military intelligence specialists), ships or submarines, crewed or uncrewed reconnaissance aircraft, satellites, or by setting up observation posts. Espionage is usually considered to be different from reconnaissance, as it is performed by non-uniformed personnel operating behind enemy lines. Often called recce (British, Canadian and Australian English) or recon (American English), the word for this activity has at its root the associated verb ''reconnoitre'' or ''reconnoiter''. Etymology The word from the Middle French ''reconoissance''. Overview Reconnaissance conducted by ground forces includes special reconnaissance, armored reconnaissance, amphibio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Hash
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with fixed size of n bits) that has special properties desirable for cryptography: * the probability of a particular n-bit output result ( hash value) for a random input string ("message") is 2^ (like for any good hash), so the hash value can be used as a representative of the message; * finding an input string that matches a given hash value (a ''pre-image'') is unfeasible, unless the value is selected from a known pre-calculated dictionary ("rainbow table"). The ''resistance'' to such search is quantified as security strength, a cryptographic hash with n bits of hash value is expected to have a ''preimage resistance'' strength of n bits. A ''second preimage'' resistance strength, with the same expectations, refers to a similar problem of finding a second message that matches the given hash value when one message is already known; * finding any pair of different mes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometric
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, behavioral profiling, and credentials. Some researchers have coined the term behaviometrics to describe the latter class of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Camera
A digital camera is a camera that captures photographs in digital memory. Most cameras produced today are digital, largely replacing those that capture images on photographic film. Digital cameras are now widely incorporated into mobile devices like smartphones with the same or more capabilities and features of dedicated cameras (which are still available). High-end, high-definition dedicated cameras are still commonly used by professionals and those who desire to take higher-quality photographs. Digital and digital movie cameras share an optical system, typically using a lens with a variable diaphragm to focus light onto an image pickup device. The diaphragm and shutter admit a controlled amount of light to the image, just as with film, but the image pickup device is electronic rather than chemical. However, unlike film cameras, digital cameras can display images on a screen immediately after being recorded, and store and delete images from memory. Many digital cameras can al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Forensic Evidence
Forensic identification is the application of forensic science, or "forensics", and technology to identify specific objects from the trace evidence they leave, often at a crime scene or the scene of an accident. Forensic means "for the courts". Human identification People can be identified by their fingerprints. This assertion is supported by the philosophy of friction ridge identification, which states that friction ridge identification is established through the agreement of friction ridge formations, in sequence, having sufficient uniqueness to individualize. Friction ridge identification is also governed by four premises or statements of facts: # Friction ridges develop on the fetus in their definitive form prior to birth. # Friction ridges are persistent throughout life except for permanent scarring, disease, or decomposition after death. # Friction ridge paths and the details in small areas of friction ridges are unique and never repeated. # Overall, friction ridge pattern ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |