|
Data Synchronization
Data synchronization is the process of establishing consistency between source and target data stores, and the continuous harmonization of the data over time. It is fundamental to a wide variety of applications, including file synchronization and mobile device synchronization. Data synchronization can also be useful in encryption for synchronizing public key servers. File-based solutions There are tools available for file synchronization, version control ( CVS, Subversion, etc.), distributed filesystems (Coda, etc.), and mirroring (rsync, etc.), in that all these attempt to keep sets of files synchronized. However, only version control and file synchronization tools can deal with modifications to more than one copy of the files. * File synchronization is commonly used for home backups on external hard drives or updating for transport on USB flash drives. The automatic process prevents copying already identical files, thus can save considerable time relative to a manual copy, al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Consistency (database Systems)
In database systems, consistency (or correctness) refers to the requirement that any given database transaction must change affected data only in allowed ways. Any data written to the database must be valid according to all defined rules, including constraints, cascades, triggers, and any combination thereof. This does not guarantee correctness of the transaction in all ways the application programmer might have wanted (that is the responsibility of application-level code) but merely that any programming errors cannot result in the violation of any defined database constraints.C. J. Date, "SQL and Relational Theory: How to Write Accurate SQL Code 2nd edition", ''O'reilly Media, Inc.'', 2012, pg. 180. Consistency can also be understood as after a successful write, update or delete of a Record, any read request immediately receives the latest value of the Record. As an ACID guarantee Consistency is one of the four guarantees that define ACID transactions; however, significant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Slepian–Wolf Coding
__NOTOC__ In information theory and communication, the Slepian–Wolf coding, also known as the Slepian–Wolf bound, is a result in distributed source coding discovered by David Slepian and Jack Wolf in 1973. It is a method of theoretically coding two lossless compressed correlated sources. Problem setup Distributed coding is the coding of two, in this case, or more dependent sources with separate encoders and a joint decoder. Given two statistically dependent independent and identically distributed finite-alphabet random sequences X^n and Y^n, the Slepian–Wolf theorem gives a theoretical bound for the lossless coding rate for distributed coding of the two sources. Theorem The bound for the lossless coding rates as shown below: : R_X\geq H(X, Y), \, : R_Y\geq H(Y, X), \, : R_X+R_Y\geq H(X,Y). \, If both the encoder and the decoder of the two sources are independent, the lowest rate it can achieve for lossless compression is H(X) and H(Y) for X and Y respectively, where ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SyncML
SyncML (Synchronization Markup Language) is the former name for a platform-independent information synchronization standard. The project is currently referred to as ''Open Mobile Alliance Data Synchronization and Device Management''. The purpose of SyncML is to offer an open standard as a replacement for existing data synchronization solutions, which have mostly been somewhat vendor-, application- or operating system specific. SyncML 1.0 specification was released on December 17, 2000, and 1.1 on February 26, 2002. Internals SyncML works by exchanging commands, which can be requests and responses. As an example: * the mobile sends an Alert command for signaling the wish to begin a refresh-only synchronization * the computer responds with a Status command for accepting the request * the mobile sends one or more Sync command containing an Add sub-command for each item (e.g., phonebook entry); if the number of entries is large, it does not include the tag; * in the latter case, the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blockchain
A blockchain is a type of distributed ledger technology (DLT) that consists of growing lists of records, called ''blocks'', that are securely linked together using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree, where data nodes are represented by leaves). The timestamp proves that the transaction data existed when the block was created. Since each block contains information about the previous block, they effectively form a ''chain'' (compare linked list data structure), with each additional block linking to the ones before it. Consequently, blockchain transactions are irreversible in that, once they are recorded, the data in any given block cannot be altered retroactively without altering all subsequent blocks. Blockchains are typically managed by a peer-to-peer, peer-to-peer (P2P) computer network for use as a public distributed ledger, where nodes collectively adhere to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Distributed Hash Table
A distributed hash table (DHT) is a distributed system that provides a lookup service similar to a hash table: key–value pairs are stored in a DHT, and any participating node can efficiently retrieve the value associated with a given key. The main advantage of a DHT is that nodes can be added or removed with minimum work around re-distributing keys. ''Keys'' are unique identifiers which map to particular ''values'', which in turn can be anything from addresses, to documents, to arbitrary data. Responsibility for maintaining the mapping from keys to values is distributed among the nodes, in such a way that a change in the set of participants causes a minimal amount of disruption. This allows a DHT to scale to extremely large numbers of nodes and to handle continual node arrivals, departures, and failures. DHTs form an infrastructure that can be used to build more complex services, such as anycast, cooperative web caching, distributed file systems, domain name services, instant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
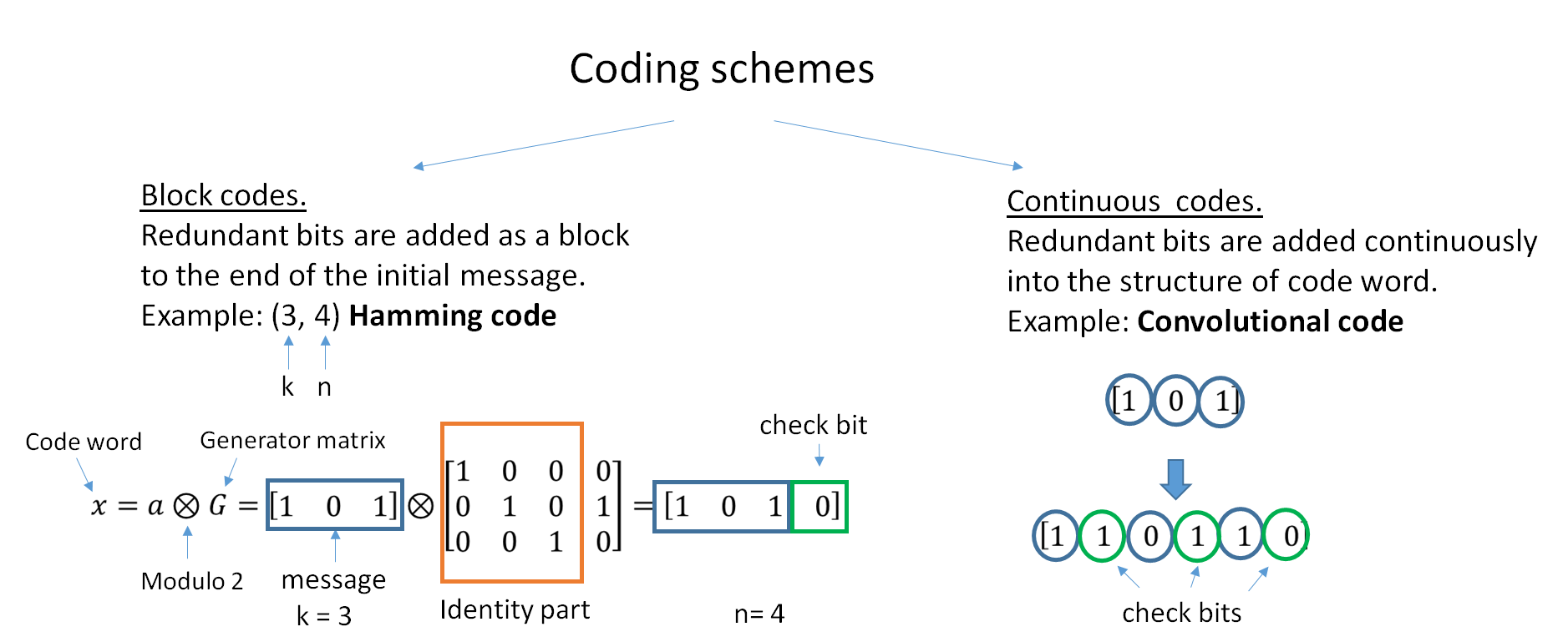
Error Correction Code
In computing, telecommunication, information theory, and coding theory, an error correction code, sometimes error correcting code, (ECC) is used for controlling errors in data over unreliable or noisy communication channels. The central idea is the sender encodes the message with redundant information in the form of an ECC. The redundancy allows the receiver to detect a limited number of errors that may occur anywhere in the message, and often to correct these errors without retransmission. The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code. ECC contrasts with error detection in that errors that are encountered can be corrected, not simply detected. The advantage is that a system using ECC does not require a reverse channel to request retransmission of data when an error occurs. The downside is that there is a fixed overhead that is added to the message, thereby requiring a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secret Sharing
Secret sharing (also called secret splitting) refers to methods for distributing a secret among a group, in such a way that no individual holds any intelligible information about the secret, but when a sufficient number of individuals combine their 'shares', the secret may be reconstructed. Whereas ''insecure'' secret sharing allows an attacker to gain more information with each share, ''secure'' secret sharing is 'all or nothing' (where 'all' means the necessary number of shares). In one type of secret sharing scheme there is one ''dealer'' and ''n'' ''players''. The dealer gives a share of the secret to the players, but only when specific conditions are fulfilled will the players be able to reconstruct the secret from their shares. The dealer accomplishes this by giving each player a share in such a way that any group of ''t'' (for ''threshold'') or more players can together reconstruct the secret but no group of fewer than ''t'' players can. Such a system is called a -threshol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Raft (computer Science)
A raft is any flat structure for support or transportation over water. It is usually of basic design, characterized by the absence of a hull. Rafts are usually kept afloat by using any combination of buoyant materials such as wood, sealed barrels, or inflated air chambers (such as pontoons), and are typically not propelled by an engine. Rafts are an ancient mode of transport; naturally-occurring rafts such as entwined vegetation and pieces of wood have been used to traverse water since the dawn of humanity. Human-made rafts Traditional or primitive rafts were constructed of wood or reeds. Modern rafts may also use pontoons, drums, or extruded polystyrene blocks. Inflatable rafts up to the 20th century used flotation chambers made of goat- or buffalo-skins, but most now use durable, multi-layered rubberized fabrics. Depending on its use and size, it may have a superstructure, masts, or rudders. Timber rafting is used by the logging industry for the transportation of logs, b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Paxos (computer Science)
Paxos is a family of protocols for solving consensus in a network of unreliable or fallible processors. Consensus is the process of agreeing on one result among a group of participants. This problem becomes difficult when the participants or their communications may experience failures. Consensus protocols are the basis for the state machine replication approach to distributed computing, as suggested by Leslie Lamport and surveyed by Fred Schneider. State machine replication is a technique for converting an algorithm into a fault-tolerant, distributed implementation. Ad-hoc techniques may leave important cases of failures unresolved. The principled approach proposed by Lamport et al. ensures all cases are handled safely. The Paxos protocol was first submitted in 1989 and named after a fictional legislative consensus system used on the Paxos island in Greece, where Lamport wrote that the parliament had to function "even though legislators continually wandered in and out of the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Replication (computing)
Replication in computing involves sharing information so as to ensure consistency between redundant resources, such as software or hardware components, to improve reliability, fault-tolerance, or accessibility. Terminology Replication in computing can refer to: * ''Data replication'', where the same data is stored on multiple storage devices * ''Computation replication'', where the same computing task is executed many times. Computational tasks may be: ** ''Replicated in space'', where tasks are executed on separate devices ** ''Replicated in time'', where tasks are executed repeatedly on a single device Replication in space or in time is often linked to scheduling algorithms. Access to a replicated entity is typically uniform with access to a single non-replicated entity. The replication itself should be transparent to an external user. In a failure scenario, a failover of replicas should be hidden as much as possible with respect to quality of service. Computer scientis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
W-shingling
In natural language processing a ''w-shingling'' is a set of ''unique'' ''shingles'' (therefore ''n-grams'') each of which is composed of contiguous subsequences of tokens within a document, which can then be used to ascertain the similarity between documents. The symbol ''w'' denotes the quantity of tokens in each shingle selected, or solved for. The document, "a rose is a rose is a rose" can therefore be maximally tokenized as follows: :(a,rose,is,a,rose,is,a,rose) The set of all contiguous ''sequences of 4 tokens'' (Thus 4=''n'', thus 4-''grams'') is : Which can then be reduced, or maximally shingled in this particular instance to . Resemblance For a given shingle size, the degree to which two documents ''A'' and ''B'' resemble each other can be expressed as the ratio of the magnitudes of their shinglings' intersection and union, or :r(A,B)= where , A, is the size of set A. The resemblance is a number in the range ,1 where 1 indicates that two documents are ident ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Synchronization
Data synchronization is the process of establishing consistency between source and target data stores, and the continuous harmonization of the data over time. It is fundamental to a wide variety of applications, including file synchronization and mobile device synchronization. Data synchronization can also be useful in encryption for synchronizing public key servers. File-based solutions There are tools available for file synchronization, version control ( CVS, Subversion, etc.), distributed filesystems (Coda, etc.), and mirroring (rsync, etc.), in that all these attempt to keep sets of files synchronized. However, only version control and file synchronization tools can deal with modifications to more than one copy of the files. * File synchronization is commonly used for home backups on external hard drives or updating for transport on USB flash drives. The automatic process prevents copying already identical files, thus can save considerable time relative to a manual copy, al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |