|
Chmod
is a shell command for changing access permissions and special mode flags of files (including special files such as directories). The name is short for ''change mode'' where ''mode'' refers to the permissions and flags collectively. The command originated in AT&T Unix version 1 and was exclusive to Unix and Unix-like operating systems until it was ported to other operating systems such as Windows (in UnxUtils) and IBM i. In Unix and Unix-like operating systems, a system call with the same name as the command, , provides access to the underlying access control data. The command exposes the capabilities of the system call to a shell user. As the need for enhanced file-system permissions grew, access-control lists were added to many file systems to augment the modes controlled via . The implementation of bundled in GNU coreutils was written by David MacKenzie and Jim Meyering. Use Although the syntax of the command varies somewhat by implementation, it generally acc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Setgid
The Unix and Linux access rights flags setuid and setgid (short for ''set user identity'' and ''set group identity'') allow users to run an executable with the file system permissions of the executable's owner or group respectively and to change behaviour in directories. They are often used to allow users on a computer system to run programs with temporarily elevated privileges to perform a specific task. While the assumed user id or group id privileges provided are not always elevated, at a minimum they are specific. The flags setuid and setgid are needed for tasks that require different privileges than what the user is normally granted, such as the ability to alter system files or databases to change their login password. Some of the tasks that require additional privileges may not immediately be obvious, though, such as the ping command, which must send and listen for control packets on a network interface. File modes The setuid and setgid bits are normally represented as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Setuid
The Unix and Linux access rights flags setuid and setgid (short for ''set user identity'' and ''set group identity'') allow users to run an executable with the file system permissions of the executable's owner or group respectively and to change behaviour in directories. They are often used to allow users on a computer system to run programs with temporarily elevated privileges to perform a specific task. While the assumed user id or group id privileges provided are not always elevated, at a minimum they are specific. The flags setuid and setgid are needed for tasks that require different privileges than what the user is normally granted, such as the ability to alter system files or databases to change their login password. Some of the tasks that require additional privileges may not immediately be obvious, though, such as the ping command, which must send and listen for control packets on a network interface. File modes The setuid and setgid bits are normally represented a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Symbolic Link
In computing, a symbolic link (also symlink or soft link) is a file whose purpose is to point to a file or directory (called the "target") by specifying a path thereto. Symbolic links are supported by POSIX and by most Unix-like operating systems, such as FreeBSD, Linux, and macOS. Support also exists in Windows 10 and 11. CTSS on IBM 7090 had files linked by name in 1963. By 1978 minicomputer operating systems from DEC, and in Data General's RDOS included symbolic links. Overview A symbolic link contains a text string that is automatically interpreted and followed by the operating system as a path to another file or directory. This other file or directory is called the "target". The symbolic link is a second file that exists independently of its target. If a symbolic link is deleted, its target remains unaffected. If a symbolic link points to a target, and sometime later that target is moved, renamed or deleted, the symbolic link is not automatically updated or deleted, b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Coreutils
The GNU Core Utilities or coreutils is a collection of GNU software that implements many standard, Unix-based shell commands. The utilities generally provide POSIX compliant interface when the environment variable is set, but otherwise offers a superset to the standard interface. For example, the utilities support long options and options after parameters. This environment variable enables a different functionality in BSD. Similar collections are available in the FOSS ecosystem, with a slightly different scope and focus (less functionality), or license. For example, BusyBox which is licensed under GPL-2.0-only, and Toybox which is licensed under 0BSD. Commands The commands implemented by coreutils are listed below. Throughout this article and customary for Unix-based systems, the term ''file'' refers to all file system items including regular files and special files such as directories. File utilities * chcon Changes file security context ( SELinux) * chgrp Chan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Octal
Octal (base 8) is a numeral system with eight as the base. In the decimal system, each place is a power of ten. For example: : \mathbf_ = \mathbf \times 10^1 + \mathbf \times 10^0 In the octal system, each place is a power of eight. For example: : \mathbf_8 = \mathbf \times 8^2 + \mathbf \times 8^1 + \mathbf \times 8^0 By performing the calculation above in the familiar decimal system, we see why 112 in octal is equal to 64+8+2=74 in decimal. Octal numerals can be easily converted from binary representations (similar to a quaternary numeral system) by grouping consecutive binary digits into groups of three (starting from the right, for integers). For example, the binary representation for decimal 74 is 1001010. Two zeroes can be added at the left: , corresponding to the octal digits , yielding the octal representation 112. Usage In China The eight bagua or trigrams of the I Ching correspond to octal digits: * 0 = ☷, 1 = ☳, 2 = ☵, 3 = ☱, * 4 = ☶, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
GNU Core Utilities
The GNU Core Utilities or coreutils is a collection of GNU software that implements many standard, Unix-based shell commands. The utilities generally provide POSIX compliant interface when the environment variable is set, but otherwise offers a superset to the standard interface. For example, the utilities support long options and options after parameters. This environment variable enables a different functionality in BSD. Similar collections are available in the FOSS ecosystem, with a slightly different scope and focus (less functionality), or license. For example, BusyBox which is licensed under GPL-2.0-only, and Toybox which is licensed under 0BSD. Commands The commands implemented by coreutils are listed below. Throughout this article and customary for Unix-based systems, the term ''file'' refers to all file system items including regular files and special files such as directories. File utilities * chcon Changes file security context ( SELinux) * chgrp Chan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
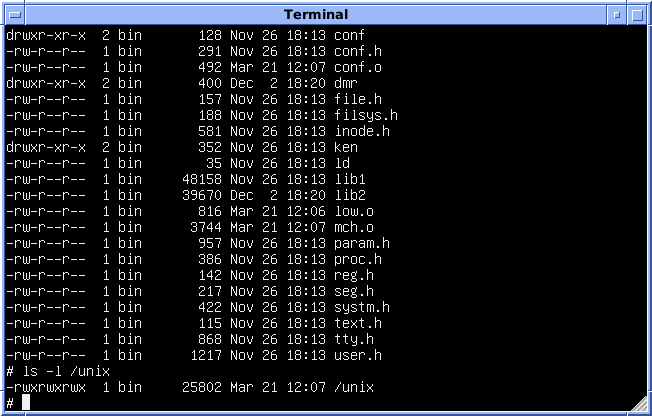
File-system Permissions
Typically, a file system maintains permission settings for each stored item commonly computer file, files and directory (computer), directories that either grant or deny the ability to manipulate file system items. Often the settings allow controlling access based on function such as read, change, navigate, and Execution (computing), execute and to different computer user, users and groups of users. One well-established technology was developed for Unix and later codified by POSIX. Another common technology is an access-control list (ACL) with multiple variants implemented in file systems and one codified by POSIX. Since POSIX defines both the older Unix-based technology as well as ACLs, the former is called ''traditional POSIX permissions'' for clarity even though it is not a well-known term. A permission-driven user interface tailors the functionality available to the user based on file system item permissions. For example, the interface might hide menu options that are not al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
UnxUtils
UnxUtils is a collection of utility programs that provide popular Unix-based shell commands ported from GNU implementations as native Windows programs that depend only on Win32 and the Microsoft C- runtime ( msvcrt.dll). The collection was last updated externally on April 15, 2003, by Karl M. Syring. , the most recent release was an open-source project at SourceForge, with the latest binary release in March, 2007 (though the files are dated 2000). The independent distribution included a main zip archive (UnxUtils.zip, 3,365,638 bytes) complemented by more recent updates (UnxUpdates.zip, 878,847 bytes, brought some binaries up to year 2003), but the SourceForge project has no UnxUpdates.zip package. An alternative collection of Unix-based utilities for Windows is GnuWin32. It has later versions of many programs, but requires supporting files (e.g. DLLs). Supported commands include: * agrep *ansi2knr * basename * bc *bison *bunzip2 *bzip2 *bzip2recover * cat *chgrp *chm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Research Unix
Research Unix refers to the early versions of the Unix operating system for DEC PDP-7, PDP-11, VAX and Interdata 7/32 and 8/32 computers, developed in the Bell Labs Computing Sciences Research Center (CSRC). The term ''Research Unix'' first appeared in the Bell System Technical Journal (Vol. 57, No. 6, Part 2 July/August 1978) to distinguish it from other versions internal to Bell Labs (such as PWB/UNIX and MERT) whose code-base had diverged from the primary CSRC version. However, that term was little-used until Version 8 Unix (1985), but has been retroactively applied to earlier versions as well. Prior to V8, the operating system was most commonly called simply UNIX (in caps) or the UNIX Time-Sharing System. Ancient UNIX is any early release of the Unix code base prior to Unix System III, particularly the Research Unix releases prior to and including Version 7 (the base for UNIX/32V as well as later developments of AT&T Unix). History AT&T licensed Version 5 to ed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
File-system Permissions
Typically, a file system maintains permission settings for each stored item commonly computer file, files and directory (computer), directories that either grant or deny the ability to manipulate file system items. Often the settings allow controlling access based on function such as read, change, navigate, and Execution (computing), execute and to different computer user, users and groups of users. One well-established technology was developed for Unix and later codified by POSIX. Another common technology is an access-control list (ACL) with multiple variants implemented in file systems and one codified by POSIX. Since POSIX defines both the older Unix-based technology as well as ACLs, the former is called ''traditional POSIX permissions'' for clarity even though it is not a well-known term. A permission-driven user interface tailors the functionality available to the user based on file system item permissions. For example, the interface might hide menu options that are not al ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Command (computing)
In computing, a command is an instruction received via an external Interface (computing), interface that directs the behavior of a computer program. Commonly, commands are sent to a program via a command-line interface, a scripting language, script, a network protocol, or as an event triggered in a graphical user interface. Many commands support arguments to specify input and to modify default behavior. Terminology and syntax varies but there are notable common approaches. Typically, an option or a flag is a name (without Whitespace character, whitespace) with a prefix such as dash or Slash (punctuation), slash that modifies default behavior. An option might have a required value that follows it. Typically, flag refers to an option that does not have a following value. A parameter is an argument that specifies input to the command and its meaning is based on its position in the command line relative to other parameters; generally ignoring options. A parameter can specify anything ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
Microsoft Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sectors of the computing industry – Windows (unqualified) for a consumer or corporate workstation, Windows Server for a Server (computing), server and Windows IoT for an embedded system. Windows is sold as either a consumer retail product or licensed to Original equipment manufacturer, third-party hardware manufacturers who sell products Software bundles, bundled with Windows. The first version of Windows, Windows 1.0, was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). The name "Windows" is a reference to the windowing system in GUIs. The 1990 release of Windows 3.0 catapulted its market success and led to various other product families ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |