|
Conformance Checking
Business process conformance checking (a.k.a. conformance checking for short) is a family of process mining techniques to compare a process model with an event log of the same process. It is used to check if the actual execution of a business process, as recorded in the event log, conforms to the model and vice versa. For instance, there may be a process model indicating that purchase orders of more than one million euros require two checks. Analysis of the event log will show whether this rule is followed or not. Another example is the checking of the so-called “ four-eyes” principle stating that particular activities should not be executed by one and the same person. By scanning the event log using a model specifying these requirements, one can discover potential cases of fraud. Hence, conformance checking may be used to detect, locate and explain deviations, and to measure the severity of these deviations. Overview Conformance checking techniques take as input a process mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Conformance
Conformance is how well something, such as a product, service or a system, meets a specified standard and may refer more specifically to: * Conformance testing, testing to determine whether a product or system meets some specified standard * SNIA Conformance Testing Program The Storage Networking Industry Association (SNIA) is a registered 501(c)(6) non-profit trade association incorporated in December 1997. SNIA has more than 185 unique members, 2,000 active contributing members and over 50,000 IT end users and st ..., a program trying to bring third-party standards conformance to the storage networking marketplace See also * Conformation (other), a variety of similar concepts applied to chemicals or animals {{disambiguation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Process Mining
Process mining is a family of techniques relating the fields of data science and process management to support the analysis of operational processes based on event logs. The goal of process mining is to turn event data into insights and actions. Process mining is an integral part of data science, fueled by the availability of event data and the desire to improve processes. Process mining techniques use event data to show what people, machines, and organizations are really doing. Process mining provides novel insights that can be used to identify the executional path taken by operational processes and address their performance and compliance problems. Process mining starts from event data. Input for process mining is an event log. An event log views a process from a particular angle. Each event in the log should contain (1) a unique identifier for a particular process instance (called case id), (2) an activity (description of the event that is occurring), and (3) a timestamp. There ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Process Modeling
The term process model is used in various contexts. For example, in business process modeling the enterprise process model is often referred to as the ''business process model''. Overview Process models are processes of the same nature that are classified together into a model. Thus, a process model is a description of a process at the type level. Since the process model is at the type level, a process is an instantiation of it. The same process model is used repeatedly for the development of many applications and thus, has many instantiations. One possible use of a process model is to prescribe how things must/should/could be done in contrast to the process itself which is really what happens. A process model is roughly an anticipation of what the process will look like. What the process shall be will be determined during actual system development.Colette Rolland and Pernici, C. Thanos (1998). ''A Comprehensive View of Process Engineering. Proceedings of the 10th International ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Event Log
In software engineering, tracing involves a specialized use of logging to record information about a program's execution. This information is typically used by programmers for debugging purposes, and additionally, depending on the type and detail of information contained in a trace log, by experienced system administrators or technical-support personnel and by software monitoring tools to diagnose common problems with software. Tracing is a cross-cutting concern. There is not always a clear distinction between ''tracing'' and other forms of ''logging'', except that the term ''tracing'' is almost never applied to logging that is a functional requirement of a program (therefore excluding logging of data from an external source, such as data acquisition in a high-energy physics experiment, and write-ahead logging). Logs that record program usage (such as a server log) or operating-system events primarily of interest to a system administrator (see for example ''Event Viewer'') fal ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Process
A business process, business method or business function is a collection of related, structured activities or tasks by people or equipment in which a specific sequence produces a service or product (serves a particular business goal) for a particular customer or customers. Business processes occur at all organizational levels and may or may not be visible to the customers. A business process may often be visualized (modeled) as a flowchart of a sequence of activities with interleaving decision points or as a process matrix of a sequence of activities with relevance rules based on data in the process. The benefits of using business processes include improved customer satisfaction and improved agility for reacting to rapid market change. Process-oriented organizations break down the barriers of structural departments and try to avoid functional silos. Overview A business process begins with a mission objective (an external event) and ends with achievement of the business object ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
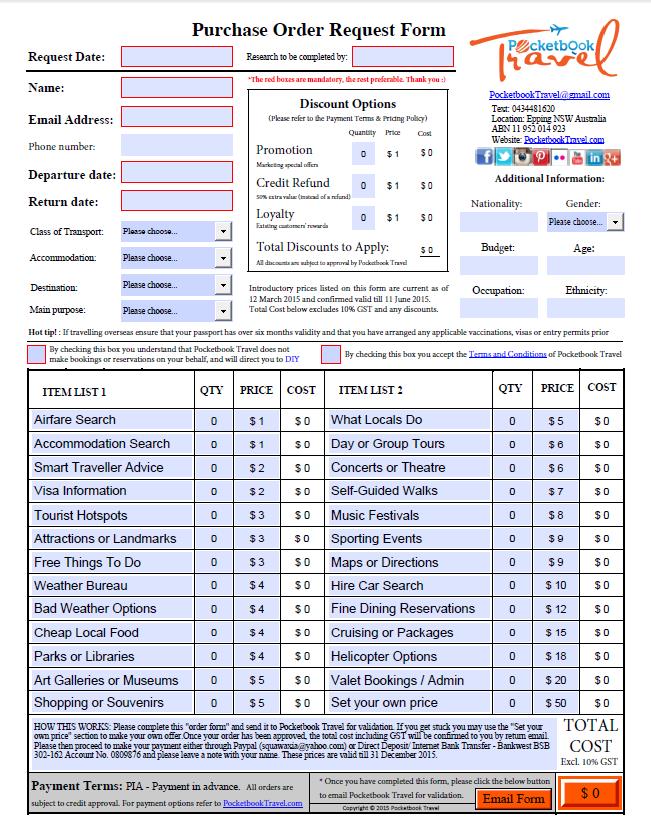
Purchase Order
A purchase order is a commercial document and first official offer issued by a buyer to a seller, indicating types, quantities, and agreed prices for products or services. It is used to control the purchasing of products and services from external suppliers. Purchase orders can be an essential part of enterprise resource planning system orders. An indent is a purchase order often placed through an agent (indent agent) under specified conditions of sale. The issue of a purchase order does not itself form a contract. If no prior contract exists, then it is the acceptance of the order by the seller that forms a contract between the buyer and seller. Overview Purchase orders allow buyers to clearly and openly communicate with the sellers to maintain transparency. They may also help a purchasing agent to manage incoming orders and pending orders. Sellers are also protected by the use of purchase orders, in case of a buyer's refusal to pay for goods or services. Purchase orders ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Four-eyes Principle
The two-person rule is a control mechanism designed to achieve a high level of security for especially critical material or operations. Under this rule, access and actions require the presence of two or more authorized people at all times. United States: nuclear weapons Per US Air Force Instruction (AFI) 91-104, "the two-person concept" is designed to prevent accidental or malicious launch of nuclear weapons by a single individual. In the case of Minuteman missile launch crews, once a launch order is received, both operators must agree that it is valid by comparing the authorization code in the order against a ''Sealed Authenticator'' (a special sealed envelope containing a verification code). These Sealed Authenticators are stored in a safe which has two separate locks. Each operator has the key to only one lock, so neither can open the safe alone. Also, each operator has one of two launch keys; once the order is verified, they must insert the keys in slots on the control panel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fraud
In law, fraud is intentional deception to secure unfair or unlawful gain, or to deprive a victim of a legal right. Fraud can violate civil law (e.g., a fraud victim may sue the fraud perpetrator to avoid the fraud or recover monetary compensation) or criminal law (e.g., a fraud perpetrator may be prosecuted and imprisoned by governmental authorities), or it may cause no loss of money, property, or legal right but still be an element of another civil or criminal wrong. The purpose of fraud may be monetary gain or other benefits, for example by obtaining a passport, travel document, or driver's license, or mortgage fraud, where the perpetrator may attempt to qualify for a mortgage by way of false statements. Internal fraud, also known as "insider fraud", is fraud committed or attempted by someone within an organisation such as an employee. A hoax is a distinct concept that involves deliberate deception without the intention of gain or of materially damaging or depriving a vi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Linguistic Description
In the study of language, description or descriptive linguistics is the work of objectively analyzing and describing how language is actually used (or how it was used in the past) by a speech community. François & Ponsonnet (2013). All academic research in linguistics is descriptive; like all other scientific disciplines, it seeks to describe reality, without the bias of preconceived ideas about how it ought to be. Modern descriptive linguistics is based on a structural approach to language, as exemplified in the work of Leonard Bloomfield and others. This type of linguistics utilizes different methods in order to describe a language such as basic data collection, and different types of elicitation methods. Descriptive versus prescriptive linguistics Linguistic description is often contrasted with linguistic prescription, — entry for "Descriptivism and prescriptivism" quotation: "Contrasting terms in linguistics." (p.286) which is found especially in education and in publi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Normative
Normative generally means relating to an evaluative standard. Normativity is the phenomenon in human societies of designating some actions or outcomes as good, desirable, or permissible, and others as bad, undesirable, or impermissible. A norm in this normative sense means a standard for evaluating or making judgments about behavior or outcomes. Normative is sometimes also used, somewhat confusingly, to mean relating to a descriptive standard: doing what is normally done or what most others are expected to do in practice. In this sense a norm is not evaluative, a basis for judging behavior or outcomes; it is simply a fact or observation about behavior or outcomes, without judgment. Many researchers in science, law, and philosophy try to restrict the use of the term normative to the evaluative sense and refer to the description of behavior and outcomes as positive, descriptive, predictive, or empirical. ''Normative'' has specialised meanings in different academic disciplines such a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deviation (statistics)
In mathematics and statistics, deviation is a measure of difference between the observed value of a variable and some other value, often that variable's mean. The sign of the deviation reports the direction of that difference (the deviation is positive when the observed value exceeds the reference value). The magnitude of the value indicates the size of the difference. Types A deviation that is a difference between an observed value and the ''true value'' of a quantity of interest (where ''true value'' denotes the Expected Value, such as the population mean) is an error. A deviation that is the difference between the observed value and an ''estimate'' of the true value (e.g. the sample mean; the Expected Value of a sample can be used as an estimate of the Expected Value of the population) is a residual. These concepts are applicable for data at the interval and ratio levels of measurement. Unsigned or absolute deviation In statistics, the absolute deviation of an element of a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Behavior
Behavior (American English) or behaviour (British English) is the range of actions and mannerisms made by individuals, organisms, systems or artificial entities in some environment. These systems can include other systems or organisms as well as the inanimate physical environment. It is the computed response of the system or organism to various stimuli or inputs, whether internal or external, conscious or subconscious, overt or covert, and voluntary or involuntary. Taking a behavior informatics perspective, a behavior consists of actor, operation, interactions, and their properties. This can be represented as a behavior vector. Models Biology Although disagreement exists as to how to precisely define behavior in a biological context, one common interpretation based on a meta-analysis of scientific literature states that "behavior is the internally coordinated responses (actions or inactions) of whole living organisms (individuals or groups) to internal and/or external sti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |